19% of the most popular Docker images have no root password.
Last Saturday, May 18, Jerry Gamblin from Kenna Security checked 1000 of the most popular Docker Hub images on the root password used in them. In 19% of cases he was absent.
The reason for the mini-study was the Talos Vulnerability Report ( TALOS-2019-0782 ), which appeared earlier this month, the authors of which — thanks to a finding by Peter Adkins of Cisco Umbrella — reported that the Docker images with the popular distribution for Alpine containers do not have a password for root:
')
The proven versions of the Docker images with Alpine were 3.3-3.9 inclusive, as well as the latest release of edge.
The authors gave the following recommendation to users affected by the problem:
The problem was fixed in Alpine versions 3.6.5, 3.7.3, 3.8.4, 3.9.2 and edge (20190228 snapshot), and the owners of exposed images were asked to comment out the root line in
Jerry Gamblin decided to inquire, "how common the practice of using null passwords in containers can be." To do this, he wrote a small Bash script , the essence of which is quite simple:
What happened? This file contains 194 lines with the names of popular Docker images with Linux systems, where the root user does not have a password set:
It should, however, be recalled that this phenomenon in itself does not mean a direct vulnerability in the security of the systems that use them: it all depends on how they are used (see the comment from the case of Alpine above) . However, we have already seen the “morality of this fable” many times: apparent simplicity often has a downside, which must always be remembered and the consequences of which should be taken into account in our application scenarios of technology.
Read also in our blog:

Background with Alpine
The reason for the mini-study was the Talos Vulnerability Report ( TALOS-2019-0782 ), which appeared earlier this month, the authors of which — thanks to a finding by Peter Adkins of Cisco Umbrella — reported that the Docker images with the popular distribution for Alpine containers do not have a password for root:
')
“The official versions of the Alpine Linux Docker image (starting with v3.3) contain the NULL password for the root user. This vulnerability resulted from the regression presented in December 2015. Its essence is that systems deployed with problem versions of Alpine Linux in a container and using Linux PAM or another mechanism that uses the system shadow file as a database for authentication can accept a zero (NULL) password for the root user. ”
The proven versions of the Docker images with Alpine were 3.3-3.9 inclusive, as well as the latest release of edge.
The authors gave the following recommendation to users affected by the problem:
“The root account must be explicitly disabled in Docker images compiled on the basis of problematic versions of Alpine. The probable exploitation of the vulnerability depends on the environment, since its success requires an outside service or application that uses Linux PAM or another similar mechanism. ”
The problem was fixed in Alpine versions 3.6.5, 3.7.3, 3.8.4, 3.9.2 and edge (20190228 snapshot), and the owners of exposed images were asked to comment out the root line in
/etc/shadow or make sure that the linux-pam package is missing linux-pam .Continued with Docker Hub
Jerry Gamblin decided to inquire, "how common the practice of using null passwords in containers can be." To do this, he wrote a small Bash script , the essence of which is quite simple:
- via Docker Hub, through a curl request to the API, a list of the Docker images placed there is requested;
- via jq, it is sorted by the field of
popularity, and the first thousand of the results obtained remain; - for each of them
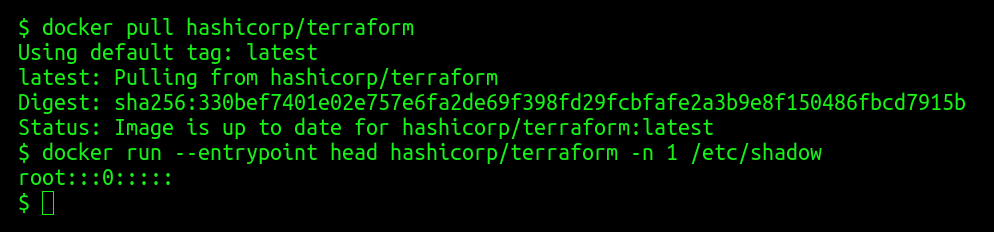
docker pullis performed; - For each image received from the Docker Hub, a
docker runis performed with reading the first line from the/etc/shadowfile; - if the string value is equal to
root:::0:::::, the name of the image is saved to a separate file.
What happened? This file contains 194 lines with the names of popular Docker images with Linux systems, where the root user does not have a password set:
“Among the most famous names in this list were the govuk / governmentpaas, hashicorp, microsoft, monsanto and mesosphere. And kylemanna / openvpn is the most popular container from the list, its statistics has more than 10 million pull'ov.
It should, however, be recalled that this phenomenon in itself does not mean a direct vulnerability in the security of the systems that use them: it all depends on how they are used (see the comment from the case of Alpine above) . However, we have already seen the “morality of this fable” many times: apparent simplicity often has a downside, which must always be remembered and the consequences of which should be taken into account in our application scenarios of technology.
PS
Read also in our blog:
Source: https://habr.com/ru/post/452754/
All Articles