This is all that remains after you: the forensic artifacts of the Troldesh cipher clerk (Shade)

If you follow the news , you probably know about the new large-scale attack on the Russian companies of the Troldesh (Shade) encryption virus, one of the most popular crypto-fiber among cybercriminals. In June alone, Group-IB discovered more than 1,100 phishing emails from Troldesh, sent on behalf of employees of major airlines, car dealers and the media.
In this article, we will look at the forensic artifacts that can be found after the Shade / Troldesh attack on a compromised device’s storage media, and also compare the tactics and techniques used by the attackers with “MITER ATT & CK”.
')
The author - Oleg Skulkin , a leading specialist in computer forensics Group-IB
Troldesh, also known as Shade, XTBL, Trojan.Encoder.858, Da Vinci, No_more_ransome is a virus that encrypts files on the user's infected device and requires a ransom to restore access to information. The latest campaigns with Troldesh have shown that now it not only encrypts files, but also mines cryptocurrency and generates traffic to websites to increase traffic and income from online advertising.
For the first time, Troldesh's activity was detected by Group-IB experts back in 2015, they noticed that the virus successfully bypassed antivirus protection. The attackers regularly changed the “packer” - a packer program that reduces the file size and made it difficult to detect and reverse - because of this, antivirus programs often missed it. By the end of 2018, Troldesh became one of the most popular viruses and confidently entered the top 3, along with RTM and Pony. Experts from PaloAlto Networks reported that Troldesh works not only for Russian purposes - among the countries affected by the actions of extortionists - the United States, Japan, India, Thailand and Canada.
Initial infection vector
Typically, Troldesh / Shade is distributed through phishing emails with malicious attachments, for example, password-protected archives containing malicious .js files, after opening of which crypto-fiber is loaded and launched. What does it mean? A good idea would be to start our research by analyzing the traces of opening such archives. Where such traces can be found? Well, for example, in Jump Lists:
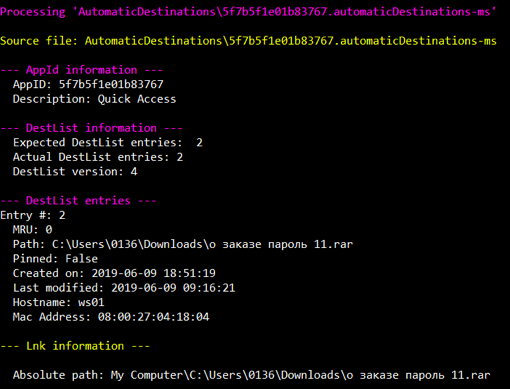
Data extracted from 5f7b5f1e01b83767.automaticDestinations-ms file using JLECmd
So, we see that the user has opened the archive with the name “about the order password 11.rar”. But how did he get into the system? The file is located in the "Downloads" directory, most likely it was downloaded from the Internet. Let's look at the history of the browser:
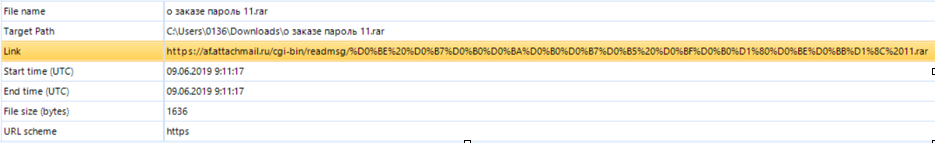
Data extracted from WebCache01.dat using Belkasoft Evidence Center
As you can see, the file was uploaded using the Microsoft Edge web browser and saved in the Downloads directory. Moreover, right before downloading, the user visited the webmail site, therefore, the archive was received via e-mail.
Thus, we are dealing with the most common technique: T1193 - “Spearphishing Attachment”.
Run and bypass security mechanisms
If we look inside the archive, we will find a JS file with almost identical name. In order for the malware to load and start working, the user must double-click on the specified file. After that, “wscript.exe” will launch a JS file that will download the malicious file from mat.tradetoolsfx [.] Com and launch it. Can we find any traces of this on the disc? Of course!
Let's look at the wscript.exe prefetch file, focusing on the files with which it interacted:
<...>
\ VOLUME {01d3dcb4976cd072-3a97874f} \ USERS \ 0136 \ APPDATA \ LOCAL \ MICROSOFT \ WINDOWS \ INETCACHE \ IE \ OEJ87644 \ 1C [1] .JPG
\ VOLUME {01d3dcb4976cd072-3a97874f} \ USERS \ 0136 \ APPDATA \ LOCAL \ TEMP \ 7ZO84024637 \ DETAILS ORDER JS
<...>
So, we have two interesting files. Firstly, now we know the name of the JS file that was in the archive, and secondly, we learned the name of the file that it downloaded. It's time to find out where it was loaded from. Let's look at WebCache01.dat again:

Data retrieved from WebCache01.dat using ESEDatabaseView
If we decode the contents of the "ResponseHeaders" field, we get the following:
HTTP / 1.1 200 OK
Content-Type: image / jpeg
Content-Length: 1300656
ETag: "5ced19b6-13d8b0"
Strict-Transport-Security: max-age = 31536000;
In fact, this is not a JPG file, but an executable file that will decrypt and run an instance of “Shade”.
