Carding and “black boxes”: how to hack ATM today
The iron boxes with money on the streets of the city can not fail to attract the attention of lovers of quick money. And if earlier purely physical methods were used to empty ATMs, now more and more skillful tricks related to computers are used. Now the most relevant of them is the “black box” with a single-board microcomputer inside. How it works, we'll talk in this article.
- The evolution of ATM carding
- The first acquaintance with the "black box"
- Analysis of ATM communications
- Where do the black boxes come from?
- “Last mile” and fake processing center

The head of the International Association of Manufacturers of ATMs (ATMIA) identified "black boxes" as the most dangerous threat to ATMs.
A typical ATM is a collection of ready-made electromechanical components placed in a single package. ATM manufacturers build their iron creations from a banknote dispenser, a card reader and other components already developed by third-party suppliers. A sort of designer LEGO for adults. The finished components are located in the ATM housing, which usually consists of two compartments: the upper compartment (“cabinet” or “service area”), and the lower compartment (safe). All electromechanical components are connected via USB and COM ports to the system unit, which in this case acts as a host. On older ATM models, you can also find connections via the SDC bus.
The evolution of ATM carding
ATMs with huge amounts inside, invariably beckon carders to themselves. At first, carders exploited only gross physical shortcomings of ATM protection - they used skimmers and shimmers to steal data from magnetic strips; fake pin-pads and pinhole cameras; and even fake ATMs.
Then, when ATMs began to be equipped with unified software that operated according to uniform standards, such as XFS (eXtensions for Financial Services), carders began attacking ATMs with computer viruses.
Among them are Trojan.Skimmer, Backdoor.Win32.Skimer, Ploutus, ATMii and other numerous named and unnamed malware that carders pitch to the ATM host either via a bootable USB flash drive or via a TCP remote control port.
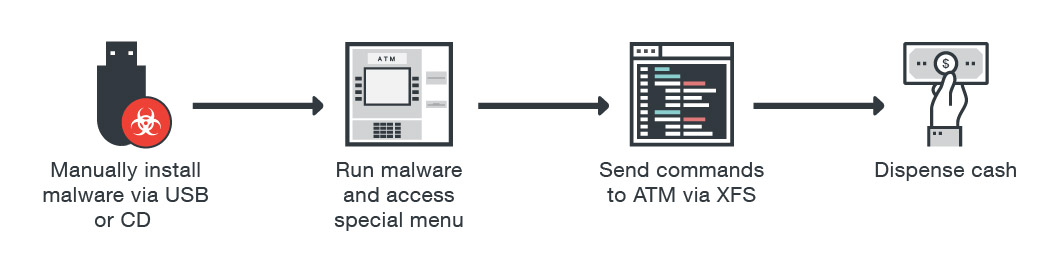
ATM infection process
Having captured the XFS subsystem, the malware can issue commands to the dispenser, without authorization. Or give commands to the card reader: read / write a magnetic stripe of a bank card and even extract transaction history stored on an EMV card chip. Special note deserves EPP (Encrypting PIN Pad; encrypted pinpad). It is considered that the pincode entered on it cannot be intercepted. However, XFS allows you to use the EPP pinpad in two modes: 1) open mode (for entering various numeric parameters, such as the amount to be cashed); 2) safe mode (EPP switches to it when you need to enter a pincode or encryption key). This XFS feature allows a card to perform a MiTM attack: intercept the safe mode activation command that is sent from the host to the EPP, and then tell the EPP pinpad that the operation should continue in open mode. In response to this message, EPP sends keystrokes in clear text.
