Training Cisco 200-125 CCNA v3.0. Day 10. Modes of operation ports switch
Today we will look at switch port modes and switch functions. The switch has two modes of operation: Access, or static access, and Trunk - the mode of the tunnel highway. The first mode is used when you connect an end device to the switch port. If you connect your personal computer or laptop to the switch, its port works as an Access port. In order to set this mode, in the settings of the switch, you must use the switchport mode access command. From our video tutorials you already know that when the command line is (config-if) #, this means that the switch interface in this case is denoted as f0 / 1 or g0 / 1. Thus, we have a switch interface subcommand, and it can be used for any other port.
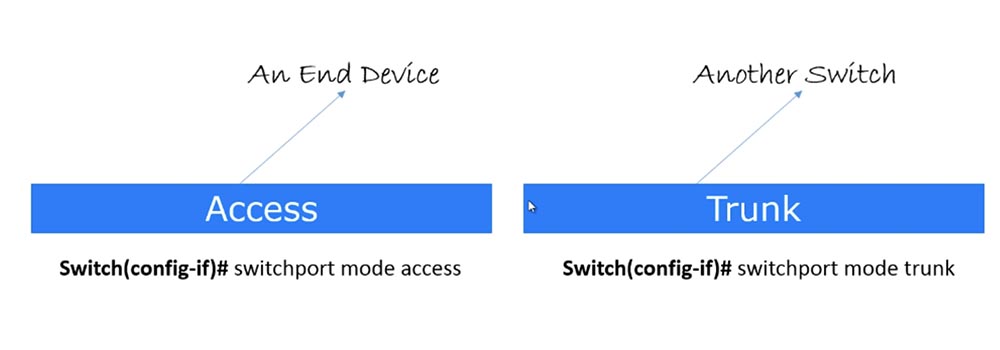
Usually, when you type the switchport mode access command, it refers to the VLAN configuration. However, at the moment you may not be worried about VLANs, rather focus on port modes. So, this mode is used to connect a specific switch port to the user's end device.
')
The second mode is known as the Trunk port, or trunk port. It is used to connect the port of one switch with another switch or router. This term was coined by Cisco, the other manufacturers of network devices call it differently. When we discuss VLAN, we will talk about the trunk mode in more detail, for now just remember that the Trunk mode is used when connecting a switch to another switch, and Access — when connecting to a terminal device. Note that we are not talking about the switch modes, but about the modes of a particular port, and any switch port can be configured for one of these modes.
To switch a port to trunk mode, you must use the switchport mode trunk command. I note that when we talk about port modes, we need to say about a special protocol for these modes, which is called the Dynamic Trunking protocol, DTP - dynamic trunking protocol. This is a proprietary protocol of Cisco, that is, it cannot be used with any other switches, except for Cisco products. There are other manufacturers of network equipment that have adopted the concept of Cisco DTP protocol, but since this series of video tutorials is focused on Cisco CCNA, we will not consider the products of other developers.
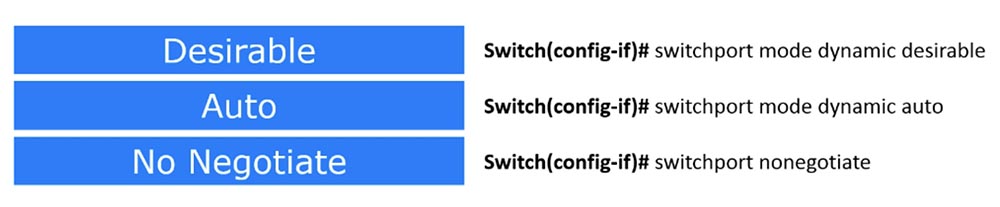
This protocol has three modes: two Dynamic Desirable and Dynamic Auto operating modes, and the third mode No Negotiate simply disables DTP.
If the port is in Dynamic Desirable mode, it immediately starts sending DTP packets, that is, becomes a trunk port. From the very name of the protocol it follows that it provides a trunk connection, and in this case, the name of the protocol mode, desirable — means that the port “wants” to become a trunk. Suppose I have a trunk port and you have Telnet, and maybe I want you to become a trunk port, but you do not want it!
But if on the other side the switch port also works in Dynamic Desirable mode, then our port operating in Dynamic Desirable mode becomes a trunk port. The same will happen if our port is working in Dynamic Auto mode, and the neighboring one - in Dynamic Desirable mode. As soon as our port receives DTP packets from it, it will immediately become a trunk port.
But if both switches are in Dynamic Auto mode, the problem arises - in this mode both switches will not do anything, because this is a passive standby mode, which does not involve any action until the port receives the DTP packet. Therefore, if both switches are in Dynamic Auto mode, no trunk trunk connection will take place.
Thus, if you want the trunk connection to be created automatically, at least one of the switches, or rather, the ports of the switch, must be in Dynamic Desirable mode.
However, keeping one of the switches constantly in a state of Dynamic Desirable is not very good. Suppose that all the switches in your organization are Dynamic Auto or Dynamic Desirable. If some bad guy intends to hack your switch and enter the system, it will be very easy for him to do it. All he needs is to get a switch, one of the ports of which is connected to your office switch, and set it to Dynamic Desirable mode. As soon as this happens, the company's switch will become a trunk and give the attacker the ability to intercept all traffic passing through it.
In trunking mode, 2 or 3 switches share the same data. This is similar to extending the capabilities of your switch - if it has 8 ports and is connected via trunk to another 8-port switch, consider that you have a 16-port switch. This is how the default trunking works, unless of course you take special measures against one switch to send its traffic to another. But usually if you organize a trunk between two 8-port switches, then you just get one 16-port switch.
If the hacker gets access to your switch and creates a trunk, the switch of the company will start sending all traffic to the attacker's switch, which can use any software to analyze the traffic of the whole organization.
To prevent such a situation, you can use the No Negotiate mode by entering the switchport command none negotiate. Therefore, be sure to use this command to disable the DTP protocol if you are not using it.
If you use the Access Switch port mode, it disables trunking. As we have said, if you need a static mode of operation, you configure Access, and if you need the Dynamic DTP mode, you use Trunk. This is the concept of using switch ports modes of operation, and I hope that you learned it.
We now turn to the consideration of the functions of communication. Basically, the switch performs three functions: Address Learning - memorizing MAC addresses; Forwarding Decision - deciding whether to send data, and Loop Avoidance, or preventing closed loops, or network loops.

