Fingerprinting via banner ads? Now it's common
Yesterday at Stack Overflow they asked a strange question : why does loading the Stack Overflow page initiate audio content? What is the sound on a text site?
Screenshot from developer tools:
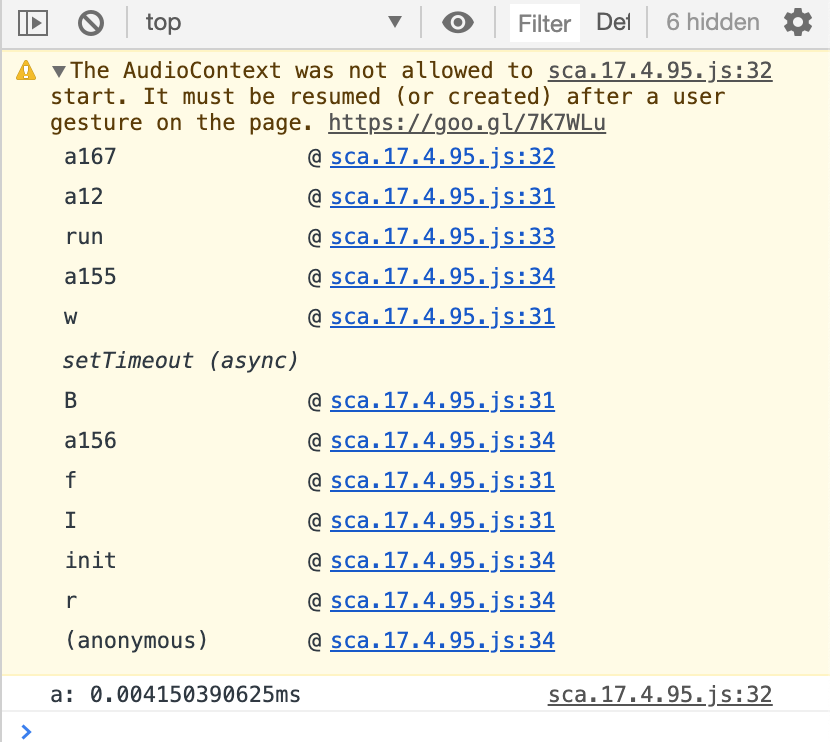
')
The answer turned out to be more interesting than it was supposed.
The author himself carefully studied the traffic and figured out that the requests are related to the script:
... and appear only if there is a certain banner ad on the page, which is delivered through the Google AdSense advertising network.

Readers at first thought it was an April Fool's joke. But one of the developers took the time and carefully figured out what exactly the above script does.
It turned out a very interesting thing. It turned out that the banner is trying to use the Audio API as one of the hundreds of pieces of data that it collects about the browser, trying to implement its fingerprinting. This is necessary to uniquely identify the browser on various sites, regardless of privacy settings. Although the browser blocks data transmission specifically via the Audio API, but it does not block most of the rest of the data, so the banner owners successfully perform fingerprinting and, possibly, de-anonymization of users.
The detected functionality is definitely not needed for the banner, that is, it is not used to enable or disable some interactive functions. They are used only in combination to create a unique “fingerprint” of the user, who then sends the banner along with the advertising ID when recording analytics for the advertiser.
For example, this fragment defines the display resolution and accessibility parameters in the system:
Check for specific cryptographic APIs:
Getting a list of installed fonts:
Identify the features of the Audio API:
Defining specific APIs in mobile browsers:
Check for DRM support for a specific platform.
And hundreds of other parameters, which together constitute a unique "portrait" of the browser. It is assigned a unique ID, which is then used to track user actions on the Internet.
It seems that the methods of fingerprinting have already gone out of the category of “dark practices” and are openly used by the largest advertisers and advertising networks. The ad blocker helps protect against such a system scan.
In such a situation, ad blocking becomes not just a convenient option, but a prerequisite for normal work on the Internet. This is the minimum but not sufficient requirement for protection against tracking.
The use of fingerprinting by advertisers has long been warned by the Electronic Frontier Foundation. The Panopticlick tool works on their website, which emulates the actions of a hostile tracker and determines how unique your browser footprint is.
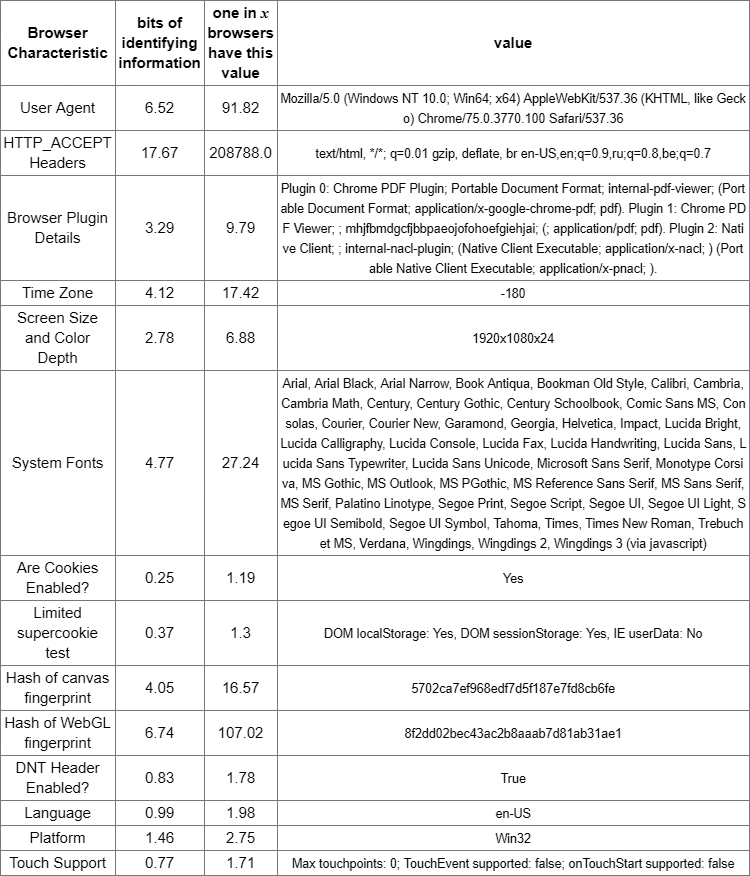
For example, the table at the top corresponds to the actual results of a browser scan, revealing 17.67 bits of identifying information. This is a unique imprint among all 208,788 users who have been tested on the site in the last 45 days.
And this is a desktop browser, and on a mobile device, fingerprinting is even easier, because scripts scan data from the phone’s sensors . Such scripts are found on many large sites on the Internet. Scanning sensors helps block bots, and is also used for tracking and analytics.
Stack Overflow representatives said they were aware of the problem. They do not like this situation and they think how to deal with it. But the fact is that banners with tracking can meet you absolutely on any site.

