Two-factor authentication on the site using a USB token. Now for Linux

In one of our previous articles, we talked about the importance of two-factor authentication on corporate portals of companies. Last time, we demonstrated how to set up secure authentication in the IIS web server.
In the comments we were asked to write instructions for the most common web servers for Linux - nginx and Apache.
You asked - we wrote.
What you need to start?
- Any modern Linux distribution. I did a test setup in MX Linux 18.2_x64. This is certainly not a server distribution, but for Debian there are hardly any differences. For other distributions, the paths to libraries / configs may vary slightly.
- Token. We continue to use the PKI e -signature Rutoken model, which is ideally suited for high-speed performance for corporate use.
- To work with a token in Linux, you must install the following packages:
libccid libpcsclite1 pcscd pcsc-tools opensc

Issuing certificates
In previous articles, we relied on the fact that server and client certificates will be issued using Microsoft CA. But since we are setting up everything in Linux, then at the same time we’ll tell you about an alternative way to write these certificates - without leaving Linux.
As a CA, we will use XCA ( https://hohnstaedt.de/xca/ ), which is available in any modern Linux distribution. All actions that we will perform in XCA can be done in the command line mode using the utilities OpenSSL and pkcs11-tool, but for greater simplicity and clarity in this article, we will not give them.
')
Beginning of work
- Install:
$ apt-get install xca - And run:
$ xca - Create our database for CA - /root/CA.xdb
We recommend storing the Certificate Authority database in a folder where only the administrator has access. This is important for protecting the private keys of root certificates, which are used to sign all other certificates.
Create keys and root CA certificate
The public key infrastructure (PKI) is based on a hierarchical system. Central to this system is the root certification authority or root CA. His certificate and must be created first.
- Create a private key for CA RSA-2048. To do this, on the Private Keys tab, click New Key and select the appropriate type.
- Set the name for the new key pair. I called it - CA Key.
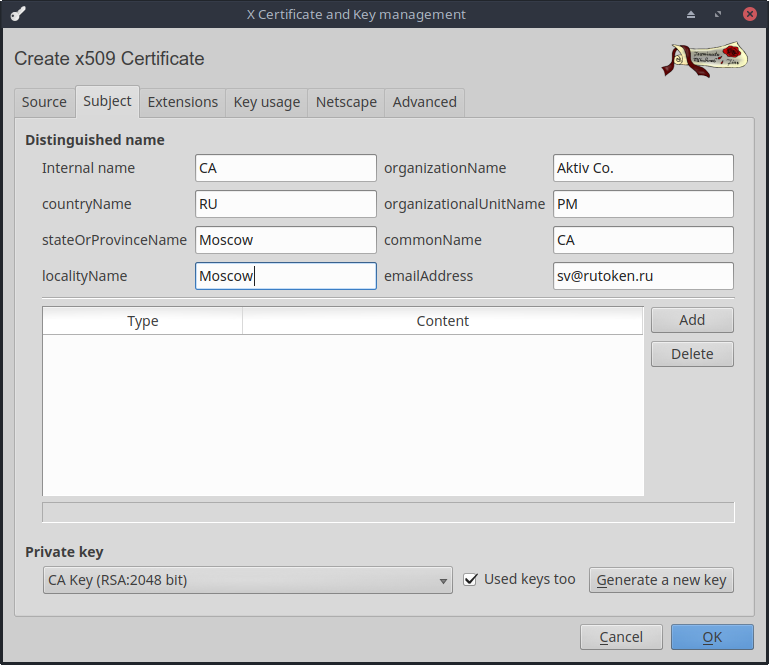
- We write out the CA certificate itself, using the created key pair. To do this, go to the Certificates tab and click New Certificate .
- Be sure to choose SHA-256 , because the use of SHA-1 can no longer be considered safe.
- As a template, be sure to select [default] CA. Do not forget to click on Apply all , otherwise the template does not apply.
- On the Subject tab, select our key pair. There you can fill in all the main fields of the certificate.
Create keys and https server certificate
- Similarly, we create the RSA-2048 private key for the server, I called it - Server Key.
- When creating a certificate, choose that the server certificate must be signed on the CA certificate.
- Do not forget to choose SHA-256 .
- As a template, select [default] HTTPS_server . Click on Apply all .
- Then on the Subject tab, select our key and fill in the required fields.

