Victory on PHDays 9. We share life hacking in three parts. Part 2
Hello! My name is Vitaly Malkin. I am the head of the security analysis department of Informzaschita and part-time captain of the True0xA3 team. A little more than a week ago we won one of the most prestigious white hacker competitions in the CIS. In the last article (if you missed it, you can read here ) we told about the importance of preliminary preparation. In this - I will talk about what happened directly at the competitions, explain why it is sometimes important to make adjustments to existing plans during the game and why, in my opinion, not one of the protected offices was hacked.
9:45 MSK
The day began with the fact that we were distributed the results of the launch of MassScan-a. We started with the fact that we immediately wrote out all the hosts with an open 445 port and at exactly 10.00 we launched the already ready meta-exploit checker for MS17-010. Guided by our plan, task # 1 was to capture the bigbrogroup domain, so two people from our team at the same time broke it. In the diagram below you can see the primary distribution of members of our team by office.
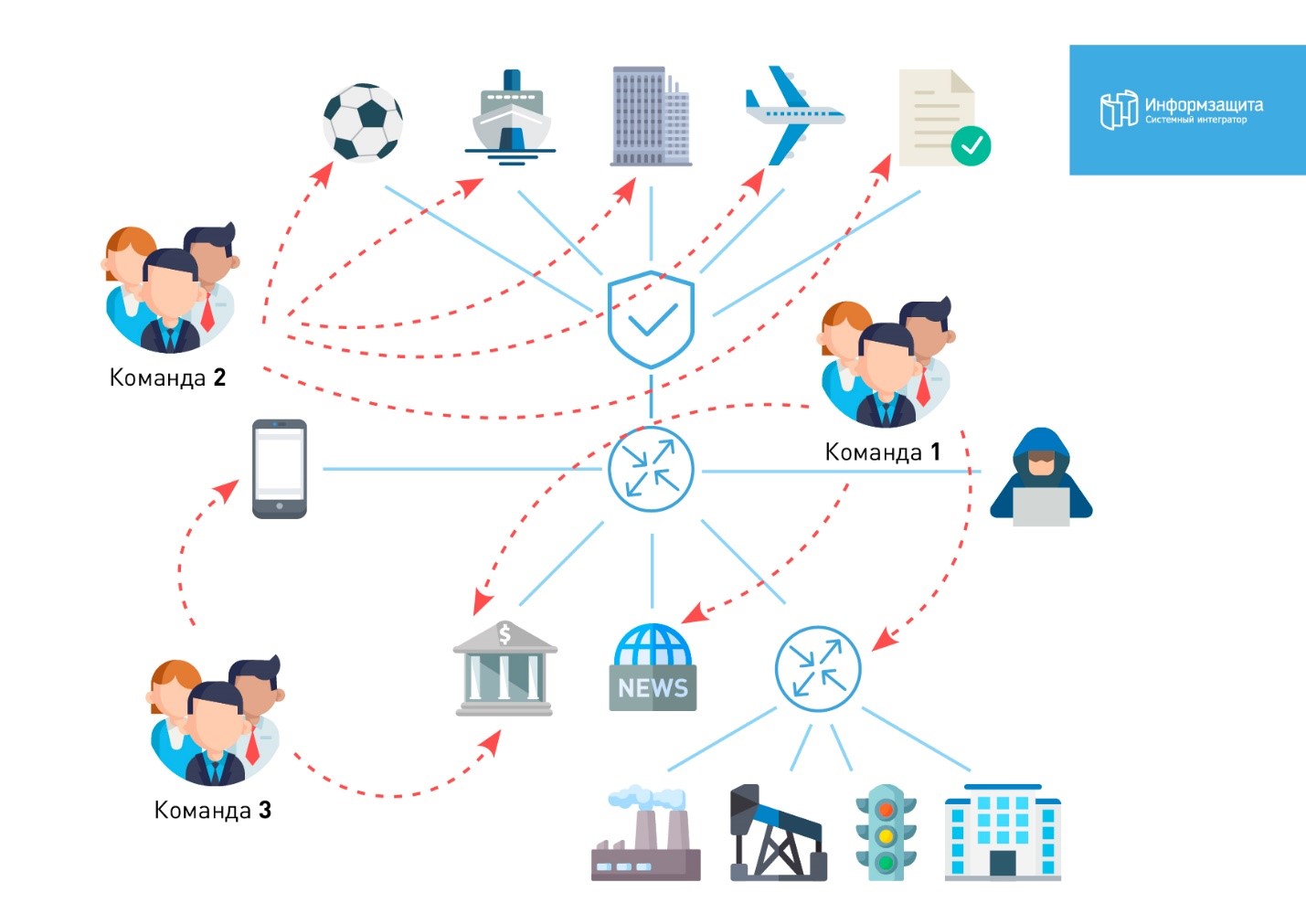
As can be seen from the diagram, we covered almost all the offices. And here the fact that there were 20 people in the team helped us a lot.
