Periodic change of passwords is an outdated practice, it's time to give it up
In many IT-systems the obligatory rule of periodic change of passwords applies. This is perhaps the most hated and most useless requirement of security systems. Some users just change the number at the end as a life hack.
This practice caused a lot of inconvenience. However, people had to endure, because it was for security . Now this advice is completely irrelevant. In May 2019, even Microsoft finally removed the requirement to periodically change passwords from the basic level of security requirements for personal and server versions of Windows 10: here is the official blog statement listing the changes to Windows 10 v 1903 (note the phrase Dropping the password -expiration policies that require periodic password changes ). The rules and system policies of Windows 10 Version 1903 and Windows Server 2019 Security Baseline are included in the Microsoft Security Compliance Toolkit 1.0 .
You can show these documents to your superiors and say: times have changed. Mandatory password change - archaism, now almost officially. Even the security audit will no longer check this requirement (if it is guided by the official rules for the basic protection of Windows computers).
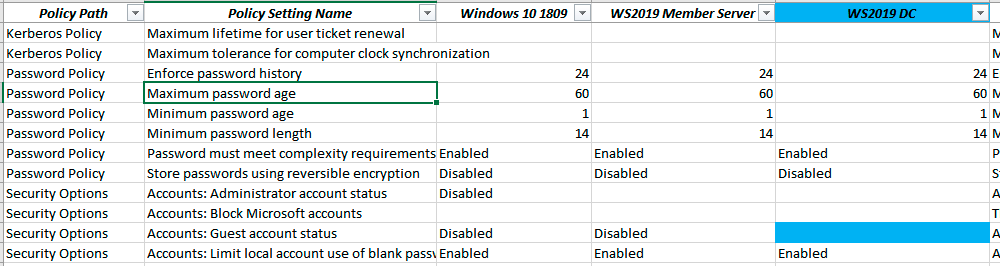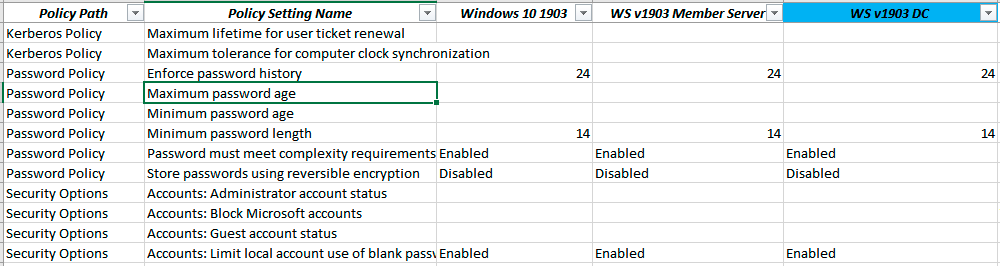
Fragment of the list with the basic security policies of Windows 10 v1809 and changes in 1903, where the corresponding policies on the time of the passwords are not applied. By the way, in the new version, the administrator and guest accounts are also canceled by default.
')
Microsoft explains popularly on a blog why it abandoned the mandatory password change rule: “Periodic expiration of a password expires only to protect against the possibility that a password (or hash) will be stolen during its validity period and will be used by an unauthorized person. If the password is not stolen, it makes no sense to change it. And if you have proof that the password has been stolen, you obviously want to act immediately rather than wait for the expiration date to fix the problem. ”
Microsoft further explains that under current conditions it is wrong to protect against password theft by this method: “If it is known that the password is likely to be stolen, how many days is an acceptable period of time to allow a thief to use this stolen password? The default is 42 days. Doesn't that seem ridiculously long? Indeed, this is a very long time, and yet our current baseline has been set to 60 days — and earlier to 90 days — because forcing a frequent expiration introduces its own problems. And if the password is not necessarily stolen, then you get these problems without good. In addition, if your users are willing to exchange a password for candy, no expiration policy will help. ”
Microsoft writes that its basic security policies are designed for use by well-managed, security-conscious enterprises. They are also intended to provide guidance for auditors. If such an organization has implemented banned password lists, multifactor authentication, detection of brute-force password attacks, and detection of abnormal login attempts, does a password need to be periodically expired? And if they have not implemented modern means of protection, will password expiration help them?
Microsoft's logic is surprisingly convincing. We have two options:
In the first case, a periodic password change does not provide additional benefits.
In the second case, a periodic password change is useless.
Thus, instead of the expiration of the password, you must first use multifactor authentication . Additional security measures are listed above: banned password lists, detection of brute-force and other abnormal login attempts.
“ Periodic password expiration is an ancient and outdated protection measure ,” sums up Microsoft, “and we do not believe that any particular value should be applied to our level of basic protection.” By removing it from our baseline, organizations can choose what best suits their perceived needs, without contradicting our recommendations. ”
If a company today forces users to periodically change passwords, what can a third-party observer think?
It turns out that the periodic change of passwords makes the company a more attractive target for attacks.

