UserGate Platform Overview
Hello!
We continue the series of articles on the subject of integrated IT integration.
And today we want to talk about one of the domestic developments that we as integrators can offer our customers to solve the problem of ensuring the perimeter security of the network. This is especially relevant in terms of sectional policies and import substitution requirements.
')
The introduction of sanctions has become a challenge, including for engineers who have received certification, a huge knowledge base on the decisions of foreign vendors, but at some point they were forced to quickly restructure themselves to the “new wave”, in fact, starting a lot.
Domestic developers also had to reach a new level in order to offer a worthy alternative to the leaders of IT solutions as soon as possible. Now we can say that they are doing pretty well. Let us turn to a specific example, namely, the UserGate inter-network screen. Let us briefly consider what tasks it allows us to solve, and what potential it has for development.
So let's talk about what UserGate offers from the functional, and in what areas it can be applied.
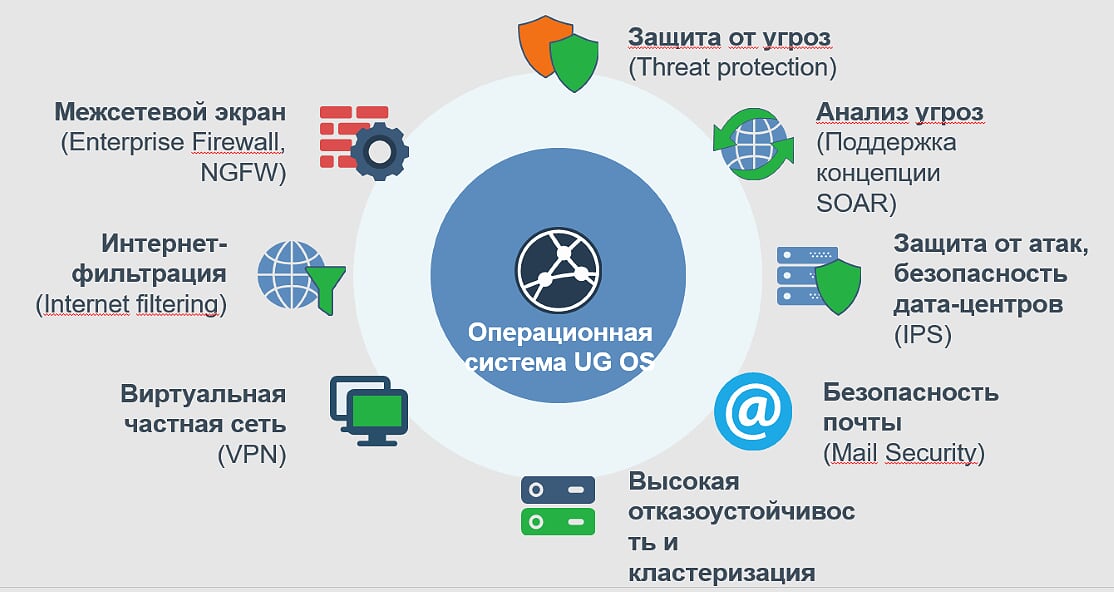
Figure 1 - UserGate Firewall Functionality

Figure 2 - Applications of UserGate firewalls
Developers paid a lot of time to creating their own platform, which does not rely on the use of someone else's source code and third-party modules. UserGate works on the basis of a specially created and constantly supported and developing UG OS operating system.
In essence, UserGate is a universal Internet gateway of the Unified Threat Management class (unified threat protection), combining the functionality of a firewall, router, gateway antivirus, intrusion detection and prevention system (VOA), VPN server, content filtering system, monitoring module and statistics and more. The product allows you to manage the company's network, optimize the traffic it uses and effectively prevent Internet threats.
Let us consider in more detail what UserGate has to offer in terms of network security functionality and protection against network threats.
UserGate’s next generation firewall (Next Generation Firewall (NGFW)) filters traffic passing through certain protocols (for example, TCP, UDP, IP), thereby protecting the network from hacker attacks and various types of intrusions based on the use of these protocols.
Intrusion Detection and Prevention System (SOW) allows you to recognize malicious activity within a network. The main task of the system is the detection, logging and prevention of threats in real time, as well as the provision of reports. The administrator can create various COW profiles (sets of signatures relevant to the protection of certain services) and set the PSB rules that define actions for the selected type of traffic that will be checked by the PSB module in accordance with the assigned profiles.
UserGate Streaming Antivirus allows you to provide anti-virus scanning of traffic without sacrificing network performance and speed. According to the vendor, the module uses an extensive database of signatures, which is constantly updated. As an additional protection, you can connect the heuristic analysis module.
