So what will happen with authentication and passwords? The second part of the Javelin Strong Authentication Status Report

Recently, the research company Javelin Strategy & Research published a report on The State of Strong Authentication 2019. Its creators gathered information about what authentication methods are used in the corporate environment and user applications, and also made interesting conclusions about the future of strong authentication.
Translation of the first part with the conclusions of the authors of the report, we have already published on Habré . And now we present to your attention the second part - with data and graphs.
From translator
I will not completely copy the entire block of the same name from the first part, but I will duplicate one paragraph.
')
All the facts and figures are given without any changes, and if you disagree with them, then it’s better not to argue with the translator, but with the authors of the report. But my comments (made up as quotations, and in the text are marked by Italian ) are my value judgment and for each of them I will be happy to argue (as well as on the quality of the translation).
User Authentication
Since 2017, the use of strong authentication in user applications has increased dramatically, mainly due to the availability of cryptographic authentication methods on mobile devices, although only a slightly smaller percentage of companies use strong authentication for Internet applications.
Overall, the percentage of companies using strong authentication in their business has tripled from 5% in 2017 to 16% in 2018 (Figure 3).
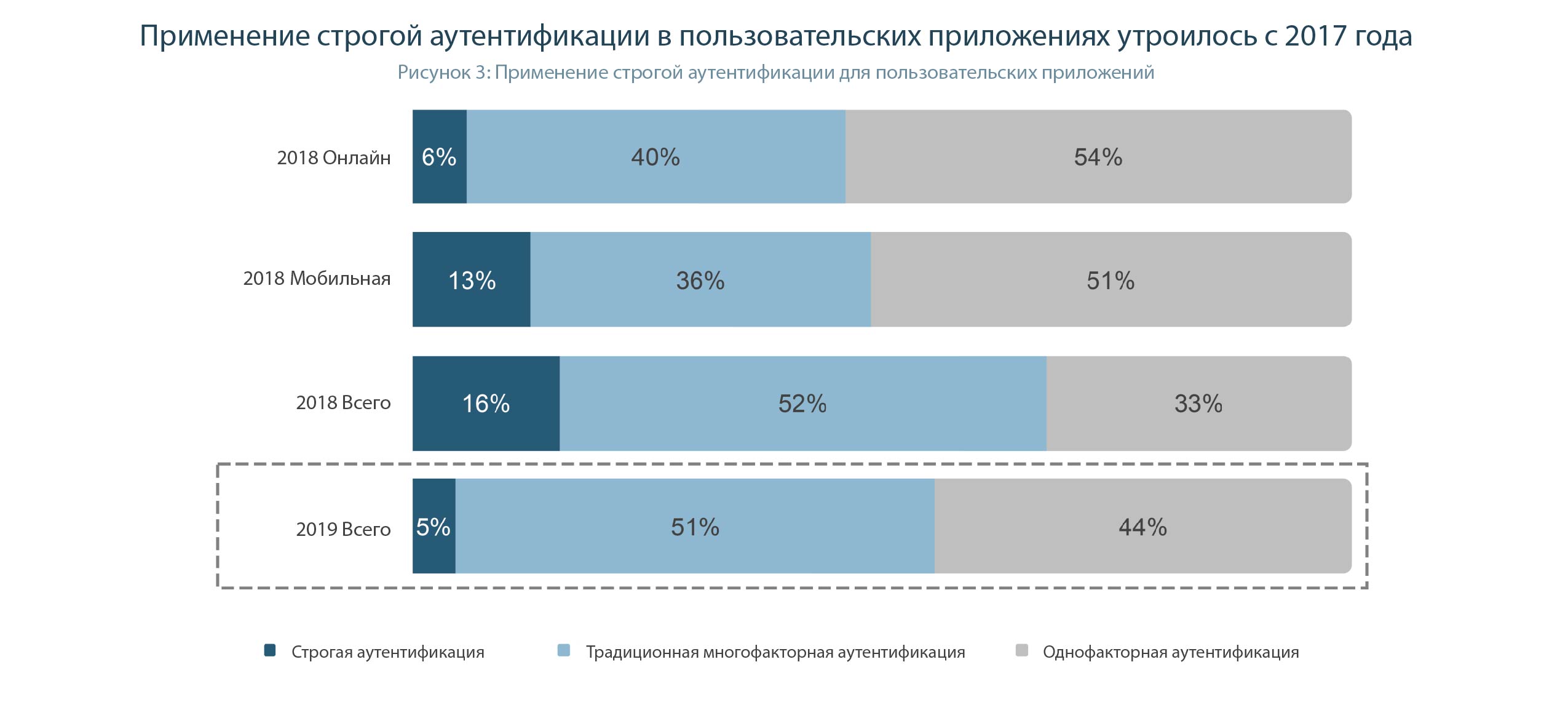
The possibilities for using strong authentication for web applications are still limited ( due to the fact that only completely new versions of some browsers support interaction with cryptographic tokens, however, this problem is solved by installing additional software such as Rutoken Plugin ), therefore many Companies use alternative methods for online authentication, such as programs for mobile devices that generate one-time passwords.
Hardware cryptographic keys ( only FIDO compliant standards are meant here ), such as those offered by Google, Feitian, One Span, and Yubico, can be used for strong authentication without installing additional software on desktops and laptops ( because most browsers already support the WebAuthn standard from FIDO ), but only 3% of companies use this feature to login to their users.
Comparison of cryptographic tokens (such as Rutoken e-signature PKI ) and secret keys that work according to FIDO standards is not only beyond the scope of this report, but also my comments to it. If at all, briefly, both types of tokens use similar algorithms and principles of operation. FIDO tokens are currently better supported by browser manufacturers, although the situation will soon change as more browsers support the Web USB API . But classical cryptographic tokens are protected by a PIN code, they can sign electronic documents and be used for two-factor authentication in Windows (any version), Linux and Mac OS X, they have APIs for various programming languages that allow implementing 2FA and EDS in desktop, mobile and Web applications , and tokens produced in Russia support the Russian GOST algorithms. In any case, a cryptographic token, regardless of what standard it is created by, is the most reliable and convenient authentication method.