Create keys and certificate for user
- The user's private key will be stored on our token. To work with it you need to install the PKCS # 11 library from our site. For popular distributions, we distribute ready-made packages that are here - https://www.rutoken.ru/support/download/pkcs/ . We also have builds for arm64, armv7el, armv7hf, e2k, mipso32el, which can be taken in our SDK - https://www.rutoken.ru/developers/sdk/ . In addition to linux builds, there are also builds for macOS, freebsd, and android.
- Add a new PKCS # 11 Provider to the XCA. To do this, go to the Options menu on the tab PKCS # 11 Provider .
- Click Add and select the path to the PKCS # 11 library. In my case, this is \ usr \ lib \ librtpkcs11ecp.so.
- We will need a formatted token Rutoken e-signature PKI. Download rtAdmin utility - https://dev.rutoken.ru/pages/viewpage.action?pageId=7995615
- We carry out
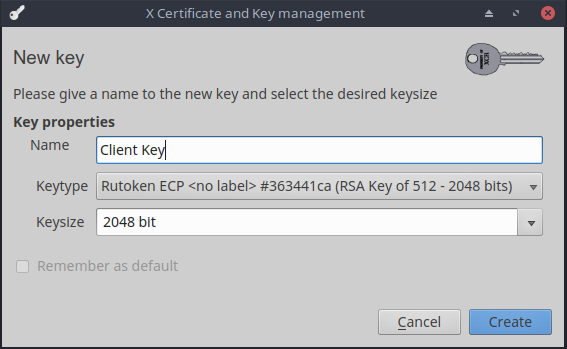
$ rtAdmin -f -q -z /usr/lib/librtpkcs11ecp.so -u <PIN- > - As the key type, select - RSA-2048 key on Rutoken EDS PKI. I called this key Client Key.
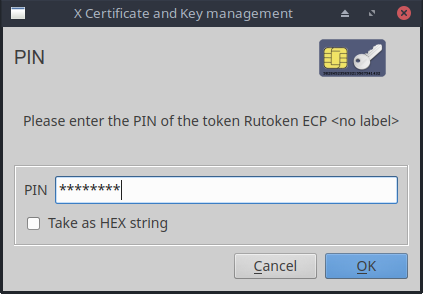
- Enter the PIN. And we are waiting for the completion of the hardware generation of the key pair.
- We create a certificate for the user by analogy with the server certificate. This time, select the [default] HTTPS_client template and do not forget to click Apply all .
- On the Subject tab enter user information. We reply affirmatively to the request for saving the token certificate.
As a result, on the Certificates tab in XCA, you should get something like this.
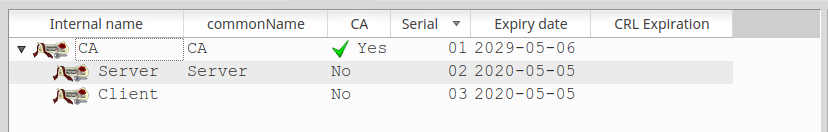
This minimum set of keys and certificates is enough to begin setting up the servers directly.
To configure, we need to export the CA certificate, server certificate and server's private key.
To do this, select the desired entry on the appropriate tab in the XCA and click Export .
Nginx
I will not write how to install and run an nginx server - there are enough articles on the Internet on this subject, not to mention official documentation. We proceed immediately to setting up HTTPS and two-factor authentication by token.
Add the following lines to the server section in nginx.conf:
server { listen 443 ssl; ssl_verify_depth 1; ssl_certificate /etc/nginx/Server.crt; ssl_certificate_key /etc/nginx/ServerKey.pem; ssl_client_certificate /etc/nginx/CA.crt; ssl_verify_client on; } A detailed description of all the parameters relating to the ssl configuration in nginx can be found here - https://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_client_certificate
I will only briefly describe those that I myself asked:
- ssl_verify_client - indicates that you need to check the certificate trust chain.
- ssl_verify_depth - determines the depth of the trusted root certificate search in the chain. Since we have a client certificate immediately signed on the root certificate, then the depth is set to 1. If the user's certificate subscribes to an intermediate CA, then 2 must be specified in this parameter, and so on.
- ssl_client_certificate - specifies the path to the trusted root certificate, which is used when checking the trust to the user's certificate.
- ssl_certificate / ssl_certificate_key - indicate the path to the server certificate / private key.
Do not forget to run nginx -t to check that there are no typos in the config, and all the files are where necessary and so on.
And actually everything! As you can see the setup is very simple.
Checking work in Firefox
Since we do everything completely in Linux, we will assume that our users also work in Linux (if they have Windows, then see the instructions for setting up browsers in the previous article .
- Launch Firefox.
- Let's try to go in at the beginning without a token. We get this picture:
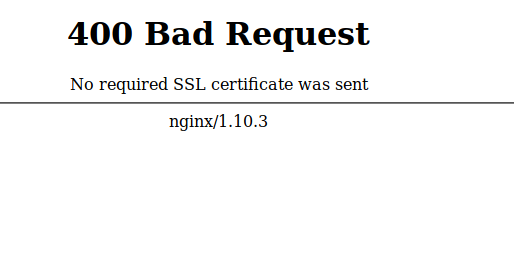
- Go to about: preferences # privacy , and go to Security Devices ...
- Click Load to add a new PKCS # 11 Device Driver and specify the path to our librtpkcs11ecp.so.
- To check that the certificate is seen, you can go to the Certificate Manager . You will be prompted to enter a PIN code. After correct input, you can verify that our certificate with a token appeared on the Your Certificates tab.
- Now we go with the token. Firefox offers to choose a certificate that will be selected on the server. Choose our certificate.

- PROFIT!

The configuration is performed once, and as seen in the certificate request window, we can save our selection. After that, at each entrance to the portal, we will only need to insert a token and enter the user's PIN-code, which was set during formatting. After such authentication, the server already knows which user logged on to it and you can no longer make any additional windows for checking, but immediately let the user into his personal account.
Apache
As with nginx, no one should have problems installing apache. If you do not know how to install this web-server, just use the official documentation.
And we start setting up our HTTPS and two-factor authentication:
- First you need to activate mod_ssl:
$ a2enmod ssl - And then enable the default HTTPS site settings:
$ a2ensite default-ssl - Now edit the configuration file: /etc/apache2/sites-enabled/default-ssl.conf:
SSLEngine on SSLProtocol all -SSLv2 SSLCertificateFile /etc/apache2/sites-enabled/Server.crt SSLCertificateKeyFile /etc/apache2/sites-enabled/ServerKey.pem SSLCACertificateFile /etc/apache2/sites-enabled/CA.crt SSLVerifyClient require SSLVerifyDepth 10
As you can see, the names of the parameters almost coincide with the names of the parameters in nginx, so I will not explain them. Again, who are interested in the details - welcome to the documentation.
Now we restart our server:$ service apache2 reload $ service apache2 restart
As you see, you can configure two-factor authentication on any web server, which is in Windows, that in Linux it is one hour maximum. And setting up browsers takes about 5 minutes. Many people believe that setting up and working with two-factor authentication is difficult and incomprehensible. I hope our article a little bit, but debunks this myth.
Source: https://habr.com/ru/post/457886/
All Articles