Security Week 22: Threat Statistics, Bank Trojans, and Popular Exploits
Last week, Kaspersky Lab published a report on the evolution of cyber threats in the first quarter of 2019. A brief overview can be found in this news, and in the post we will take a closer look at two topics: banking Trojans for Android and Windows, as well as vulnerabilities most often exploited by hackers in Windows and popular software.
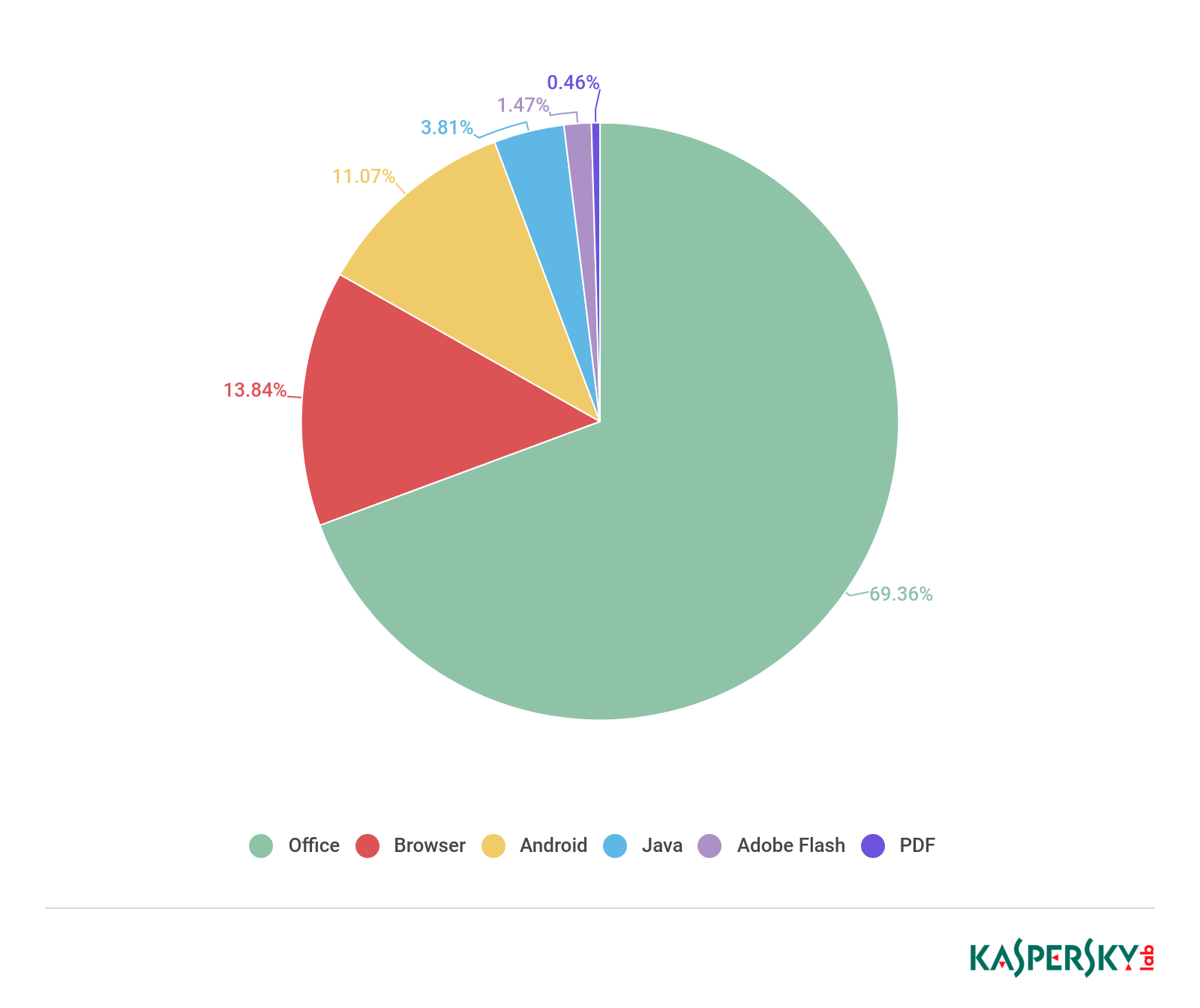
Let's start with vulnerabilities. Most often, real-world vulnerability attacks are aimed at Microsoft Office - the proportion of exploits for this office suite was 69%. Four of the most popular vulnerabilities were discovered and closed in 2017. This vulnerability is most commonly used in the Equation Editor component. It affects all versions of Office, starting from 2007 and ending with 2016, including Office 365. Despite the release of the patch as early as November 2017, cybercriminals seem to be able to find enough victims with old versions of software. It is interesting how the priorities of the attackers change depending on the popularity of this or that software, and here it makes sense to look at similar reports from previous years. Let's start from afar - from 2012.

