Project Salmon: how to effectively counter Internet censorship using a proxy with levels of trust to users
The governments of many countries in one way or another limit the access of citizens to information and services on the Internet. Fighting such censorship is an important and difficult task. Usually simple solutions can not boast of high reliability or long-term efficiency. More sophisticated methods of overcoming blockages have disadvantages in terms of ease of use, low productivity or do not allow to maintain the quality of Internet use at the proper level.
A group of American scientists from the University of Illinois has developed a new method of overcoming blocking, which is based on the use of proxy technology, as well as segmentation of users by the level of trust for the effective identification of agents working for censors. We present to your attention the main points of this work.
')
Description of the approach
Scientists have developed a tool Salmon - a system of proxy servers, managed by volunteers from countries without restrictions on the use of the Internet. In order to protect these servers from blocking by censors, the system uses a special algorithm for assigning users a level of trust.
The method involves exposing potential agents of censors, which are represented by ordinary users, to find out the IP address of the proxy server and block it. In addition, the Sibyl attacks are counteracted using the requirements to provide a link to a valid account on the social network when registering in the system or to receive a recommendation from a user with a high level of trust.
How it works
It is assumed that the censor is a state-controlled body that has the ability to take control of any router inside the country. It is also assumed that the task of the censor is to block access to certain resources, and not to calculate users for further arrests. The system cannot prevent such a development of events in any way - the state has plenty of opportunities to learn about the services citizens use. One of them is the use of honeypot servers to intercept communications.
It is also assumed that the state has significant resources, including human. Censor can solve problems for which hundreds and thousands of full-time employees are required.
Some more basic theses:
- The task of the system is to enable the bypass of locks (that is, provide the IP address of the proxy server) to all users living in regions with online censorship.
- Agents / employees of Internet censoring agencies and departments may try to connect to the system under the guise of ordinary users.
- The censor can block any proxy server whose address it becomes known to it.
- In this case, the organizers of the Salmon system understand that the censor somehow learned the server address.
All this brings us to the description of the three key components of the blocking system.
- The system calculates the probability that the user is an agent of censoring organizations. Users who are recognized as such agents with a high probability are banned.
- Each user has a level of trust that needs to be earned. The highest-speed proxy servers are dedicated to users with the highest levels of trust. In addition, it allows you to separate reliable, time-tested users from beginners, because it is among them most likely to be agents of censors.
- Users with a high level of trust can invite new users to the system. The result is a social graph of reliable users.
Everything is logical: the censor usually needs to block the proxy server here and now, he will not wait for a long time to try to “pump” the accounts of his agents in the system. In addition, it is clear that new users may initially receive different levels of trust - for example, friends and relatives of project creators are less likely to cooperate with censor states.
Levels of trust: implementation details
