News of the week: Offline Runet Control Center, Bitcoin at $ 8,000, Vulnerability in Intel Processors

In this digest read:
- rules of operation of the Autonomous Runet Monitoring and Management Center;
- Russian government agencies worked 9 years under the supervision of the Chinese;
- Bitcoin increased from $ 5,000 to $ 8,000;
- during the year the number of attacks on sites increased by 60%;
- Intel found four critical vulnerabilities;
- another version of the key to the Voynich manuscript.
The principle of operation of the Center for Monitoring and Control of Autonomous Runet
Earlier this week, the official legal information portal published a government decree “On approving the Rules for granting from the federal budget subsidies for the establishment and operation of the Center for Monitoring and Managing a Public Communication Network, as well as creating, operating and developing an information system for monitoring and managing a public communication network ".
')
The document describes the nuances of the work of the Center, as well as sources of funding. The center will create and support the operation of information systems for monitoring traffic routes on the Internet, monitoring and managing a public telecommunications network, and filtering Internet traffic when children use websites. In 2019, a subsidy of 100 million rubles was allocated to finance the organization.
Russian structures have worked for nine years under the supervision of Chinese cybercriminals
Two companies at once, Positive Technologies and Kaspersky Lab, announced the discovery of a cyber group, which in several years successfully attacked more than 30 Russian companies and government agencies. Presumably, the group operates from China .
In most cases, team members used a similar work scenario. The first stage was the formation of a specific task in the task scheduler. Then, specialized OS and software commands were launched, which made it possible to penetrate into the organization’s network. How cybercriminals used the information received is unclear.
In five days, Bitcoin went up from $ 6,000 to $ 8,000
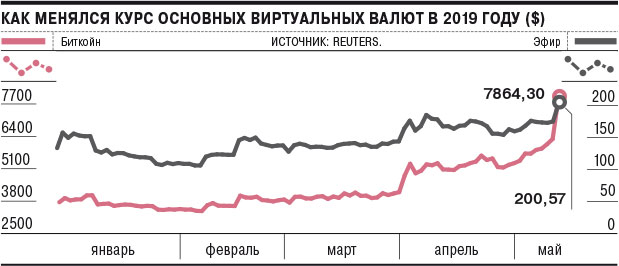
In just a few days, Bitcoin rose from $ 6,000 to $ 8,000 , and unexpectedly for many. And this is not a short-term leap, because the value of Bitcoin does not fall. The reasons for the growth are unclear. Perhaps positive news served as a stimulus for growth.
Bitcoin growth is part of a wider cryptocurrency boom. Last Saturday, the price of ether (Ethereum) for the first time in 2019 rose above $ 200. Other cryptocurrencies, including Litecoin, Bitcoin Cash, Monero and Dash, are at or near the highs of 2019.
The number of malicious attacks on websites increased by 60% over the year.

Analysts estimate that last year attackers attacked 62 sites per day, the total number of attacks increased by almost 60% compared to 2017. At the same time, infected sites occupy only 1% of all existing sites. In absolute terms, this figure is more impressive - the fact is that malicious activity is seen on 17.6 million resources.
Nevertheless, webmasters of many resources continue to neglect the basics of security, apparently considering that search engines will warn the owner about the threat. But in fact, this is not always the case.
The most vulnerable are sites with common CMS like WordPress and Drupal. According to analysts, serious gaps like XSS or CSRF, vulnerabilities to SQL injections are on 20% of WordPress sites and 15% of resources based on CMS Joomla. In the case of Drupal, this figure was only 2%, but in this system most of the kernel vulnerabilities - such problems were found in 34% of Drupal-sites.
Critical vulnerabilities in Intel processors
In many media , information appeared about four new vulnerabilities in Intel processors . They give attackers the ability to steal user data. You can fix the problem, although it is quite difficult - you need to update the processor microcode, releasing patches for operating systems. In this case, the correction may lead to a drop in PC performance by up to 40%.
Official Vulnerability Codes - CVE-2018-12126: Microarchitectural Data Sampling (Microarchitectural Store Buffer Data Sampling); CVE-2018-12130: Microarchitectural Fetching Data Buffer (Microarchitectural Fill Buffer Data Sampling); CVE-2018-12127: microarchitectural sampling of data loading port (Microarchitectural Load Port Data Sampling); CVE-2019-11091: Microarchitectural Data Sampling Uncacheable Memory. The names are given for a reason, they indicate which element of the processor can be attacked.
Linguist found the key to the Voynich manuscript

And again the news about the Voynich manuscript is one of the most mysterious in the whole history. At the end of April, linguist Gerard Cheshire of the University of Bristol published an article that describes the language system of the document . The scientist believes that the language of the manuscript is Proto-Roman, enumerating the characteristic features of the language and individual fragments of the manuscript as evidence.
According to the researcher, the language was distinguished by a complex sound system, had no punctuation marks in their classical form, and was heavily influenced by Latin. The focus of the article is on the writing system and identifying links with other languages, which should confirm the hypothesis of the Proto-Romanesque origin of the text.
Source: https://habr.com/ru/post/452382/
All Articles