10:15
By this time, one of the members of Team-1 is finding a host vulnerable to MS17-010 in bigbrogroup.phd. We exploited the vulnerability in an incredible rush. Several years ago, we were already in a situation where we received a meterpreter shell to an important node and after 10 seconds we were thrown out of it, simultaneously closing the port. This year this did not happen: we successfully hijack a node, close the SMB port and change the RDP port to 50002. We take a very responsible approach to the issue of maintaining access, so we add several local administrators and install our own RAT. After that we move on.
10:25
We continue to deal with what we have found. Besides the fact that this node has access to the internal network and to the domain controller, it also detects the domain administrator token. This is a jackpot! We immediately check that it is not rotten, and there is no limit to our joy. The first domain has fallen. Hacking time - 27 minutes 52 seconds.
')
Finally, half an hour after the start of the competition, we still go into the hacker portal and try to understand what we need to do to get a public. We see the standard set: domain administrator, workstation administrator, exchange, and also several top data. We download from the domain ntds.dit, simultaneously uncovering a CUDA station. What was our surprise when we saw that the domain enabled reversible encryption, allowing us to get all user passwords in the clear. To form an understanding of which users are interesting to us, we used two people from Team 1 to analyze the structure of AD and its groups. Five minutes later we had all the answers. We send them to the portal and start to wait. Honestly - by that time I really wanted to shed the first blood to maintain morale so to speak, but only an hour later we could understand how the checker works:
a) checker is automated;
b) the checker has a hard format;
c) the checker a few seconds after sending the answer did not accept our answer, because it was in the wrong format.
Having mastered the format, at about 11.00 we get the coveted First blood. Eeeee!
11:15 am
Team 1 is divided into two parts. Members of one subcommand continue to be fixed in the domain: they receive krbtgt, strengthen the domain, change passwords for accounts. PHDays organizers made it clear at the briefing - who was the first to stand up, and sneakers. Therefore, we change the passwords on the accounts, to be sure: if someone throws us out, they will receive a minimum of points.
Team-2 while continuing to explore the domain, and finds the answer to another task. On the desktop of the financial director found a financial report, so necessary to someone. But the trouble is - it is in the archive, which is password-protected. Well, no wonder we uncovered the CUDA station. With a slight movement of the hand we turn the archive into a hash and send it to hashcat.
Team-2 at this time finds some interesting services with RCE and begins to "twist" them. This is a monitoring in CF-media based on Nagios. This is a system of drawing graphs from the ship company, built on the technology that we see for the first time. And also some more potentially interesting services like a converter from DOC to PDF.
The second subcommand of Team 1, meanwhile, deals with the bank and finds an interesting base on MongoDB, in which, among other things, is the name of our team and its balance in some system. We “spin up” our balance by 50 million and move on.
2:00 pm
We are overtaken by the first failures. First, the two services in which we received RCE in the protected segments became unavailable. The defenders simply turned them off. Of course we are going to complain to the organizers. It leads to nothing. Well, yes, in Standoff, alas, there is no business that would give a hint for such a hat. In addition, we can not find a list of customers. We assume that it is hidden somewhere in the depths of 1C, but there are neither bases nor working configurations. This is a dead end.
We are trying to raise the VPN channel between our remote servers and the ICS network. For unknown reasons, we do this on a bigbrogroup domain controller, and at the time of building the bridge between the interfaces, the connection is terminated. Domain controller is not available. The part of the team that captured the bigbrogroup almost had a heart attack: the first quarrels begin, the general tension increases.
Suddenly, we understand that the domain controller is still accessible from our servers, but the channel is very unstable. As in a step-by-step strategy, we disable bridge mode via RDP, the domain controller is available again. Fuh !!! Everyone calms down. VPN, we end up with a different server, the domain controller is holim and cherish. All teams have zero points, this calms down.
16:50
The organizers finally publish the miner and we, using psexec, install it on all nodes under our control. We get an additional stable income.