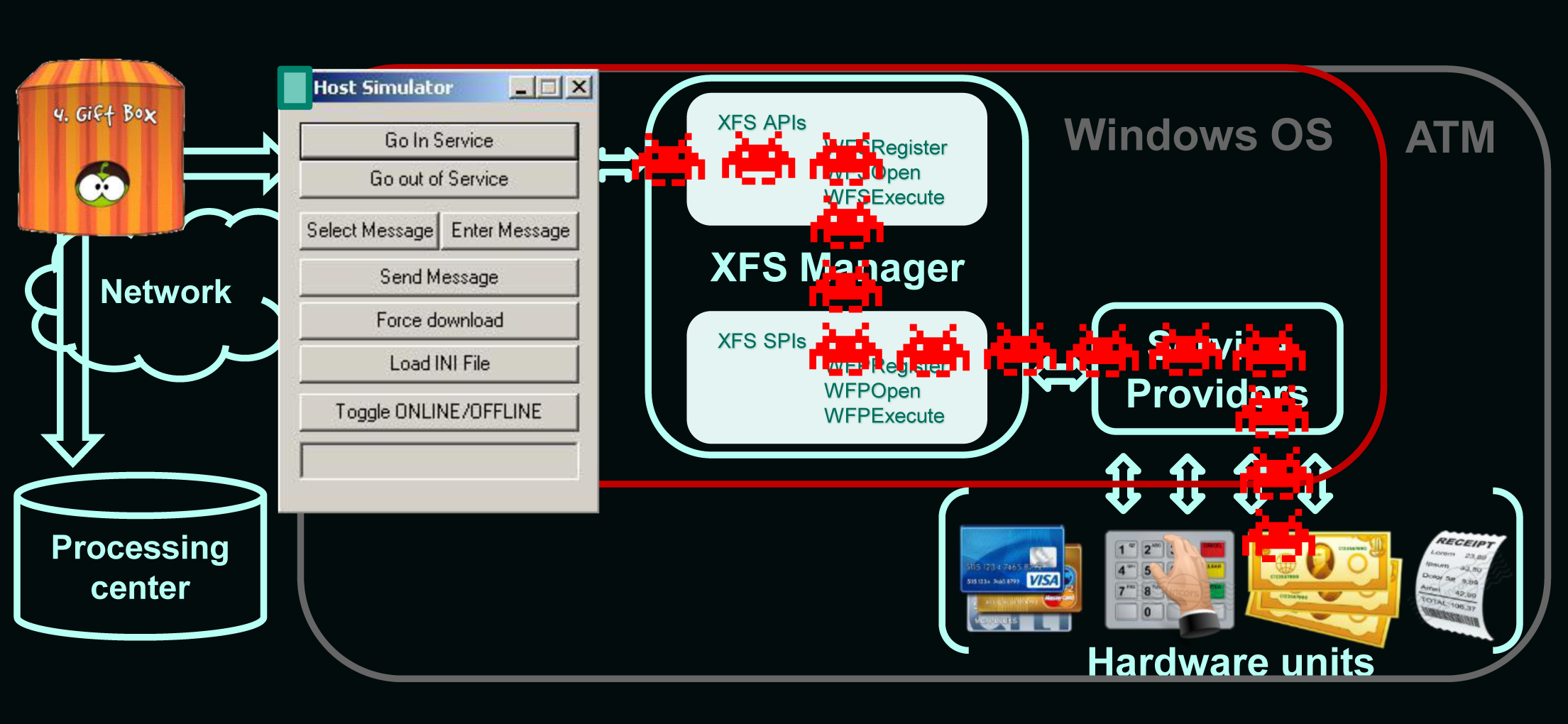
The principle of the "black box"
In recent years, according to Europol, malware for ATMs has evolved markedly. Carders no longer need physical access to an ATM to infect it. They can infect ATMs via remote network attacks using the corporate network of the bank. According to Group IB, in 2016, in more than 10 countries in Europe, ATMs were subjected to remote attack.
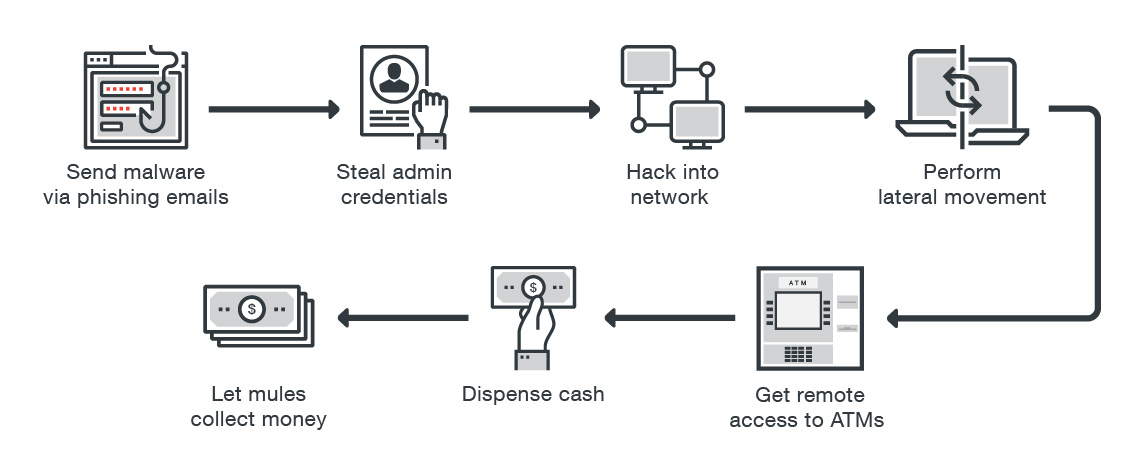
ATM attack via remote access
Antiviruses, blocking firmware updates, blocking USB ports and encrypting the hard disk - to some extent, protect the ATM from virus attacks of carders. But what if the carder does not attack the host, but connects directly to the periphery (via RS232 or USB) - to the card reader, pin-pad or cash dispenser?