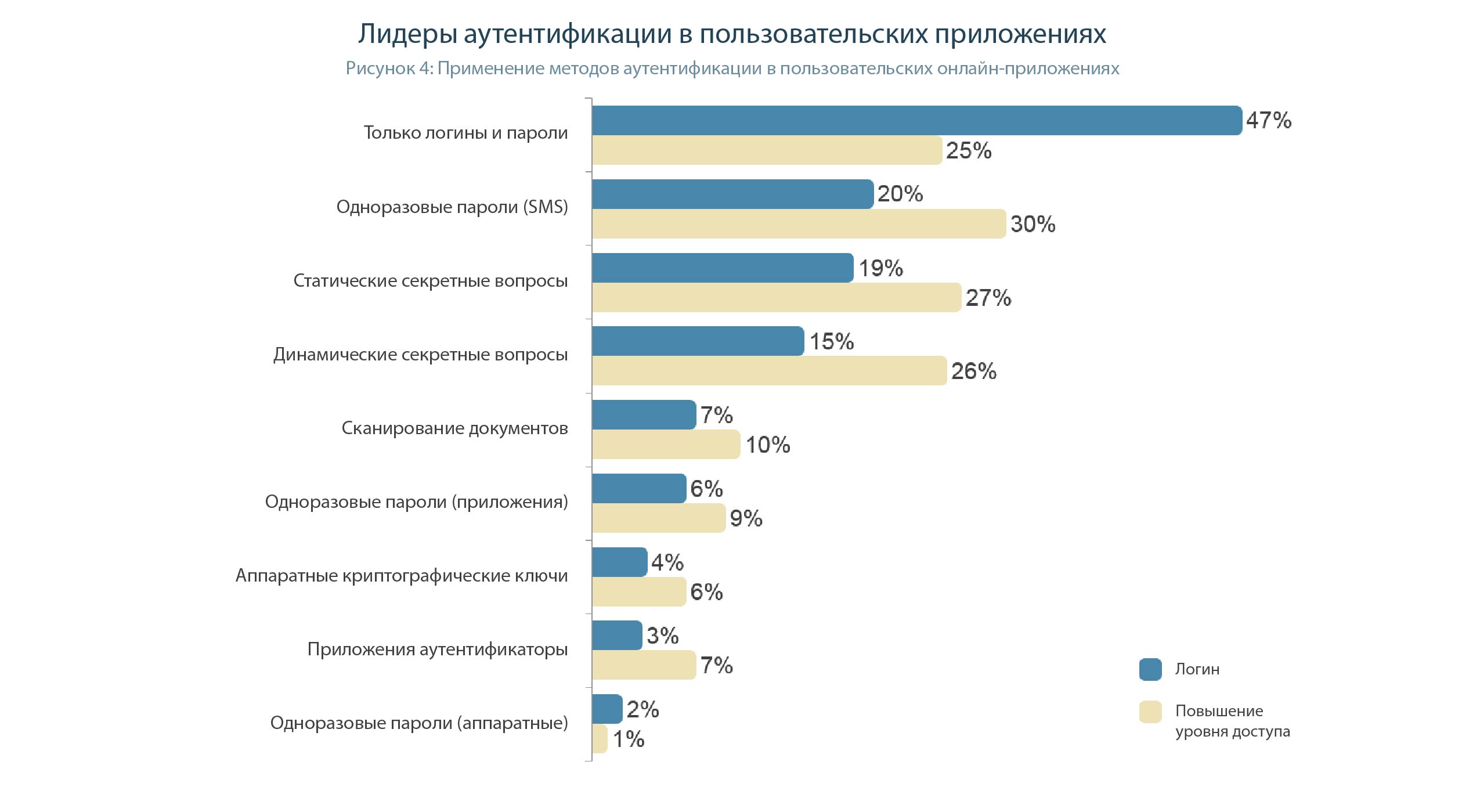
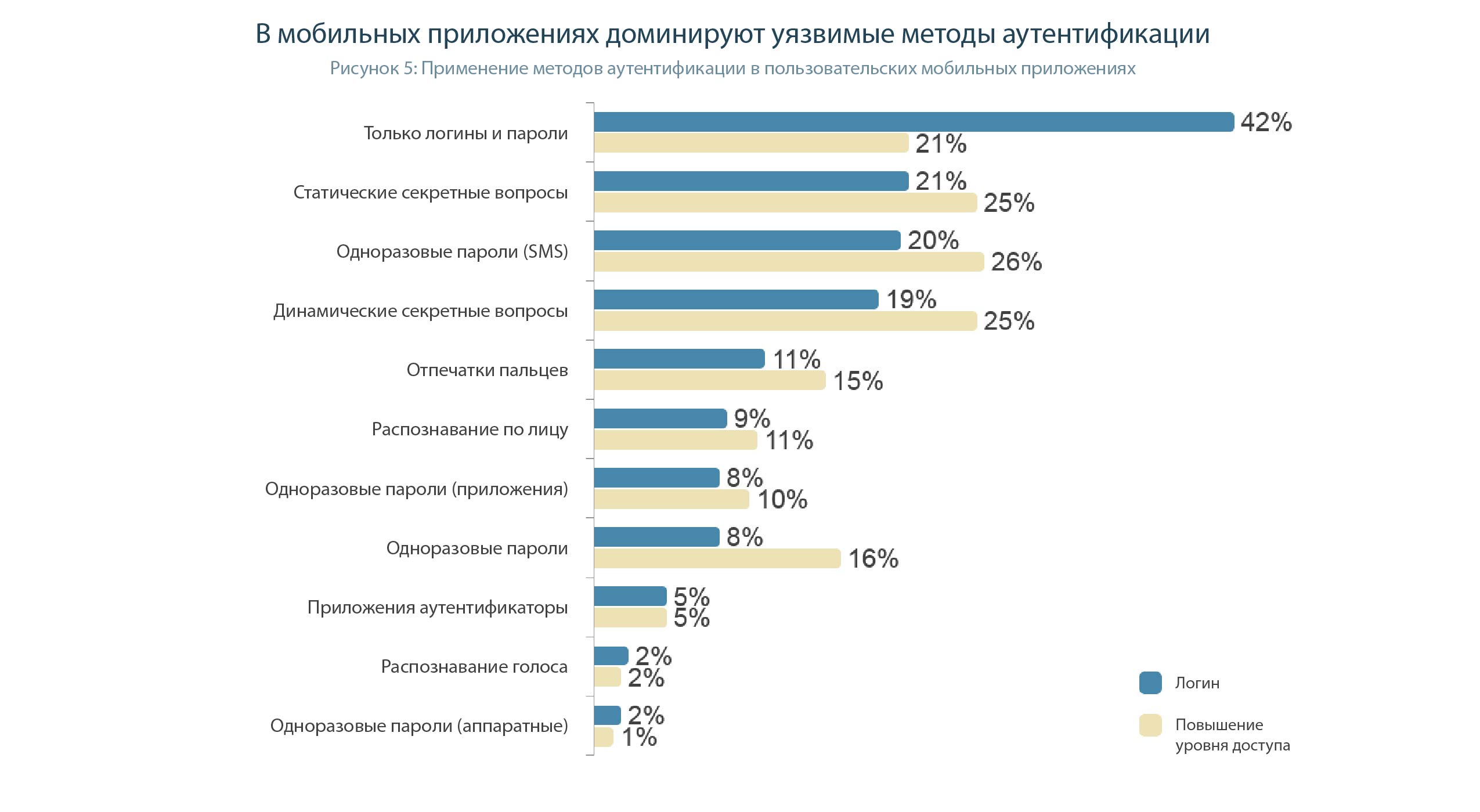
Beyond security: other benefits of strong authentication.
