China and Iran use replay attacks to combat Telegram
In the bug trackers of the popular MTProxy servers mtg and mtprotoproxy, there were reports that in Iran and China, the supervisory authorities learned to somehow detect and block telegram proxies, even using randomization of the packet length (dd prefix).
As a result, an amusing story emerged: the attackers used replay attacks to identify MTProxy proxy servers.
Connection packets with the proxy are “recorded” by a third party, and after some time a connection attempt is made using the saved packet header along with the “corrupted” data.
If you look at the structure of the MTProxy package
')
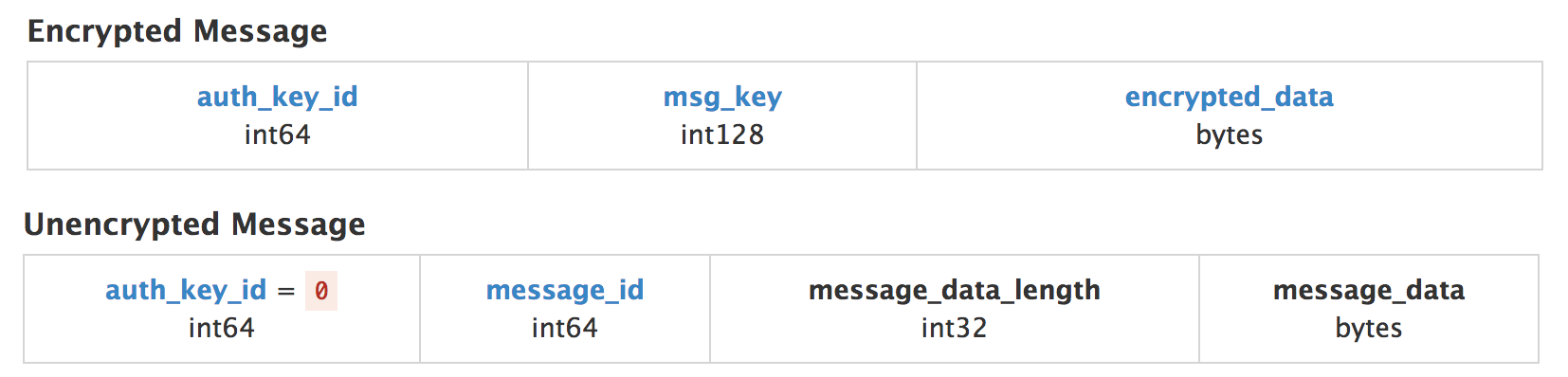 (picture taken here from this article)
(picture taken here from this article)
then it turns out to imagine how it can work:
the proxy server analyzes the packet header, recognizes it as valid, and sends it further directly to the Telegram server. Telegram servers accept the packet, but respond to it with an error message that is sent back by the proxy server, and it can be detected just along the packet length (error packets are much shorter than normal).
Based on this, the server address is blocked.
Proxy developers have already released updates. When connecting, it is checked that there have not yet been any connections with such auth_key_id (which is essentially a 64-bit random number):
github.com/alexbers/mtprotoproxy/commit/4cae6290b9529485125366771005460309a835b5
github.com/9seconds/mtg/commit/33852ca4818c365778edccb7441a11decff90009
github.com/seriyps/mtproto_proxy/commit/0f4d180a06eefb8aaa92c1d202ead8015a938a4c
In addition to this, quite interesting information appeared a few days ago in the Russian network communities and telegram channels that our native RKN began using open proxies to check public mtproxy servers. On the one hand, this is quite a logical step, since they don’t want or can’t do such checks from their addresses, because their subnet ranges will quickly become known to server owners, and on the other hand, in many cases “public proxies” are hacked soho routers, which makes the situation very piquant.
A detailed article on this can be found on tjournal.
Enthusiasts have already developed a script that automatically retrieves the current list of open proxies and applies ipset rules to effectively filter addresses from this list.
In addition to the script is a brief instruction on its use, written in a very lively and inspiring language.
As a result, an amusing story emerged: the attackers used replay attacks to identify MTProxy proxy servers.
Replay Attack - An attack on the authentication system by recording and then replaying previously sent correct messages or parts of them.( wiki )
Connection packets with the proxy are “recorded” by a third party, and after some time a connection attempt is made using the saved packet header along with the “corrupted” data.
If you look at the structure of the MTProxy package
')
 (picture taken here from this article)
(picture taken here from this article)then it turns out to imagine how it can work:
the proxy server analyzes the packet header, recognizes it as valid, and sends it further directly to the Telegram server. Telegram servers accept the packet, but respond to it with an error message that is sent back by the proxy server, and it can be detected just along the packet length (error packets are much shorter than normal).
Based on this, the server address is blocked.
Proxy developers have already released updates. When connecting, it is checked that there have not yet been any connections with such auth_key_id (which is essentially a 64-bit random number):
github.com/alexbers/mtprotoproxy/commit/4cae6290b9529485125366771005460309a835b5
github.com/9seconds/mtg/commit/33852ca4818c365778edccb7441a11decff90009
github.com/seriyps/mtproto_proxy/commit/0f4d180a06eefb8aaa92c1d202ead8015a938a4c
In addition to this, quite interesting information appeared a few days ago in the Russian network communities and telegram channels that our native RKN began using open proxies to check public mtproxy servers. On the one hand, this is quite a logical step, since they don’t want or can’t do such checks from their addresses, because their subnet ranges will quickly become known to server owners, and on the other hand, in many cases “public proxies” are hacked soho routers, which makes the situation very piquant.
A detailed article on this can be found on tjournal.
Enthusiasts have already developed a script that automatically retrieves the current list of open proxies and applies ipset rules to effectively filter addresses from this list.
In addition to the script is a brief instruction on its use, written in a very lively and inspiring language.
Source: https://habr.com/ru/post/452144/
All Articles