CAN or not CAN? Or why do I need a network of microcontrollers?
I had to ask myself this question ten years ago or more. The work that had to be done was to donate a second life to the control panel. This is such a thing in the whole wall, consisting of light bulbs and switches with switches. I think I will not be mistaken, assuming that the shields began to be made since the light bulbs appeared, since by that time the switches were probably already known. A craving for beauty, in general, came to people from ancient times.
Now many will prefer display panels to shields. But whether display lovers will be in the majority depends on a lot of things unknown to us. But now it's not about that.
Anyone who can keep up the conversation about electrical wiring for five minutes will immediately tell me that the shield consists of flat panels on which switches and light bulbs are placed, as well as a box with many wires. After all, a light bulb without wires is only for the purpose of either breaking it or stupidly or, if you come creatively and turn on the imagination, place it near the most inquisitive in your mouth and quickly find out where the emergency room is located.
Everything was so, a bunch of wires leaving the box to the switches and light bulbs, only the light bulbs are small. Apparently, the granddaughter of the famous light bulb Ilyich.
And now, I remember, I looked out the window, and there the 21st century. So you have to do everything anew and differently. Instead of light bulbs - cost-effective LEDs. Instead of wires - wiring. Instead of one box, there are many, many small boxes, controllers, therefore.
It turned out that if each controller can service four LEDs and two switches, then it will look optimal. I mean, not so terrifying. And if the power bus and the information bus, just four wires, pass through all the controllers, a certain elegance will appear. It also turned out that 104 controllers would be required. In an amicable way, here it would be necessary to set and solve the traveling salesman problem. And then, perhaps, controllers would spend less. But it was not good.
By that time, I already knew what CAN is and the level of my respect for Bosch was much higher than that of a decent restaurant chef or neat housewife. And BMW car manufacturers, I'm sure, even went to visit Bosch engineers.
The Controller Area Network, as foreigners would say, in my opinion, as a technical solution, arose from the desire to do something, finally, well. I will not conceal that you will not feel all the delights of the results of the work of engineers as soon as you master two volumes of the standard, and much later. When you communicate with eyewitnesses, interview witnesses. Now the volumes have increased, but maybe you can immediately start from the third, since now it is called CAN_FD. However, let me continue.
Even before the collision with the shield, I had to deal with other people's engineering solutions on the use of CAN, as well as make some mistakes. Errors usually occur in the intervals between reading instructions and studying descriptions. It is good that only from the second time they look like a rake.
Now a few thousand words for the reader who is tolerant of boring and does not consider them enemies.
CAN can be installed where RS485 previously worked on twisted pair. Twisted pair is not an indispensable condition, it is just convenient to compare. Using twisted pair, via CAN, like RS485, you can send messages from the controlling controller to the slave and get a response. The similarity is striking, but let's better focus on the differences. Some of the differences may carry a minus sign for some of the readers. But I would advise them not to be upset, but to recall the law of Lomonosov.
Thanks to the synchronous organization of the protocol, resolution of collisions on the bus is implemented by hardware, on the fly, so to speak. The following points out what this leads to and what it gives the restless engineer.
You can receive a message without asking.
No need to wait until the answer is ready, you can ask someone else at this time.
The slave controller can also ask and get an answer.
Due to synchronous operation, the CAN bus length is inversely proportional to the transmission speed or the like.
The maximum speed is 1 Mbaud (10 - on the way).
The fact that the message was not corrupted during transmission, the sender knows immediately after the last bit. More precisely, everyone knows this on the bus.
If the message is corrupted for one, the attempt is not counted by all.
If the message was able to pass to the bus, the subscriber will not receive it only on the condition that it is broken.
The number of controllers on the bus should not exceed 127.
Messages are limited in length. They consist of an identifier, a length pointer in bytes and a data block with exactly as many bytes as indicated. There are a few more service bits, but let's keep silent about them, as the service should be unobtrusive. The identifier can be 11 or 29 bits. The data block can contain from 0 to 8 bytes (64 is on the way).