Let's start with remembering addresses. We already talked about this, but since we are talking about switches, let me remind you again. As soon as the switch turns on the network, all network devices are connected to it within 30-40 seconds and they begin to “communicate”. I will say that computers love to communicate, constantly broadcasting broadcasting, saying: "Hey, here's my MAC address!". Suppose we have five network devices, and each has its own broadcast, for example, it can be ARP requests. Each time you turn on your computer, it reports its MAC address to the network. If the switch receives a broadcast message from the first device connected to port # 1, it reads its MAC address contained in this message and remembers that its first port is connected to this particular address. Based on this information, the switch creates an entry in its MAC address table. This table is sometimes called a CAM table, or associative memory table. Similarly, it comes in relation to the second, third, fourth, fifth network device - as soon as the switch receives a broadcast message with a MAC address, it immediately enters it into its table, creating the corresponding entry.
If a network device wants to contact any MAC address, the switch checks whether there is an entry about this address in its table, and on the basis of this information makes a decision on data transfer. Let's take a closer look at this process.
There are two types of data transfer decisions with a switch at the second (channel) level of the OSI model - it is Cut Through, or pass-through transfer, and Store & Forward - transfer with intermediate storage. Consider the difference between these two types of switching.

Suppose that one network device is about to communicate with another device. To do this, it sends a frame containing its MAC address, destination MAC address, and other necessary information. As soon as the switch receives this frame, it first looks at the destination MAC address, which is in the first few bytes of the frame, and immediately sends the frame to the destination port. This is what Cut Through switching is.
If the Store & Forward transfer type is used, the switch waits until it receives the entire frame. It then checks the received frame for errors that may have occurred during the transfer. If there are no errors, it sends a frame to the destination port.
Some people believe that the Cut Through mode is quite enough, others say: “No, we definitely need error checking”! This question has no definite solution, it all depends on the specific situation. If you need fast transfer and you want the switch to forward traffic as quickly as possible, you use the Cut Through switching mode. If you need more reliable, proven traffic, you use Store & Forward.
Now let's take a look at Loop Avoidance. As you remember, I have already said in one of my lessons that when a switch receives a broadcast message, it transmits it to all ports. Now I drew 2 switches and red arrows showed reception and transmission of data. Usually you connect one switch with another cable, forming a trunk. However, as the network grows, you are no longer satisfied with one cable through which data is transmitted, you want to speed up the traffic exchange process and connect devices with a second cable, creating another trunk.