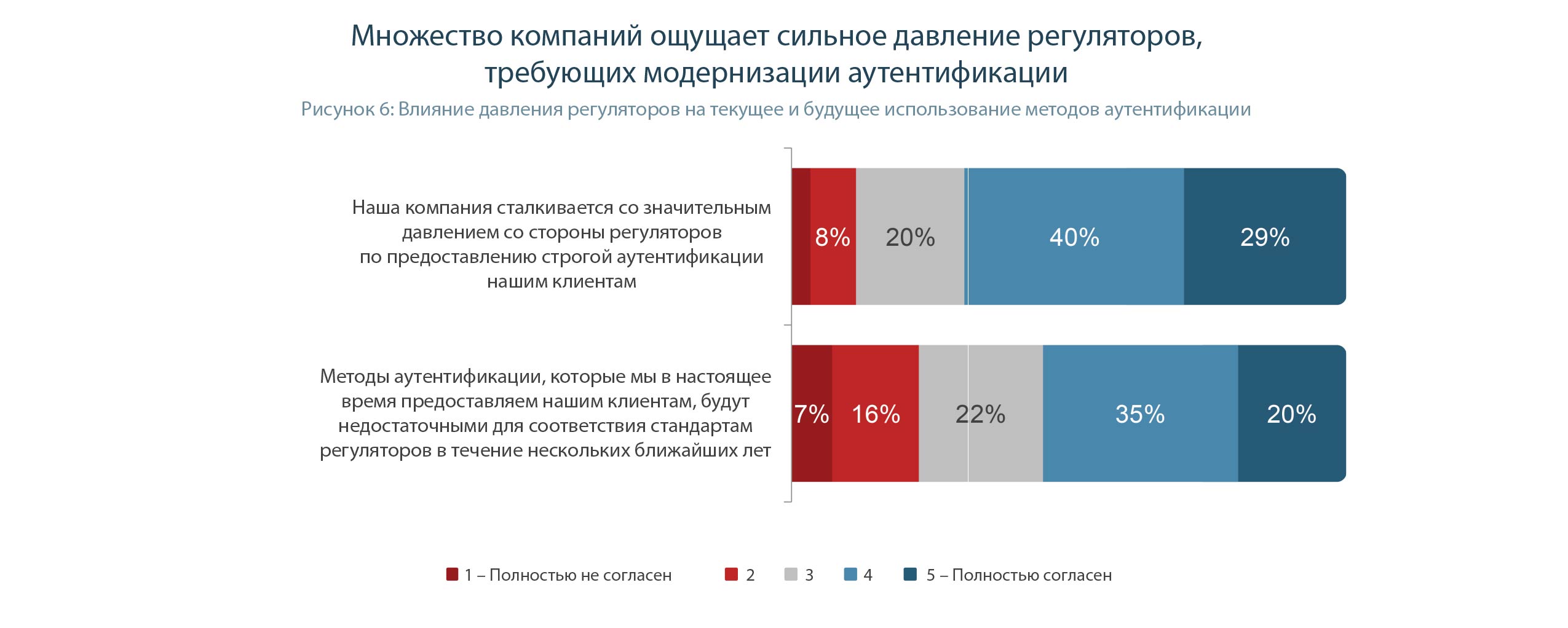
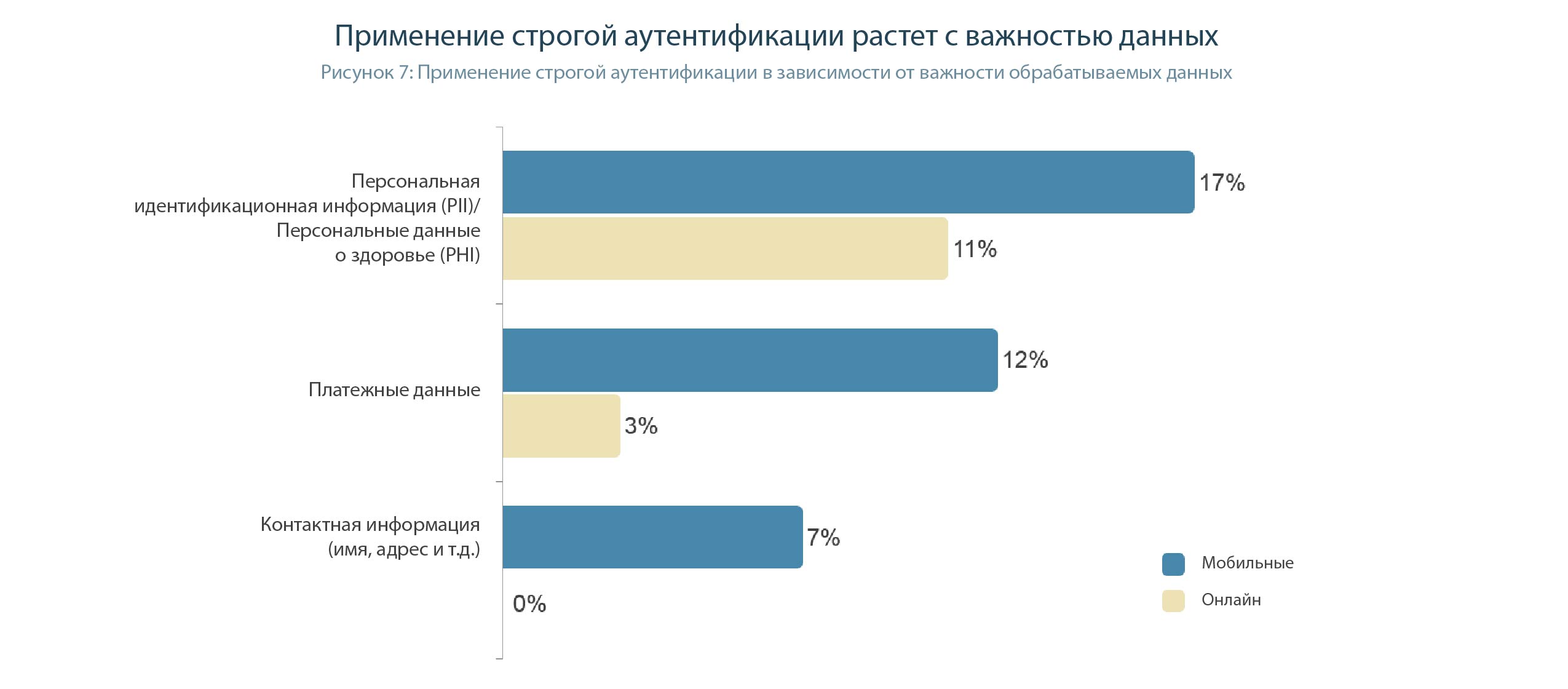
Not surprisingly, the use of strong authentication is closely related to the importance of data stored by the business. The greatest legal and regulatory pressure is faced by companies that store confidential personal information (Personally Identifiable Information (PII)), such as social security numbers or personal health information (Personal Health Information (PHI)). Such companies are the most aggressive adherents of strong authentication. The pressure on business is heightened by the expectations of customers who want to know that organizations that they trust in their most sensitive data use reliable authentication methods. Organizations that handle sensitive PII or PHI are more than twice as likely to use strong authentication than organizations that store only user contact information (Figure 7).