UserGate is capable of processing transit mail traffic (SMTP (S), POP3 (S)), analyzing its source, as well as the content of the letter and attachments, which guarantees reliable protection against spam, viruses, pharming and phishing attacks. UserGate also provides the ability to flexibly configure the filtering of mail traffic by user groups.
It is possible to transfer HTTP / HTTPS and email traffic (SMTP, POP3) to external ICAP servers, for example, for anti-virus scanning or for analyzing data transmitted by users of DLP systems. The administrator can specify which traffic is required to send to ICAP, as well as configure work with server farms.
In the new version of the platform, it became possible to set up an automated process control system (APCS) and control it. The administrator can control the traffic by setting the rules for detecting, blocking and logging events. This allows you to automate the basic operations of the process, while maintaining the possibility of control and human intervention, if necessary.
UserGate significantly reduces the time between attack detection and response to it by automating security with a scripting engine (SOAR - Security Orchestration, Automation and Response). This concept is at the peak of popularity and allows the administrator to create scenarios (launched according to plan or when an attack is detected), where automatic actions are written in response to certain events. This approach provides a flexible setting of security policies, reduces human participation by automating repetitive tasks, and also enables the prioritization of scenarios for the earliest possible response to critical threats.
Now let's see what technologies UserGate offers to provide solutions for fault tolerance and reliability.
UserGate supports 2 types of clusters: a configuration cluster that allows you to specify uniform settings for the nodes within the cluster, and a fault tolerance cluster, designed to ensure uninterrupted network operation. A failover cluster can operate in two modes: Asset Asset Asset and Asset Passive. Both support synchronization of user sessions, which ensures transparent for users switching traffic from one node to another.
The FTP over HTTP module allows you to access the contents of the FTP server from the user's browser.
When connecting the system to several providers, UserGate allows you to configure a gateway for each of them to provide access to the Internet. The administrator can also adjust the balancing of traffic between providers, specifying the weight of each gateway, or specify one of the gateways as the main one with switching to other providers in case the main gateway is unavailable.
Bandwidth management rules serve to limit the channel for specific users, hosts, services, or applications. Among other things, UserGate products have a fairly wide functionality for traffic routing and publishing local resources.
UserGate allows both static and dynamic routing. Dynamic routing is performed using OSPF and BGP protocols, which makes it possible to use UserGate in a complex routed enterprise network. The administrator can create NAT rules in the system (to provide users with access to the Internet), as well as rules for securely publishing internal resources to the Internet using reverse proxy for HTTP / HTTPS and DNAT for other protocols.
In principle, nothing innovative, but in order for the customer’s engineers to feel relatively calm, these technologies are quite enough.
If you have access to the Internet, there is the task of controlling traffic. Not so long ago, the majority of corporate clients were primarily interested in minimizing the costs of Internet access (especially for small firms) and security (this task has long been successfully solved by all sorts of antivirus software). Today, more and more attention is paid to how employees use the Web and how to ensure that their actions do not threaten the security of business critical services.
The use of the Internet filtering module provides administrative control over the use of the Internet and blocking visits to potentially dangerous resources, as well as, when necessary, non-work related sites. To analyze the security of resources requested by users, reputation services, MIME content types (photos, videos, texts, etc.), special morphological dictionaries provided by UserGate, as well as black and white URL lists are used. Using Useragent, an administrator can disable or allow work with a certain type of browsers. UserGate provides the ability to create your own black and white lists, dictionaries, MIME types, morphological dictionaries and Useragent, applying them to users and groups of users. Even secure sites may contain unwanted images on banners, the content of which does not depend on the owner of the resource. UserGate solves this problem by blocking banners, protecting users from negative content. UserGate has, in our, a very interesting function of injecting code onto web pages. It allows you to insert the necessary code into all web pages that the user views. Further, the administrator can receive various metrics for each page element and, if necessary, hide various elements from displaying on web pages.
With the help of MITM technology (Man In The Middle), it is possible to filter not only normal, but also encrypted traffic (HTTPS, SMTPS, POP3S protocols), signing with a trusted root certificate for encryption after analysis. The system allows you to set up a selective test of traffic, for example, do not decrypt the resources of the “Finance” category.
UserGate helps to forcibly activate a secure search feature for Google, Yandex, Yahoo, Bing, Rambler, Ask and YouTube. With this protection, it is possible to achieve high efficiency, for example, when filtering responses to requests by graphic or video content. You can also block search engines that do not implement the secure search function. In addition, administrators have the tools to block games and applications in the most popular social networks, despite the fact that access to social networks themselves can be allowed.
