Security Week 27: Insulin Pump Vulnerabilities
 Last week, the US Food and Drug Administration (FDA) issued a warning to users of Medtronic MiniMed insulin pumps ( news , list of vulnerable devices on the FDA website). The manufacturer launched a program to replace the pump with safe models: in seven devices out of 11, the problem cannot be solved by updating the software.
Last week, the US Food and Drug Administration (FDA) issued a warning to users of Medtronic MiniMed insulin pumps ( news , list of vulnerable devices on the FDA website). The manufacturer launched a program to replace the pump with safe models: in seven devices out of 11, the problem cannot be solved by updating the software.Insulin pumps are used in the treatment of diabetes mellitus and consist of a control device, a replaceable insulin tank and a kit for subcutaneous administration. The FDA pumps of two series (MiniMed 508 and MiniMed Paradigm) mentioned in the FDA message can be wirelessly connected to a control device, which under normal conditions is used by the attending physician or the patient himself to change the operating parameters. As it turned out, anyone can take control, it is enough to be within the range of the radio transmitter. Such vulnerabilities are far from being discovered for the first time, but for the first time, both the manufacturer and state services are trying to solve the problem in a coordinated manner. The reaction rate is noteworthy: 570 days passed between the first reports of the researchers and the official recall.
For obvious reasons, the researchers who discovered the problem did not reveal the details of the vulnerability, but something can be understood from short descriptions of the problems. In March last year, a proof-of-concept was developed for MiniMed 508 and Paradigm models, which coincide with the list released last week by the FDA. In August 2018, according to the results of the study, the manufacturer issued a warning, but at that time the problem was assessed as less serious. Two types of vulnerabilities were found: first, the data transfer between the pump and the wireless accessories (for example, a blood glucose meter ) was carried out in clear text. In this case, there was a risk of leakage of private information.
Secondly, when interacting with the control device, authorization, apparently, took place, but the complex from the controller and pump was subject to the so-called replay attack. In other words, it was possible to reproduce the sequence of data transmitted by the controller and cause, for example, reintroduction of insulin. However, as of the middle of last year, the risk of vulnerabilities was rated as “medium” (4.8 and 5.3 points by CVSS v3), since the replay attack was relevant for pump functions that were turned off by default.
')
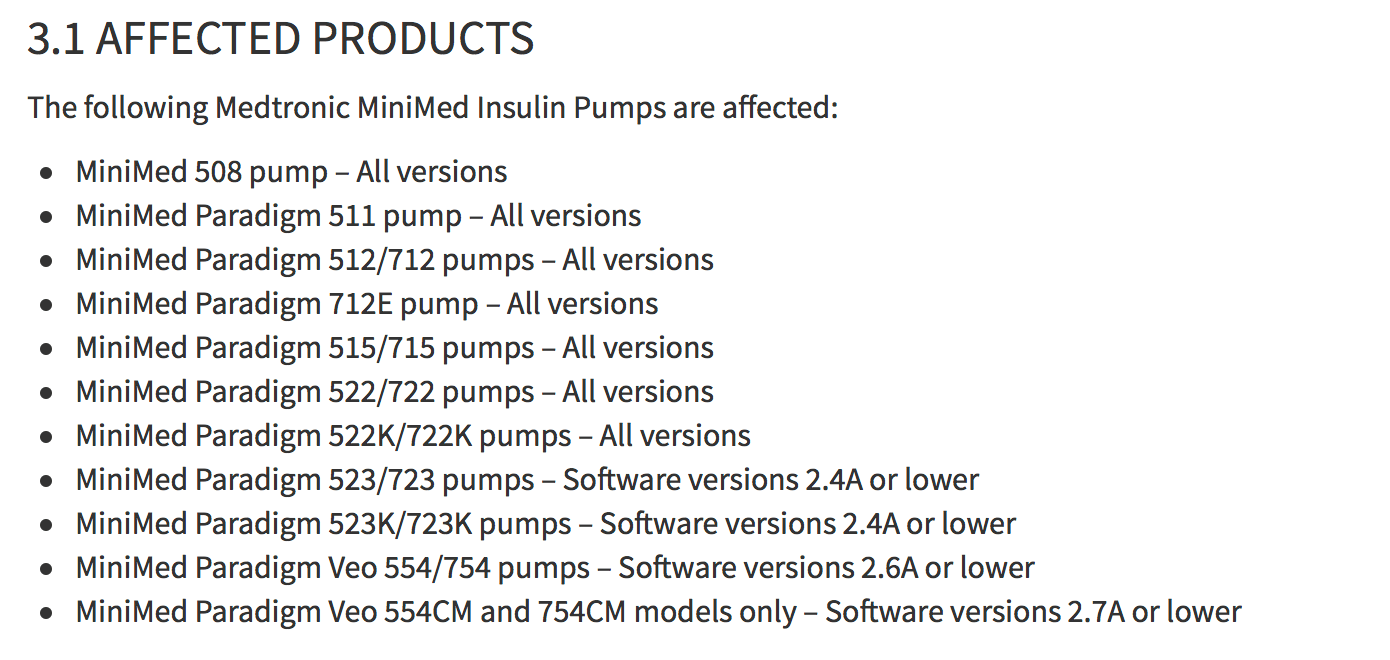
What has changed over the past year? Almost the same list of devices (in the picture above) was declared vulnerable not under certain settings, but in general in all cases. This new vulnerability ( CVE-2019-10964 ) was assigned a “dangerous” rating of 7.3 on the CVSS scale, although from the point of view of a security researcher, this could well be an “old” problem, but with new consequences. Due to the lack of a correct system for authorizing devices that interact with Medtronic pumps, not only a replay attack is possible. You can transfer arbitrary information to the pump, change settings, and generally control the insulin injection process, causing both overdose and lack of medication. Both options can be very dangerous for health.

One of the accessories mentioned in the FDA warning is the Carelink USB device. In fact, this is a wireless adapter that allows you to download information about the pump and view it in the company's software on the computer. Such medical devices make life easier for people, and wireless communication makes them even more convenient. But in this case, it was necessary to protect the data transfer as much as possible: when it comes to health, the problem is the usual data leakage, and even more so if the device, designed to improve the quality of life, begins to threaten it.
Medtronic provides a list of tips for those who are forced to use a vulnerable pump (due to the inaccessibility of safe models in the region or for some other reason). It is recommended to keep the device with you all the time, not to share its serial number with anyone (this hints at a simple authorization and / or encryption scheme by serial number, but judging by the researchers' quotes, it is not necessary to know the serial number for hacking). You also need to immediately cancel any injection, not initiated by the owner, constantly monitor the level of glucose in the blood. In addition, the CareLink USB device is recommended to disconnect from the computer when not in use.
In short, a convenient medical device becomes a little less convenient. According to the manufacturer, there have been no cases of intentional exploitation of the vulnerability. This is good news, but they are most likely caused by a lack of motivation for cybercriminals. And what if it appears?
Another news last week was the discovery of a new attack on IoT devices with default passwords (for example, routers or IP cameras). A malicious script known as Silex, destroyed the file system of devices, making them inoperative. Apparently, for someone monetary motivation was not of interest, and the device (about 4000 suffered) was rendered simply out of love for art. The loss of the Internet and the disruption of the local network is a serious problem, but such an attack on a vital IoT in medicine is much worse.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/458408/
All Articles