Again, hundreds of thousands of payments to citizens in the traffic police and FSSP were in the public domain.
Remember I wrote on Habré and in my Telegram channel how the details of payments in favor of traffic police and FSSP of users of payment sites, paygibdd.ru , gos-oplata.ru , fines.net and oplata-fssp.ru were in open access . ?
Just do not laugh, this is not a joke at all - the same server with the data of the same system was again open to the whole world.
Well, let's go understand ...
: . . , . To begin with, let me remind you a bit of the chronology of events:
- 04/12/2019 (at night) Elasticsearch server was found that does not require authentication to connect.
- 04/13/2019 (in the morning) an alert was sent to the server owners.
- 04/13/2019 (in the afternoon) the server was "quietly" removed from open access.
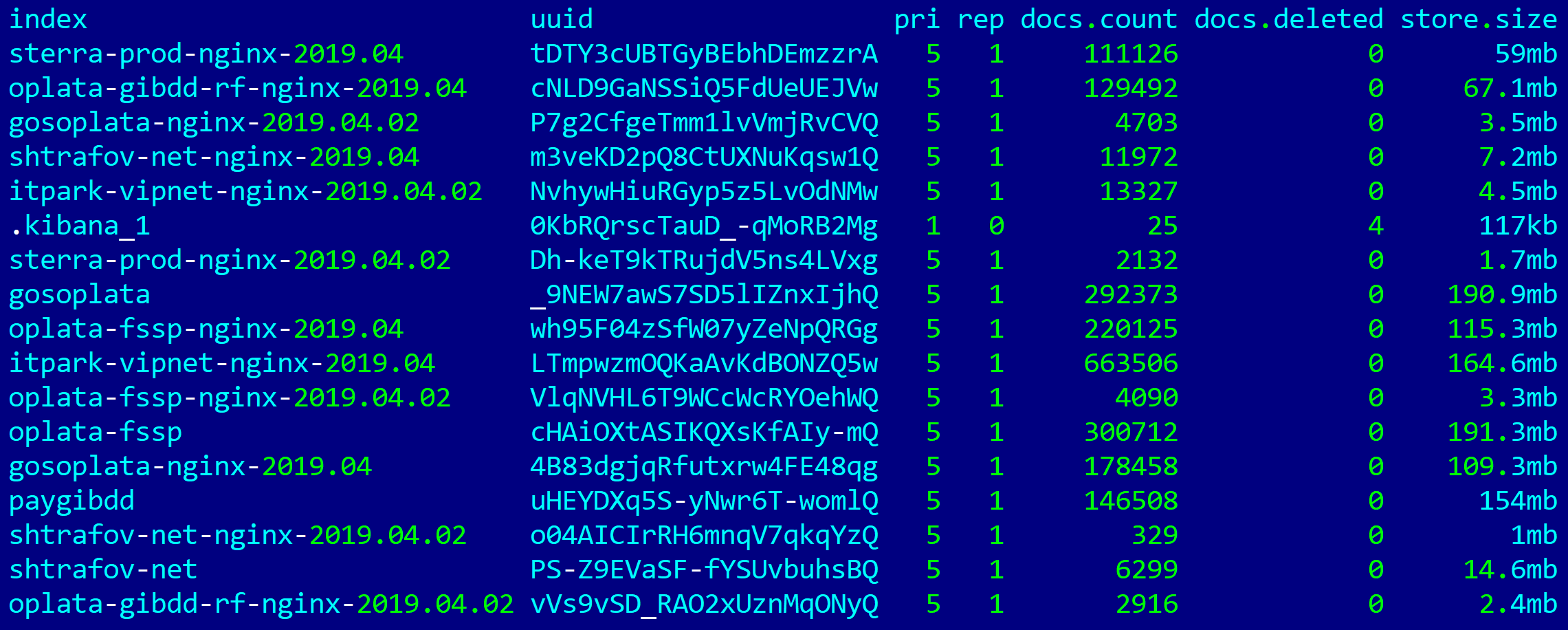
At the time of the first server shutdown, Elasticsearch indexes looked like this:
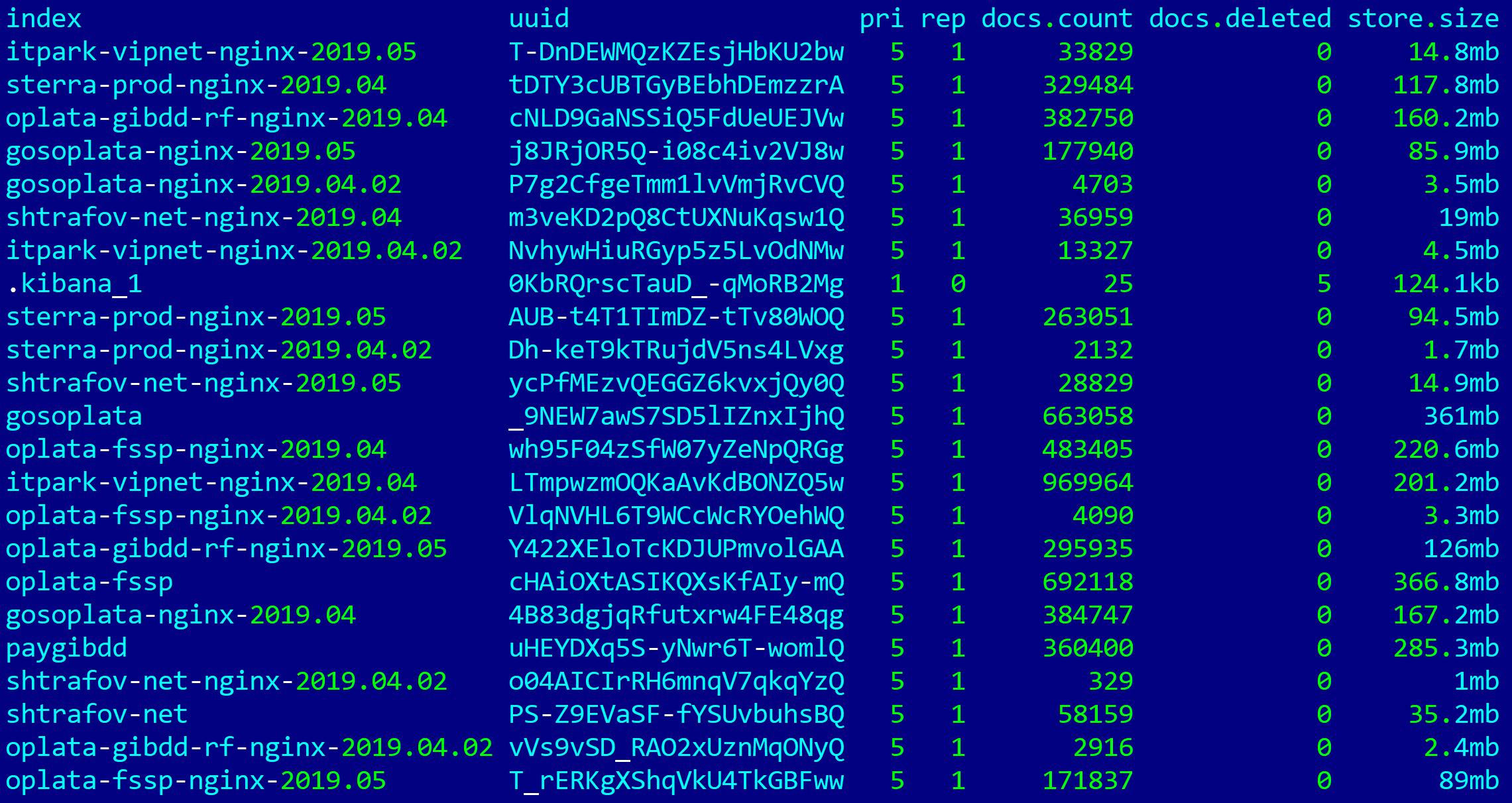
And on May 21, 2019, around 4:00 pm (MSK), the same Elasticsearch server, with the same (plus new) indices, appears again in open access:
I didn’t believe my eyes when I saw (immediately after speaking on PHDays on the topic of detecting open databases) a notification from our DeviceLock Data Breach Intelligence in the mail. To be honest, the first thought was that it was some kind of glitch system.
However, no, it was not a glitch and having rechecked everything manually, at 01:25 on 05.22.2019 I again sent an alert to the same addresses as for the first time.
From the moment of the first closing, this server was scanned by Shodan 11 times and until May 21st Elasticsearch was covered on it.
