How did I find my first vulnerability?
Foreword
Hello. I am 20 years old. More recently, I studied at a lyceum and was preparing to enroll in a medical college, and now I am a full-service developer in an American company. In fact, I am very glad that I didn’t work out with medicine - programming was my hobby, and now I can do it all the time. Now I would like to write more likely not about success in IT. Right now I want to talk about how I read a couple of books on vulnerabilities (to protect my projects) and I managed to put this knowledge into practice.
Disclaimer
All materials, screenshots, as well as links to third-party resources are posted for educational purposes. The author is not responsible for their use by other visitors of Habr. The company was notified in advance of 48 hours of the vulnerability and received enough data to fix it.
How it all began
It was quite an ordinary day. I did a few tasks at work and made myself a cup of coffee. For one, I decided to read one article about deployments on AWS, which I once repost myself in VK (by the way, I never read the article). In the column to the right of the article, several other articles and a partner banner for the hosting provider are displayed.

')
I do not remember what exactly made me go to the site, but when I went, I noticed one interesting feature: the link leads to the registration page and one field is immediately filled in - the promotional code.
If you compare the promotional code that is in the input field and in the address bar - we will see that they are completely the same.

What can we do about it?
Trite - try to change. If the promotional code is compared with the value in the database - with a high probability we will get an error. But If you change the input, there is no request to the server and it turns out that the input is checked only when you press the registration button.
I think here it is already possible to do something more interesting: we change our promo code right in the address bar and see what happens. If they do not have a promotional code specifically for Habr, which I guessed right away,
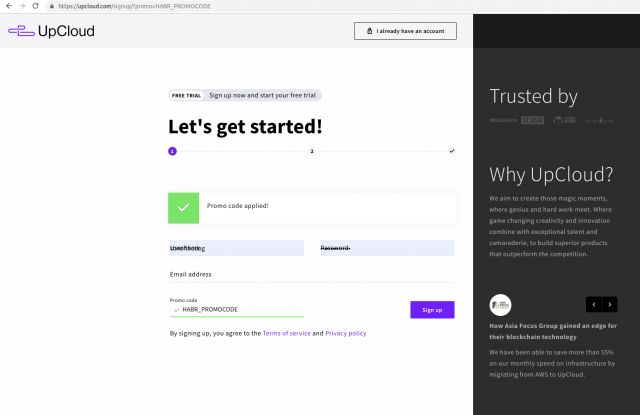
The next step is to look at the HTML code. PCM by input field -> View item code.

It is immediately clear that we are changing the value of the input field. Let's try to get out of it and add for example a link. For this we just need to change the link and we can change the page content:
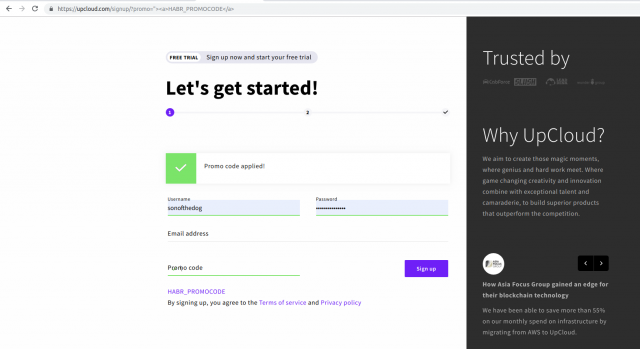
Result: we have just found an xss vulnerability on the site hosting provider.
So, what is next?
I think it is worth going deeper. Link - somehow small and not interesting. We want to tell all this to the owners of the service and, ideally, to receive a reward (the company, by the way, does not have a bug bounty, which means all this is not paid, but then I didn’t know about it yet). Let's try to place the block, zastilzovit it and insert the image. What is needed for this? all the same - change the url.
I think to describe html and css is not worth it, so I just put here what happened. Habr blocks part of the tags, others discards - I can not put the link code here.
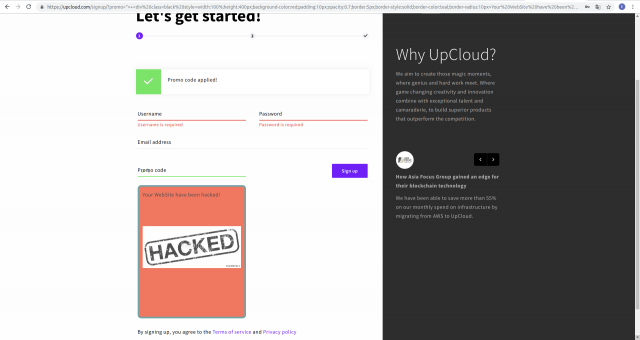
I'll post a link here. I do not know if it works at the moment, but it worked when laying out the post. To whom it is necessary - will pull out the link and parsit.
Reward
Do not think that upCloud completely refused to pay. Instead, they offered their services for free. But I refused this type of payment, because I’m not interested in renting a server now.
How can I exploit this vulnerability?
Everything is simple: you can start with collecting data from all new users, and finish with phishing sites and use someone else’s hosting as your own. You can replace all links on the page with your own or replace the form with users. It is enough to send them as referrals. And of course, you can substitute the request to the server from the form so that it does not check the promotional code (when registering, the promotional code is checked and the client returns an error with an error, but this is all solved by switching on).
What the developers forgot to do:
It's simple - validate user input. SQL-Inj does not work there - the service hangs on WordPress, and it, in turn, processes incoming lines.
Therefore, we can:
- Check the promo code with the base when rendering the page
It is slow and not justified. It is not worth the additional load on the base, and there is no point in this if it is checked all the same during registration. - Run through the regular entrance code
/ [A-Z0-9] / g - enough to validate values and protect against vulnerability. And it works faster than a request to the database, and the effect is not worse - XSS is removed.
Conclusion
The owners of the service were notified 48 hours + 2 days before that, I had been negotiating via email and LinkedIn with those who are at least somehow involved in the development. All the conversations came to: "Please tell us how you did it, but we, of course, will not pay for the vulnerabilities." I also add that in the same way the site accepts third-party js-scripts: both through a third-party source and by direct writing the code, however, in the second case, Google Chrome automatically detects xss and renders the error page instead of the service page.
I hope each programmer will validate all input data and will not forget about querystring. And I am also sure that the article was to help someone notice in advance + fix this problem in their country.
Thank you very much for your attention.
Source: https://habr.com/ru/post/456180/
All Articles