The “unbreakable” eyeDisk is protected by an iris scan, but transmits the password in clear text

EyeDisk USB drive with biometric protection that is “impossible to crack”
Most modern methods of biometric protection do not always mean increased security. The failure of eyeDisk developers actually shows more general trends. Unfortunately, in the IT industry it happens that, under the impression of "brilliant" new technologies, people forget about the basics of security.
The developers advertised eyeDisk as an “unbreakable” USB-drive - and successfully issued over $ 21 thousand pre-orders on Kickstarter.
In fact, the eyeDisk device is a flash card with an integrated camera that scans the iris. Since the computing power of the gadget is not enough for image analysis and authentication, the picture, along with the password, is transferred via USB to the computer where the special software works.
')
Scanning and recognition take about 0.5 seconds.

A 32GB flash drive is sold for $ 99, and investors could order it for $ 50 as part of a crowdfunding campaign. The most expensive 128 GB flash drive costs $ 178 ($ 89). Sales began in March 2019.
The “unbreakable” flash drive attracted the attention of hackers from PenTest Partners. They write that the first thing connected the media to the Windows virtual machine. It was recognized as three devices, including a USB camera. The infrared camera takes funny black and white photos: for example, bearded people do not have a beard.
Then penterster opened eyeDisk and examined its insides. Subsequently, it was not useful for hacking, but this is the standard procedure. They paid attention to a curious fact: there are three MCUs on the board (highlighted in red and green in the photos), but there is no central control unit among them, each chip has its own role.
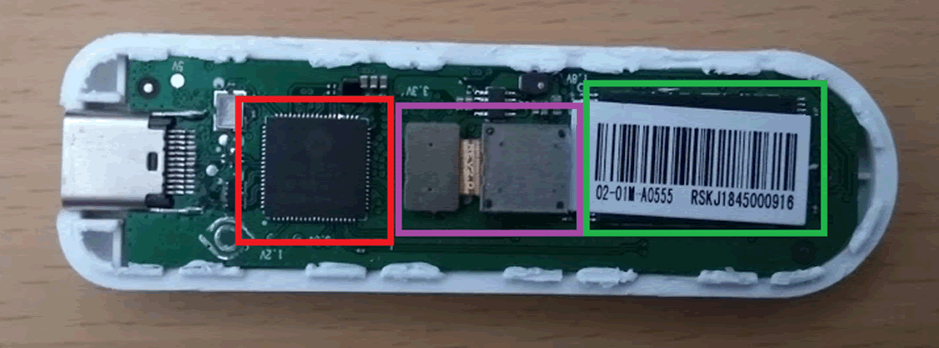
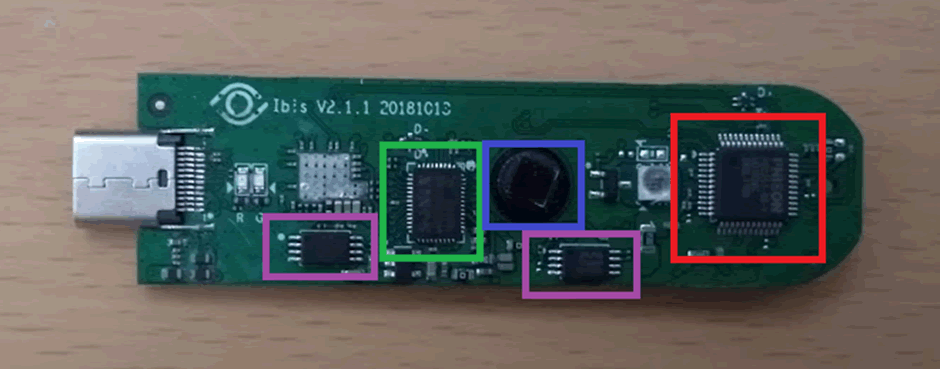
The camera is shown in blue, and purple is two tssop8 chips (PUYA P25Q040H SPI NOR Flash).
Then it's software time. The latest versions of the Wireshark sniffer are able to listen on USB traffic. For reference, USB mass storage is a shell for SCSI commands, so the general pattern looks like this:
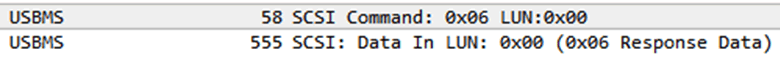
Here are the LUN (Logical Unit Number), under which the device is recognized, and the CDB command descriptor block (Command Descriptor Block). In this case, the top packet sends a SCSI command with opcode 0x06 and receives a response from the device. In USB terminology, the word “In” indicates the direction to the host, “Out” to the device.
Contents of the first package:

The contents of the response packet:
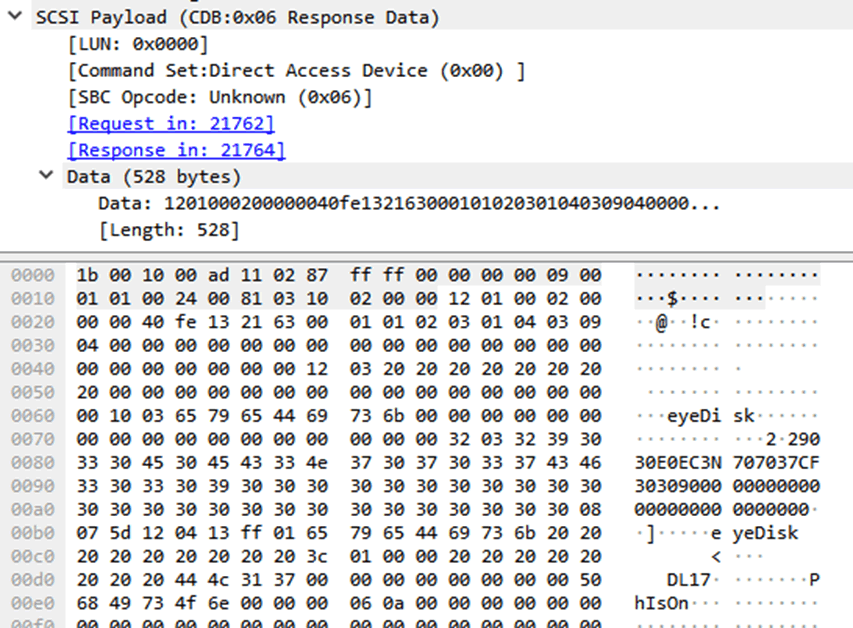
But what packets are transmitted at the time of unlocking the device after successful authentication. First SCSI command from host:
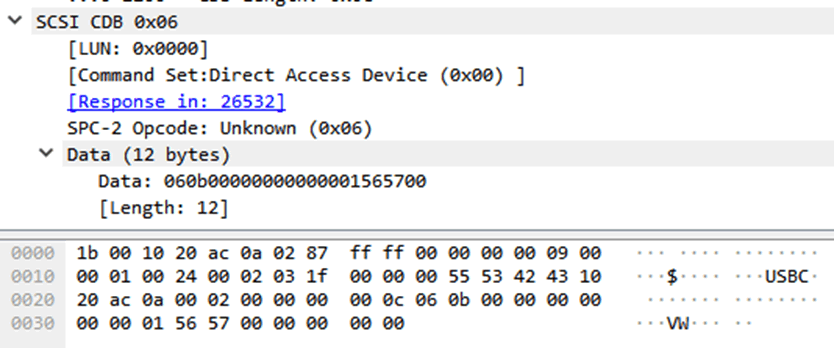
And the device response:
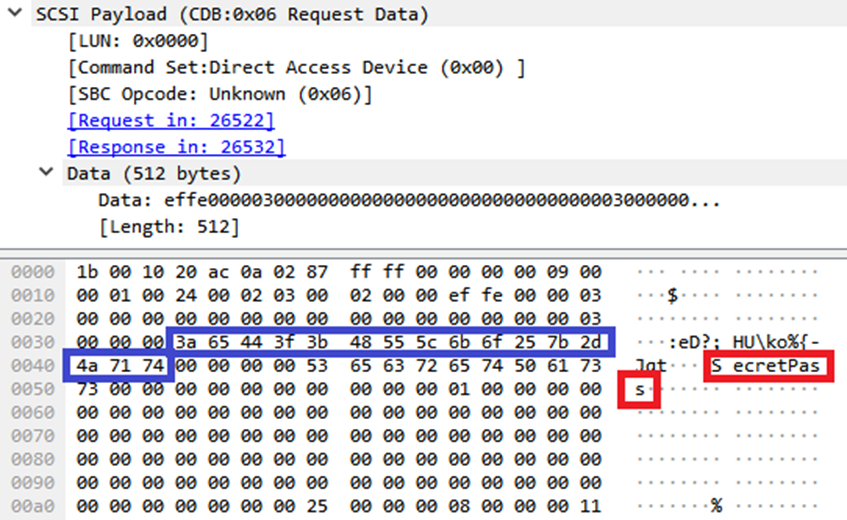
The red color shows the password that is set for the device. As you can see, it is transmitted in the clear. But listening to the USB bus does not pose any difficulty, which the developers did not think at all. Or they were freelancers who were not directly told to implement password encryption (see the article “Web developers write unsafe code by default” : the web has the same problem).
The blue color in the screenshot highlights 16 bytes of the iris hash - the second factor of two-factor authentication.
The most interesting thing is that if you enter the wrong password or scan an arbitrary iris, the program sends exactly the same data packet to the device, receiving the same answer.
That's all that constitutes an “unbreakable” eyeDisk drive.
Pentesters fumbled a bit more with flash memory, made a dump and found a specific memory area where the password is stored. Although it was already, in principle, optional. The principal vulnerability is that, for verification, the software requests a password from the device and an iris scan of the real user, which is transmitted in the open form. Information is transmitted with each authentication attempt, and verification occurs on the host.
The vulnerability report was sent to eyeDisk a month ago, the manufacturer promised to fix the vulnerability, but so far it hasn’t given an answer;
Listening to traffic very often reveals vulnerabilities in the Internet of Things and other peripherals. Developers sometimes forget that any transmission channel can be heard. Trendy modern technologies like iris scanning or other biometrics will not add security if we ignore encryption.
Take part in the PKI survey from GlobalSign until May 24, 2019 and you will get the opportunity to win prizes, one of which is the Amazon Gift Card for $ 500.

The survey is available at: www.surveymonkey.com/r/GlobalSignPKI-2019
Source: https://habr.com/ru/post/451896/
All Articles