“And so it will come down”: that cloud providers do not agree on personal data
The application for cloud services came to us somehow. We figured out in general what was required of us, and sent back a list of questions for further details. Then we analyzed the answers and understood: the customer wants to place personal data of the second level of security in the cloud. We answer him: "You have a second level of personal data, sorry, we can only make a private cloud." And he: “You know, but in company X, I can place everything in public”.

Photo by Steve Crisp, Reuters
Strange things! We went to the site of company X, studied their certification documents, shook our heads and understood: there are a lot of open questions in the placement of personnel and they should be properly ventilated. What we do in this post.
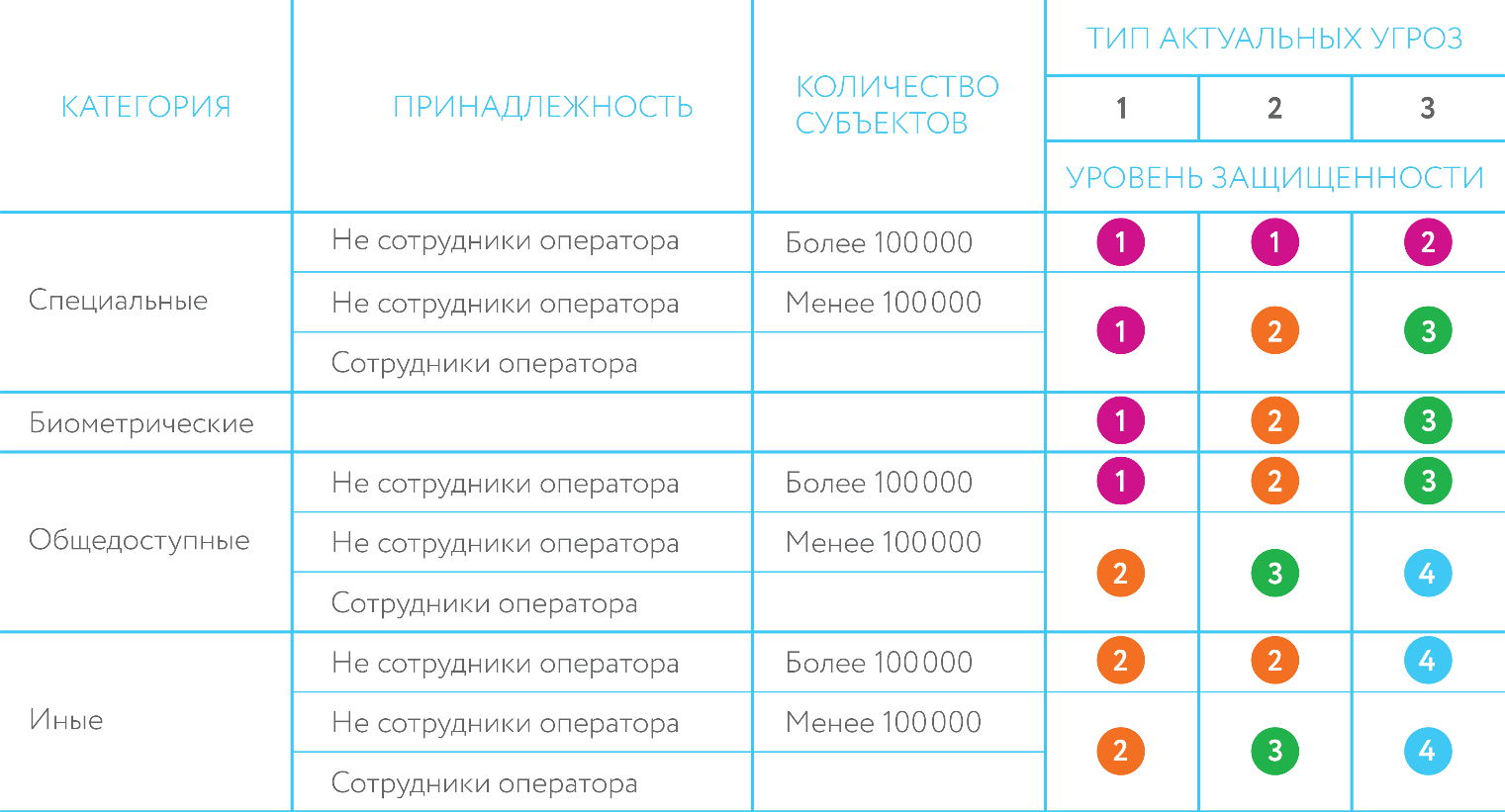
To begin with, let's look at the grounds on which personal data are generally related to a particular level of security. It depends on the category of data, on the number of subjects of this data that the operator stores and processes, as well as on the type of actual threats.