The level of trust is not only among users, but also among proxy servers. The system assigns a server with the same level of trust to a user with a certain level. At the same time, the level of user confidence can either increase or decrease, and in the case of servers it only grows.
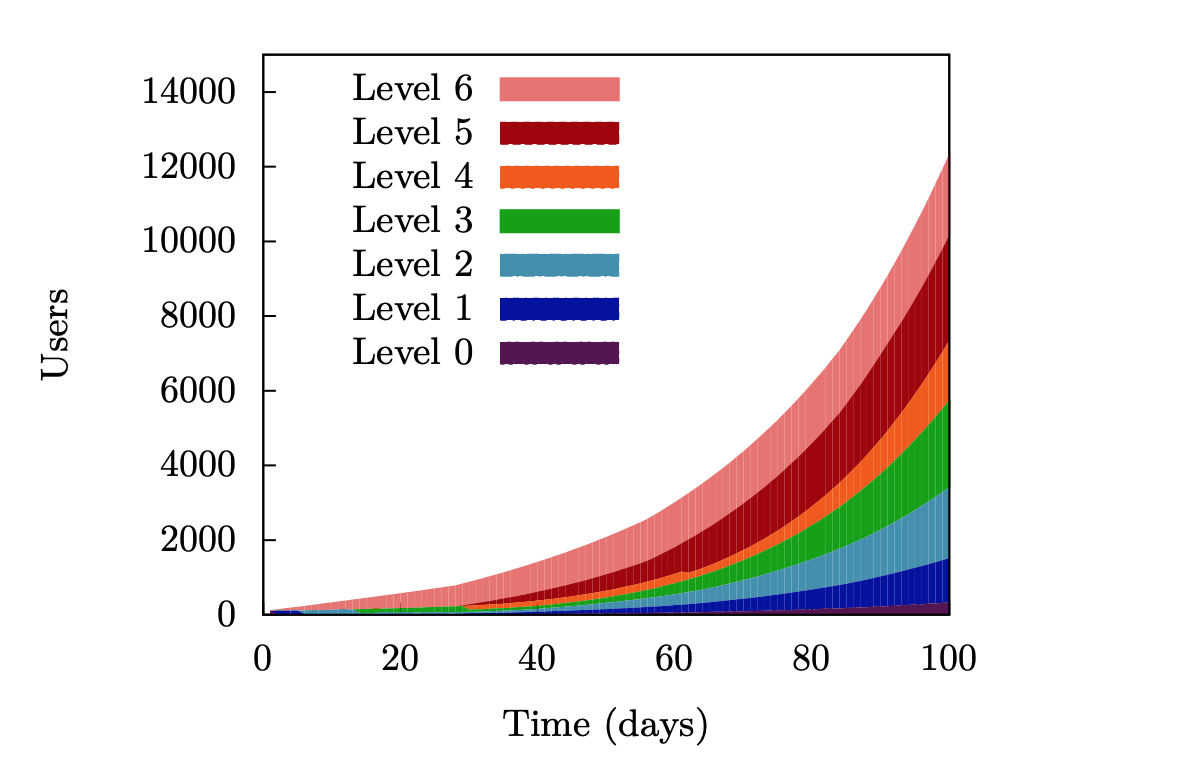
Every time when the censors block the server with which a particular user worked, his level of trust decreases. Confidence increases if the server is not blocked for a long time - with each new level the required time is doubled: to go from level n to n + 1, you need 2 n + 1 days of uninterrupted proxy server operation. The path to the maximum, sixth level of trust takes more than two months.

The need to wait so long to find out the addresses of the highest quality proxy servers is an extremely effective measure to counter the censors.
Server trust level is the minimum level of trust assigned to it by users. For example, if a new server in the system is assigned to users, among which there is a minimum rating of 2, then a proxy will receive the same one. If then the server will be used by a person with a rating of 3, but users from the second level will remain, then the server's rating will be 2. If all users of the server have upgraded, then it is upgraded for a proxy. At the same time, the server cannot lose the level of trust; on the contrary, if it is blocked, then users will be fined.
Users with a high level of trust receive two types of rewards. First, the servers are not the same. There are minimum bandwidth requirements (100 Kbit / s), but the server volunteer owner can offer and more - there is no upper limit. The Salmon system selects the most efficient servers for users with the highest rating.
In addition, users with a high level of trust are better isolated from censor attacks, because the censor must wait for months to find out the proxy address. As a result, the probability of server blocking for people with high risk is several times lower than for those with low confidence.
In order to connect as many deserving users as possible to the best proxies, the creators of Salmon have developed a recommendation system. Highly rated (L) users can invite their friends to join the platform. Invited people receive an L-1 rating.
The recommender system works in waves. The first wave of invited users gets the opportunity to invite their friends only after about four months. Users from the second and subsequent waves must wait 2 months.
System Modules
The system consists of three components:
- Salmon client for Windows;
- a server daemon program that volunteers install (versions for Windows and Linux);
- The server is a central directory storing the database of all proxy servers and dealing with the distribution of IP addresses among users.
System Client Application Interface
In order to use the system, a person must create an account using a Facebook account.
Conclusion
At the moment, the Salmon method is not widely used, only small pilot projects for users in Iran and China are known. Despite the fact that this is an interesting project, it does not fully provide anonymity, protection of volunteers, and the creators themselves admit that he is subject to attacks using honeypot services. Nevertheless, the implementation of a system with levels of trust looks like an interesting experiment that can be continued.
That's all for today, thank you for your attention!
Useful links and materials from Infatica :
- Experiment: Is it possible to reduce the negative effects of DoS-attacks using a proxy
- Study: Creating a lock-resistant proxy service using game theory
- The story of the fight against censorship: how does the flash proxy method created by scientists from MIT and Stanford
- How to understand when a proxy is lying: verification of the physical locations of network proxies using an active geolocation algorithm
- How to disguise on the Internet: compare server and resident proxies
Source: https://habr.com/ru/post/457442/
All Articles