Improving the work of Wi-Fi. General principles and useful things

Everyone who collected, bought, or at least tuned in a radio receiver, probably heard such words as: sensitivity and selectivity (selectivity).
Sensitivity - this parameter shows how well your receiver can receive a signal even in the most remote areas.
And selectivity, in turn, shows how well the receiver can tune to a particular frequency without the influence of other frequencies. These “other frequencies”, that is, not related to the transmission of a signal from the selected radio station, in this case play the role of radio interference.
Increasing the transmitter power, we force receivers with low sensitivity to receive our signal at all costs. An important role is played by the mutual influence of signals from different radio stations on each other, which complicates the setup, reducing the quality of radio communications.
')
In the Wi-Fi environment, radio broadcasts are used as the medium for transmitting data. Therefore, many of the things with which radio engineers and radio amateurs of the past and even the nineteenth century have operated, are still relevant today.
But something has changed. The digital format has replaced the analog format, which has caused a change in the nature of the transmitted signal.
The following is a description of common factors that influence the operation of Wi-Fi wireless networks within the IEEE 802.11b / g / n standards.
Some nuances of Wi-Fi networks
For on-air broadcasting far from large populated areas, when you can only receive a signal from a local FM radio station and another “Mayak” in the VHF band at your receiver, the question of mutual influence does not arise.
Another thing Wi-Fi devices that work only in two limited ranges: 2.4 and 5 GHz. Below are a few problems that have to, if not overcome, then know how to get around.
Problem one - different standards work with different ranges.
In the 2.4 GHz band, devices that support 802.11b / g / n work; in the 5 GHz band - 802.11a and 802.11n.
As you can see, only 802.11n devices can operate both in the 2.4 GHz band and in the 5 GHz band. In other cases, we must either support broadcasting in both bands, or accept the fact that some clients will not be able to connect to our network.
The second problem - Wi-Fi devices operating in the range of the nearest action, can use the same frequency range.
For devices operating in the 2.4 GHz frequency band, 13 wireless channels of 20 MHz width for the 802.11b / g / n standard or 40 MHz for the 802.11n standard with 5 MHz intervals are available and allowed for use in Russia.
Therefore, any wireless device (client or access point) interferes with adjacent channels. Another thing is that the transmitter power of the client device, for example, a smartphone, is much lower than that of the most common access point. Therefore, throughout the article we will only talk about the mutual influence of access points on each other.
The most popular channel, which is offered to customers by default, is 6. But you should not delude yourself that by choosing the next digit, we will get rid of the parasitic influence. An access point operating on channel 6 gives strong interference to channels 5 and 7 and weaker ones to channels 4 and 8. As the gaps between the channels increase, their mutual influence decreases. Therefore, to reduce mutual interference to a minimum, it is highly desirable that their carrier frequencies be separated from each other by 25 MHz (5 inter-channel intervals).
The trouble is that of all channels with little influence on each other, only 3 channels are available: these are 1, 6 and 11.
We have to look for some way to circumvent the existing restrictions. For example, the mutual influence of devices can be compensated by decreasing power.
The benefits of moderation in everything
As mentioned above, power reduction is not always bad. Moreover, with increasing power, the quality of reception can deteriorate significantly and the point here is not at all in the “weakness” of the access point. Below we consider in which cases it may be useful.
Radio download
The effect of the load can be seen firsthand, at the time of selecting a device for connection. If there are more than three or four items in the list of Wi-Fi networks, you can already talk about downloading the radio. In addition, each network is a source of interference for its neighbors. And interference affects network performance, because it dramatically increases the noise level and this leads to the need for constant re-sending packets. In this case, the main recommendation is to lower the transmitter power at the access point, ideally, to persuade all neighbors to do the same so as not to interfere with each other.
The situation is reminiscent of the school class in the classroom, when the teacher was absent. Each student begins to talk with a neighbor on the desk and other classmates. In the general noise, they hear each other poorly and begin to speak louder, then even louder and eventually start to scream. The teacher quickly resorts to the class, takes some disciplinary action and restores the normal situation. If, in the role of teacher, we represent a network administrator, and in the role of schoolchildren, the owners of access points, we will get an almost direct analogy.
