Two in one: tourist data and tickets for cultural events were publicly available.
Today we will consider two cases at once - the data of clients and partners of two completely different companies were freely available “thanks to” open Elasticsearch servers with logs of information systems (IS) of these companies.

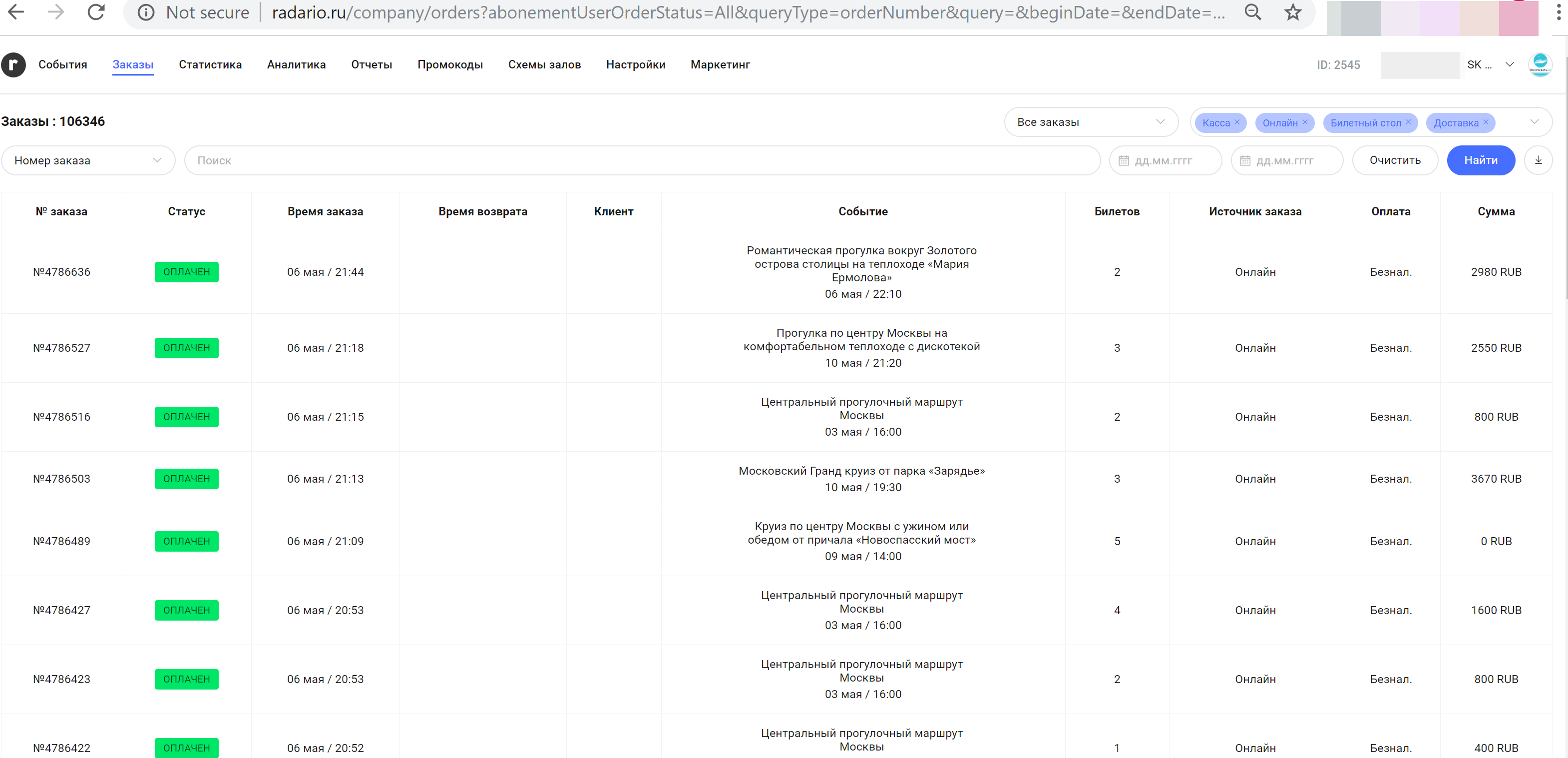
In the first case, these are tens of thousands (and maybe hundreds of thousands) of tickets to various cultural events (theaters, clubs, river walks, etc.) sold through the Radario system ( www.radario.ru ).
In the second case, these are data on tourist travels of thousands (possibly several tens of thousands) of travelers who bought tours through travel agencies connected to the Sletat.ru system ( www.sletat.ru ).