Unfortunately, companies do not yet want to implement reliable authentication methods. Nearly one third of business decision makers consider passwords to be the most effective authentication method, among all those listed in Figure 9, and 43% consider passwords to be the easiest authentication method.
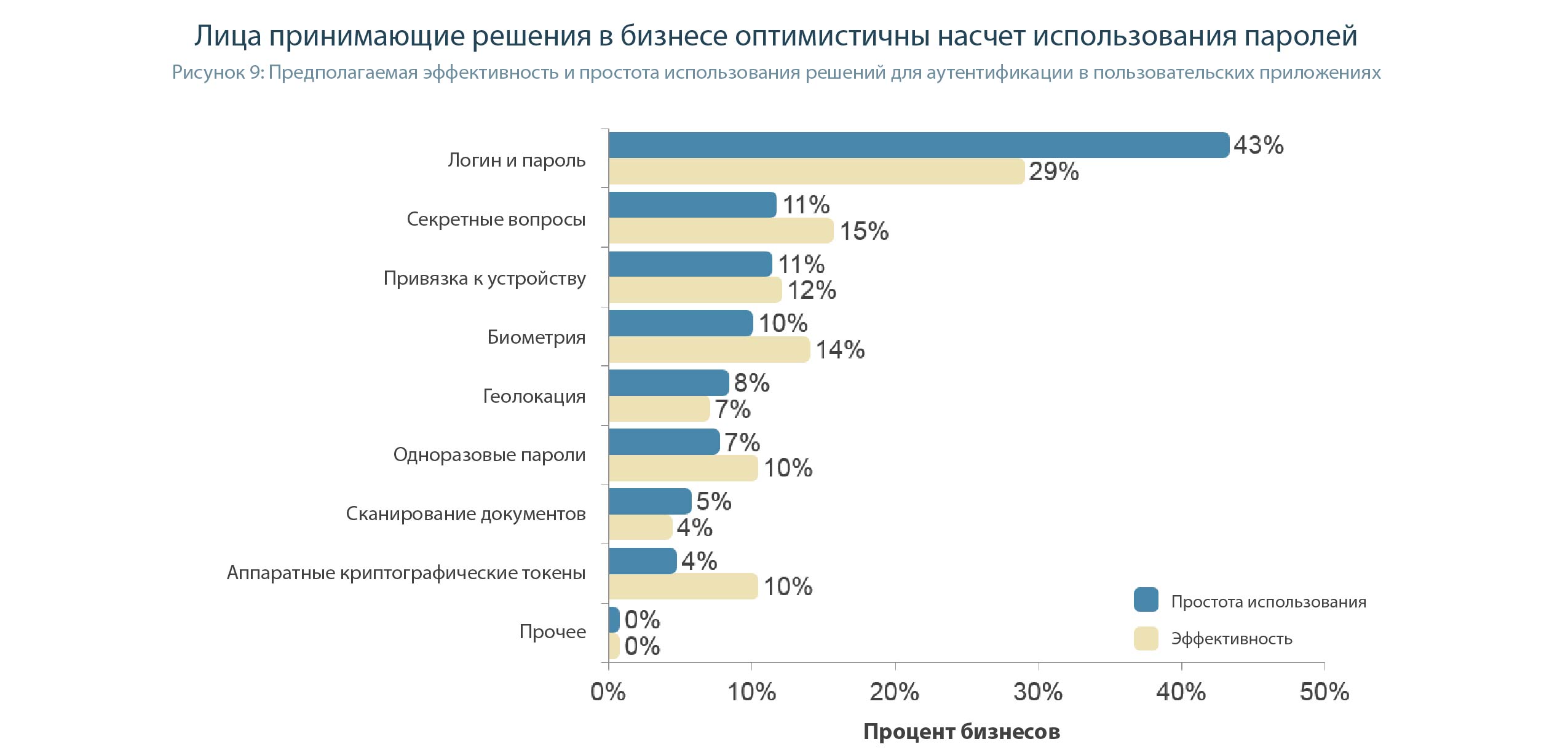
This diagram proves to us that business application developers all over the world are the same ... They see no profit in implementing advanced mechanisms for protecting access to accounts and share the same misconceptions. And only the actions of regulators can make a difference.
We will not touch passwords. But what should we believe in to assume that control questions are more secure than cryptographic tokens ?? The effectiveness of the control questions, which are simply chosen, was estimated at 15%, and not breakable tokens - only 10. At least the film “The Illusion of Deception” would be watched, although in an allegorical form, it is shown how easily the magicians lured the swindler from an entrepreneur Answers and left him without money.
And one more fact, speaking a lot about the qualifications of those who are responsible for security mechanisms in user applications. In their understanding, the process of entering a password is a simpler operation than authentication using a cryptographic token. Although it would seem that it may be easier to connect the token to the USB port and enter a simple PIN code.