Of course, you can physically disconnect one cable and leave the second, and the connection between the switches will not be interrupted, however, most network administrators prefer to use both trunks. Thus, for the connection of two switches, we have not one, but two ways, and such a connection can lead to the problem of packet loops. It occurs when there is more than one path at layer 2 of the OSI model between two endpoints, for example, when two switches have several connections to each other or two switch ports are connected to each other.
Now I will draw on the left another device - a computer. When this computer broadcasts, the switch receives traffic and forwards it to all its ports. In our case, this means that the left switch will send traffic on both the upper and lower cables that are connected to its two ports. When the right switch receives traffic over the top cable, it will send it to its second port, to which the bottom cable is connected, and this traffic will rush back to the left switch. When the traffic from the left switch reaches the right switch on the lower cable, the right switch will redirect it to its first port, and since it is a broadband transmission, it will send it on the upper cable to the left switch.

In turn, the left switch, having received traffic from the right one, will redirect it to another port and send it back, and do this for both ports to which the cables are connected. This process will be repeated to infinity, that is, between two switches, a closed loop is formed, or a closed loop of the same traffic.
Detect cycled traffic in the system is very difficult. There are no indicators that would show a traffic loop, in contrast to Layer 3 of the OSI model, where there are many mechanisms for preventing obsession. This is because, at the OSI model level 2, the headers do not support the TTL frame lifetime, and if the frame is looping, it can live forever.
In addition, the filter table of the MAC address of the switch will be confused regarding the location of the device, because the switch will receive a frame from more than one communication channel and will not be able to match it with any particular device.
The network protocol Spanning-Tree Protocol, or STP, which prevents traffic loops in the network topology, helps solve this problem. You can learn more about this protocol from the Wikipedia article, for now all you need is to familiarize yourself with its concept. The STP protocol checks if we have a redundant connection. In our case, we have 2 connections between the same switches, that is, there is redundancy. In the following video tutorials, I will tell you in detail how STP works, but now I’ll just say that it acts according to its own rules and logically disconnects the extra cable. Physically, both cables remain connected, but logically one of them is disconnected. Thus, both ports connected by the upper cable continue to exchange traffic, but one of the ports connected by the lower cable is logically disconnected.
Suppose that the connection on the upper cable for some reason was interrupted. In this case, the STP protocol immediately includes one of the ports connected by the lower cable, and data exchange continues without interruption.
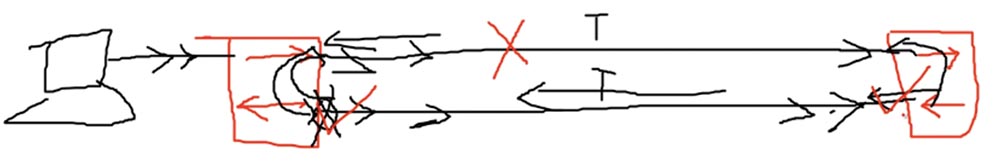
I gave you a very brief concept of how STP works: this is the mechanism that disables the redundant connection. In this slide, you can see the STP protocol analogy - a fallen tree blocked the road, and the road was “interrupted”.
In the following video tutorials we will return to many topics that were briefly covered in previous episodes. Therefore, I tell my students not to worry that we will miss something important: it's like building a building when no one starts painting the walls of the first floor until the other floors are erected. I don’t know how many video lessons will be in our course, maybe 40 or 50, because if any topic will interest you more, I will dedicate a separate lesson to it. Just believe that with my help you will master all the knowledge to obtain a CCNA certificate and even learn much more than is necessary.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

Usually, when you type the switchport mode access command, it refers to the VLAN configuration. However, at the moment you may not be worried about VLANs, rather focus on port modes. So, this mode is used to connect a specific switch port to the user's end device.
')
The second mode is known as the Trunk port, or trunk port. It is used to connect the port of one switch with another switch or router. This term was coined by Cisco, the other manufacturers of network devices call it differently. When we discuss VLAN, we will talk about the trunk mode in more detail, for now just remember that the Trunk mode is used when connecting a switch to another switch, and Access — when connecting to a terminal device. Note that we are not talking about the switch modes, but about the modes of a particular port, and any switch port can be configured for one of these modes.
To switch a port to trunk mode, you must use the switchport mode trunk command. I note that when we talk about port modes, we need to say about a special protocol for these modes, which is called the Dynamic Trunking protocol, DTP - dynamic trunking protocol. This is a proprietary protocol of Cisco, that is, it cannot be used with any other switches, except for Cisco products. There are other manufacturers of network equipment that have adopted the concept of Cisco DTP protocol, but since this series of video tutorials is focused on Cisco CCNA, we will not consider the products of other developers.