Immediately, I note that not only the names of the companies that made the data publicly available differ, but also the approach of these companies to the recognition of the incident and the subsequent reaction to it. But first things first…
: . . , .
The first case. "Radar"
On the evening of May 6, 2019 , our system discovered the Elasticsearch server , which belongs to the Radario e-ticket service, in the public domain .
According to the already established sad tradition, the server contained detailed logs of the information system of the service, from which it was possible to obtain personal data, user names and passwords, as well as the e-tickets themselves for various events throughout the country.
The total amount of logs exceeded 1 TB.
According to the search engine Shodan, the server was openly accessible from 11.03.2019. I notified the staff of “Radario” on 06/05/2019 at 22:50 (MSK) and on 07/05/2019 around 09:30 the server became unavailable.
In the logs there was a universal (single) authorization token, which provides access to all tickets purchased through special links, like:
http://radario.ru/internal/tickets/XXXXXXXX/print?access_token=******JuYWw6MDIzOWRjOTM1NzJiNDZjMTlhZGFjZmRhZTQ3ZDgyYTk http://radario.ru/internal/orders/YYYYYYY/print?access_token=******JuYWw6MDIzOWRjOTM1NzJiNDZjMTlhZGFjZmRhZTQ3ZDgyYTk The problem also lay in the fact that ticket counts were used for numbering orders and simply looked through the ticket number ( XXXXXXXX ) or order ( YYYYYYY ), it was possible to get all the tickets from the system.
To check the relevance of the database, I even honestly bought myself the cheapest ticket:


and later found it on a public server in the IP logs:
http://radario.ru/internal/tickets/11819272/print?access_token==******JuYWw6MDIzOWRjOTM1NzJiNDZjMTlhZGFjZmRhZTQ3ZDgyYTk Separately, I would like to emphasize that the tickets were available both for events that have already taken place and for those that are still being planned. That is, a potential attacker could use someone else's ticket for the passage to the planned event.
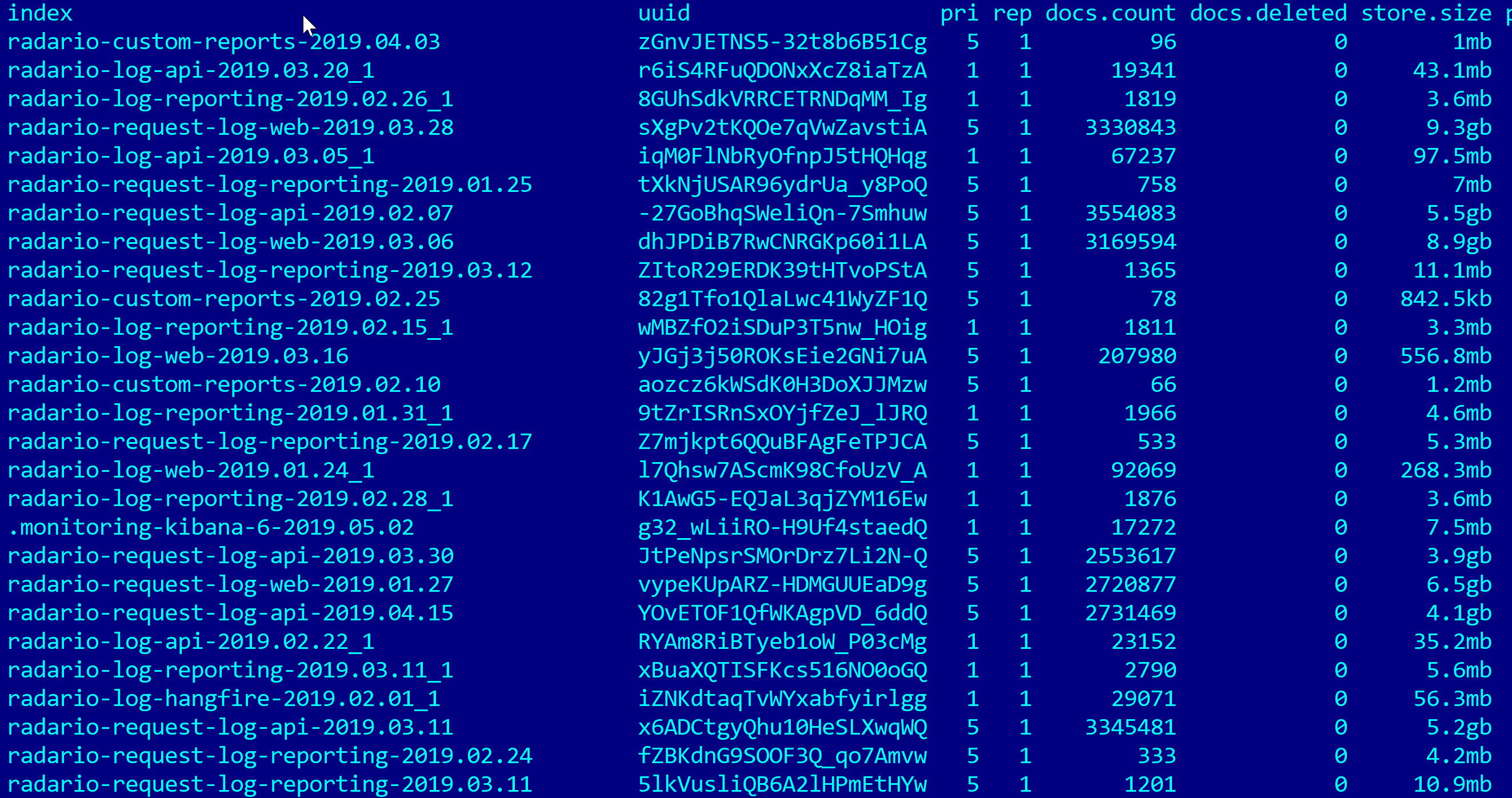
On average, each Elasticsearch index containing logs for one specific day (starting from January 24, 2019 and May 7, 2019) contained from 25 to 35 thousand tickets.