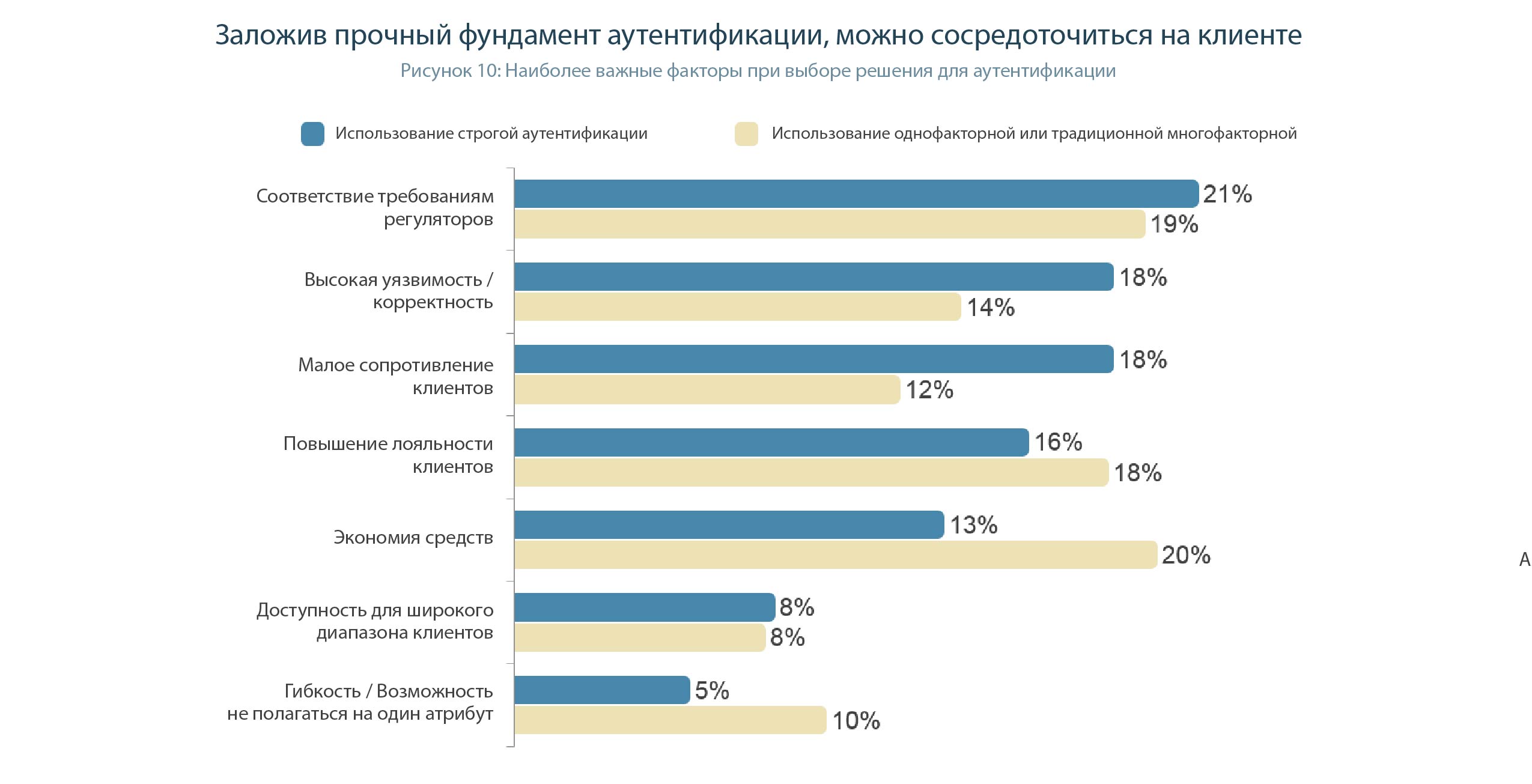
It is important to note that the introduction of strong authentication allows enterprises to no longer think about the authentication methods and the rules of operation required to block fraudulent schemes to meet the real needs of their customers.
While regulatory compliance is a reasonable top priority, both for enterprises that use strong authentication and for those that do not, companies that already use strong authentication will be much more likely to say that increasing customer loyalty is the most important indicator they consider when evaluating an authentication method. (18% vs 12%) (Figure 10).
Corporate Authentication
Since 2017, the introduction of strong authentication in enterprises is growing, but a bit more modest than for consumer applications. The share of enterprises using strong authentication increased from 7% in 2017 to 12% in 2018. Unlike user applications, in a corporate environment, the use of non-password authentication methods is somewhat more common in web applications than on mobile devices. About half of enterprises report using only user names and passwords to authenticate their users when logging into the system, and every fifth (22%) also relies exclusively on passwords for secondary authentication when accessing sensitive data ( i.e., the user logs into the application first, using a simpler authentication method, and if you want to gain access to critical data, you will perform another authentication procedure (this time usually using a more reliable method ).
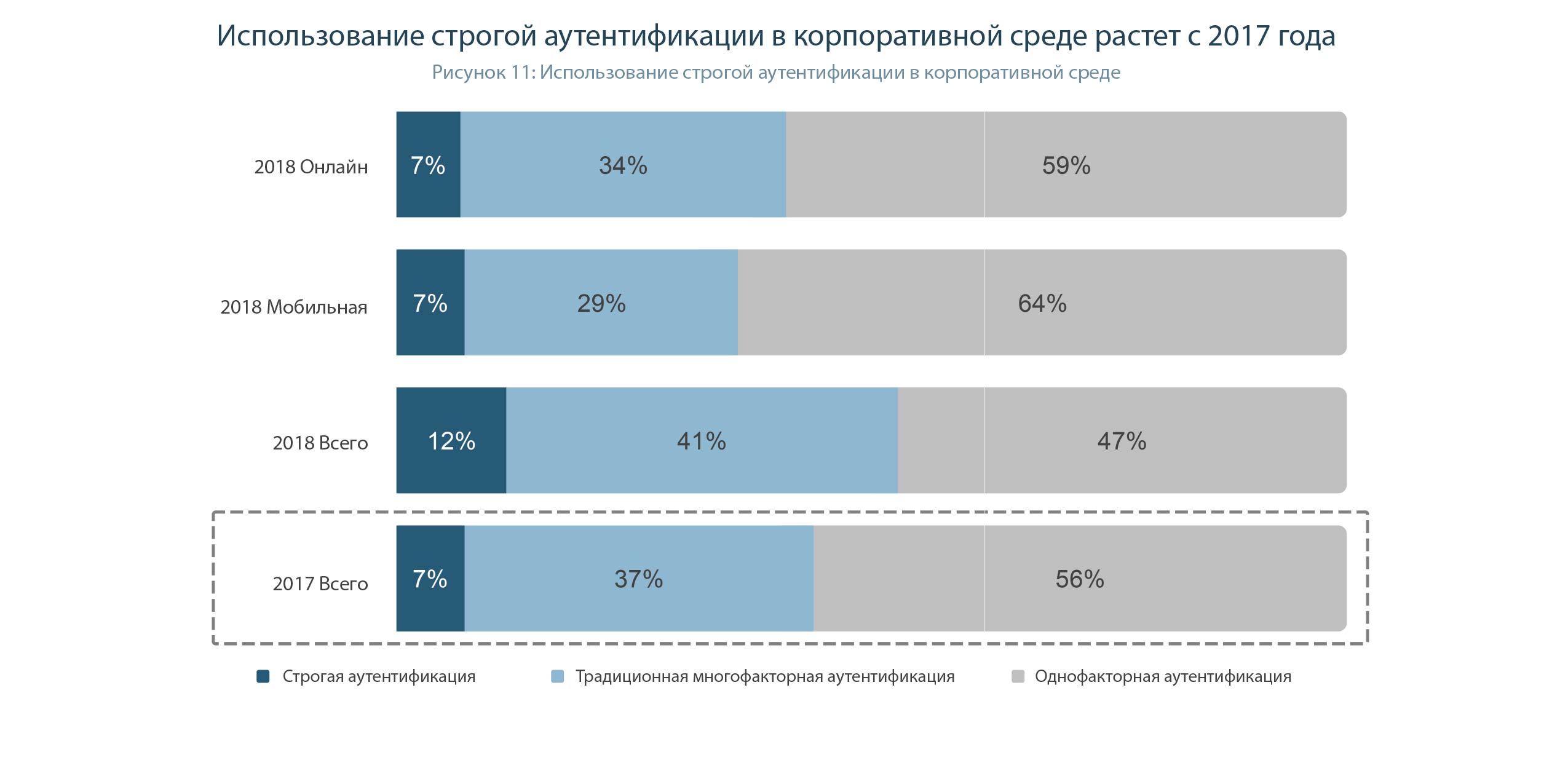
It is necessary to understand that the report does not take into account the use of cryptographic tokens for two-factor authentication in the Windows, Linux and Mac OS X operating systems. And this is currently the most massive use of 2FA. (Alas, but tokens created by FIDO standards are able to implement 2FA only for Windows 10).