')
In the report for 2012, a completely different picture is observed: users have a massively installed Oracle Java components and vulnerable versions of Adobe Reader and Adobe Flash. This trinity accounts for 80% of all actively used exploits. In 2014, Java is attacked frequently, but vulnerabilities in browsers come in second.

In the statistics for 2016, the share of Java and Adobe Reader is still significant, but the most popular exploits are aimed at browsers and office software. How to evaluate such changes? First of all, in such statistics, large-scale attacks are evaluated. In targeted attacks, completely different vulnerabilities can be exploited, for example, this bug in Windows itself, recently discovered. Popular exploits are chosen by cybercriminals whenever possible to put hacking computers (and for some time mobile devices on Android) onto the stream. Although you shouldn’t forget about new serious vulnerabilities, at the moment a fully patched and updated office suite and browser are the first things to worry about.

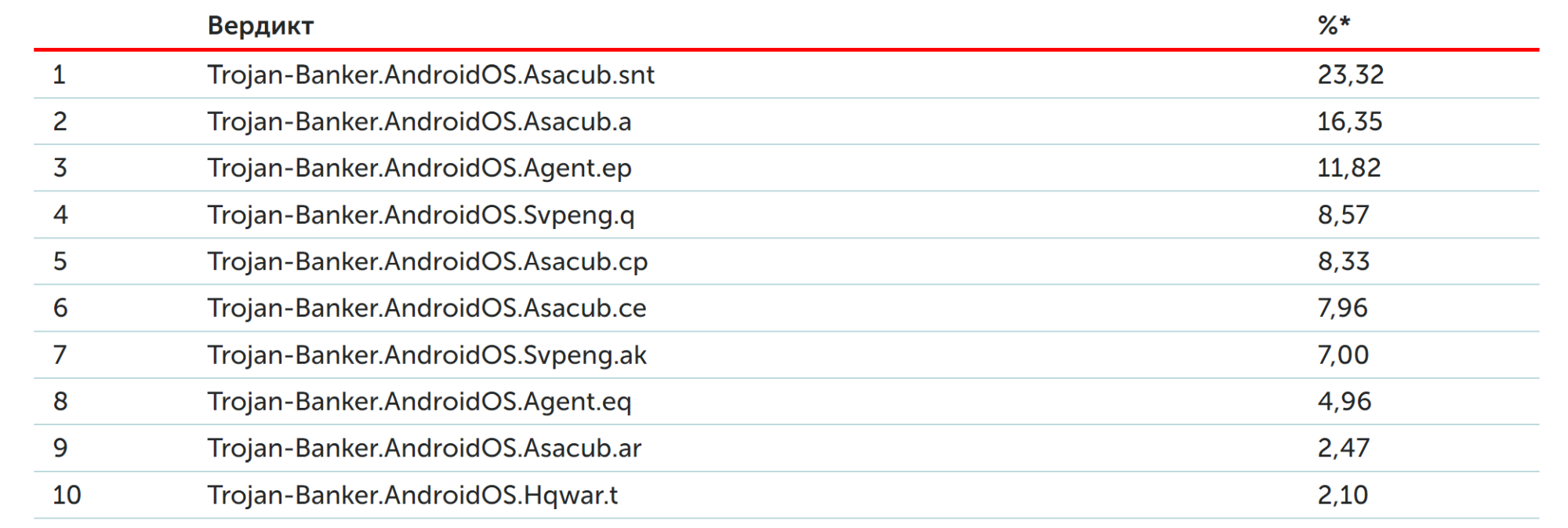
Every month, Kaspersky Lab products block tens of thousands of malicious attacks on Android devices that aim to steal money from user accounts. Relative to the total number of attacks, this is actually a bit: in Australia, 0.81% of all users were attacked in the first quarter, and this is the highest figure. In Russia, banker Trojans were blocked by 0.64% of users. Banking Trojans on desktops are more common - detected by 1-3% of users depending on the country. As usual, attention to such malware is due to immediate and sensitive financial losses in the event of a successful infection. Look at the list of the most popular malware to steal money on Android:
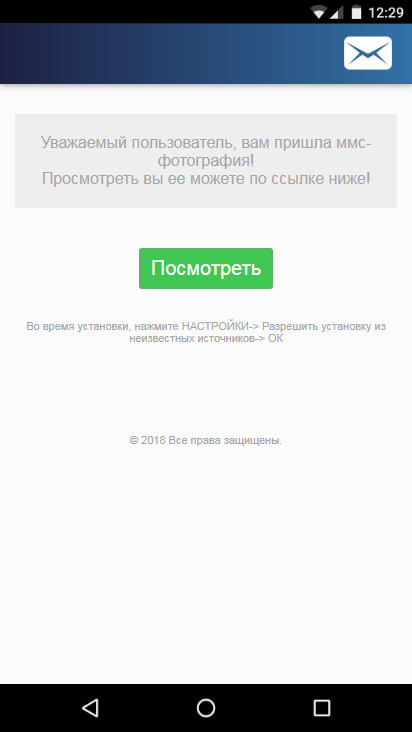
What do mobile trojans look like? Let's start with the top lines of the rating. The Asacub family is described in detail in this last article. Trojans known since 2015 are distributed via SMS and MMS messages, with a link to a page offering to view photos. Instead of a photo the installation file is downloaded.
When installing, the program asks for device administrator rights or access to the accessibility service (Accessibility Service, due to its regular misuse, applications that use it were banned on Google Play in 2017).