This protocol has three modes: two Dynamic Desirable and Dynamic Auto operating modes, and the third mode No Negotiate simply disables DTP.
If the port is in Dynamic Desirable mode, it immediately starts sending DTP packets, that is, becomes a trunk port. From the very name of the protocol it follows that it provides a trunk connection, and in this case, the name of the protocol mode, desirable — means that the port “wants” to become a trunk. Suppose I have a trunk port and you have Telnet, and maybe I want you to become a trunk port, but you do not want it!
But if on the other side the switch port also works in Dynamic Desirable mode, then our port operating in Dynamic Desirable mode becomes a trunk port. The same will happen if our port is working in Dynamic Auto mode, and the neighboring one - in Dynamic Desirable mode. As soon as our port receives DTP packets from it, it will immediately become a trunk port.
But if both switches are in Dynamic Auto mode, the problem arises - in this mode both switches will not do anything, because this is a passive standby mode, which does not involve any action until the port receives the DTP packet. Therefore, if both switches are in Dynamic Auto mode, no trunk trunk connection will take place.
Thus, if you want the trunk connection to be created automatically, at least one of the switches, or rather, the ports of the switch, must be in Dynamic Desirable mode.
However, keeping one of the switches constantly in a state of Dynamic Desirable is not very good. Suppose that all the switches in your organization are Dynamic Auto or Dynamic Desirable. If some bad guy intends to hack your switch and enter the system, it will be very easy for him to do it. All he needs is to get a switch, one of the ports of which is connected to your office switch, and set it to Dynamic Desirable mode. As soon as this happens, the company's switch will become a trunk and give the attacker the ability to intercept all traffic passing through it.
In trunking mode, 2 or 3 switches share the same data. This is similar to extending the capabilities of your switch - if it has 8 ports and is connected via trunk to another 8-port switch, consider that you have a 16-port switch. This is how the default trunking works, unless of course you take special measures against one switch to send its traffic to another. But usually if you organize a trunk between two 8-port switches, then you just get one 16-port switch.
If the hacker gets access to your switch and creates a trunk, the switch of the company will start sending all traffic to the attacker's switch, which can use any software to analyze the traffic of the whole organization.
To prevent such a situation, you can use the No Negotiate mode by entering the switchport command none negotiate. Therefore, be sure to use this command to disable the DTP protocol if you are not using it.
If you use the Access Switch port mode, it disables trunking. As we have said, if you need a static mode of operation, you configure Access, and if you need the Dynamic DTP mode, you use Trunk. This is the concept of using switch ports modes of operation, and I hope that you learned it.
We now turn to the consideration of the functions of communication. Basically, the switch performs three functions: Address Learning - memorizing MAC addresses; Forwarding Decision - deciding whether to send data, and Loop Avoidance, or preventing closed loops, or network loops.

Let's start with remembering addresses. We already talked about this, but since we are talking about switches, let me remind you again. As soon as the switch turns on the network, all network devices are connected to it within 30-40 seconds and they begin to “communicate”. I will say that computers love to communicate, constantly broadcasting broadcasting, saying: "Hey, here's my MAC address!". Suppose we have five network devices, and each has its own broadcast, for example, it can be ARP requests. Each time you turn on your computer, it reports its MAC address to the network. If the switch receives a broadcast message from the first device connected to port # 1, it reads its MAC address contained in this message and remembers that its first port is connected to this particular address. Based on this information, the switch creates an entry in its MAC address table. This table is sometimes called a CAM table, or associative memory table. Similarly, it comes in relation to the second, third, fourth, fifth network device - as soon as the switch receives a broadcast message with a MAC address, it immediately enters it into its table, creating the corresponding entry.
If a network device wants to contact any MAC address, the switch checks whether there is an entry about this address in its table, and on the basis of this information makes a decision on data transfer. Let's take a closer look at this process.
There are two types of data transfer decisions with a switch at the second (channel) level of the OSI model - it is Cut Through, or pass-through transfer, and Store & Forward - transfer with intermediate storage. Consider the difference between these two types of switching.