Moreover, if a complex of measures is needed for the implementation of 2FA in online and mobile applications, including the revision of these applications, for the introduction of 2FA in Windows, you only need to configure a PKI (for example, based on Microsoft Certification Server) and authentication policies in AD.
And since the protection of the entrance to the working PC and domain is an important element of protecting corporate data, the introduction of two-factor authentication is becoming more and more.
The next two most common methods for authenticating users when logging on to the system are one-time passwords provided through a separate application (13% of enterprises) and one-time passwords delivered via SMS (12%). Although the percentage of using both methods is very similar, but OTP SMS is most often used to increase the level of authorization (in 24% of companies). (Figure 12).
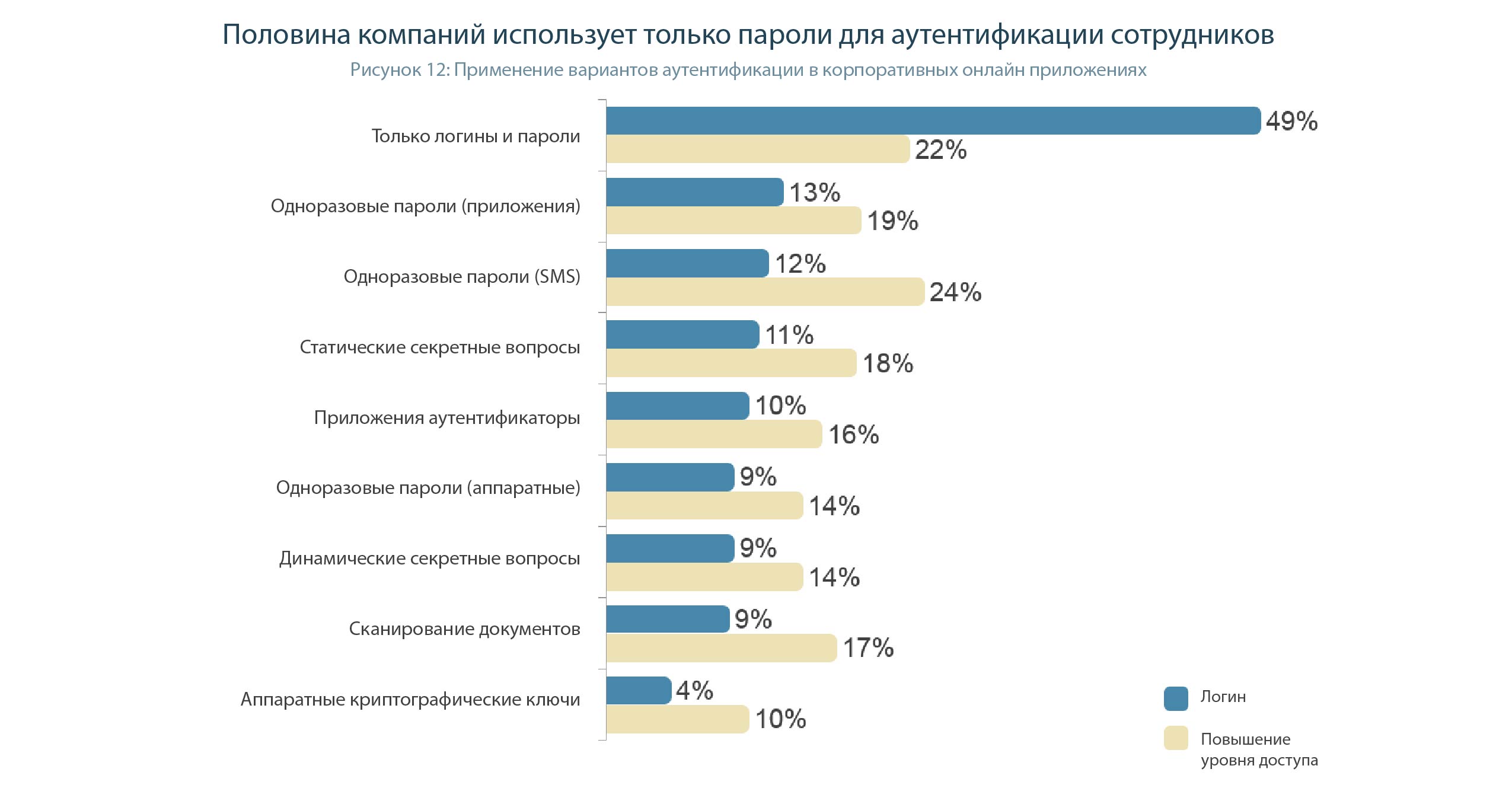
The growing use of strong authentication in the enterprise can probably be explained by the increased availability of cryptographic authentication methods on the enterprise identity management platforms (in other words, corporate SSO and IAM systems have learned to use tokens).