The first acquaintance with the "black box"
Today, technically savvy carders do just that , using a so-called ATM to steal cash from an ATM. “Black boxes” are specifically programmed single board microcomputers, like the Raspberry Pi. “Black boxes” empty ATMs cleanly, completely magical (from the point of view of bankers) way. Carders connect their magic device directly to the banknote dispenser; to extract from it all the money available. Such an attack acts to bypass all software protection deployed on the ATM host (antivirus, integrity monitoring, full disk encryption, etc.).
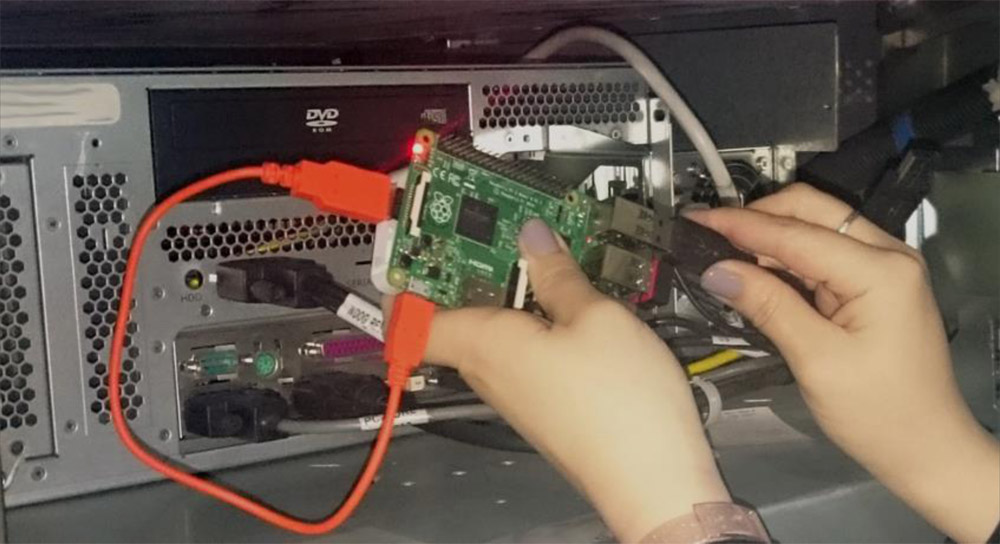
"Black Box" based on Raspberry Pi
The largest manufacturers of ATMs and government intelligence agencies, faced with several implementations of the "black box", warned that these clever computers are encouraging ATMs to spit out all the available cash; 40 banknotes every 20 seconds. Also, special services warn that carders often target ATMs in pharmacies, shopping centers; and also on ATMs that serve motorists "on the go."
At the same time, in order not to glow in front of the cameras, the most cautious carders take to the aid of some not too valuable partner, a mule. And so that he could not assign the "black box" to himself, use the following scheme . Key functionality is removed from the “black box” and a smartphone is connected to it, which is used as a channel for remote transmission of commands to the trimmed “black box” via IP protocol.

Modification of the "black box", with activation via remote access
How does it look from the point of view of bankers? On the records from the camcorder clips, something like this happens: a certain personality opens the upper compartment (service area), connects the magic box to the ATM, closes the upper compartment and leaves. After a while, a few people, seemingly ordinary customers, approach the ATM, and withdraw huge amounts of money. Then the carder returns and removes his little magical device from the ATM. Usually, the fact of an ATM attack with a “black box” is revealed only after a few days: when the empty safe and the cash withdrawal journal do not match. As a result, bank employees can only scratch their heads .
ATM Communications Analysis
As noted above, the interaction between the system unit and peripheral devices is carried out via USB, RS232 or SDC. Carder connects directly to the port of the peripheral device and sends him commands - bypassing the host. It's quite simple, because standard interfaces do not require any specific drivers. And the proprietary protocols, through which the periphery and the host interact, do not require authorization (after all, the device is inside the trusted zone); therefore, these unprotected protocols, in which the periphery and the host interact, are easy to listen to and easily replayable.