Team-2 tightens Nagios vulnerability. The vulnerable version <= 5.5.6 CVE-2018-15710 CVE-2018-15708 is installed there. A public exploit exists, but uses a reverse connection to download a web shell. We are behind NAT, so we have to rewrite the exploit and break it into two parts. The first one makes Nagios connect to our remote server via the Internet, and the second one, located directly on the server, gives Nagios to the web shell. After receiving the web shell, WSO was loaded and the vulnerable PHP script “magpie_debug.php” was removed. This gives us proxy access to the CF-media domain. The connection is unstable and it is difficult to use it, we decide to send an exploit to Bug-bounty, while at this time we are trying to “rise” to Root.
18:07
And here are the promised surprises from the organizers: BigBroGroup buy CF-media! In general, we assumed a similar turn. During the study of the bigbrogroup domain controller, we noticed trust between this domain and the cf-media domain.
Unfortunately, at that time there was no network access. But at the time of the merger announcement, he appeared. This saved us from the headache associated with pivotting through nagios. The bigbrogroup credentials work on cf-media, but users are unprivileged. There are no easily exploited vulnerabilities, but we do not despair. Something must be.
18:30
We are knocked out from the domain controller BigBroGroup. Who! Where? It seems that the team CARK. They change the domain administrator password, but we have four backup ones. We change back, reset all passwords. It does not help, we are again knocked out. At the same time, we find vectors in CF-media. On one of the servers, the same local administrator password is used as in the bigbrogroup domain. Well, password reuse, it remains to pick up a hash! Using hashkiller we find the password - “P @ ssw0rd”. Breaking further.
19:00
The battle for bigbrogroup doesn't stop. CARKA twice changes the password to krbtgt, we lost all admins. This is the end?
19:30
We get the administrator domain CF-media, we begin to pass the flags. Despite the fact that the domain seems to be configured as secure as possible, reverse encryption is enabled again. We get appearances, logins, passwords. We repeat everything as in the past domain: we fix, hardenim, change passwords, prokidyvaem VPN. Find the second financial report. By the way, what's up with the first? The first is already straightened, but is not accepted by the orgs. It turns out that you need to pass the encrypted 7z !!! Brutality did not need anything, three hours for nothing !!!
As a result, we hand over both. We have about 1 million points, CARK has 125.000, the rest are zeros. CARKA begins to hand over flags to the Bigbrogroup. We understand that it needs to be urgently stopped, but HOW ?!
7:45 pm
There was a solution !!! We still have the credentials of local administrators. Connect, pick up the ticket and decide to just drop the domain. The domain goes to power off, we close all ports on servers, except RDP, we change passwords of local administrators. Now we are on our own, and they are on their own. Another would be to achieve a stable VPN and everything would be fine. You exited ...