')
The definition of the types of actual threats is given in the Resolution of the Government of the Russian Federation No. 1119 dated November 1, 2012 “On the approval of requirements for the protection of personal data when they are processed in personal data information systems”:
The main thing in these definitions is the presence of undocumented (undeclared) capabilities. To confirm the absence of undocumented software capabilities (in the case of the cloud this is a hypervisor), FSTEC of Russia is certified. If the PD operator accepts that there are no such opportunities in the software, then the corresponding threats are irrelevant. Threats of the 1st and 2nd types are extremely rarely accepted by the PD operators.
In addition to determining the level of personal data protection, the operator should also identify specific actual threats to the public cloud and, based on the identified level of personal data protection and current threats, determine the necessary measures and means to protect against them.
In the FSTEC, all the main threats are clearly listed in the BDU (Threat Databank). Cloud infrastructure providers and certifiers use this database in their work. Here are examples of threats:
Protection from these threats is possible only with the help of the hypervisor, since it is he who manages the virtual resources. Thus, the hypervisor must be considered as a means of protection.
And in accordance with the order of FSTEC No. 21 dated February 18, 2013, the hypervisor must be certified for the absence of NDV by level 4, otherwise the use of personal data of level 1 and 2 with it will be illegal ( “p.12. ... To ensure 1 and 2 levels of protection of personal data, as well as to ensure 3 levels of protection of personal data in information systems for which threats of type 2 are relevant, information security tools are applied, the software of which has been tested not lower than level 4 of control I undeclared capabilities ").
The required level of certification, NDV-4, has only one hypervisor, the Russian development - Horizon VS. To put it mildly, not the most popular solution. Commercial clouds are usually built on the basis of VMware vSphere, KVM, Microsoft Hyper-V. None of these products are certified to NDV-4. Why? It is likely that obtaining such certification for manufacturers is not yet economically justified.
And it remains for us for Persons 1 and 2 levels in the public cloud only Horizon Sun. Sad but true.
At first glance, everything is quite strict: these threats should be eliminated by properly configuring the standard NDV-4 certified hypervisor protection mechanisms. But there is one loophole. In accordance with the Order of FSTEC No. 21 ( “ p. 2 The security of personal data when it is processed in the personal data information system (hereinafter referred to as the information system) is provided by the operator or person processing personal data on behalf of the operator in accordance with the legislation of the Russian Federation” ) Providers independently assess the relevance of possible threats and choose protection measures accordingly. Therefore, if the threats of UBI.44 and UBI.101 are not taken up to date, there will be no need to use a hypervisor certified according to NDV-4, which should provide protection against them. And this will be enough to obtain a certificate of compliance with the public cloud 1 and 2 levels of personal data protection, which Roskomnadzor will be completely satisfied with.