After installation, the trojan receives commands from the management server. Since it becomes an application for sending and receiving SMS by default, it can transfer money from the victim's account and receive confirmation codes from banks via SMS, transparent to the user. He is also able to block the launch of banking clients on a smartphone so that it is not possible to check the balance. As of August 2018, 98% of all Asacub attacks were in Russia. In the total statistics for 2018, Asacub accounted for 58% of attacks. In the second and third places are the Trojan-Banker.AndroidOS.Agent and Trojan family of banking Trojans.
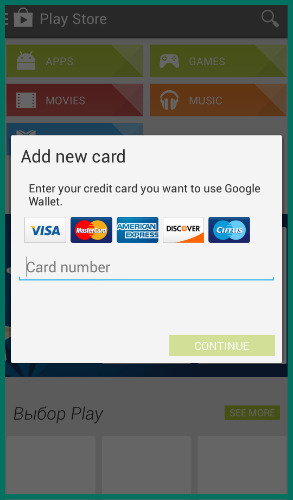
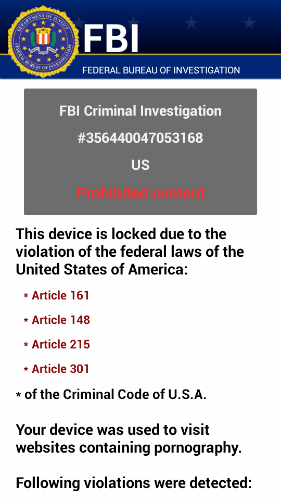
The Svpeng family exists even longer - the first mentions are from 2013 . Unlike Asacub, this malware targets users worldwide. The screenshot above shows the result of the Trojan: when you open the Google application store, its window is covered with a request to enter credit card information. In addition to stealing money directly from the accounts of the victims, some versions of the malware also extort money from the user.
Owners of traditional PCs and laptops face financial threats more often than mobile device users. On the desktop, there is a greater variety of malware, and losses in some cases may be higher. For example, the RTM banking trojan, which ranks first in its category, targets the Remote Banking Service system in enterprises. In the case of Android Trojans, the willingness of the user to recognize the threat plays an important role: for such malware often requires several permissions to obtain extended rights from the owner. To distinguish such requests from legitimate ones (which also often “pop up”) from technically unqualified owners of smartphones do not. From here and consequences: according to the Central Bank of the Russian Federation for 2017, about a billion rubles were stolen from citizens' accounts. In half of the cases, however, not technical means are used, but banal social engineering. Be carefull!
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