Spread miner across all nodes in the CF-media domain. The CARK overtakes us in terms of total volume, but we are clearly catching up with them, because we have more power.
In the picture you can see the distribution of the team at night.
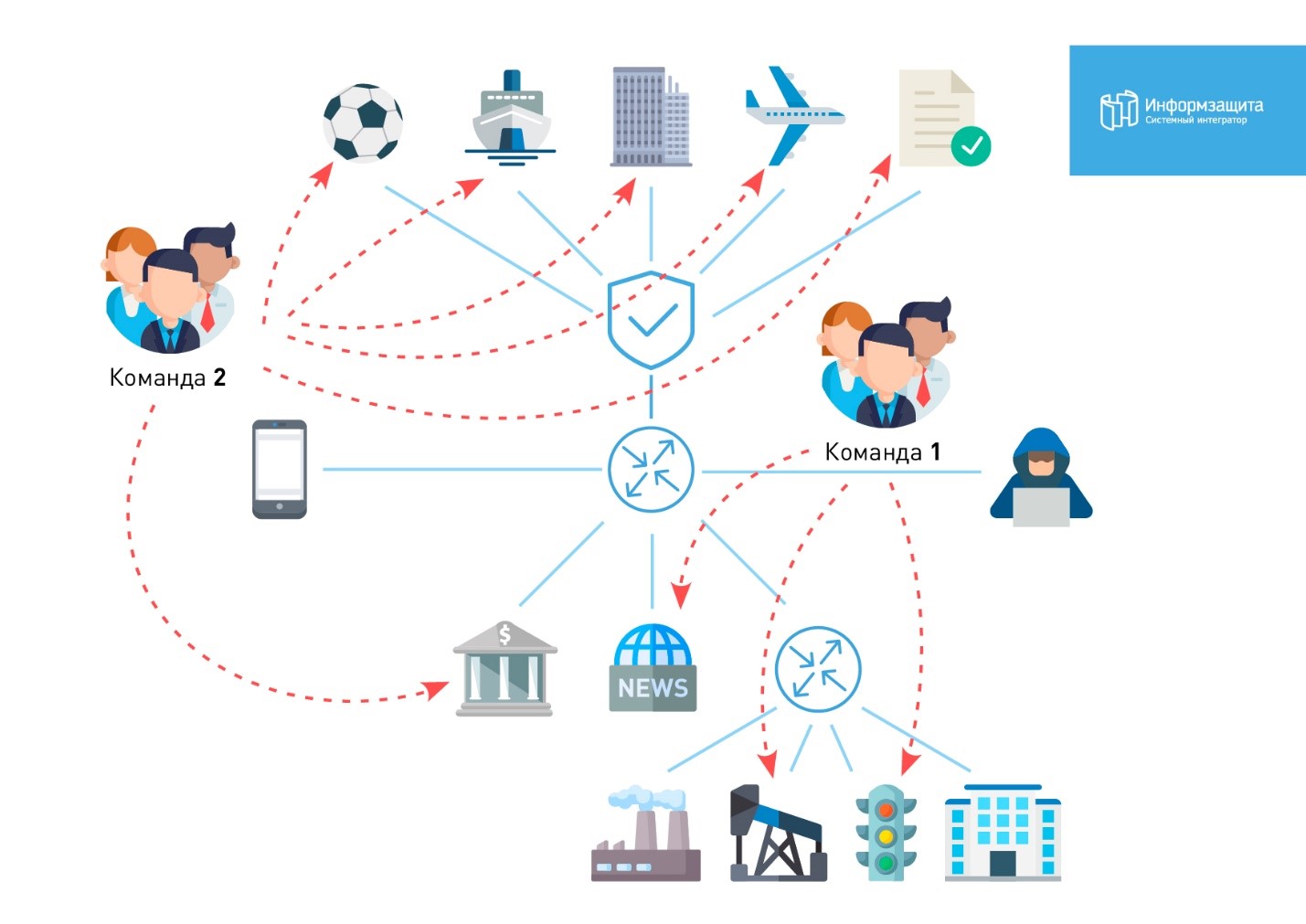
The guys gradually begin to go home. By midnight, nine people remain. Efficiency is greatly reduced. Every hour we leave to wash and breathe — so as not to fall asleep.
Getting to the process control system.
02:00
The night is very hard. We find vectors several times, but they are already closed. It is not entirely clear whether they were originally closed, or whether CARK had already been here before us and closed them. Gradually mastering the process control system, we find a controller vulnerable to an attack through NetBus. Using the meta-layer module, we do something, not fully understanding what. The light in the city goes out. The organizers are ready to count the task, if we can turn the light back on. At this point, the VPN connection drops again. The server on which the VPN is deployed is under the control of CARK. It seems again that this is the end: we were too noisy discussing the process control system and they were able to somehow turn us off.
3:30 am
The most persistent "cuts" sleep. Only seven remain awake. Suddenly (for no apparent reason) the VPN starts up again. We quickly repeat the focus with the light. There are 200,000 posts !!!
Part of the team continues to look for other vectors, part continues to work actively with the ACS TP. We find two more potential vulnerabilities. One of them we manage to exploit. The result may be a rewrite of the controller firmware. We agree with the organizers that we will wait until the morning and together we will decide what to do.
05:30
The VPN works 10 minutes per hour, the rest of the time it dies. We are trying to find anything. Our performance is almost zero. We decide to sleep at least an hour. SPOILER: bad idea.
Five guys continue to break the process control system.
By the morning, we understand that we were significantly off points by the rest, by almost 1 million. CARKA was able to pass two tasks from the industrial control system and several tasks from the telecom and bigbrogroup. They have a lot of nain, but according to our calculations, they have a stock that they have not yet sold. At the current rate, he went to 200-300 tons. Public. This scares us: there is a feeling that they may have several flags in the store that they can save for the final breakthrough. In our regiment arrives. Morning sound check at the site is a bit annoying, but invigorating.
We are still trying to break the process control system, but without much hope. The gap between the teams claiming the first and second place, and the rest is too big. We do not believe that the organizers will leave everything as it is.
After a joint performance with CARK on the stage, we change the paradigm from “we need to score more points”, but to “we must not let CARK score more points”.