Of course, besides Roskomnadzor, the FSTEC can come in with verification, and this organization is much more meticulous in technical matters. She would certainly be interested in, why exactly the threats of UBI.44 and UBI.101 were considered irrelevant? But usually FSTEC undertakes verification only when it receives information about some bright incident. In this case, the federal service first comes to the operator of personal data - that is, the customer of cloud services. In the worst case, the operator receives a small fine - for example, for Twitter at the beginning of the year the penalty in a similar case was 5,000 rubles. Then FSTEC goes further to the cloud service provider. Which may well be deprived of a license due to non-compliance with regulatory requirements - and these are already completely different risks, both for the cloud provider and for its customers. But, I repeat, the FSTEC usually needs a clear reason to check. So cloud providers are willing to take risks. Until the first serious incident.
There is also a group of "more responsible" providers, who believe that it is possible to close all threats by adding a vGate-type add-on to the hypervisor. But in a virtual environment distributed among customers for some threats (for example, the above UBI.101), an effective protection mechanism can be implemented only at the level of the NDV-4 certified hypervisor, since any add-on systems for the regular functions of the hypervisor’s resource management work (in particular , RAM) do not affect.
We have a cloud segment implemented on a hypervisor certified by FSTEC (but without certification for NDV-4). This segment is certified, so that personal data of 3 and 4 security levels can be placed in the cloud based on it - there is no need to comply with the requirements for protection against undeclared capabilities. Here, by the way, is the architecture of our protected cloud segment:

Systems for personal data 1 and 2 levels of security, we sell only on dedicated equipment. Only in this case, for example, the threat of UBI.101 is really not relevant, since server racks that are not united by one virtual environment cannot influence each other even when placed in one data center. For such cases, we offer the rental service of dedicated equipment (it is also called Hardware as a service, equipment as a service).
If you are not sure what level of security is required for your personal data system, we also help in their classification.
Our small market survey showed that some cloud operators are quite willing to risk the security of customer data and their own future to receive an order. But we in these matters adhere to a different policy, which we briefly described just above. We will be happy to answer in the comments on your questions.

Photo by Steve Crisp, Reuters
Strange things! We went to the site of company X, studied their certification documents, shook our heads and understood: there are a lot of open questions in the placement of personnel and they should be properly ventilated. What we do in this post.
How things should work
To begin with, let's look at the grounds on which personal data are generally related to a particular level of security. It depends on the category of data, on the number of subjects of this data that the operator stores and processes, as well as on the type of actual threats.
')

The definition of the types of actual threats is given in the Resolution of the Government of the Russian Federation No. 1119 dated November 1, 2012 “On the approval of requirements for the protection of personal data when they are processed in personal data information systems”:
“Threats of the 1st type are relevant for the information system, if for it, including threats related to the presence of undocumented (non-declared) capabilities in the system software used in the information system.
Threats of the 2nd type are relevant for an information system, if for it, including threats related to the presence of undocumented (undeclared) capabilities in the application software used in the information system.
Threats of the 3rd type are relevant for an information system if it is relevant for threats that are not related to the presence of undocumented (non-declared) capabilities in the system and application software used in the information system. ”
The main thing in these definitions is the presence of undocumented (undeclared) capabilities. To confirm the absence of undocumented software capabilities (in the case of the cloud this is a hypervisor), FSTEC of Russia is certified. If the PD operator accepts that there are no such opportunities in the software, then the corresponding threats are irrelevant. Threats of the 1st and 2nd types are extremely rarely accepted by the PD operators.
In addition to determining the level of personal data protection, the operator should also identify specific actual threats to the public cloud and, based on the identified level of personal data protection and current threats, determine the necessary measures and means to protect against them.
In the FSTEC, all the main threats are clearly listed in the BDU (Threat Databank). Cloud infrastructure providers and certifiers use this database in their work. Here are examples of threats:
UBI.44 : “The threat is the possibility of violating the security of user data of programs operating inside a virtual machine by malicious software operating outside the virtual machine.” This threat is caused by the presence of hypervisor software vulnerabilities, which ensure the isolation of the address space used to store user data of programs running inside the virtual machine from unauthorized access by malicious software running outside the virtual machine.