So Carders can use a software or hardware traffic analyzer, connecting it directly to the port of a specific peripheral device (for example, to a card reader) - to collect the transmitted data. Using the traffic analyzer, the carder learns all the technical details of the operation of the ATM, including the undocumented functions of its periphery (for example, the function of changing the firmware of the peripheral device). As a result, the carder gains full control of the ATM. At the same time, detecting the presence of a traffic analyzer is rather difficult.
Direct control over the banknote dispenser device means that the ATM cassettes can be emptied without any fixation in the logs that the software deployed on the host makes in normal mode. For those who are not familiar with the ATM hardware and software architecture, this is really how magic can look.
Where do the black boxes come from?
ATM vendors and subcontractors are developing debugging utilities to diagnose the hardware of the ATM, including electrical engineers who are responsible for cash withdrawals. Among such utilities: ATMDesk , RapidFire ATM XFS . The figure below shows some more of these diagnostic tools.

ATMDesk Control Panel
RapidFire ATM XFS Control Panel
Comparative characteristics of several diagnostic tools
Access to such utilities is normally limited to personalized tokens; and they work only with the open door of an ATM safe. However, simply replacing a few bytes in a binary code utility, carders can "test" cash withdrawal - bypassing the checks provided by the utility manufacturer. Carders install these modified utilities on their laptop or single-board microcomputer, which are then connected directly to a banknote dispenser for unauthorized cash withdrawals.
Last mile and fake processing center
Direct interaction with the periphery, without communication with the host is only one of the effective methods of carding. Other techniques rely on the fact that we have a wide variety of network interfaces through which an ATM connects to the outside world. From X.25 to Ethernet and cellular. Many ATMs can be identified and localized through the Shodan service (the most concise instructions on its use are presented here ), followed by an attack parasitizing the vulnerable security configuration, the administrator’s laziness, and vulnerable communications between different departments of the bank.
The “last mile” of communication between the ATM and the processing center is rich in a wide variety of technologies that can serve as an entry point for the card. The interaction can be carried out through a wired (telephone line or Ethernet) or wireless (Wi-Fi, cellular communication: CDMA, GSM, UMTS, LTE) method of communication. Security mechanisms can include: 1) hardware or software tools to support VPN (both standard, built-in operating systems, and from third-party manufacturers); 2) SSL / TLS (both specific to a specific ATM model, and from third-party manufacturers); 3) encryption; 4) message authentication.
However, it seems that for the banks the listed technologies are very complex, and therefore they do not bother with special network protection; or implement it with errors. At best, the ATM communicates with the VPN server, and already within the private network it connects to the processing center. In addition, even if the banks manage to implement the above-mentioned defense mechanisms, the carder already has effective attacks against them. So even if security complies with the PCI DSS standard, ATMs are still vulnerable.
One of the basic requirements of PCI DSS: all sensitive data, when transferred over a public network, must be encrypted. And after all, we really have networks that were originally designed so that the data is completely encrypted in them! Therefore, there is a temptation to say: "We have the data encrypted, because we use Wi-Fi and GSM." However, many of these networks do not provide sufficient protection. Cellular networks of all generations have long been hacked. Finally and irrevocably. And even there are suppliers who offer devices to intercept the data transmitted through them.
Therefore, either in unsafe communication or in a “private” network, where each ATM broadcasts itself to other ATMs, a MiTM-attack “fake processing center” can be initiated - which will cause the cardder to seize control of the data flows transmitted between ATM and processing center.
Thousands of ATMs are potentially susceptible to such MiTM attacks . On the way to the authentic processing center - the cardrer inserts his fake. This fake processing center gives the ATM a team to issue banknotes. At the same time, the cardder adjusts its processing center so that cash withdrawal takes place regardless of which card is inserted into the ATM - even if its validity period has expired, or there is a zero balance on it. The main thing is that the fake processing center “recognizes” it. As a fake processing center, either an artisanal hand-made article or a processing center simulator, originally developed for debugging network settings (another gift from the “manufacturer” to carders), can be used.
The following figure shows a dump of commands for issuing 40 banknotes from the fourth cassette, sent from a fake processing center and stored in ATM-software logs. They look almost like real ones.
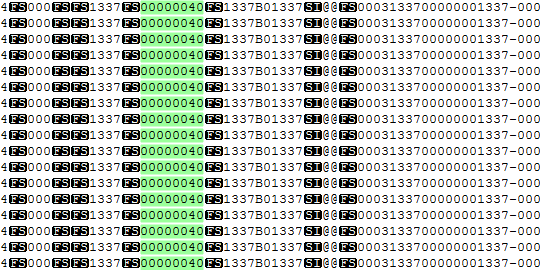
Dump commands fake processing center
')
Source: https://habr.com/ru/post/455210/
All Articles