Security Week 21: a hole in Whatsapp, a new vulnerability in Intel processors, Zero-Day in Windows
Last week, three interesting information security events took place: an exploitable vulnerability in Whatsapp was closed, for critical vulnerabilities in Windows, patches were released even for unsupported OS versions, and another Specter-like problem was found in Intel processors. Let's start with a vulnerability in the Remote Desktop Services component ( news , post on a Microsoft blog). Technical details of the vulnerability are not disclosed, but it is known that the bug allows you to gain control over the system using the RDP protocol without authorization.

Vulnerabilities are affected by Windows 7 and Windows 2008 Server, as well as unsupported Windows XP and Windows 2003 Server. The article by Brian Krebs points out the similarity of the vulnerability with the EternalBlue bug in the SMB protocol, which in 2017 led to a large-scale epidemic of the WannaCry Trojan cipher. In this case, the attacker can gain access to any unpatched system accessible via the RDP protocol and, through it, extend the attack to other computers on the local network. Despite the prompt release of the patch, we will most likely hear about the consequences of exploiting this bug.
To reduce the likelihood of a large-scale attack, Microsoft released patches for Windows XP and 2003 Server, which are not officially supported by the company. On May 14, Microsoft closed several other vulnerabilities, including the critical CVE-2019-0863 bug in Windows Error Reporting. Unlike the problem in RDP, this vulnerability affects modern versions of the OS up to Windows 10 and can be used to escalate privileges. This vulnerability is actively exploited by hackers.
The most discussed incident of last week was a report of a serious vulnerability in Whatsapp messenger ( news ). Vulnerability CVE-2019-3568 was closed by the Whatsapp update for Android and iOS on May 13 . Interestingly, in the announcement of the new version for Android, the main change does not indicate a patch at all, but “displaying stickers on full screen”:
')
In the discussion, it was noted that ordinary users would rather update the client because of the stickers, but few people think about security yet. Check Point Software analyzed the patch and found a couple of new checks on the size of the SRTCP packets used for Internet telephony. Apparently, the absence of these checks caused a buffer overflow. But what happened next - no one knows, we can only assume getting control over the application and exfiltration of data. But there was a lot of talk about the source of the exploit.
According to the Financial Times, active exploitation of the exploit was noticed at the same time on Facebook (the current owner of the messenger) and in the human rights organization Citizen Lab. At last, a British lawyer contacted who received several video calls from unknown numbers on an Apple phone with an installed messenger. To exploit the vulnerability, you need to send a specially prepared data packet to the addressee that the WhatsApp client perceives as a video call. Answer the call is not required. According to the Financial Times, the vulnerability was found by the NSO Group, which specializes in selling exploits to government agencies and special services. Identify the developer failed by metadata.
An interesting development of the history was the post of the founder of the Telegram messenger Pavel Durov ( original , Habré translation ) entitled “Why WhatsApp will never be safe.” How safe Telegram itself is also a subject for discussion, both technical and emotional. But this is not the case: Durov's post is an example of how security becomes an advertising tool. An advantage (real or imaginary) that a significant part of the target audience considers important. This is good news: if the market players somehow have to advertise their services as being protected from hacking, sooner or later they will really need to do something in this direction .
We will complete the news review with four new attacks from third-party channels ( news ). Corresponding vulnerabilities were found in Intel processors, they were discovered during internal checks at the company itself (for a detailed article on the Intel website), as well as by researchers at the Technical University in Graz in Austria (mini-site with the “talking” URL cpu.fail ).