Let's start with vulnerabilities. Most often, real-world vulnerability attacks are aimed at Microsoft Office - the proportion of exploits for this office suite was 69%. Four of the most popular vulnerabilities were discovered and closed in 2017. This vulnerability is most commonly used in the Equation Editor component. It affects all versions of Office, starting from 2007 and ending with 2016, including Office 365. Despite the release of the patch as early as November 2017, cybercriminals seem to be able to find enough victims with old versions of software. It is interesting how the priorities of the attackers change depending on the popularity of this or that software, and here it makes sense to look at similar reports from previous years. Let's start from afar - from 2012.

')
In the report for 2012, a completely different picture is observed: users have a massively installed Oracle Java components and vulnerable versions of Adobe Reader and Adobe Flash. This trinity accounts for 80% of all actively used exploits. In 2014, Java is attacked frequently, but vulnerabilities in browsers come in second.

In the statistics for 2016, the share of Java and Adobe Reader is still significant, but the most popular exploits are aimed at browsers and office software. How to evaluate such changes? First of all, in such statistics, large-scale attacks are evaluated. In targeted attacks, completely different vulnerabilities can be exploited, for example, this bug in Windows itself, recently discovered. Popular exploits are chosen by cybercriminals whenever possible to put hacking computers (and for some time mobile devices on Android) onto the stream. Although you shouldn’t forget about new serious vulnerabilities, at the moment a fully patched and updated office suite and browser are the first things to worry about.

Every month, Kaspersky Lab products block tens of thousands of malicious attacks on Android devices that aim to steal money from user accounts. Relative to the total number of attacks, this is actually a bit: in Australia, 0.81% of all users were attacked in the first quarter, and this is the highest figure. In Russia, banker Trojans were blocked by 0.64% of users. Banking Trojans on desktops are more common - detected by 1-3% of users depending on the country. As usual, attention to such malware is due to immediate and sensitive financial losses in the event of a successful infection. Look at the list of the most popular malware to steal money on Android:

What do mobile trojans look like? Let's start with the top lines of the rating. The Asacub family is described in detail in this last article. Trojans known since 2015 are distributed via SMS and MMS messages, with a link to a page offering to view photos. Instead of a photo the installation file is downloaded.

When installing, the program asks for device administrator rights or access to the accessibility service (Accessibility Service, due to its regular misuse, applications that use it were banned on Google Play in 2017).

After installation, the trojan receives commands from the management server. Since it becomes an application for sending and receiving SMS by default, it can transfer money from the victim's account and receive confirmation codes from banks via SMS, transparent to the user. He is also able to block the launch of banking clients on a smartphone so that it is not possible to check the balance. As of August 2018, 98% of all Asacub attacks were in Russia. In the total statistics for 2018, Asacub accounted for 58% of attacks. In the second and third places are the Trojan-Banker.AndroidOS.Agent and Trojan family of banking Trojans.

The Svpeng family exists even longer - the first mentions are from 2013 . Unlike Asacub, this malware targets users worldwide. The screenshot above shows the result of the Trojan: when you open the Google application store, its window is covered with a request to enter credit card information. In addition to stealing money directly from the accounts of the victims, some versions of the malware also extort money from the user.

Owners of traditional PCs and laptops face financial threats more often than mobile device users. On the desktop, there is a greater variety of malware, and losses in some cases may be higher. For example, the RTM banking trojan, which ranks first in its category, targets the Remote Banking Service system in enterprises. In the case of Android Trojans, the willingness of the user to recognize the threat plays an important role: for such malware often requires several permissions to obtain extended rights from the owner. To distinguish such requests from legitimate ones (which also often “pop up”) from technically unqualified owners of smartphones do not. From here and consequences: according to the Central Bank of the Russian Federation for 2017, about a billion rubles were stolen from citizens' accounts. In half of the cases, however, not technical means are used, but banal social engineering. Be carefull!
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/453686/
All Articles