On one of our servers, run Cain & Abel and transfer all traffic to our server. We find several Kazakh VPNs, we “chop” them up. As a result, we decide to hack all the traffic, set up a local firewall on the gateway to ban all traffic to the automated process control system of the network (here's how to protect the automatic process control system). The organizers come running and say that they do not have access to the automated process control system. We saw them accesses for their IP-addresses (here's how not to protect the process control system).
12:47
No wonder they were nervous. Organizers throw up another surprise. From nowhere, four domain accounts for each domain pop up. Mobilize the team.
The task of Team 1 is to climb into the protected segments as quickly and as quickly as possible. Task 2 Commands - using Outlook Web Access to change account passwords. Some defenders, something zapodozriv, just turn off the VPN. Some are trickier - translate their systems into Chinese. The functional works, but it is impossible to use it (orgi, ay!). Through VPN we are connected to three networks. From the first throws us out in a minute.
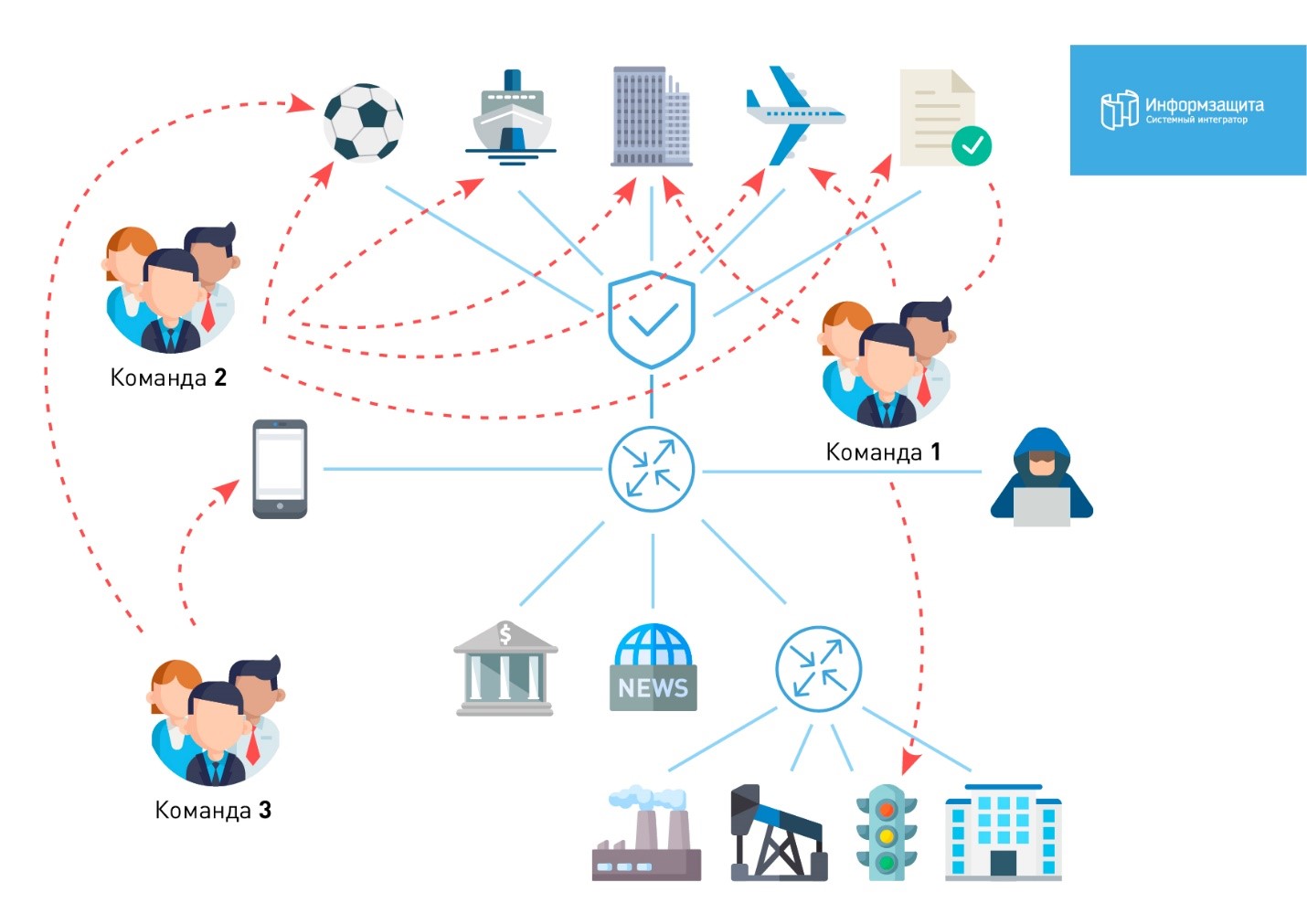
12:52
We find in the behealthy network a server vulnerable to MS17-010 (protected! Segment). We exploit, without encountering resistance, we get the domain administrator hash and through Pth go to the domain controller. Guess what we find there? Reversible encryption!