Screenshot from developer tools:

')
The answer turned out to be more interesting than it was supposed.
The author himself carefully studied the traffic and figured out that the requests are related to the script:
https://static.adsafeprotected.com/sca.17.4.95.js... and appear only if there is a certain banner ad on the page, which is delivered through the Google AdSense advertising network.

Readers at first thought it was an April Fool's joke. But one of the developers took the time and carefully figured out what exactly the above script does.
It turned out a very interesting thing. It turned out that the banner is trying to use the Audio API as one of the hundreds of pieces of data that it collects about the browser, trying to implement its fingerprinting. This is necessary to uniquely identify the browser on various sites, regardless of privacy settings. Although the browser blocks data transmission specifically via the Audio API, but it does not block most of the rest of the data, so the banner owners successfully perform fingerprinting and, possibly, de-anonymization of users.
The detected functionality is definitely not needed for the banner, that is, it is not used to enable or disable some interactive functions. They are used only in combination to create a unique “fingerprint” of the user, who then sends the banner along with the advertising ID when recording analytics for the advertiser.
For example, this fragment defines the display resolution and accessibility parameters in the system:
function "==typeof matchMedia&&a239.a341.a77 (" all and(min--moz - device - pixel - ratio: 0) and(min - resolution: .001 dpcm) ")},function(){return" function "==typeof matchMedia&&a239.a341.a77 (" all and(-moz - images - in -menus: 0) and(min - resolution: .001 dpcm) ")},function(){return" function "==typeof matchMedia&&a239.a341.a77 (" screen and(-ms - high - contrast: active) and(-webkit - min - device - pixel - ratio: 0), (-ms - high - contrast: none) and(-webkit - min - device - pixel - ratio: 0) ")},function(){return" function "==typeof matchMedia&&a239.a341.a77 (" screen and(-webkit - min - device - pixel - ratio: 0) ")},function(){return" Check for specific cryptographic APIs:
return "function" == typeof MSCredentials && a239.a341.a66(MSCredentials) }, function() { return "function" == typeof MSFIDOSignature && a239.a341.a66(MSFIDOSignature) }, function() { return "function" == typeof MSManipulationEvent && a239.a341.a66(MSManipulationEvent) }, function() { Getting a list of installed fonts:
return "object" == typeof document && a239.a341.a68("fonts", document.fonts) Identify the features of the Audio API:
return "undefined" != typeof window && "undefined" !== window.StereoPatternNode && a239.a341.a66(window.StereoPannerNode) Defining specific APIs in mobile browsers:
return "function" == typeof AppBannerPromptResult && a239.a341.a66(AppBannerPromptResult) Check for DRM support for a specific platform.
}, function() { return !!a239.a341.a72() && a239.a341.a66(a239.a341.a72().webkitGenerateKeyRequest) && a239.a341.a66(a239.a341.a72().webkitCancelKeyRequest) && a239.a341.a66(a239.a341.a72().webkitSetMediaKeys) && a239.a341.a66(a239.a341.a72().webkitAddKey) }, function() { And hundreds of other parameters, which together constitute a unique "portrait" of the browser. It is assigned a unique ID, which is then used to track user actions on the Internet.
It seems that the methods of fingerprinting have already gone out of the category of “dark practices” and are openly used by the largest advertisers and advertising networks. The ad blocker helps protect against such a system scan.
In such a situation, ad blocking becomes not just a convenient option, but a prerequisite for normal work on the Internet. This is the minimum but not sufficient requirement for protection against tracking.
The use of fingerprinting by advertisers has long been warned by the Electronic Frontier Foundation. The Panopticlick tool works on their website, which emulates the actions of a hostile tracker and determines how unique your browser footprint is.

For example, the table at the top corresponds to the actual results of a browser scan, revealing 17.67 bits of identifying information. This is a unique imprint among all 208,788 users who have been tested on the site in the last 45 days.
And this is a desktop browser, and on a mobile device, fingerprinting is even easier, because scripts scan data from the phone’s sensors . Such scripts are found on many large sites on the Internet. Scanning sensors helps block bots, and is also used for tracking and analytics.
Stack Overflow representatives said they were aware of the problem. They do not like this situation and they think how to deal with it. But the fact is that banners with tracking can meet you absolutely on any site.

Source: https://habr.com/ru/post/458022/
All Articles