In addition to the tickets themselves, the index contained logins (email addresses) and text passwords for access to the private offices of Radario partners selling tickets to their events through this service:
Content: \"ReturnUrl=&UserEmail=***@yandex.ru&UserPassword=***\" In total, more than 500 login / password pairs were detected. Ticket sales statistics are visible in the partners' personal accounts:
Also in open access were the names, phone numbers and e-mail addresses of buyers who decided to return, tickets purchased earlier:
"Content": "{\"name\":\"***\",\"surname\":\"*** \",\"middleName\":\" \",\"passportType\":1,\"passportNumber\":\"\",\"passportIssueDate\":\"11-11-2011 11:11:11\",\"passportIssuedBy\":\"\",\"email\":\"***@mail.ru\",\"phone\":\"+799*******\",\"ticketNumbers\":[\"****24848\",\"****948732\"],\"refundReason\":4,\"comment\":\"\"}" In one randomly chosen day, more than 500 such records were found.
I received a response to the alert from the Technical Director of Radario:
I am the technical director of Radario, and I would like to thank you for finding the problem. Access to the elastic, as you know, we have closed and are resolving the issue of reissuing tickets for customers.
A little later, the company made an official statement:
In the electronic ticket sales system Radario, a vulnerability was discovered and promptly eliminated, which could lead to a leak of customer service data, Kirill Malyshev, marketing director of the company, told the Moscow City News Agency.
“We really discovered a vulnerability in the operation of the system associated with regular updates, which was fixed immediately after detection. As a result of vulnerability, under certain conditions, unfriendly actions of third parties could lead to data leakage, but no incidents were recorded. At the moment, all malfunctions have been resolved, ”said K. Malyshev.
The representative of the company stressed that it was decided to reissue all tickets sold during the resolution of the problem in order to completely eliminate the possibility of any fraud against the clients of the service.
A few days later, I checked the availability of data on the leaked links - access to the "illuminated" tickets was really covered. In my opinion, this is a competent, professional approach to solving data leakage problems.
