Experiment: How to Disguise Using Tor to Bypass Locks

Internet censorship is becoming an increasingly important issue worldwide. This leads to an increase in the “arms race” - government agencies and private corporations in different countries strive to block various content and struggle with the means of circumventing such restrictions, while developers and researchers strive to create effective tools to combat censorship.
Scientists from Carnegie Mellon Universities, Stanford University and SRI International conducted an experiment in which they developed a special service to mask the use of Tor, one of the most popular tools for bypassing locks. We present you a story about the work done by researchers.
')
Tor against locks
Tor provides users anonymity by using special relays - that is, intermediate servers between the user and the site he needs. Usually there are several relays between the user and the site, each of which can decipher only a small amount of data in the packet being sent - just enough to find out the next point in the chain and send it there. As a result, even if the relay is added to the chain, controlled by hackers or censors, they will not be able to find out the destination and the destination of the traffic.
As an anti-censorship tool, Tor works efficiently, but the censors can still block it completely. Iran and China have carried out successful blocking campaigns. They were able to identify Tor traffic by scanning TLS handshakes and other distinctive features of Tor.
Subsequently, the developers managed to adapt the system to bypass the locks. Censors responded by blocking HTTPS connections to multiple sites, including Tor. Project developers have created a program obfsproxy, which additionally encrypts traffic. This competition is ongoing.
The initial data of the experiment
The researchers decided to develop a tool that would disguise the use of Tor, to make its use possible even in regions where the system is completely blocked.
- As initial assumptions, scientists have put forward the following:
- Censor controls the isolated internal network segment, which connects to the external uncensored Internet.
- The authorities involved in blocking control the entire network infrastructure within the censored network segment, but not software on end-user computers.
- The censor seeks to prevent users from accessing undesirable materials from its point of view; it is assumed that all such materials are located on servers outside the controlled network segment.
- Routers at the perimeter of this segment analyze the unencrypted data of all packets in order to block unwanted content and prevent the relevant packets from penetrating inside the perimeter.
- All Tor relays are located outside the perimeter.
How it works
To mask the use of Tor, researchers have created a StegoTorus intrument. Its main goal is to improve Tor’s ability to resist automated protocol analysis. The tool is located between the client and the first relay in the chain, uses its own encryption protocol and steganography modules to make it difficult to identify Tor traffic.
At the first step, a module called chopper comes into operation - it converts traffic into a sequence of blocks of different lengths, which are not sent in order.
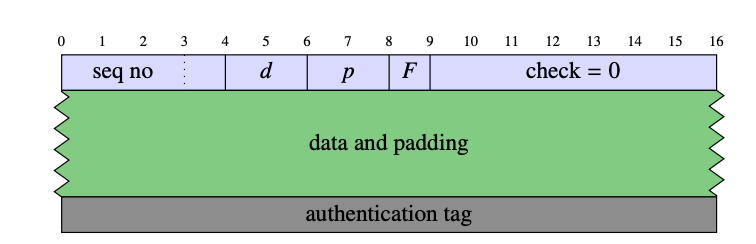
Data is encrypted using AES in GCM mode. The block header contains a 32-bit sequence number, two length fields (d and p) —they indicate the amount of data, a special field F, and a 56-bit verification field, the value of which should be zero. The minimum block length is 32 bytes, and the maximum is 217 + 32 bytes. The length is controlled by steganography modules.
When establishing a connection, the first few bytes of information are a handshake message, with its help the server understands whether it is dealing with an existing or a new connection. If the connection belongs to a new link, the server responds with a handshake, and each of the exchange participants allocates session keys from it. In addition, the system implements a mechanism for reking (rekeying) - it is similar to the allocation of the session key, but instead of handshake-messages are used blocks. This mechanism changes the sequence number, but does not touch the link ID.
After both data exchange participants have sent and received the fin block, the link is closed. To protect against replay attacks or block delivery delays, both participants must remember the ID for how long after closing.
Built-in steganography module hides Tor-traffic inside the p2p-protocol - by analogy with the work of Skype with secure VoIP-communications. HTTP steganography module simulates unencrypted HTTP traffic. The system mimics the real user with a regular browser.
Attack Resistance
In order to test how the proposed method increases the efficiency of Tor, the researchers developed two types of attacks.
The first of these is to isolate Tor streams from TCP streams based on the fundamental characteristics of the Tor protocol — this is the method used to block the Chinese power system. The second attack is to study the already known Tor streams to extract information about which sites the user has visited.
The researchers confirmed the effectiveness of the first type of attack against the "vanilla Tor" - for this they collected traces of visits to sites from the top 10 Alexa.com twenty times through the usual Tor, obfsproxy and StegoTorus with the HTTP-steganography module. As a reference, CAIDA datasets with data on port 80 were used for comparison - almost certainly all of these are HTTP connections.
The experiment showed that it is easy to calculate the usual Tor. The Tor protocol is too specific and has a number of characteristics that are easy to calculate - for example, when using it, TCP connections last 20-30 seconds. The Obfsproxy tool also almost does not hide these obvious moments. StegoTorus, in turn, generates traffic that is much closer to the CAIDA reference.

In the event of an attack, the researchers compared the likelihood of such disclosures in the case of “vanilla Tor” and their StegoTorus solutions. For evaluation, the AUC (Area Under Curve) scale was used. According to the results of the analysis, it turned out that in the case of normal Tor without additional protection, the probability of disclosing data on the visited sites is significantly higher.

Conclusion
The story of the opposition of the authorities of countries introducing censorship on the Internet, and the developers of blocking bypass systems indicates that only comprehensive protection measures can be effective. The use of only one tool cannot guarantee access to the necessary data and that information about the bypass of the lock will not be known to the censors.
Therefore, when using any tools to ensure privacy and access to content, it is important not to forget that there are no ideal solutions and, if possible, to combine different methods to achieve the greatest efficiency.
Useful links and materials from Infatica :
- Study: Creating a lock-resistant proxy service using game theory
- The story of the fight against censorship: how does the flash proxy method created by scientists from MIT and Stanford
- How to understand when a proxy is lying: verification of the physical locations of network proxies using an active geolocation algorithm
- How to disguise on the Internet: compare server and resident proxies
Source: https://habr.com/ru/post/454002/
All Articles