For specifics, here are a few numbers. If you want to work at a speed of 1Mbaud, then the length of the tire should not be more than 35 meters (some prefer 40, that is, hotter). If it is necessary to transmit something over a distance of 8 km, then the speed should not exceed 5 Kbaud. By the way, the reader is entitled to ask why the kilobod, and not the kilobit? Because not all baud become bits. Something like this.
How can you dispose of all these completely non-secret ingredients? Those who see the game of cubes in everything will immediately remember that there is such a wonderful thing as CANopen and many more beautiful combinations and abbreviations and nothing to reinvent the wheel. So I often want to answer: “Doesn’t the bicycle like two eggs that many cook for breakfast do not look like a bicycle? Why not go to a public catering and not to take an omelet? ”. But I'd rather not say anything and continue, without being distracted by shouts from the audience.
At the time when the 29-bit identifier had not yet come up with, only 11-bit existed. Some began to use it to push the name (number) of the desired type of data there. Others used as the address of the controller being accessed. Both made sense. For example, you can ask:
- And give us, my dear, chateau of the thirteenth year in a liter paper package.
Or so:
Wrap me, please, what is hidden on your bottom shelf to the right.
By the way, such a construction can also work in CAN:All lie! And you quickly fold everything from the shelves into my bag.
But you often don’t use this construction, because you’ll have to wait some time afterwards.
Wait until all the answers are lined up one by one and will not be available to the requesting controller. We have already left the cinema, if that.
In my case, I would accept an identifier variant as an address. Of the 11 bits, 7 were required, and another 4 remained to make some messages more urgent than others, and also to mark some of the controllers as main ones.
Some inconvenience migrated here from RS485, namely, the addresses had to be set manually on each controller. Then check and reinstall. And, perhaps, go back to the previous step and repeat.
Fortunately, by that time two circumstances already existed.
First, a 29 bit identifier has already appeared. And the second is that many manufacturers of microcontrollers began to consider it a good condition for each chip to have its own unique and rather long number.
Now, in the long identifier, 24 bits could be boldly allocated for a unique address. Another 5 remained, to ensure that trains differed in urgency, direction (there, back), the presence of the dining car and cars with increased comfort.
If you stop fooling around and become serious, call the subordinate controllers agents, and the rest bosses, then you can make a table. It will be shown later.
A little more about addressing. The unique number of the chip, as a rule, occupies the number of bits considerably exceeding 24, for example, 96 in STM32FXXX. Therefore, you need to somehow get 24 out of 96. I chose the XOR operation. You can choose something else, but a small problem will remain. These are address matches after reduction.
The likelihood of this problem is extremely small, but it is. It is solved, but adds work to the service men. Here we must remember that CAN messages may not contain data at all. This is what we need when deciding. It consists of the following actions.
The managing controller (boss) sends a broadcast request to which all agents must respond (this is a request with a zero address). Response messages with zero data length and matching addresses will not spoil each other, but will reach the boss as one.
Now it remains to calculate how many responses are received and how many should be. If these two numbers are the same, then everything is in order. If there are fewer answers than controllers, then there is a coincidence of addresses and service engineers have a job. And if there are more answers than controllers, then you need to think about a thesis, since you are on the verge of discovery.
If the change in the length of a message is considered as some variations of its meaning, then you can get additional features, which I will tell you later if mom does not call for food.
Even from the interesting, if you use both short and long identifiers at the same time, you can get, for example, group addressing or partially broadcast requests. But we will not go deep yet.
Let's return to coding of the identifier.
