Electron application notarization procedure for macOS 10.14.5
With the release of macOS 10.14.5, Apple added the mandatory Notarization process for applications before distributing them. What is this and what difficulties have arisen with this update when developing on Electron.js I would like to tell you.

Introduction
2 years after the Electron.js boom, all the hot holivars about how bad he is and why they are needed are silenced. Let's not rekindle them again in the comments. Thank.
On our project, electron-builder is used to build the application, but for electron-packager this procedure will be approximately the same.
The project itself is a cloud gaming launcher through which a native client is launched to access a remote computer.
Signing an application with the electron-builder does not look complicated, but for the sake of completeness, I will briefly describe this procedure. If you have no problem signing the application, you can skip this chapter.
Signing application
To sign the application, we need to export certificates from the Apple developer account. We will need:
- Developer ID Application
- Developer ID Installer
- * 3rd Party Mac Developer Application and 3rd Party Mac Developer Installer (If you plan to publish the application in the AppStore)
The Developer ID Installer certificate is issued for a specific application, this requires the bundleID. For electron-builder, it is set by the "appId" parameter in package.json
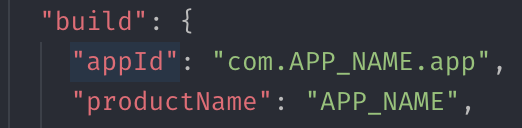
Certificates need to be collected in a single file. To do this, add them to the keychain (2 clicks on the certificate).
Then go to keychain, select the necessary certificates and in the context menu click "export items". After export, we get one file with the extension .p12.
After receiving the certificate file, add the following entries to the environment variables
- CSC_LINK (path to the .p12 certificate file)
- CSC_KEY_PASSWORD (certificate access password)
If you do not add these variables, the collector will automatically search for the appropriate keys in the keychain repository. Adding these records allows you to pinpoint the certificates you want to use for signing.
After these operations, you can start the build process and everything should go smoothly.
Smoothly this worked until the release of macOS 10.14.5 ....
What has changed with the release of macOS 10.14.5
A small digression. Performing the last work on the new patch at night, I decided to leave the build production version for the morning. Noticing that the update came on macOS launched it and went to sleep.
The next morning, I was surprised to see that the build falls from an unfamiliar error at the time of signing the application - "Unnotarized Developer ID".
Do not postpone for tomorrow what you can do today. Benjamin Franklin
The essence of the problem
Starting with macOS 10.14.5, Apple introduced a mandatory notarization procedure. Apple’s first article on this was in 2018, but it was with this update that this procedure became mandatory. How she looks like.
You build the application -> send it to the Apple server -> Apple assures it -> Returns the status of a successful assurance -> The command for setting the assurance stamp is executed.
For developers on Xcode, you just need to tick the notary
The process of notarizing the collected application can also be performed by a command in the terminal.
$ xcrun altool --notarize-app --primary-bundle-id "com.example.ote.zip" --username "AC_USERNAME" --password "@keychain:AC_PASSWORD" --file OvernightTextEditor_11.6.8.zip - primary-bundle-id - application bundleID
- username - username on developer.apple.com
- password - "app-specific password". It can be created in your account appleid.apple.com under the account of the developer.
If you do not perform the procedure of notarization, then when the user tries to install the application, a window with an error flies. The gatekeeper is responsible for checking the security of the application. It was he who broke the application build on the electron-builder.

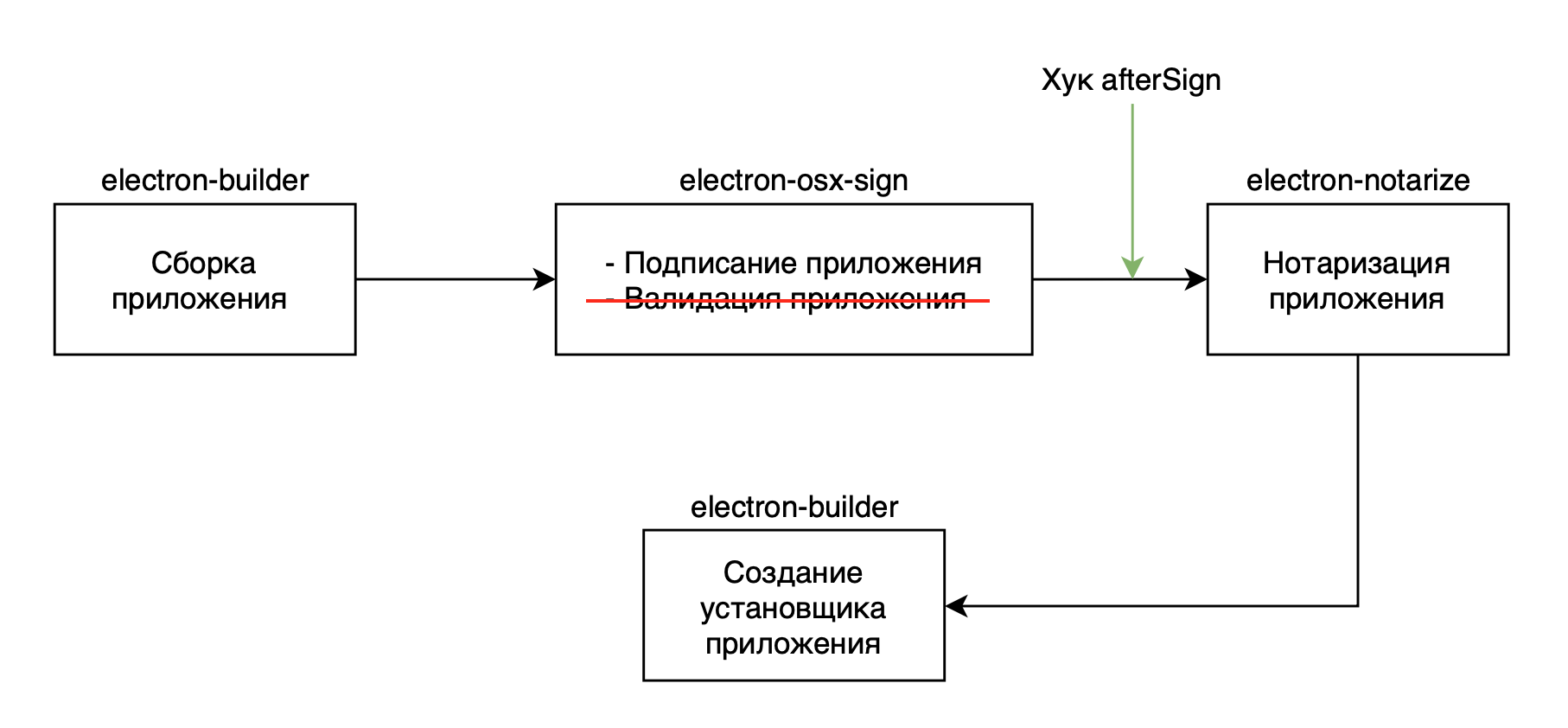
What did the build process of electron-builder look like?
After the application was assembled into the .app file, the application was signed using the electron-osx-sign utility. After signing with the certificate, the process of checking the application with the gatekepper was launched. But with the release of the update, the gatekeeper began to check the correct notarization of the application, this did not allow to successfully complete the application signing procedure.