It seems that those who defended this segment did their homework poorly. We get all the information for tasks, except for the part related to 1C. There is an option to pick it up for another 40-50 minutes, but we decide to just drop the domain. We do not need competitors.
13:20
We pass the job: we have 2.900.000 points and several unaccepted bounty bugs. CARKs have a little more than 1 million. They give up their cryptocurrency and raise 200 tons. We are not too afraid to catch up with us almost unreal.
13:55
Suited people, congratulations. We are still afraid of some kind of setup, but it seems not, we are real champions!
Here is a chronicle of 28 hours from True0xA3. A lot of what is left overs. For example, going on stage, the torment of Wi-Fi and GSM, communication with reporters, but it seems to me that this is not the most interesting.
It was a very cool experience for all of us and I hope that I managed to convey at least a little of the atmosphere that surrounded us all this time and show how interesting it is to be involved. There is another, the last article, in which we will evaluate our mistakes, and we will try to draw up a plan for their correction. After all, there is nothing better than to learn from the mistakes of others.
The first day
9:45 MSK
The day began with the fact that we were distributed the results of the launch of MassScan-a. We started with the fact that we immediately wrote out all the hosts with an open 445 port and at exactly 10.00 we launched the already ready meta-exploit checker for MS17-010. Guided by our plan, task # 1 was to capture the bigbrogroup domain, so two people from our team at the same time broke it. In the diagram below you can see the primary distribution of members of our team by office.

As can be seen from the diagram, we covered almost all the offices. And here the fact that there were 20 people in the team helped us a lot.
10:15
By this time, one of the members of Team-1 is finding a host vulnerable to MS17-010 in bigbrogroup.phd. We exploited the vulnerability in an incredible rush. Several years ago, we were already in a situation where we received a meterpreter shell to an important node and after 10 seconds we were thrown out of it, simultaneously closing the port. This year this did not happen: we successfully hijack a node, close the SMB port and change the RDP port to 50002. We take a very responsible approach to the issue of maintaining access, so we add several local administrators and install our own RAT. After that we move on.
10:25
We continue to deal with what we have found. Besides the fact that this node has access to the internal network and to the domain controller, it also detects the domain administrator token. This is a jackpot! We immediately check that it is not rotten, and there is no limit to our joy. The first domain has fallen. Hacking time - 27 minutes 52 seconds.
')
Finally, half an hour after the start of the competition, we still go into the hacker portal and try to understand what we need to do to get a public. We see the standard set: domain administrator, workstation administrator, exchange, and also several top data. We download from the domain ntds.dit, simultaneously uncovering a CUDA station. What was our surprise when we saw that the domain enabled reversible encryption, allowing us to get all user passwords in the clear. To form an understanding of which users are interesting to us, we used two people from Team 1 to analyze the structure of AD and its groups. Five minutes later we had all the answers. We send them to the portal and start to wait. Honestly - by that time I really wanted to shed the first blood to maintain morale so to speak, but only an hour later we could understand how the checker works:
a) checker is automated;
b) the checker has a hard format;
c) the checker a few seconds after sending the answer did not accept our answer, because it was in the wrong format.
Having mastered the format, at about 11.00 we get the coveted First blood. Eeeee!
11:15 am
Team 1 is divided into two parts. Members of one subcommand continue to be fixed in the domain: they receive krbtgt, strengthen the domain, change passwords for accounts. PHDays organizers made it clear at the briefing - who was the first to stand up, and sneakers. Therefore, we change the passwords on the accounts, to be sure: if someone throws us out, they will receive a minimum of points.
Team-2 while continuing to explore the domain, and finds the answer to another task. On the desktop of the financial director found a financial report, so necessary to someone. But the trouble is - it is in the archive, which is password-protected. Well, no wonder we uncovered the CUDA station. With a slight movement of the hand we turn the archive into a hash and send it to hashcat.