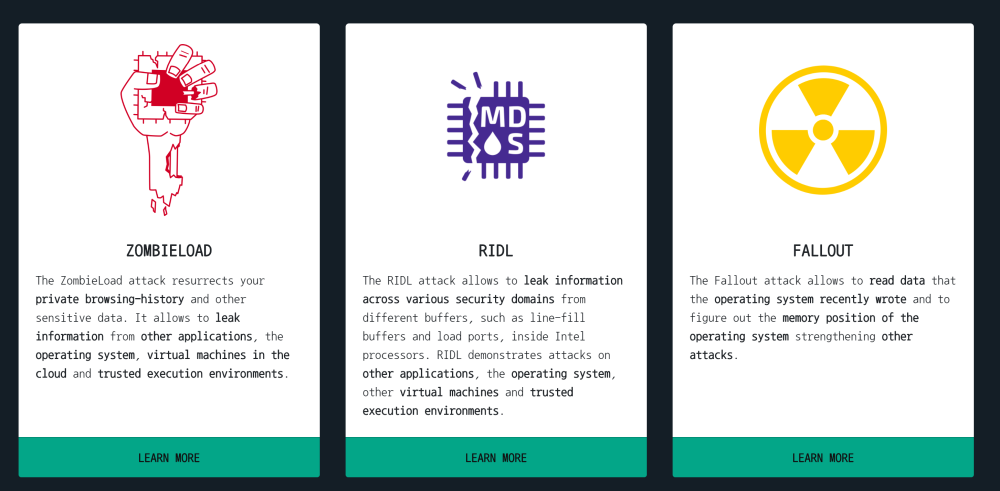
Independent researchers identified four attack vectors, and each set a realistic scenario for obtaining any data of interest to the attacker. In the case of an attack, Zombieload is the browsing history of the browser. The RIDL attack allows you to pull out secrets from applications or virtual machines running on the system. The Fallout attack can only strengthen other attacks, obtaining information about the reading of data previously recorded in the memory by the operating system. Finally, the Store-to-leak Forwarding method can theoretically be used to bypass the ASLR.
Intel is trying not to adopt creative (and slightly frightening) names of attacks and call them a complex micro-architectural data sampling. The MDS technique allows the local process to read inaccessible data from memory using the same method of attacks on third-party channels as the previously discovered Specter family. Intel promises to close vulnerabilities in the following revisions of processors, and 8th and 9th generation CPUs are not partially affected by this attack. For the rest of the processors, a microcode update will be released, and for additional security from the (yet theoretical) threat, as usual, you will have to pay with a drop in performance .
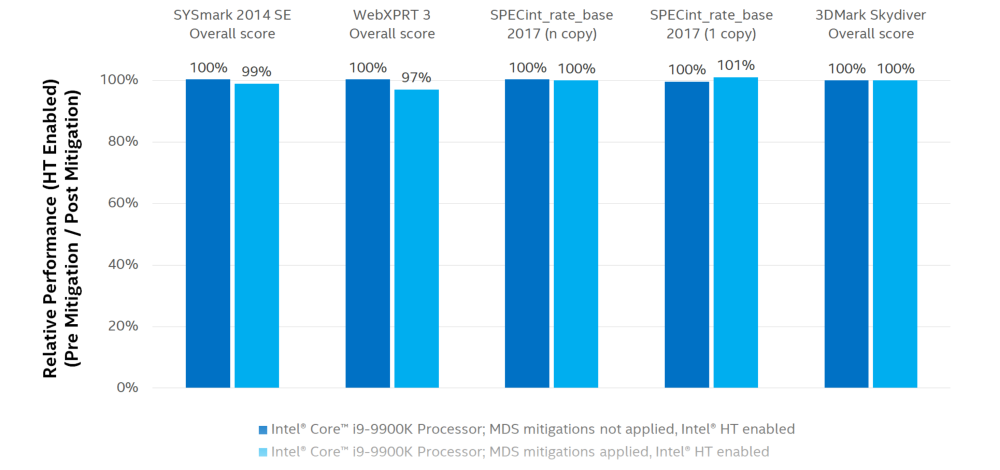
According to Intel, this is a few percent, but the very fact of determining the price of security, which we all will have to pay, is interesting here.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

Vulnerabilities are affected by Windows 7 and Windows 2008 Server, as well as unsupported Windows XP and Windows 2003 Server. The article by Brian Krebs points out the similarity of the vulnerability with the EternalBlue bug in the SMB protocol, which in 2017 led to a large-scale epidemic of the WannaCry Trojan cipher. In this case, the attacker can gain access to any unpatched system accessible via the RDP protocol and, through it, extend the attack to other computers on the local network. Despite the prompt release of the patch, we will most likely hear about the consequences of exploiting this bug.
