Extreme Networks switches with Insight architecture. Or why on the virtual machine switches
Extreme Networks' SLX, VSP and EXOS switchboards have models with a special hardware architecture under the general name “Insight”. Unlike the standard version, when the Contol and Data Plane of the switch are connected only by the PCIe bus (with all the resulting bandwidth limitations), the “Insight” switches have several Data Plane interfaces directly connected to the virtual machines that are deployed on the Control Plane. Consider how it works and what resources are utilized:
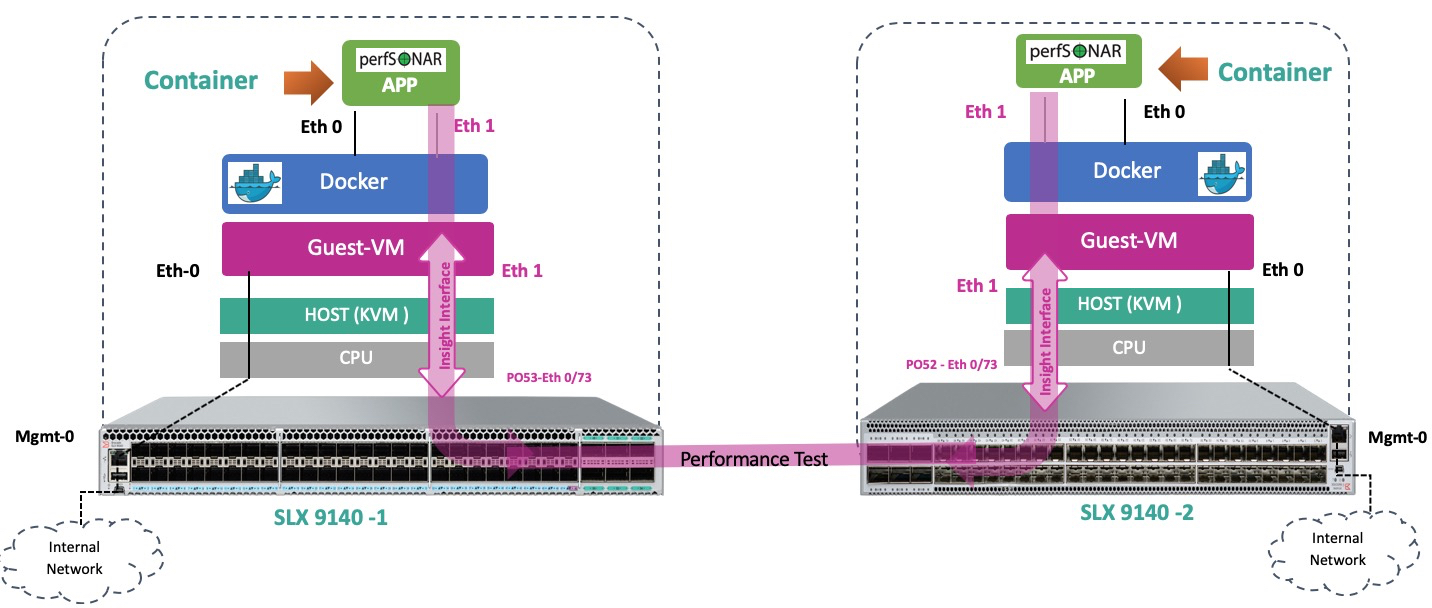
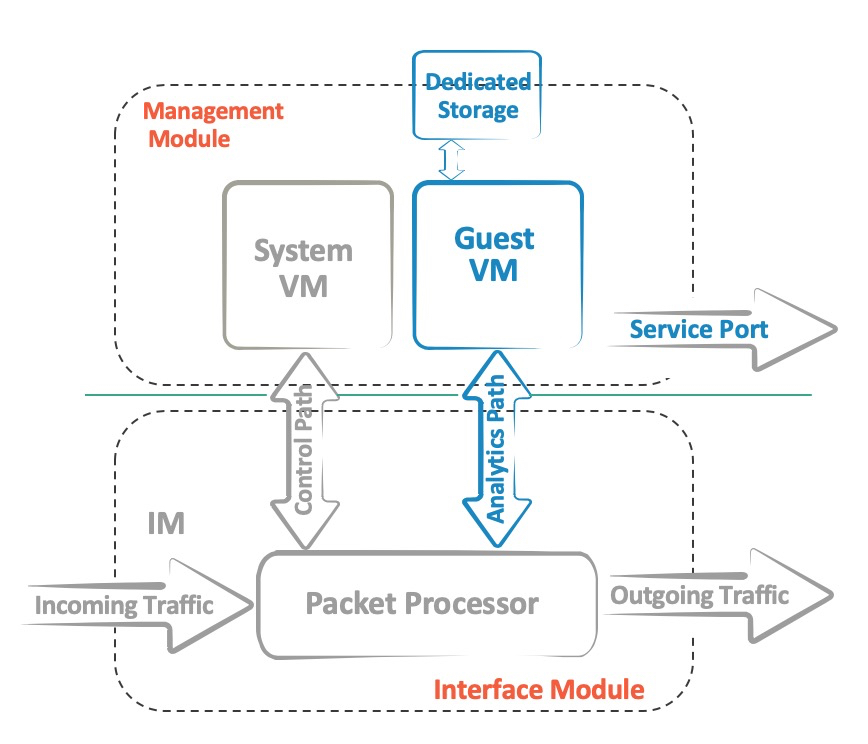
“Insight” interfaces are usually several dedicated 10GE links that are connected to the Control Plane from the ASIC via a multiplexer. There, they are mounted as ethernet interfaces of an isolated Ubuntu Linux 16.04 virtual machine, briefly called TPVM (Third Party Virtual Machine). Such a physical separation allows you to transfer large amounts of traffic with minimal latency, without causing degradation of performance neither Control nor Data Plane. The very same virtualization is based on KVM. Together, this makes it possible to run tools and services such as tcpdump, p0f, snort, distributed DPI or analytics, as well as many other services directly on the device, without deploying additional network infrastructure. To speed up the deployment of the TVPM itself, the image has many necessary packages that are preinstalled beforehand:
')
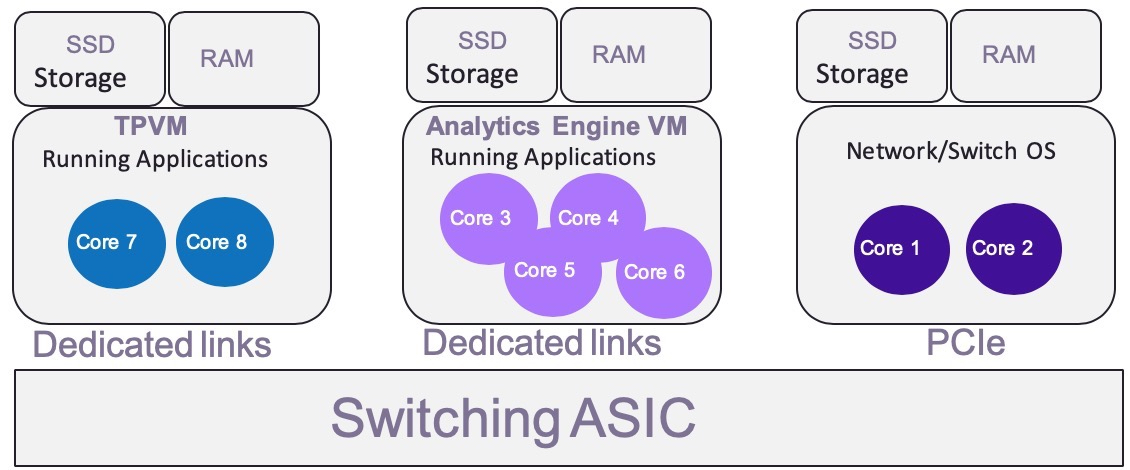
The onboard “Insight” switches are equipped with an Intel XEON x86 CPU, an increased RAM and SSD drive, which allows you to allocate resources in the event that multiple VMs are deployed. The resources themselves are allocated and isolated so as not to disrupt the OS of the switch itself.
To use TPVM for its intended purpose, you need to do only four steps:
Below is actually a small example of how it all unfolds and works. After the TPVM image has been loaded on scp2, you need to run several commands to install the VM:
When TPVM has already loaded, there are several ways to access it. By default, the VM will try to get the address via DCHP, or it can assign a link-local IPv6 address, after which you can get SSH access. There is also a console connection via TTY to TPVM.
The eth0 interface is our management, and eth1 is the “Insight” that we need to configure
By analogy with the stacking technology, the last ports on the front panel of the switch have a dual purpose and we need to transfer them to Insight mode, after which the data transfer via them will be temporarily impossible.
The system will create a 0/125 interface which we will use
Check the interfaces on the switch:
and on TPVM
Now on the “Insight” you can hang the ACL, configure the VLAN (or several) and inspect the traffic.
Further use is limited only by the requirements or imagination of the customer. Extreme Networks engineers, partners, and customers have tested many different applications such as:
If you have questions, please contact our local Extreme Networks representative .

