How to protect 5G in a “smart” city: we apply a new security architecture

In the past, our post dealt with the study of an international team of scientists
A Security Architecture for 5G Networks who were looking for a way to protect fifth-generation networks. Researchers are proposing a new security architecture for this. In order to better understand the terms and concepts that are relevant to the study, you should read the first post or the full text of the work . Here we will talk about the practical application of security architecture, and immediately on the example of such a huge object as a "smart" city.
5G in smart cities
')
One of the important features of the ecosystem of a “smart” city is a large number of Internet of Things devices included in it. These IoT devices collect data, which are then analyzed and used to improve the management efficiency (including automated) of various elements of a “smart” city. Moreover, 5G technology for “smart” cities is a cost-effective and easily scalable solution that will allow you to create dedicated logical networks (slices) with the ability to fully configure the rules and security tools and is not dependent on physical networks (Wi-Fi).
Due to the speed of data transmission in 5G networks, information received from various sensors and devices is almost instantly transmitted between parts of the ecosystem and allows you to optimize, for example, the production and consumption of electricity in the city and respond quickly to accidents or malfunctions in the network. But in order for a “smart” city to function safely, 5G networks must be protected from unwanted exposure and disruption. The basic requirements for the security of such networks relate to methods of communication, confidentiality and integrity, as well as the ability to access them. The 5G network security architecture is described in more detail in the diagram below, using smart electricity meters as an example.
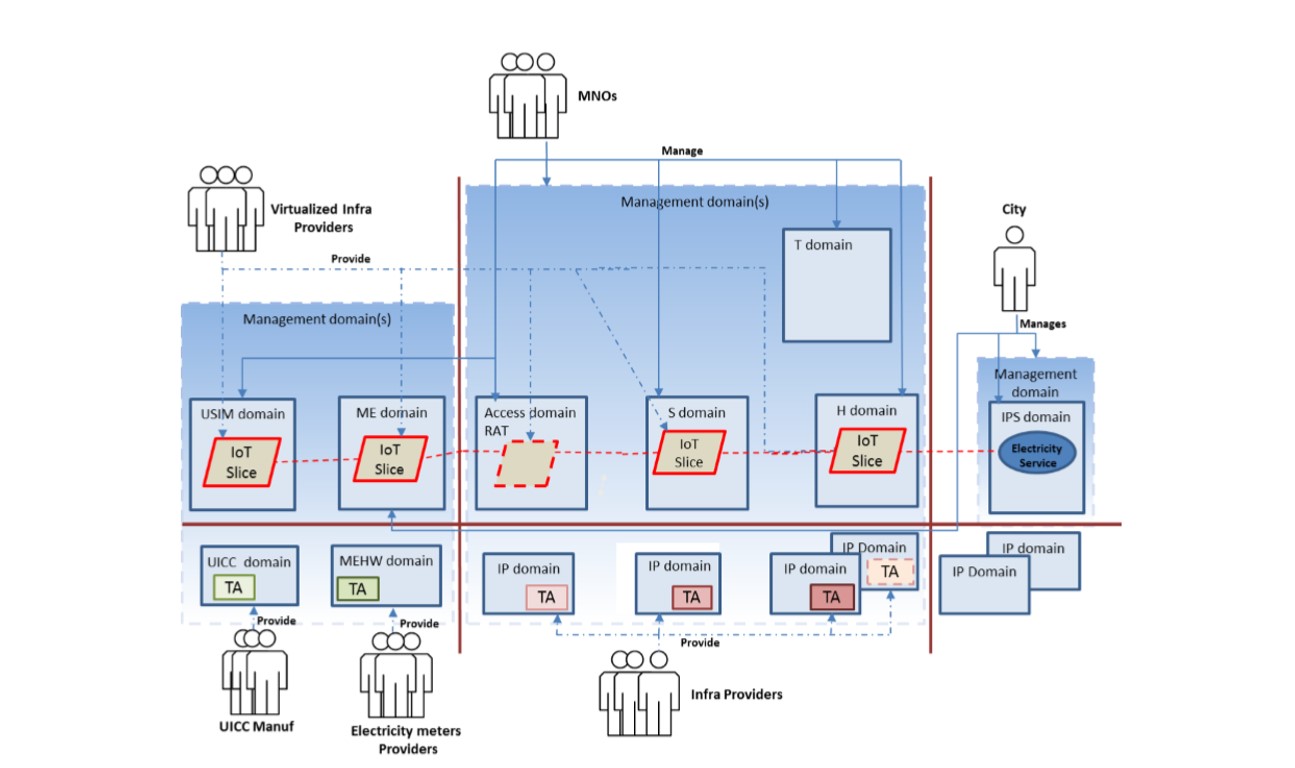 Figure 1. Smart City Security Architecture
Figure 1. Smart City Security ArchitectureFigure 1 shows the relationships and relationships between participants, processes, and resources that are included in the security architecture domains of a smart city. In this case, it is:
· Manufacturers of UICC modules
· Suppliers of electric meters
· 5G infrastructure and virtualized infrastructure providers
· MNO (mobile operators)
· The city itself, which is responsible for electricity supply.