To reduce the likelihood of a large-scale attack, Microsoft released patches for Windows XP and 2003 Server, which are not officially supported by the company. On May 14, Microsoft closed several other vulnerabilities, including the critical CVE-2019-0863 bug in Windows Error Reporting. Unlike the problem in RDP, this vulnerability affects modern versions of the OS up to Windows 10 and can be used to escalate privileges. This vulnerability is actively exploited by hackers.
The most discussed incident of last week was a report of a serious vulnerability in Whatsapp messenger ( news ). Vulnerability CVE-2019-3568 was closed by the Whatsapp update for Android and iOS on May 13 . Interestingly, in the announcement of the new version for Android, the main change does not indicate a patch at all, but “displaying stickers on full screen”:
')
In the discussion, it was noted that ordinary users would rather update the client because of the stickers, but few people think about security yet. Check Point Software analyzed the patch and found a couple of new checks on the size of the SRTCP packets used for Internet telephony. Apparently, the absence of these checks caused a buffer overflow. But what happened next - no one knows, we can only assume getting control over the application and exfiltration of data. But there was a lot of talk about the source of the exploit.
According to the Financial Times, active exploitation of the exploit was noticed at the same time on Facebook (the current owner of the messenger) and in the human rights organization Citizen Lab. At last, a British lawyer contacted who received several video calls from unknown numbers on an Apple phone with an installed messenger. To exploit the vulnerability, you need to send a specially prepared data packet to the addressee that the WhatsApp client perceives as a video call. Answer the call is not required. According to the Financial Times, the vulnerability was found by the NSO Group, which specializes in selling exploits to government agencies and special services. Identify the developer failed by metadata.
An interesting development of the history was the post of the founder of the Telegram messenger Pavel Durov ( original , Habré translation ) entitled “Why WhatsApp will never be safe.” How safe Telegram itself is also a subject for discussion, both technical and emotional. But this is not the case: Durov's post is an example of how security becomes an advertising tool. An advantage (real or imaginary) that a significant part of the target audience considers important. This is good news: if the market players somehow have to advertise their services as being protected from hacking, sooner or later they will really need to do something in this direction .
We will complete the news review with four new attacks from third-party channels ( news ). Corresponding vulnerabilities were found in Intel processors, they were discovered during internal checks at the company itself (for a detailed article on the Intel website), as well as by researchers at the Technical University in Graz in Austria (mini-site with the “talking” URL cpu.fail ).

Independent researchers identified four attack vectors, and each set a realistic scenario for obtaining any data of interest to the attacker. In the case of an attack, Zombieload is the browsing history of the browser. The RIDL attack allows you to pull out secrets from applications or virtual machines running on the system. The Fallout attack can only strengthen other attacks, obtaining information about the reading of data previously recorded in the memory by the operating system. Finally, the Store-to-leak Forwarding method can theoretically be used to bypass the ASLR.
Intel is trying not to adopt creative (and slightly frightening) names of attacks and call them a complex micro-architectural data sampling. The MDS technique allows the local process to read inaccessible data from memory using the same method of attacks on third-party channels as the previously discovered Specter family. Intel promises to close vulnerabilities in the following revisions of processors, and 8th and 9th generation CPUs are not partially affected by this attack. For the rest of the processors, a microcode update will be released, and for additional security from the (yet theoretical) threat, as usual, you will have to pay with a drop in performance .

According to Intel, this is a few percent, but the very fact of determining the price of security, which we all will have to pay, is interesting here.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/452652/
All Articles