The platform supports various user authorization mechanisms: Captive-portal, Kerberos, NTLM, and accounts can come from various sources - LDAP, Active directory, FreeIPA, TACACS +, Radius, SAML IDP. Authorization of SAML IDP, Kerberos or NTLM allows you to transparently (without asking for a user name and password) to connect Active Directory domain users. The administrator can configure security rules, channel width, firewall rules, content filtering and application control for individual users, user groups, as well as all known or unknown users. In addition, the product supports the application of security rules to users of terminal services using special agents (Terminal Services Agents), as well as the use of an authorization agent for Windows-based platforms. To ensure greater security of user accounts, it is possible to use multifactor authentication using TOTP (Time-based One Time Password Algorithm) tokens, SMS or email. The functionality of providing temporary access to the network can be useful for guest WiFi with confirmation via email or sms. At the same time, administrators can create separate security settings for each temporary client.
In this article we have tried to briefly talk about the functionality that is implemented on the UserGate firewall platform. So far, the technology of organizing virtual networks for the geo-distribution network, and secure user access to company resources, etc. have remained outside the brackets.
All these topics, including examples of configurations of various technologies, are planned in the following articles on the UserGate platform.
We continue the series of articles on the subject of integrated IT integration.
And today we want to talk about one of the domestic developments that we as integrators can offer our customers to solve the problem of ensuring the perimeter security of the network. This is especially relevant in terms of sectional policies and import substitution requirements.
')
The introduction of sanctions has become a challenge, including for engineers who have received certification, a huge knowledge base on the decisions of foreign vendors, but at some point they were forced to quickly restructure themselves to the “new wave”, in fact, starting a lot.
Domestic developers also had to reach a new level in order to offer a worthy alternative to the leaders of IT solutions as soon as possible. Now we can say that they are doing pretty well. Let us turn to a specific example, namely, the UserGate inter-network screen. Let us briefly consider what tasks it allows us to solve, and what potential it has for development.
So let's talk about what UserGate offers from the functional, and in what areas it can be applied.

Figure 1 - UserGate Firewall Functionality

Figure 2 - Applications of UserGate firewalls
Developers paid a lot of time to creating their own platform, which does not rely on the use of someone else's source code and third-party modules. UserGate works on the basis of a specially created and constantly supported and developing UG OS operating system.
In essence, UserGate is a universal Internet gateway of the Unified Threat Management class (unified threat protection), combining the functionality of a firewall, router, gateway antivirus, intrusion detection and prevention system (VOA), VPN server, content filtering system, monitoring module and statistics and more. The product allows you to manage the company's network, optimize the traffic it uses and effectively prevent Internet threats.
Let us consider in more detail what UserGate has to offer in terms of network security functionality and protection against network threats.
Firewalling
UserGate’s next generation firewall (Next Generation Firewall (NGFW)) filters traffic passing through certain protocols (for example, TCP, UDP, IP), thereby protecting the network from hacker attacks and various types of intrusions based on the use of these protocols.
Intrusion Detection and Prevention
Intrusion Detection and Prevention System (SOW) allows you to recognize malicious activity within a network. The main task of the system is the detection, logging and prevention of threats in real time, as well as the provision of reports. The administrator can create various COW profiles (sets of signatures relevant to the protection of certain services) and set the PSB rules that define actions for the selected type of traffic that will be checked by the PSB module in accordance with the assigned profiles.
Anti-virus traffic check
UserGate Streaming Antivirus allows you to provide anti-virus scanning of traffic without sacrificing network performance and speed. According to the vendor, the module uses an extensive database of signatures, which is constantly updated. As an additional protection, you can connect the heuristic analysis module.
Check email traffic
UserGate is capable of processing transit mail traffic (SMTP (S), POP3 (S)), analyzing its source, as well as the content of the letter and attachments, which guarantees reliable protection against spam, viruses, pharming and phishing attacks. UserGate also provides the ability to flexibly configure the filtering of mail traffic by user groups.
Work with external security systems
It is possible to transfer HTTP / HTTPS and email traffic (SMTP, POP3) to external ICAP servers, for example, for anti-virus scanning or for analyzing data transmitted by users of DLP systems. The administrator can specify which traffic is required to send to ICAP, as well as configure work with server farms.
ACS TP control
In the new version of the platform, it became possible to set up an automated process control system (APCS) and control it. The administrator can control the traffic by setting the rules for detecting, blocking and logging events. This allows you to automate the basic operations of the process, while maintaining the possibility of control and human intervention, if necessary.
Setting Security Policies with Scripts
UserGate significantly reduces the time between attack detection and response to it by automating security with a scripting engine (SOAR - Security Orchestration, Automation and Response). This concept is at the peak of popularity and allows the administrator to create scenarios (launched according to plan or when an attack is detected), where automatic actions are written in response to certain events. This approach provides a flexible setting of security policies, reduces human participation by automating repetitive tasks, and also enables the prioritization of scenarios for the earliest possible response to critical threats.