Asymmetrical connection
As mentioned earlier, the transmitter power of the access point is usually stronger by 2-3 times than on client mobile devices: tablets, smartphones, laptops, and so on. Therefore, the appearance of “gray areas” is very likely, where the client will receive a good stable signal from the access point, and the transmission from the client to the point will work “not very”. Such a connection is called asymmetric.
To maintain a stable connection with good quality, it is highly desirable that there is a symmetrical connection between the client device and the access point, when reception and transmission in both directions work quite effectively.
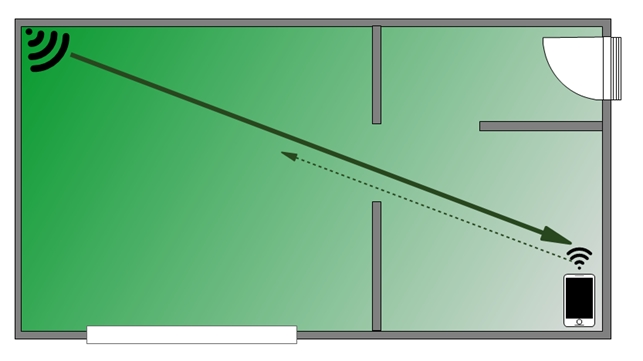
Figure 1. Asymmetric connection on the example of a flat plan.
To avoid asymmetric connections, you should avoid rashly increasing transmitter power.
When power increase is required
The factors listed below require an increase in power in order to maintain stable communication.
Interference from other types of radio and other electronics
Bluetooth devices, for example, headphones, wireless keyboards and mice that operate in the 2.4 GHz frequency band and interfere with the operation of the access point and other Wi-Fi devices.
The following devices can also have a negative effect on signal quality:
- microwave ovens;
- baby monitors;
- CRT monitors, wireless speakers, cordless phones and other wireless devices;
- external sources of electrical voltage, such as power lines and power substations,
- electric motors;
- shielded cables, as well as coaxial cables and connectors used with some types of satellite dishes.
Long distances between Wi-Fi devices
Any radios have a limited range. In addition to the design features of the wireless device, the maximum reach distance can be reduced by external factors, such as obstacles, radio interference, and so on.
All this leads to the formation of local “inaccessible zones”, where the signal from the access point is “not enough” to the client device.
Barriers to signal flow
Various obstacles (walls, ceilings, furniture, metal doors, etc.) located between Wi-Fi devices can reflect or absorb radio signals, which leads to a deterioration or complete loss of communication.
Such simple and clear things as reinforced concrete walls, sheet metal coating, steel frame, and even mirrors and tinted glass significantly reduce the signal intensity.
Interesting fact : the human body attenuates the signal by about 3 dB.
The table below shows the loss of Wi-Fi signal efficiency when passing through various media for a 2.4 GHz network.

* Effective distance - indicates the magnitude of the decrease in radius of action after passing the corresponding obstacle compared with open space.
Let's sum up the interim results.
As mentioned above, high signal strength does not in itself improve the quality of communication via Wi-Fi, but can interfere with establishing good communication.
At the same time, there are situations when it is necessary to provide higher power for stable transmission and reception of a Wi-Fi radio signal.
These are contradictory requirements.
Useful features from Zyxel that can help
Obviously, you need to use some interesting features that will help get out of this controversial situation.
IMPORTANT ! You can learn about the many nuances in building wireless networks, as well as the possibilities and practical use of equipment at specialized Zyxel - ZCNE courses. Find out about the next courses here .
Client steering
As noted earlier, the problems described mainly affect the 2.4 GHz range.
Happy owners of modern devices can use the frequency range of 5 GHz.
Benefits:
- more channels, so it's easier to choose those that will affect each other at a minimum;
- other devices, such as Bluetooth, do not use this range;
- support for channels 20/40/80 MHz wide.