Team-2 at this time finds some interesting services with RCE and begins to "twist" them. This is a monitoring in CF-media based on Nagios. This is a system of drawing graphs from the ship company, built on the technology that we see for the first time. And also some more potentially interesting services like a converter from DOC to PDF.
The second subcommand of Team 1, meanwhile, deals with the bank and finds an interesting base on MongoDB, in which, among other things, is the name of our team and its balance in some system. We “spin up” our balance by 50 million and move on.
2:00 pm
We are overtaken by the first failures. First, the two services in which we received RCE in the protected segments became unavailable. The defenders simply turned them off. Of course we are going to complain to the organizers. It leads to nothing. Well, yes, in Standoff, alas, there is no business that would give a hint for such a hat. In addition, we can not find a list of customers. We assume that it is hidden somewhere in the depths of 1C, but there are neither bases nor working configurations. This is a dead end.
We are trying to raise the VPN channel between our remote servers and the ICS network. For unknown reasons, we do this on a bigbrogroup domain controller, and at the time of building the bridge between the interfaces, the connection is terminated. Domain controller is not available. The part of the team that captured the bigbrogroup almost had a heart attack: the first quarrels begin, the general tension increases.
Suddenly, we understand that the domain controller is still accessible from our servers, but the channel is very unstable. As in a step-by-step strategy, we disable bridge mode via RDP, the domain controller is available again. Fuh !!! Everyone calms down. VPN, we end up with a different server, the domain controller is holim and cherish. All teams have zero points, this calms down.
16:50
The organizers finally publish the miner and we, using psexec, install it on all nodes under our control. We get an additional stable income.
Team-2 tightens Nagios vulnerability. The vulnerable version <= 5.5.6 CVE-2018-15710 CVE-2018-15708 is installed there. A public exploit exists, but uses a reverse connection to download a web shell. We are behind NAT, so we have to rewrite the exploit and break it into two parts. The first one makes Nagios connect to our remote server via the Internet, and the second one, located directly on the server, gives Nagios to the web shell. After receiving the web shell, WSO was loaded and the vulnerable PHP script “magpie_debug.php” was removed. This gives us proxy access to the CF-media domain. The connection is unstable and it is difficult to use it, we decide to send an exploit to Bug-bounty, while at this time we are trying to “rise” to Root.
18:07
And here are the promised surprises from the organizers: BigBroGroup buy CF-media! In general, we assumed a similar turn. During the study of the bigbrogroup domain controller, we noticed trust between this domain and the cf-media domain.
Unfortunately, at that time there was no network access. But at the time of the merger announcement, he appeared. This saved us from the headache associated with pivotting through nagios. The bigbrogroup credentials work on cf-media, but users are unprivileged. There are no easily exploited vulnerabilities, but we do not despair. Something must be.
18:30
We are knocked out from the domain controller BigBroGroup. Who! Where? It seems that the team CARK. They change the domain administrator password, but we have four backup ones. We change back, reset all passwords. It does not help, we are again knocked out. At the same time, we find vectors in CF-media. On one of the servers, the same local administrator password is used as in the bigbrogroup domain. Well, password reuse, it remains to pick up a hash! Using hashkiller we find the password - “P @ ssw0rd”. Breaking further.
19:00
The battle for bigbrogroup doesn't stop. CARKA twice changes the password to krbtgt, we lost all admins. This is the end?
19:30
We get the administrator domain CF-media, we begin to pass the flags. Despite the fact that the domain seems to be configured as secure as possible, reverse encryption is enabled again. We get appearances, logins, passwords. We repeat everything as in the past domain: we fix, hardenim, change passwords, prokidyvaem VPN. Find the second financial report. By the way, what's up with the first? The first is already straightened, but is not accepted by the orgs. It turns out that you need to pass the encrypted 7z !!! Brutality did not need anything, three hours for nothing !!!
As a result, we hand over both. We have about 1 million points, CARK has 125.000, the rest are zeros. CARKA begins to hand over flags to the Bigbrogroup. We understand that it needs to be urgently stopped, but HOW ?!
7:45 pm
There was a solution !!! We still have the credentials of local administrators. Connect, pick up the ticket and decide to just drop the domain. The domain goes to power off, we close all ports on servers, except RDP, we change passwords of local administrators. Now we are on our own, and they are on their own. Another would be to achieve a stable VPN and everything would be fine. You exited ...
Spread miner across all nodes in the CF-media domain. The CARK overtakes us in terms of total volume, but we are clearly catching up with them, because we have more power.