Patch for the possibility of notarization
Github user Kallin quite quickly proposed a commit solution, with the addition of two new parameters to the settings. The first is "gatekeeperAssess" - disables assembly validation after signing and the second "sign" - which disables signing with the certificate of the installation file (dmg). This commit is included in the release of electron-builder 20.43.0.
For the very notarization process, electron-userland has an electron-notarize module that performs this task; you just need to write a small script and run it using the afterSign hook.
The process of signing and notarizing the application
Initially, you need to check that you have the electron-builder version> = 20.43.0 installed and install the electron-notarize package.
Add 2 entries to the environment variables:
- appleId - login developer.apple.com
- appleASP - "app-specific password", which can be created in the appleid.apple.com personal account.

Now we will create a notarization script that will be executed after the application is signed.
const notarize = require('electron-notarize').notarize; module.exports = async (context) => { const { electronPlatformName } = context; if (electronPlatformName === 'darwin') { try { console.log('Try notarize app'); await notarize({ appBundleId: 'APP_BUNDLE_ID', appPath: './dist/mac/APP_NAME.app', appleId: process.env.appleId, appleIdPassword: process.env.appleASP, }); console.log('Success notarize'); } catch (err) { console.log(err); } } }; We keep it in a convenient place for you.
Also for correct notarization we will need to determine access rights.
to system resources for our application. To do this, create the file build / entitlements.mac.inherit.plist
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>com.apple.security.cs.allow-jit</key> <true/> <key>com.apple.security.cs.allow-unsigned-executable-memory</key> <true/> <key>com.apple.security.cs.allow-dyld-environment-variables</key> <true/> <key>com.apple.security.cs.disable-library-validation</key> <true/> <key>com.apple.security.cs.disable-executable-page-protection</key> <true/> <key>com.apple.security.cs.debugger</key> <true/> <key>com.apple.security.automation.apple-events</key> <true/> </dict> </plist> The contents of the file in my case. There may be another configuration for you. Description of all fields .
Required for Electron.js is - com.apple.security.cs.allow-unsigned-executable-memory.
Now update the settings in package.json
In the section for macOS:

- gatekeeperAssess (disables application validation on the electron-osx-sign side)
- hardenedRuntime (allows you to create a list of permissions for security and access to system resources)
- entitlements (path to access permission file for our application)
In the general settings section of the electron-builder:

- afterSign (path to the notarial script, which will be executed after signing the application)
Run the build process. It may seem that it is slightly suspended, but transferring the file to the Apple server and waiting for a response takes some time (from 3 to 10 minutes)
The status of notarization can be viewed in the terminal by running the command:
$ xcrun altool --notarization-history 0 -u $appleId -p $appleASP
The answer will be represented by a table. The status field can be 'process', 'approved', 'invalid'

With the status 'invalid' by the request number, you can see what exactly went wrong.
$ xcrun altool --notarization-info "RequestUUID" -u $appleId
That's the whole process of signing and notarization. I hope my article will be useful to you. Thank.
Small addition
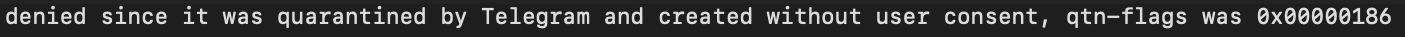
When transferring the application for testing, an interesting bug was found. The application received through Telegram simply refused to start. When viewing the logs, it was found that the application was quarantined by Telegram. For what reason and how did it happen, I could not find the answer. When you send a file through Yandex.Disk (or any other way to download via a browser), this problem does not occur.
useful links
')
Source: https://habr.com/ru/post/455874/
All Articles