A dedicated slice, which covers all data transfer processes between IoT gadgets (dotted red line in Figure 1), is fully controlled by mobile operators.
The electrical meters in the diagram refer to the common domain of the UE (user equipment) which consists of the domains of the UICC modules, USIM modules, MEHW (mobile hardware) and ME (mobile devices). The operator’s network hardware is a variety of infrastructure provider (IP) domains. The city’s power supply is a part of the common domain of the external network, which includes the domains of infrastructure providers and Internet connection protocols (IPS). Internet of Things slices are created using virtualized network functions (VNF). Architecture participants either manage domains (blue lines) or are their suppliers (dotted blue lines).
In this case, in general, the relationship between the participants of the architecture can be described as follows:
1. The city “trusts” mobile operators to restrict access to a certain network slice and provide it to authorized meters only.
2. Also, the city “trusts” mobile operators to protect the data received from these meters in the process of their transfer to the electricity service.
3. Users “trust” the city and mobile operators to securely collect and transmit information.
4. Mobile operators "trust" manufacturers of UUIC modules to securely store network keys in these modules.
Spheres and Classes of Security Management in the Smart City Network Architecture
In the table below, the authors of the study collected security and safety management classes related to the normal operation of electric meters and the power supply system of a “smart” city. For each sphere, they selected the appropriate classes, and for the classes - potential problems and ways to solve them. For the chosen scenario of using the architecture, the main problems arise from the limitations of the devices themselves and the unique patterns of data transfer between these devices.
To overcome these limitations, it is necessary to implement efficient protocols and solutions related to application domains, networks and access networks. Outdated software and data transmission patterns of Internet of Things devices can create problems with access to one and problems with security in other domains of the network. To deal with these problems, the authors, for example, suggest using network “slicing” technologies into slices that will allow you to isolate individual applications, as well as the use of hardware to monitor the state of the network.


An example of an attack on a network and its consequences
The two most important for the work described above system of "smart" power supply technologies are NFV (virtualization of network functions) and SDN (software-configured network). These technologies allow operators to create cost-effective tools for "cutting" networks into individual slices for data transmission. The mobile network functions in this case are virtualized, and the data flows between them are controlled by SDN controllers. In addition, SDN technology allows you to separate from each other areas of management and data due to the possibility of programming network settings and network policies.
One of the main threats to any mobile network is the loss of communication. Moreover, such a loss can be the result of a DoS attack (denial of service), when an attacker overloads SDN controllers in the domains “home”, “service” or “access”. This type of attack affects one of the functions in the transport layer (more precisely, the forwarding function) through the function in the control layer (for example, through the routing table reconfiguration function). Hackers in this case can measure the response time of the network and determine how to initiate the configuration of the routing tables. Thanks to such a fingerprinting attack (from “fingerprinting”) and the information obtained during its course, subsequent hackers' DoS attacks, during which they will endlessly call this function to overload the SDN controller, will become much more effective.
The consequences of such attacks will be:
1. Loss of communication between “customers” (in this case, electric meters) with the network and the power supply service.
2. The deterioration of the overall state of the network and the negative impact on the implementation of virtualized network functions. The mobile operator can either independently take responsibility for eliminating the threat, or transfer this task to infrastructure providers.
3. Loss of confidence in mobile operators from users. In this case, the operator is responsible for the operation of the meters and for the elimination of such threats.
The security architecture in this example is used to identify all security domains and domains affected by a particular threat and to which, therefore, certain security management classes need to be applied. Fingerprinting attacks are related to the availability and infrastructure management class in the field of infrastructure and virtualization. One of the potential mechanisms to protect against them can be the delay of the first packets of each data stream and, thus, the concealment of information about timings that can be used by hackers.
findings
In two posts on the 5G security architecture, we tried to present the main tools and ways that the authors of the A Security Architecture for 5G Networks study offer to protect 5G networks from possible attacks, and at the same time consider the practical application of their ideas. It is possible that the approach described in this study will soon be applied around the world, like the concepts of domains, layers, spheres and security management classes, or a completely logical idea that it is necessary to evaluate and ensure network security at the stage of its deployment. And this is really important, because the deployment of networks of the fifth generation in the world is happening right now, before our eyes.
With the advent of 5G, new elements and tools will appear in the infrastructure, for example, “cutting” networks into slices, virtualization of network functions and software-configured networks, and the scale of the systems (as well as their security requirements) will greatly increase. Security methods for networks of previous generations are not able to cover all the vectors of attacks on the 5G infrastructure. At a minimum, they are not prepared for new use cases with a large number of participants with different rights who simultaneously have access to this infrastructure. This is especially noticeable on the example of large 5G ecosystems, such as “smart” cities. Therefore, the emergence of new concepts such as the 5G network security architecture, which offer an alternative to well-established approaches and are ready to ensure the protection of fifth-generation networks, may become vital for the normal introduction and development of 5G technologies in the future. Which has already come.
Source: https://habr.com/ru/post/455094/
All Articles