Now let's see what technologies UserGate offers to provide solutions for fault tolerance and reliability.
Clustering and failover support
UserGate supports 2 types of clusters: a configuration cluster that allows you to specify uniform settings for the nodes within the cluster, and a fault tolerance cluster, designed to ensure uninterrupted network operation. A failover cluster can operate in two modes: Asset Asset Asset and Asset Passive. Both support synchronization of user sessions, which ensures transparent for users switching traffic from one node to another.
FTP over HTTP
The FTP over HTTP module allows you to access the contents of the FTP server from the user's browser.
Multiple Provider Support
When connecting the system to several providers, UserGate allows you to configure a gateway for each of them to provide access to the Internet. The administrator can also adjust the balancing of traffic between providers, specifying the weight of each gateway, or specify one of the gateways as the main one with switching to other providers in case the main gateway is unavailable.
Bandwidth Management
Bandwidth management rules serve to limit the channel for specific users, hosts, services, or applications. Among other things, UserGate products have a fairly wide functionality for traffic routing and publishing local resources.
UserGate allows both static and dynamic routing. Dynamic routing is performed using OSPF and BGP protocols, which makes it possible to use UserGate in a complex routed enterprise network. The administrator can create NAT rules in the system (to provide users with access to the Internet), as well as rules for securely publishing internal resources to the Internet using reverse proxy for HTTP / HTTPS and DNAT for other protocols.
In principle, nothing innovative, but in order for the customer’s engineers to feel relatively calm, these technologies are quite enough.
Traffic Management and Internet Access Control
If you have access to the Internet, there is the task of controlling traffic. Not so long ago, the majority of corporate clients were primarily interested in minimizing the costs of Internet access (especially for small firms) and security (this task has long been successfully solved by all sorts of antivirus software). Today, more and more attention is paid to how employees use the Web and how to ensure that their actions do not threaten the security of business critical services.
The use of the Internet filtering module provides administrative control over the use of the Internet and blocking visits to potentially dangerous resources, as well as, when necessary, non-work related sites. To analyze the security of resources requested by users, reputation services, MIME content types (photos, videos, texts, etc.), special morphological dictionaries provided by UserGate, as well as black and white URL lists are used. Using Useragent, an administrator can disable or allow work with a certain type of browsers. UserGate provides the ability to create your own black and white lists, dictionaries, MIME types, morphological dictionaries and Useragent, applying them to users and groups of users. Even secure sites may contain unwanted images on banners, the content of which does not depend on the owner of the resource. UserGate solves this problem by blocking banners, protecting users from negative content. UserGate has, in our, a very interesting function of injecting code onto web pages. It allows you to insert the necessary code into all web pages that the user views. Further, the administrator can receive various metrics for each page element and, if necessary, hide various elements from displaying on web pages.
With the help of MITM technology (Man In The Middle), it is possible to filter not only normal, but also encrypted traffic (HTTPS, SMTPS, POP3S protocols), signing with a trusted root certificate for encryption after analysis. The system allows you to set up a selective test of traffic, for example, do not decrypt the resources of the “Finance” category.
UserGate helps to forcibly activate a secure search feature for Google, Yandex, Yahoo, Bing, Rambler, Ask and YouTube. With this protection, it is possible to achieve high efficiency, for example, when filtering responses to requests by graphic or video content. You can also block search engines that do not implement the secure search function. In addition, administrators have the tools to block games and applications in the most popular social networks, despite the fact that access to social networks themselves can be allowed.
The platform supports various user authorization mechanisms: Captive-portal, Kerberos, NTLM, and accounts can come from various sources - LDAP, Active directory, FreeIPA, TACACS +, Radius, SAML IDP. Authorization of SAML IDP, Kerberos or NTLM allows you to transparently (without asking for a user name and password) to connect Active Directory domain users. The administrator can configure security rules, channel width, firewall rules, content filtering and application control for individual users, user groups, as well as all known or unknown users. In addition, the product supports the application of security rules to users of terminal services using special agents (Terminal Services Agents), as well as the use of an authorization agent for Windows-based platforms. To ensure greater security of user accounts, it is possible to use multifactor authentication using TOTP (Time-based One Time Password Algorithm) tokens, SMS or email. The functionality of providing temporary access to the network can be useful for guest WiFi with confirmation via email or sms. At the same time, administrators can create separate security settings for each temporary client.
Conclusion
In this article we have tried to briefly talk about the functionality that is implemented on the UserGate firewall platform. So far, the technology of organizing virtual networks for the geo-distribution network, and secure user access to company resources, etc. have remained outside the brackets.
All these topics, including examples of configurations of various technologies, are planned in the following articles on the UserGate platform.
Source: https://habr.com/ru/post/458062/
All Articles