Case two. "Sletat.ru"
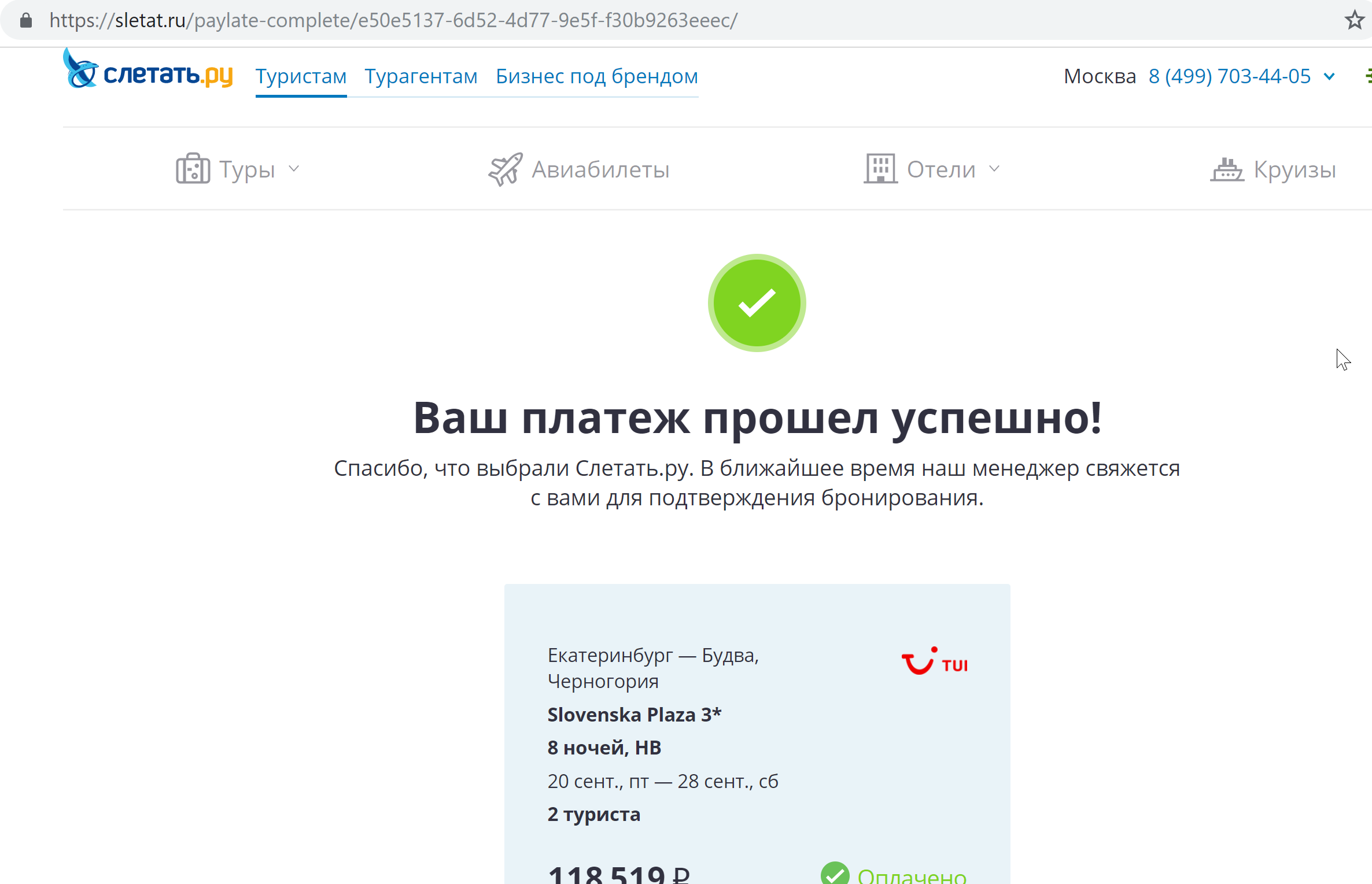
Early in the morning of May 15, 2019, DeviceLock Data Breach Intelligence revealed a publicly accessible Elasticsearch server with some IP logs.

Later it was found that the server belongs to the service for the selection of tours "Fly.ru".