“Insight” interfaces are usually several dedicated 10GE links that are connected to the Control Plane from the ASIC via a multiplexer. There, they are mounted as ethernet interfaces of an isolated Ubuntu Linux 16.04 virtual machine, briefly called TPVM (Third Party Virtual Machine). Such a physical separation allows you to transfer large amounts of traffic with minimal latency, without causing degradation of performance neither Control nor Data Plane. The very same virtualization is based on KVM. Together, this makes it possible to run tools and services such as tcpdump, p0f, snort, distributed DPI or analytics, as well as many other services directly on the device, without deploying additional network infrastructure. To speed up the deployment of the TVPM itself, the image has many necessary packages that are preinstalled beforehand:
- build-essential
- checkinstall
- iperf
- mtools
- netperf
- qemu-guest-agent
- tshark
- valgrind
- vim-gnome
- wireshark
- xterm

')
The onboard “Insight” switches are equipped with an Intel XEON x86 CPU, an increased RAM and SSD drive, which allows you to allocate resources in the event that multiple VMs are deployed. The resources themselves are allocated and isolated so as not to disrupt the OS of the switch itself.

To use TPVM for its intended purpose, you need to do only four steps:
- Download and install TVPM
- Configure Insight Interfaces
- Add ACL or traffic mirroring on these interfaces
- Run TPVM applications
Below is actually a small example of how it all unfolds and works. After the TPVM image has been loaded on scp2, you need to run several commands to install the VM:
slx# show tpvm status TPVM is not installed slx# tpvm install Installation starts. To check the status use 'show tpvm status' command slx# show tpvm status TPVM is being installed now When TPVM has already loaded, there are several ways to access it. By default, the VM will try to get the address via DCHP, or it can assign a link-local IPv6 address, after which you can get SSH access. There is also a console connection via TTY to TPVM.
slx# show tpvm ip-address IPv4: eth0 192.168.2.249 docker0 172.17.0.1 IPv6:2a02:0000:c000:0:da80:00ff:f00b:8800 eth0: fe80::da80:00ff:f00b:8800 slx# ssh 192.168.2.249 -l admin vrf mgmt-vrf admin@192.168.2.249's password: Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0–128-generic x86_64) Last login: Tue Apr 2 12:12:46 2019 admin@TPVM:~$ sudo -s [sudo] password for admin: root@TPVM:~# id uid=0(root) gid=0(root) groups=0(root) The eth0 interface is our management, and eth1 is the “Insight” that we need to configure
root@TPVM:~# ip -4 link 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT group default qlen 1000 link/ether d8:00:00:00:00:04 brd ff:ff:ff:ff:ff:ff 3: eth1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000 link/ether d8:00:00:00:00:02 brd ff:ff:ff:ff:ff:ff 4: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN mode DEFAULT group default link/ether 02:42:28:2d:60:b9 brd ff:ff:ff:ff:ff:ff By analogy with the stacking technology, the last ports on the front panel of the switch have a dual purpose and we need to transfer them to Insight mode, after which the data transfer via them will be temporarily impossible.
slx# conf t slx(config)# hardware slx(config-hardware)#connector 0/48 slx(config-connector-0/48)# no breakout slx(config-connector-0/48)# insight mode The system will create a 0/125 interface which we will use
slx(config)# interface Port-channel 22 slx(config-Port-channel-22)# insight enable slx(config-Port-channel-22)# no shutdown slx(config)# interface Ethernet 0/125 slx(conf-if-eth-0/125)# channel-group 22 mode on type standard slx(conf-if-eth-0/125)# no shutdown Check the interfaces on the switch:
slx(conf-if-eth-0/125)# do show interface ethernet 0/125 Ethernet 0/125 is up, line protocol is up (connected) slx(conf-if-eth-0/125)# do show interface port-channel 22 Port-channel 22 is up, line protocol is up and on TPVM
root@TPVM:~#dmesg [ 2172.748418] ixgbe 0000:00:09.0 eth1: NIC Link is Up 10 Gbps [ 2172.748508] IPv6: eth1: link becomes ready Now on the “Insight” you can hang the ACL, configure the VLAN (or several) and inspect the traffic.
root@TPVM:~# tcpdump -i eth1 -n -v tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes 02:38:38.107923 IP6 fe80::8802 > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28 02:38:39.059939 IP6 fe80::8802 > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28 02:38:39.119922 LLDP, length 111: slx 02:38:40.120076 LLDP, length 111: slx Further use is limited only by the requirements or imagination of the customer. Extreme Networks engineers, partners, and customers have tested many different applications such as:
- VNC server
- DHCP server
- AAA server (Radius and TACACS)
- DNS server
- Ostinato - Ostinato packet crafter, network traffic generator and analyzer with GUI.
- SNMP trap receiver
- Surricata - Real time intrusion detection (IDS), inline intrusion prevention (IPS), network security monitoring (NSM) and offline PCAP processing.
- Syslog server
- Google-chrome and cURL
- Arpsponge
- Perfsonar
- Puppet
- Logstash
- Docker-Container (version supported: docker-1.13.0)
If you have questions, please contact our local Extreme Networks representative .
Source: https://habr.com/ru/post/456860/
All Articles