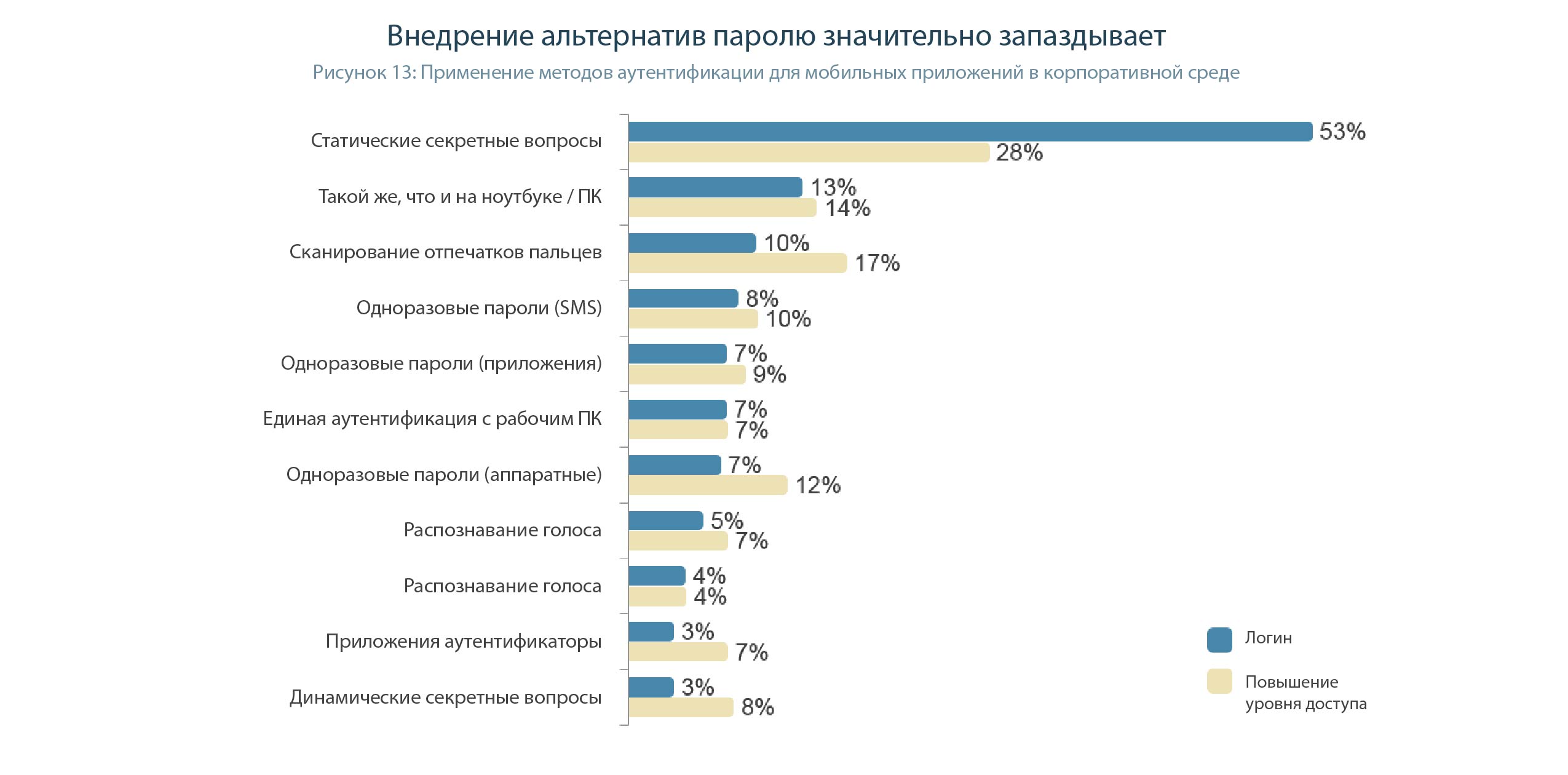
For mobile authentication of employees and contractors, enterprises rely more on passwords than on authentication in consumer applications. Just over half (53%) of enterprises use passwords to authenticate user access to company data through a mobile device (Figure 13).
In the case of mobile devices, one could believe in the great power of biometrics, if not for many cases with fakes of prints, voices, faces and even iris. One search query will show that there is simply no reliable biometric authentication method. Truly accurate sensors certainly exist, but they are very expensive and large in size - and they are not installed in smartphones.
Therefore, the only working 2FA method in mobile devices is the use of cryptographic tokens, which are connected to the smartphone via NFC, Bluetooth and USB Type-C interfaces.
The company's financial data protection is the main reason for investing in password-free authentication (44%), with the fastest growth since 2017 (an increase of eight percentage points). This is followed by the protection of intellectual property (40%) and personnel (HR) data (39%). And it is clear why - not only is the value associated with these types of data widely recognized, since a relatively small number of employees also work with them. That is, the implementation costs are not so large, and only a few people need to learn how to work with a more complex authentication system. In contrast, the data types and devices that most enterprise employees typically access are still protected exclusively with passwords. Employee documents, workstations, and corporate e-mail portals are the areas of greatest risk, since only a quarter of enterprises protect these assets using passwordless authentication (Figure 14).
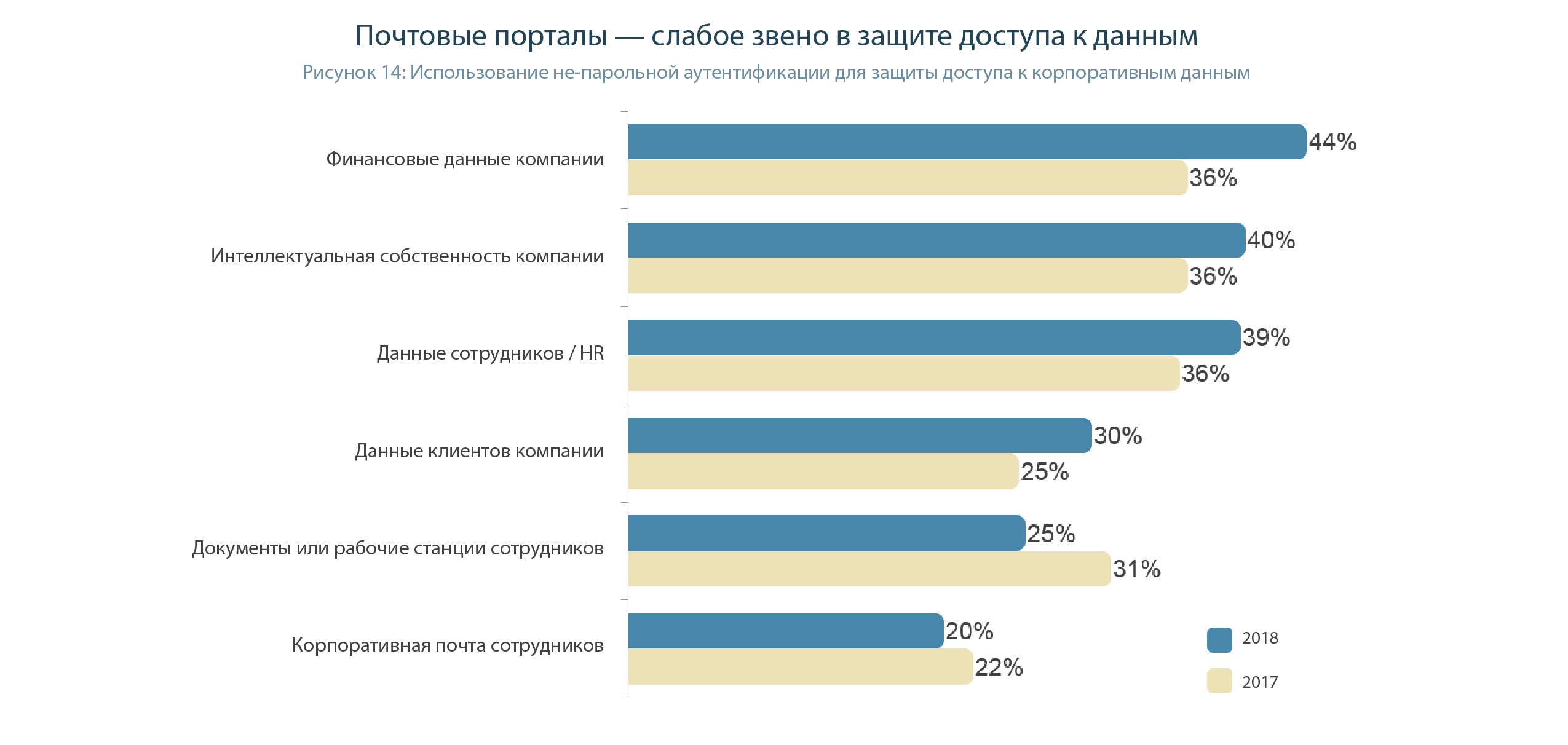
In general, corporate e-mail is a very dangerous and “holey” thing, the degree of potential danger of which is underestimated by most IT directors. Employees receive dozens of letters every day, so why not even one phishing (that is, fraudulent) one among them? This letter will be in the style of the letters of the company, so the employee without fear of clicking on the link in this letter. Well, then there can be anything, for example, downloading a virus to a machine under attack or dumping passwords (including using social engineering, through entering a fake authentication form created by an attacker).