Suppose that one network device is about to communicate with another device. To do this, it sends a frame containing its MAC address, destination MAC address, and other necessary information. As soon as the switch receives this frame, it first looks at the destination MAC address, which is in the first few bytes of the frame, and immediately sends the frame to the destination port. This is what Cut Through switching is.
If the Store & Forward transfer type is used, the switch waits until it receives the entire frame. It then checks the received frame for errors that may have occurred during the transfer. If there are no errors, it sends a frame to the destination port.
Some people believe that the Cut Through mode is quite enough, others say: “No, we definitely need error checking”! This question has no definite solution, it all depends on the specific situation. If you need fast transfer and you want the switch to forward traffic as quickly as possible, you use the Cut Through switching mode. If you need more reliable, proven traffic, you use Store & Forward.
Now let's take a look at Loop Avoidance. As you remember, I have already said in one of my lessons that when a switch receives a broadcast message, it transmits it to all ports. Now I drew 2 switches and red arrows showed reception and transmission of data. Usually you connect one switch with another cable, forming a trunk. However, as the network grows, you are no longer satisfied with one cable through which data is transmitted, you want to speed up the traffic exchange process and connect devices with a second cable, creating another trunk.

Of course, you can physically disconnect one cable and leave the second, and the connection between the switches will not be interrupted, however, most network administrators prefer to use both trunks. Thus, for the connection of two switches, we have not one, but two ways, and such a connection can lead to the problem of packet loops. It occurs when there is more than one path at layer 2 of the OSI model between two endpoints, for example, when two switches have several connections to each other or two switch ports are connected to each other.
Now I will draw on the left another device - a computer. When this computer broadcasts, the switch receives traffic and forwards it to all its ports. In our case, this means that the left switch will send traffic on both the upper and lower cables that are connected to its two ports. When the right switch receives traffic over the top cable, it will send it to its second port, to which the bottom cable is connected, and this traffic will rush back to the left switch. When the traffic from the left switch reaches the right switch on the lower cable, the right switch will redirect it to its first port, and since it is a broadband transmission, it will send it on the upper cable to the left switch.

In turn, the left switch, having received traffic from the right one, will redirect it to another port and send it back, and do this for both ports to which the cables are connected. This process will be repeated to infinity, that is, between two switches, a closed loop is formed, or a closed loop of the same traffic.
Detect cycled traffic in the system is very difficult. There are no indicators that would show a traffic loop, in contrast to Layer 3 of the OSI model, where there are many mechanisms for preventing obsession. This is because, at the OSI model level 2, the headers do not support the TTL frame lifetime, and if the frame is looping, it can live forever.
In addition, the filter table of the MAC address of the switch will be confused regarding the location of the device, because the switch will receive a frame from more than one communication channel and will not be able to match it with any particular device.
The network protocol Spanning-Tree Protocol, or STP, which prevents traffic loops in the network topology, helps solve this problem. You can learn more about this protocol from the Wikipedia article, for now all you need is to familiarize yourself with its concept. The STP protocol checks if we have a redundant connection. In our case, we have 2 connections between the same switches, that is, there is redundancy. In the following video tutorials, I will tell you in detail how STP works, but now I’ll just say that it acts according to its own rules and logically disconnects the extra cable. Physically, both cables remain connected, but logically one of them is disconnected. Thus, both ports connected by the upper cable continue to exchange traffic, but one of the ports connected by the lower cable is logically disconnected.
Suppose that the connection on the upper cable for some reason was interrupted. In this case, the STP protocol immediately includes one of the ports connected by the lower cable, and data exchange continues without interruption.

I gave you a very brief concept of how STP works: this is the mechanism that disables the redundant connection. In this slide, you can see the STP protocol analogy - a fallen tree blocked the road, and the road was “interrupted”.
In the following video tutorials we will return to many topics that were briefly covered in previous episodes. Therefore, I tell my students not to worry that we will miss something important: it's like building a building when no one starts painting the walls of the first floor until the other floors are erected. I don’t know how many video lessons will be in our course, maybe 40 or 50, because if any topic will interest you more, I will dedicate a separate lesson to it. Just believe that with my help you will master all the knowledge to obtain a CCNA certificate and even learn much more than is necessary.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/455487/
All Articles