Disadvantages:
- radio signal signal in this range worse passes through obstacles. Therefore, it is desirable to have not one “super-penetrative”, but two or three access points with more modest signal power in different rooms. On the other hand, it will give a more even coverage than to catch the signal from one, but “super-strong”.
However, in practice, as always, there are nuances. For example, some devices, operating systems, and software by default still offer a 2.4GHz “good old” range for the connection. This is done to reduce compatibility issues and simplify the network connection algorithm. If the connection is made automatically or the user does not have time to notice this fact, the possibility of using the 5 GHz range will remain aside.
Client Steering, which by default offers client devices a 5 GHz connection, will help to change this. If this range is not supported by the client, it will still be able to use 2.4 GHz.
This feature is available:
- access points Nebula and NebulaFlex;
- in the NXC2500 and NXC5500 wireless network controllers;
- in firewalls with a controller function.
Auto healing
Above, there have been many arguments in favor of flexible power control. However, the question remains: how to do it?
To do this, Zyxel wireless controllers have a special feature: Auto Healing.
The controller with its help checks the status and operability of access points. If it turns out that one of them does not work, then the neighboring ones will be instructed to increase the signal power in order to fill the resulting zone of silence. After the missing access point is back in operation, neighboring points are instructed to reduce the signal power so as not to interfere with each other’s work.
This feature is also present in the special line of wireless controllers: NXC2500 and NXC5500.
Secure Wireless Border
Neighboring access points from a parallel network not only interfere, but can also be used as a springboard for attacking a network.
In turn, the wireless controller should deal with this. In the arsenal of NXC2500 and NXC5500 controllers, there are enough tools, such as standard WPA / WPA2-Enterprise authentication, various Extensible Authentication Protocol (EAP) implementations, built-in firewall.
Thus, the controller not only finds unauthorized access points, but also blocks suspicious activities on the corporate network, which are more likely to have malicious intent.
Rogue AP Detection function (Rogue AP Containment)
First, let's look at what a Rogue AP is.
Rogue APs are foreign access points that are not controlled by the network administrator. Nevertheless, they are present within reach of the Wi-Fi network of the enterprise. For example, it can be personal access points for employees that are plugged in without a permission into the power outlet of a working office. This kind of initiative badly affects the security of the network.
In fact, such devices form a channel for third-party connection to the enterprise network, bypassing the main security system.
For example, a foreign access point (RG) is not formally in the enterprise network, but a wireless network with the same SSID name is created on it as on the legal access points. As a result, the RG point can be used to intercept passwords and other secret information when clients of the corporate network mistakenly try to connect to it and try to transfer their credentials. As a result, user credentials will be known to the owner of the “phishing” point.
Most Zyxel access points have a built-in radio scan function to detect extraneous points.
IMPORTANT ! Detection of someone else's points (AP Detection) will work only if at least one of these “watchdog” access points is configured to work in network monitoring mode.
After the Zyxel access point, when operating in the monitoring mode, detects the alien points, a blocking procedure can be undertaken.
Suppose Rogue AP imitates a legal access point. As mentioned above, an attacker can duplicate corporate SSID settings on a false point. Then the Zyxel access point will try to prevent dangerous activity, introducing interference through the broadcast of dummy broadcast packets. This will make it impossible for clients to connect to the Rogue AP and intercept their credentials. And the “spy” access point will not be able to fulfill its mission.
As you can see, the mutual influence of access points not only introduces annoying interference when working with each other, but can also be used to protect against malicious attacks.
Conclusion
The material in the framework of a small article does not allow to tell about all the nuances. But even with a quick overview, it becomes clear that the development and maintenance of a wireless network have quite interesting nuances. On the one hand, it is necessary to deal with the mutual influence of signal sources, including by reducing the power of access points. On the other hand, it is necessary to maintain the signal level at a high enough level for stable communication.
Bypassing this contradiction is possible using the special functions of the wireless network controllers.
Also worth noting is the fact that the company Zyxel is working to improve all that helps to achieve high-quality communication, without resorting to high costs.
Sources
Source: https://habr.com/ru/post/451768/
All Articles