For addressing purposes, 24 bits are allocated in the extended identifier, and six in the standard one. An address with a value of 0x000000 is a broadcast for the extended identifier. For a standard identifier, a zero address (6 bits) is also considered a broadcast. The five leading (most significant) bits in the long and short identifier, called the header, affect the meaning of the message and are denoted by the letters NVADR:
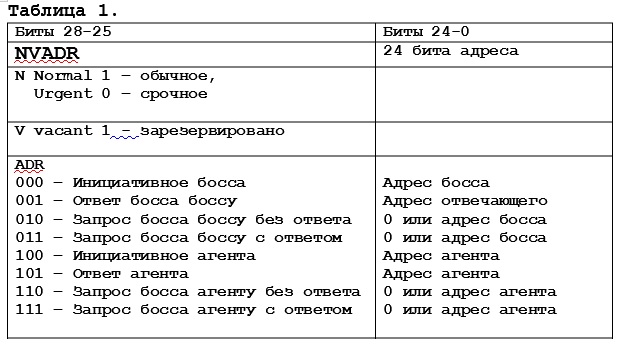
Of course, for the dispatch board it was necessary to implement only a part of this scheme. In the first project with a shield (or on a shield, how correctly?), Cortex chips from NXP were used, and in the following projects (there were such ones) M0 from STMicroelectronics was already used.
A few words about the use of short identifiers. Those six bits that are assigned for addressing address not the controller, but the group. At start, this group is initially zero for everyone. Next, the agents are configured, after which some or all of them become owned by their group. Now by a request to the group, we get the answers of those agents that we have collected in this group.
Now, a little about what is added, if we interpret messages with different lengths of data in different ways. For example, a query with a zero length is good at debugging, as mentioned above. A request with a length of 3 serves the space of byte variables of size 16384. A request with a length of 4 does the same, but is intended for a gateway agent that serves a second level CAN bus. This tire may consist of one or two agents, but remote for a couple of kilometers.
A query with a length of 5 and 6, similarly, is intended for a two-byte variable space of size 4194304. Two bits are not used for addressing. One bit controls write-read. Another signals an error.
Next, 7 and 8 serve four byte words. They are also 4194304.
These spaces are common to all agents. Each of them, depending on the destination, uses only a segment of the space of variables. The controller for measuring the temperature at two points is shown in the photo. This is for debugging and testing.
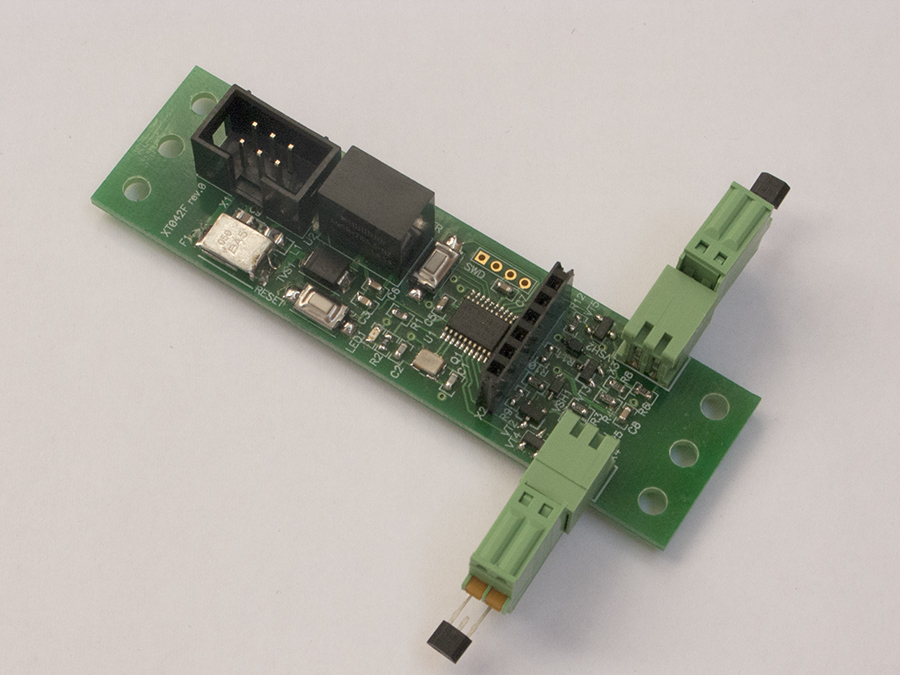
Controllers are connected by a flat cable for 6 cores. On food are doubled. The twenty-foot chip is STM32F042.
On the reverse side, there is a MAX3051, a CAN driver in the SOT23-8 package.
Well, my mother is calling for food.
')
Source: https://habr.com/ru/post/455620/
All Articles