From the cbto__0 index , it was possible to get thousands (11.7 thousand including duplicates) of email addresses, as well as some payment information (cost of tours) and tour data (when, where, air ticket data of all travelers included in the tour, etc. ) in the amount of about 1.8 thousand records:
"full_message": " : {\"SuccessReturnUrl\":\"https://sletat.ru/tour/7-1939548394-65996246/buy/?ClaimId=b5e3bf98-2855-400d-a93a-17c54a970155\",\"ErrorReturnUrl\":\"https://sletat.ru/\",\"PaymentAgentId\":15,\"DocumentNumber\":96629429,\"DocumentDisplayNumber\":\"4451-17993\",\"Amount\":36307.0,\"PaymentToolType\":3,\"ExpiryDateUtc\":\"2020-04-03T00:33:55.217358+03:00\",\"LifecycleType\":2,\"CustomerEmail\":\"XXX@mail.ru\",\"Description\":\"\",\"SettingsId\":\"8759d0dd-da54-45dd-9661-4e852b0a1d89\",\"AdditionalInfo\":\"{\\\"TourOfficeAdditionalInfo\\\":{\\\"IsAdditionalPayment\\\":false},\\\"BarrelAdditionalInfo\\\":{\\\"Tickets\\\":[{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX VIKTORIIA\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false},{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX ANDREI\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false},{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX Andrei\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false}],\\\"Segments\\\":[{\\\"Flight\\\":\\\"5659\\\",\\\"AviaCompany\\\":null,\\\"AviaCompanyIataCode\\\":null,\\\"DepartureCity\\\":\\\"LED\\\",\\\"DepartureAirport\\\":\\\"LED\\\",\\\"DepartureAirportIataCode\\\":\\\"LED\\\",\\\"DepartureDate\\\":\\\"2019-04-11T02:45:00\\\",\\\"DepartureTime\\\":null,\\\"ArrivalCity\\\":\\\"SHJ\\\",\\\"ArrivalAirport\\\":\\\"SHJ\\\",\\\"ArrivalAirportIataCode\\\":\\\"SHJ\\\",\\\"ArrivalDate\\\":\\\"2019-04-11T09:40:00\\\",\\\"ArrivalTime\\\":null,\\\"FareCode\\\":null},{\\\"Flight\\\":\\\"5660\\\",\\\"AviaCompany\\\":null,\\\"AviaCompanyIataCode\\\":null,\\\"DepartureCity\\\":\\\"SHJ\\\",\\\"DepartureAirport\\\":\\\"SHJ\\\",\\\"DepartureAirportIataCode\\\":\\\"SHJ\\\",\\\"DepartureDate\\\":\\\"2019-04-14T10:45:00\\\",\\\"DepartureTime\\\":null,\\\"ArrivalCity\\\":\\\"LED\\\",\\\"ArrivalAirport\\\":\\\"LED\\\",\\\"ArrivalAirportIataCode\\\":\\\"LED\\\",\\\"ArrivalDate\\\":\\\"2019-04-14T15:50:00\\\",\\\"ArrivalTime\\\":null,\\\"FareCode\\\":null}]},\\\"Tickets\\\":[{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX VIKTORIIA\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false},{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX ANDREI\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false},{\\\"Passenger\\\":{\\\"FIO\\\":\\\"XXX Andrei\\\"},\\\"ReservationSystem\\\":null,\\\"TicketNumber\\\":null,\\\"IsRefundPossible\\\":false}],\\\"Segments\\\":[{\\\"Flight\\\":\\\"5659\\\",\\\"AviaCompany\\\":null,\\\"AviaCompanyIataCode\\\":null,\\\"DepartureCity\\\":\\\"LED\\\",\\\"DepartureAirport\\\":\\\"LED\\\",\\\"DepartureAirportIataCode\\\":\\\"LED\\\",\\\"DepartureDate\\\":\\\"2019-04-11T02:45:00\\\",\\\"DepartureTime\\\":null,\\\"ArrivalCity\\\":\\\"SHJ\\\",\\\"ArrivalAirport\\\":\\\"SHJ\\\",\\\"ArrivalAirportIataCode\\\":\\\"SHJ\\\",\\\"ArrivalDate\\\":\\\"2019-04-11T09:40:00\\\",\\\"ArrivalTime\\\":null,\\\"FareCode\\\":null},{\\\"Flight\\\":\\\"5660\\\",\\\"AviaCompany\\\":null,\\\"AviaCompanyIataCode\\\":null,\\\"DepartureCity\\\":\\\"SHJ\\\",\\\"DepartureAirport\\\":\\\"SHJ\\\",\\\"DepartureAirportIataCode\\\":\\\"SHJ\\\",\\\"DepartureDate\\\":\\\"2019-04-14T10:45:00\\\",\\\"DepartureTime\\\":null,\\\"ArrivalCity\\\":\\\"LED\\\",\\\"ArrivalAirport\\\":\\\"LED\\\",\\\"ArrivalAirportIataCode\\\":\\\"LED\\\",\\\"ArrivalDate\\\":\\\"2019-04-14T15:50:00\\\",\\\"ArrivalTime\\\":null,\\\"FareCode\\\":null}]}\",\"FinancialSystemId\":9,\"Key\":\"18fe21d1-8c9c-43f3-b11d-6bf884ba6ee0\"}" By the way, links to paid tours are quite working:
In the indices with the name graylog_ in the open form were the logins and passwords of travel agencies connected to the system “Fly.ru” and selling tours to their customers:
"full_message": "Tours by request 155213901 added to local cache with key 'user_cache_155213901' at 5/6/2019 4:49:07 PM, rows found 0, sortedPriceLength 215. QueryString: countryId=90&cityFromId=1265&s_nightsMin=6&s_nightsMax=14&stars=403%2c404&minHotelRating=1¤cyAlias=RUB&pageSize=300&pageNumber=1&s_showcase=true&includeOilTaxesAndVisa=0&login=zakaz%40XXX.ru&password=XXX, Referer: , UserAgent: , IP: 94.154.XX.XX." According to my estimations, several hundred login / password pairs appeared.