This practice caused a lot of inconvenience. However, people had to endure, because it was for security . Now this advice is completely irrelevant. In May 2019, even Microsoft finally removed the requirement to periodically change passwords from the basic level of security requirements for personal and server versions of Windows 10: here is the official blog statement listing the changes to Windows 10 v 1903 (note the phrase Dropping the password -expiration policies that require periodic password changes ). The rules and system policies of Windows 10 Version 1903 and Windows Server 2019 Security Baseline are included in the Microsoft Security Compliance Toolkit 1.0 .
You can show these documents to your superiors and say: times have changed. Mandatory password change - archaism, now almost officially. Even the security audit will no longer check this requirement (if it is guided by the official rules for the basic protection of Windows computers).

Fragment of the list with the basic security policies of Windows 10 v1809 and changes in 1903, where the corresponding policies on the time of the passwords are not applied. By the way, in the new version, the administrator and guest accounts are also canceled by default.
')
Microsoft explains popularly on a blog why it abandoned the mandatory password change rule: “Periodic expiration of a password expires only to protect against the possibility that a password (or hash) will be stolen during its validity period and will be used by an unauthorized person. If the password is not stolen, it makes no sense to change it. And if you have proof that the password has been stolen, you obviously want to act immediately rather than wait for the expiration date to fix the problem. ”
Microsoft further explains that under current conditions it is wrong to protect against password theft by this method: “If it is known that the password is likely to be stolen, how many days is an acceptable period of time to allow a thief to use this stolen password? The default is 42 days. Doesn't that seem ridiculously long? Indeed, this is a very long time, and yet our current baseline has been set to 60 days — and earlier to 90 days — because forcing a frequent expiration introduces its own problems. And if the password is not necessarily stolen, then you get these problems without good. In addition, if your users are willing to exchange a password for candy, no expiration policy will help. ”
Alternative
Microsoft writes that its basic security policies are designed for use by well-managed, security-conscious enterprises. They are also intended to provide guidance for auditors. If such an organization has implemented banned password lists, multifactor authentication, detection of brute-force password attacks, and detection of abnormal login attempts, does a password need to be periodically expired? And if they have not implemented modern means of protection, will password expiration help them?
Microsoft's logic is surprisingly convincing. We have two options:
- The company has introduced modern protection measures.
- The company has not introduced modern protection measures.
In the first case, a periodic password change does not provide additional benefits.
In the second case, a periodic password change is useless.
Thus, instead of the expiration of the password, you must first use multifactor authentication . Additional security measures are listed above: banned password lists, detection of brute-force and other abnormal login attempts.
“ Periodic password expiration is an ancient and outdated protection measure ,” sums up Microsoft, “and we do not believe that any particular value should be applied to our level of basic protection.” By removing it from our baseline, organizations can choose what best suits their perceived needs, without contradicting our recommendations. ”
Conclusion
If a company today forces users to periodically change passwords, what can a third-party observer think?
- Given: the company uses an archaic defense mechanism.
- Assumption: the company has not introduced modern protective mechanisms.
- Conclusion: these passwords are easier to get and use.
It turns out that the periodic change of passwords makes the company a more attractive target for attacks.

Source: https://habr.com/ru/post/457036/
All Articles