So what techniques do we deal with here? Scripting (T1064), User Execution (T1204) and Masquerading (T1036).
Pinning system
“Shade” uses a rather trivial way of attaching it to the system — the registry key “Software \ Microsoft \ Windows \ CurrentVersion \ Run” (T1060). We already know that the malicious JS file was opened by the user "0136", so take a look at the corresponding file "NTUSER.DAT":
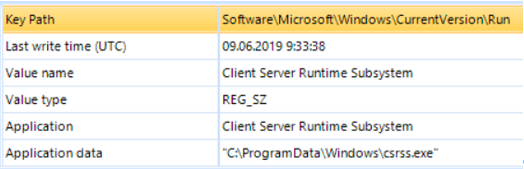
The pinning mechanism found by the Belkasoft Evidence Center
But that is not all! Further more interesting:
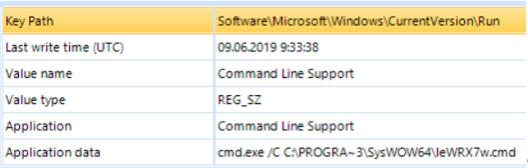
The pinning mechanism found by the Belkasoft Evidence Center
As you can see in the illustration, there is another interesting entry pointing to C: \ ProgramData \ SysWOW64 \ leWRX7w.cmd. Let's see what's inside this file:
echo CreateObject ("Wscript.Shell"). Run "" ^ & WScript.Arguments (0) ^ & "", 0, False> "% TEMP% / pxNXSB.vbs" && start / WAIT wscript.exe "% TEMP% /pxNXSB. TEMP% \ pxNXSB.vbs "
So, we have another file. Judging by its content, it is used by attackers for the extraction of cryptocurrency “ZCash”. Thus, even if the victim pays a ransom, the resources of her system will still be used by intruders.
Effects
First of all, “Shade” is a crypto-fiber, so the first thing that catches your eye is the set of files with the extension “CRYPTED000007”, the files “Read Me”, and also “fresh” wallpapers on your desktop:
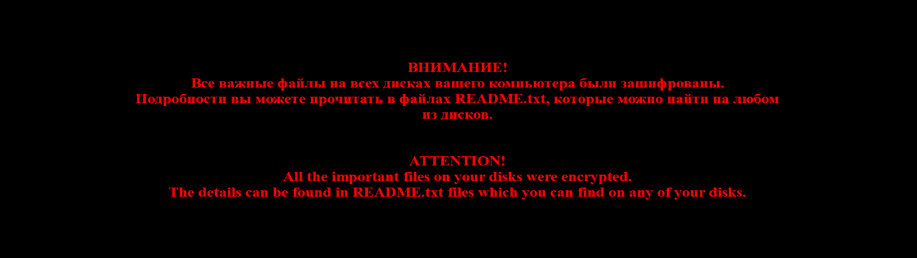
A file with this image can be found in the directory C: \ Users \% username% \ AppData \ Roaming. What equipment are we dealing with? Data Encrypted for Impact (T1486).
But, as you already understood, “Shade” is not an ordinary crypto-fiber. In addition to the crypto-fiber itself, we also discovered a miner, which means that it is worth mentioning another technique - “Resource Hijacking”.
MITER ATT & CK
Our analysis revealed a number of tactics and techniques of distributors «Shade», let's summarize:
| ID | Name | Description |
|---|---|---|
| T1193 | Spearphishing Attachment | Shade is distributed via phishing emails with malicious attachments. |
| T1204 | User Execution | The JS file from the archive attached to the email must be run by the user. |
| T1064 | Scripting | Attackers use JS files to download malware |
| T1036 | Masquerading | Downloaded malicious files have the extension "JPG" instead of "EXE" |
| T1060 | Registry Run Keys / Startup Folder | “Shade” uses the “Software \ Microsoft \ Windows \ CurrentVersion \ Run” registry key to pin it to the system. |
| T1486 | Data Encrypted for Impact | Shade encrypts files for ransom |
| T1496 | Resource hijacking | “Shade” uses the victim’s computer resources for cryptocurrency mining |
Source: https://habr.com/ru/post/457592/
All Articles