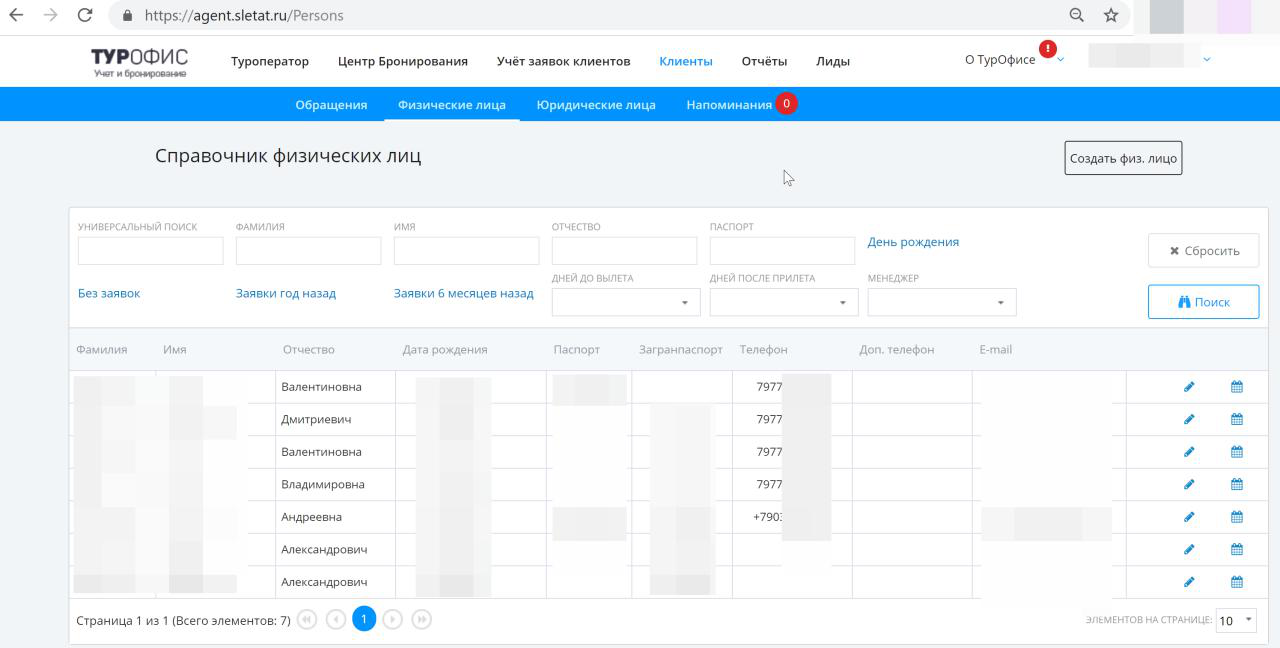
From the personal office of the travel agency on the agent.sletat.ru portal , it was possible to obtain customer data, including passport numbers, passport numbers, birth dates, name, phone numbers and email addresses.
I notified the service “Sletat.ru” on 05/15/2019 at 10:46 (MSK) and after several hours (until 16:00) the Elasticsearch server disappeared from free access. Later, in response to the publication in Kommersant, the management of the service made a very strange statement through the media:
The head of the company, Andrey Vershinin, explained that “Sletat.ru” provides a number of the largest tour operators-partners with access to the search history of queries. And I assumed that DeviceLock received it: “However, in this database there are no passport data of tourists, logins and passwords of travel agencies, billing data, etc.”. Andrei Vershinin noted that so far no evidence of such serious accusations against Sletat.ru has been received. “Now we are trying to contact DeviceLock. We believe that this zakazuha. Some people do not like our rapid growth, ”he added. "
As shown above, both logins, passwords, and passport data of tourists were freely available for quite a long time (at least from 03/29/2019, when the company's server was first recorded in the public domain by the search engine Shodan). Of course, no one contacted us. I hope that, at least they informed the travel agencies about the leak and forced them to change their passwords.
News about information leaks and insiders can always be found on my Information Leaks Telegram channel.
')
Source: https://habr.com/ru/post/452698/
All Articles