Only on May 24, 2019 in the morning, this Elasticsearch disappeared from public access a second time. During this time, the indices have grown solidly:
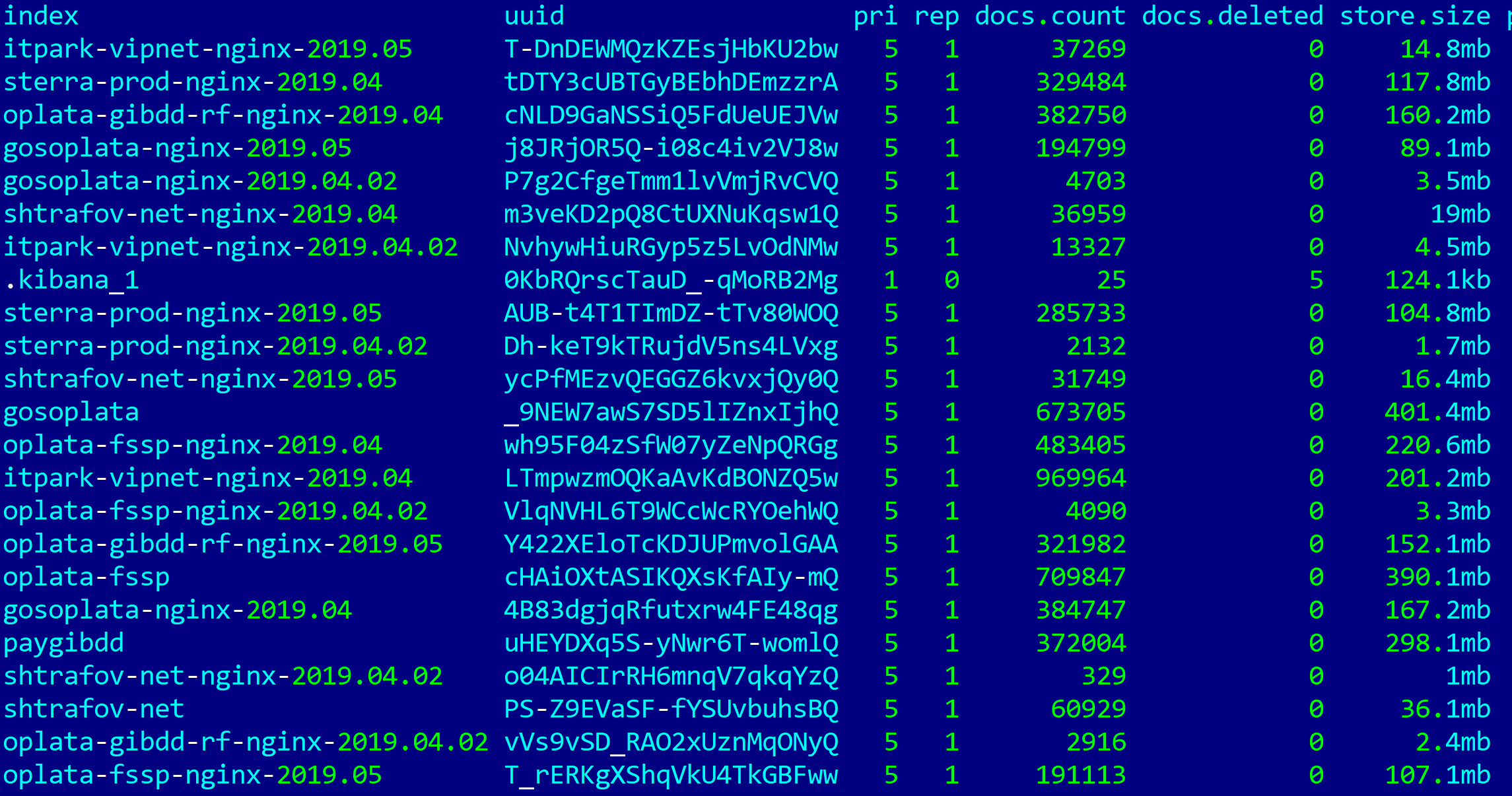
And if you look at the data (only significant information containing personal data of citizens) in the indices for the period from May 1 to May 22, the picture is as follows:
- 127,525 entries in paygibdd index
- 49,627 records in the index shtrafov-net
- 162,282 entries in oplata-fssp index
- 220,201 records in gosoplata index
Sample data from the gosoplata index:
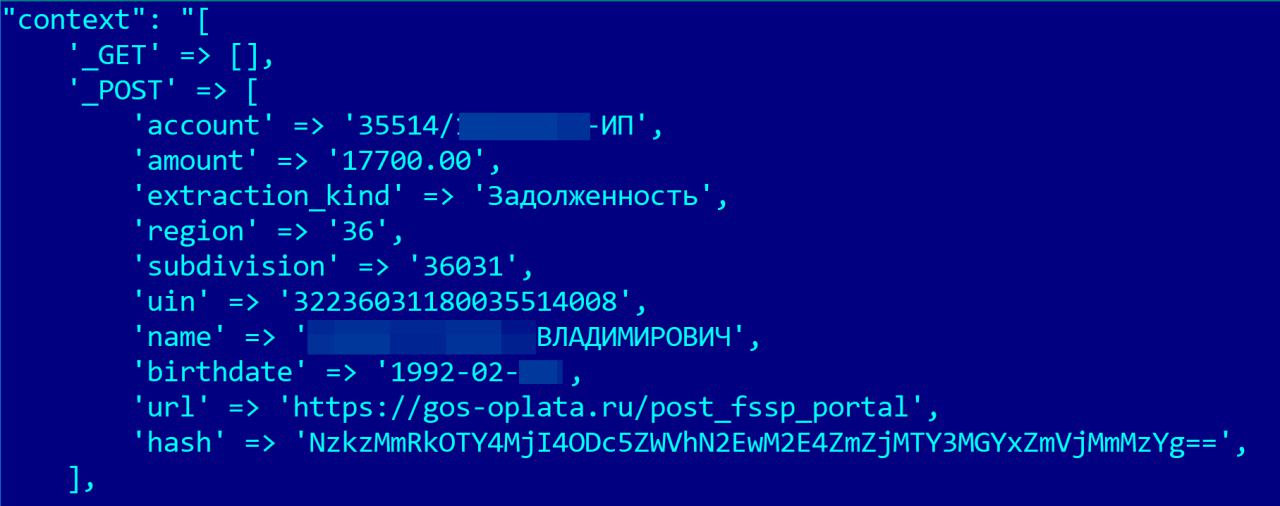
Sample data from paygibdd index:
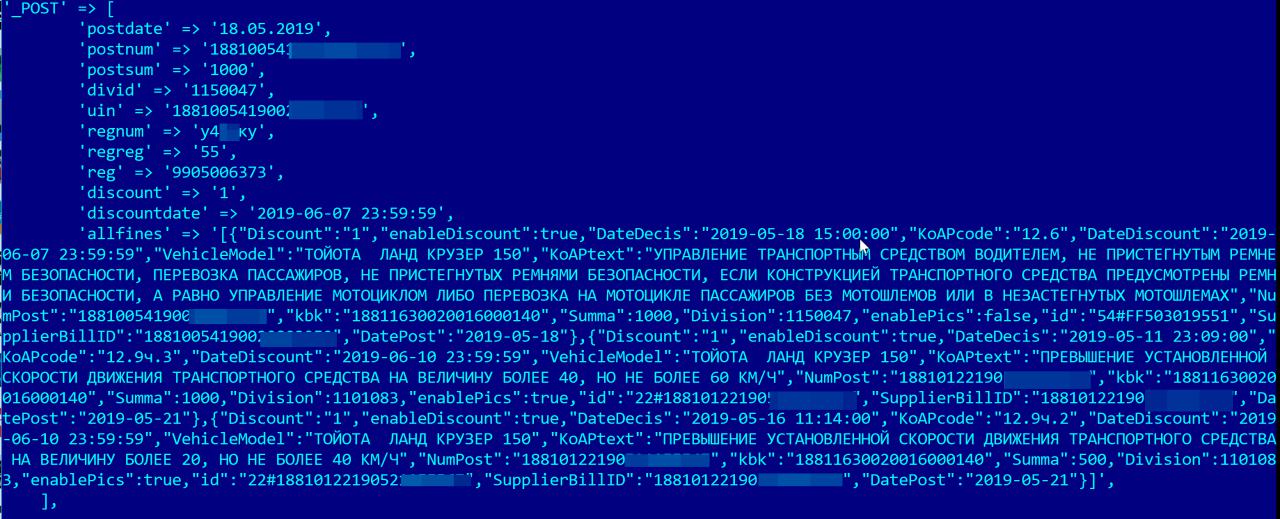
Well, the cherry on the cake was a letter from one of the addresses to which I sent alerts:
We received your letter about the open ElasticSearch - thanks for the information, the database was closed. The system administrator who re-accessed is fired. Also, the legal department is preparing to send a statement to the Ministry of Internal Affairs for the Republic of Tatarstan on the signs of the presence in the actions of the system administrator of the 272 and 273 articles of the Criminal Code of the Russian Federation.
News about information leaks and insiders can always be found on my Information Leaks Telegram channel: https://t.me/dataleak .
')
Source: https://habr.com/ru/post/454048/
All Articles