The vulnerability of teleconferencing software Zoom allows any sites to spy on users via a webcam
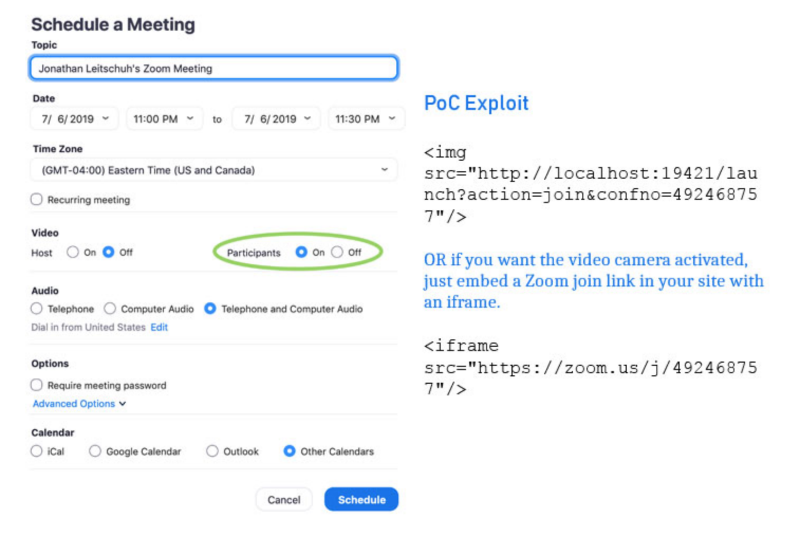
Image: Medium.com
A security researcher has discovered a vulnerability in Zoom teleconferencing software. When using the program on Mac computers, any website opened by the user can activate the camera on the device without requesting permission for this action. This can even be done if the Zoom has already been removed from the computer.
')
What is the problem
Researcher Jonathan Leichuh (Jonathan Leitschuh) has published details of the critical vulnerability CVE-2019-13450. In combination with another security bug, it may allow attackers to remotely spy on Mac users.
Leichu was told by the Zoom team about the vulnerability more than 90 days before the publication of information about it, but the patch closing the bug was released after publication in the blog of the researcher. Thus, all 4 million project users are at risk. Zoom is one of the most popular cloud applications for TV and audio conferences, webinars and training events.
The vulnerability is the incorrect function of the click-to-join function - it was created to automatically activate the Zoom client installed on the computer. With its help, participants can instantly connect to the conference using a browser. To do this, just click on the link-invitation type zoom.us/j/492468757 .
The researcher discovered that in order to activate this feature, Zoom launches a local web server running on port 19421 on the computer, which in an “insecure way” receives commands via HTTPS GET parameters, and any site opened in a browser can interact with it.
To exploit a security bug, an attacker needs to create an invitation link in Zoom and embed it in an external site as a tag to an image or via iFrame. Then you need to convince the victim to go to the site to be able to activate the webcam on her Mac.
In addition to spying on the victim, the vulnerability can be used to carry out a DoS attack on the target computer. To do this, you need to send a large number of GET requests to the local web server.
How to protect
Simple removal of Zoom does not help protect against the problem described. According to the researcher, the click-to-join function supports the command to automatically reset Zoom without user permission.
According to Leich, Zoom experts have released a patch that prohibits attackers from activating a video camera on the victim’s device. At the same time, the ability to secretly connect users to an online conference using malicious Zoom links still remains.
Today, many services operate on the basis of data analysis algorithms. As practice shows, the risks are hidden not only in the vulnerable functionality, but also in the data itself, on the basis of which the system makes decisions.
Along with the advent of new machine learning algorithms, the area of their application has expanded. For several years, machine learning in the field of information security has been used not only to detect attacks, but also to conduct them.
Researchers are actively studying malicious machine learning (adversarial attack). However, in an attempt to overtake the intruders and predict their next step, they forget about the possibilities that attackers are using now: model theft, vulnerabilities in the framework, substitution of training data, logical vulnerabilities.
On Thursday, July 11, at 14:00 , Positive Technologies experts Arseny Reutov and Alexander Murzin will hold a webinar on the topic “Security Risks of Using Artificial Intelligence Techniques”. It will focus on the risks of using machine learning techniques in modern applications.
Participation in the webinar is free, registration is required.
Source: https://habr.com/ru/post/459450/
All Articles