Night
In the picture you can see the distribution of the team at night.

The guys gradually begin to go home. By midnight, nine people remain. Efficiency is greatly reduced. Every hour we leave to wash and breathe — so as not to fall asleep.
Getting to the process control system.
02:00
The night is very hard. We find vectors several times, but they are already closed. It is not entirely clear whether they were originally closed, or whether CARK had already been here before us and closed them. Gradually mastering the process control system, we find a controller vulnerable to an attack through NetBus. Using the meta-layer module, we do something, not fully understanding what. The light in the city goes out. The organizers are ready to count the task, if we can turn the light back on. At this point, the VPN connection drops again. The server on which the VPN is deployed is under the control of CARK. It seems again that this is the end: we were too noisy discussing the process control system and they were able to somehow turn us off.
3:30 am
The most persistent "cuts" sleep. Only seven remain awake. Suddenly (for no apparent reason) the VPN starts up again. We quickly repeat the focus with the light. There are 200,000 posts !!!
Part of the team continues to look for other vectors, part continues to work actively with the ACS TP. We find two more potential vulnerabilities. One of them we manage to exploit. The result may be a rewrite of the controller firmware. We agree with the organizers that we will wait until the morning and together we will decide what to do.
05:30
The VPN works 10 minutes per hour, the rest of the time it dies. We are trying to find anything. Our performance is almost zero. We decide to sleep at least an hour. SPOILER: bad idea.
Five guys continue to break the process control system.
Morning
By the morning, we understand that we were significantly off points by the rest, by almost 1 million. CARKA was able to pass two tasks from the industrial control system and several tasks from the telecom and bigbrogroup. They have a lot of nain, but according to our calculations, they have a stock that they have not yet sold. At the current rate, he went to 200-300 tons. Public. This scares us: there is a feeling that they may have several flags in the store that they can save for the final breakthrough. In our regiment arrives. Morning sound check at the site is a bit annoying, but invigorating.
We are still trying to break the process control system, but without much hope. The gap between the teams claiming the first and second place, and the rest is too big. We do not believe that the organizers will leave everything as it is.
After a joint performance with CARK on the stage, we change the paradigm from “we need to score more points”, but to “we must not let CARK score more points”.
On one of our servers, run Cain & Abel and transfer all traffic to our server. We find several Kazakh VPNs, we “chop” them up. As a result, we decide to hack all the traffic, set up a local firewall on the gateway to ban all traffic to the automated process control system of the network (here's how to protect the automatic process control system). The organizers come running and say that they do not have access to the automated process control system. We saw them accesses for their IP-addresses (here's how not to protect the process control system).
12:47
No wonder they were nervous. Organizers throw up another surprise. From nowhere, four domain accounts for each domain pop up. Mobilize the team.
The task of Team 1 is to climb into the protected segments as quickly and as quickly as possible. Task 2 Commands - using Outlook Web Access to change account passwords. Some defenders, something zapodozriv, just turn off the VPN. Some are trickier - translate their systems into Chinese. The functional works, but it is impossible to use it (orgi, ay!). Through VPN we are connected to three networks. From the first throws us out in a minute.

12:52
We find in the behealthy network a server vulnerable to MS17-010 (protected! Segment). We exploit, without encountering resistance, we get the domain administrator hash and through Pth go to the domain controller. Guess what we find there? Reversible encryption!
It seems that those who defended this segment did their homework poorly. We get all the information for tasks, except for the part related to 1C. There is an option to pick it up for another 40-50 minutes, but we decide to just drop the domain. We do not need competitors.
13:20
We pass the job: we have 2.900.000 points and several unaccepted bounty bugs. CARKs have a little more than 1 million. They give up their cryptocurrency and raise 200 tons. We are not too afraid to catch up with us almost unreal.
13:55
Suited people, congratulations. We are still afraid of some kind of setup, but it seems not, we are real champions!
Here is a chronicle of 28 hours from True0xA3. A lot of what is left overs. For example, going on stage, the torment of Wi-Fi and GSM, communication with reporters, but it seems to me that this is not the most interesting.
It was a very cool experience for all of us and I hope that I managed to convey at least a little of the atmosphere that surrounded us all this time and show how interesting it is to be involved. There is another, the last article, in which we will evaluate our mistakes, and we will try to draw up a plan for their correction. After all, there is nothing better than to learn from the mistakes of others.
Source: https://habr.com/ru/post/454366/
All Articles