To prevent such things from happening, emails must be signed. Then it will be immediately clear which letter was created by a legal employee, and which attacker. In Outlook / Exchange, for example, an electronic signature based on cryptographic tokens is turned on quite quickly and simply and can be used in conjunction with two-factor authentication in PCs and Windows domains.
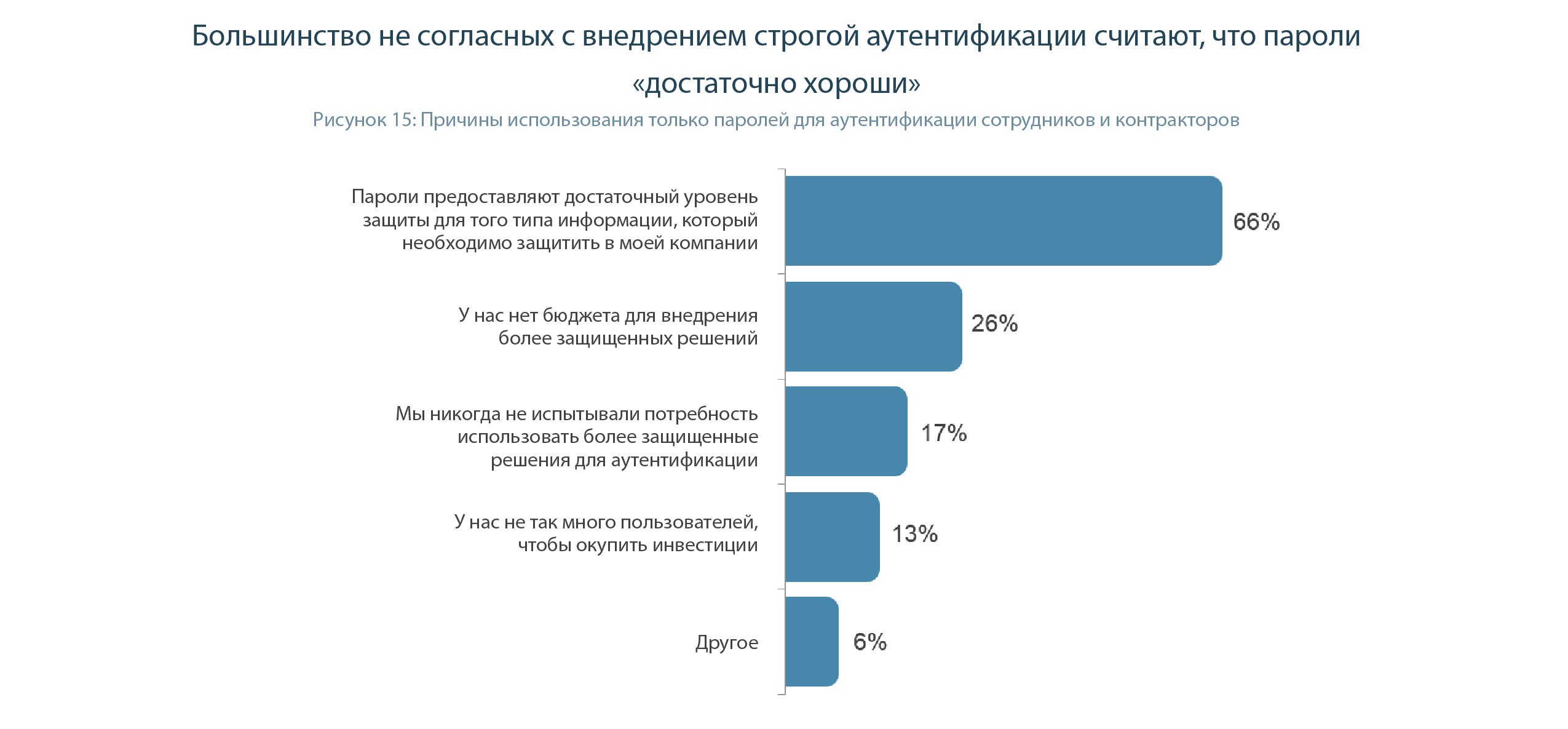
Among those executives who rely solely on password authentication within the enterprise, two-thirds (66%) do this because they believe that passwords provide sufficient security for the type of information their company must protect (Figure 15).
But strong authentication methods are becoming more common. Largely due to the fact that their availability increases. More and more Identity and Access Management (IAM) systems, browsers and operating systems support authentication using cryptographic tokens.
Strong authentication has another advantage. Since the password is no longer used (replaced by a simple PIN code), there are no requests from employees asking them to change their forgotten password. Which in turn reduces the burden on the IT department of the enterprise.
Results and conclusions
- Managers often do not have the necessary knowledge to assess the real effectiveness of various authentication options. They are used to trusting such outdated protection methods like passwords and secret questions simply because "it worked before."
- Users of this knowledge are even less so ; for them the main thing is simplicity and convenience . So far they have no incentive to choose more secure solutions .
- User application developers often have no reason to implement two-factor authentication instead of password authentication. There is no competition for the level of protection in user applications.
- All responsibility for hacking is transferred to the user . Called a one-time password to the attacker - to blame . Your password was intercepted or spied - guilty . I did not demand from the developer to use reliable authentication methods in the product - it is to blame .
- The correct regulator should first of all require companies to implement solutions that block data leakage (in particular, two-factor authentication), and not punish for data leakage that has already occurred .
- Some software developers are trying to sell old and not particularly reliable solutions to consumers in the beautiful packaging of an “innovative” product. For example, authentication, by binding to a specific smartphone or using biometrics. As can be seen from the report, only a solution based on strong authentication, that is, cryptographic tokens, can be truly reliable .
- The same cryptographic token can be used for a number of tasks : for strong authentication in the enterprise operating system, in the corporate and user applications, for electronic signing of financial transactions (important for banking applications), documents and email.
Source: https://habr.com/ru/post/452146/
All Articles