Realization of this threat is possible provided that the malicious software successfully overcomes the borders of the virtual machine not only due to exploiting the hypervisor vulnerabilities, but also by implementing such an impact from lower (relative to the hypervisor) levels of the system functioning ”.
UBI.101 : “The threat lies in the possibility of unauthorized access to the protected information of one consumer of cloud services by another. This threat is due to the fact that, due to the nature of cloud technologies, cloud service consumers have to share the same cloud infrastructure. Realization of this threat is possible in case of making mistakes in the separation of cloud infrastructure elements between consumers of cloud services, as well as in isolating their resources and separating data from each other. ”
Protection from these threats is possible only with the help of the hypervisor, since it is he who manages the virtual resources. Thus, the hypervisor must be considered as a means of protection.
And in accordance with the order of FSTEC No. 21 dated February 18, 2013, the hypervisor must be certified for the absence of NDV by level 4, otherwise the use of personal data of level 1 and 2 with it will be illegal ( “p.12. ... To ensure 1 and 2 levels of protection of personal data, as well as to ensure 3 levels of protection of personal data in information systems for which threats of type 2 are relevant, information security tools are applied, the software of which has been tested not lower than level 4 of control I undeclared capabilities ").
The required level of certification, NDV-4, has only one hypervisor, the Russian development - Horizon VS. To put it mildly, not the most popular solution. Commercial clouds are usually built on the basis of VMware vSphere, KVM, Microsoft Hyper-V. None of these products are certified to NDV-4. Why? It is likely that obtaining such certification for manufacturers is not yet economically justified.
And it remains for us for Persons 1 and 2 levels in the public cloud only Horizon Sun. Sad but true.
How everything (in our opinion) actually works
At first glance, everything is quite strict: these threats should be eliminated by properly configuring the standard NDV-4 certified hypervisor protection mechanisms. But there is one loophole. In accordance with the Order of FSTEC No. 21 ( “ p. 2 The security of personal data when it is processed in the personal data information system (hereinafter referred to as the information system) is provided by the operator or person processing personal data on behalf of the operator in accordance with the legislation of the Russian Federation” ) Providers independently assess the relevance of possible threats and choose protection measures accordingly. Therefore, if the threats of UBI.44 and UBI.101 are not taken up to date, there will be no need to use a hypervisor certified according to NDV-4, which should provide protection against them. And this will be enough to obtain a certificate of compliance with the public cloud 1 and 2 levels of personal data protection, which Roskomnadzor will be completely satisfied with.
Of course, besides Roskomnadzor, the FSTEC can come in with verification, and this organization is much more meticulous in technical matters. She would certainly be interested in, why exactly the threats of UBI.44 and UBI.101 were considered irrelevant? But usually FSTEC undertakes verification only when it receives information about some bright incident. In this case, the federal service first comes to the operator of personal data - that is, the customer of cloud services. In the worst case, the operator receives a small fine - for example, for Twitter at the beginning of the year the penalty in a similar case was 5,000 rubles. Then FSTEC goes further to the cloud service provider. Which may well be deprived of a license due to non-compliance with regulatory requirements - and these are already completely different risks, both for the cloud provider and for its customers. But, I repeat, the FSTEC usually needs a clear reason to check. So cloud providers are willing to take risks. Until the first serious incident.
There is also a group of "more responsible" providers, who believe that it is possible to close all threats by adding a vGate-type add-on to the hypervisor. But in a virtual environment distributed among customers for some threats (for example, the above UBI.101), an effective protection mechanism can be implemented only at the level of the NDV-4 certified hypervisor, since any add-on systems for the regular functions of the hypervisor’s resource management work (in particular , RAM) do not affect.
How we work
We have a cloud segment implemented on a hypervisor certified by FSTEC (but without certification for NDV-4). This segment is certified, so that personal data of 3 and 4 security levels can be placed in the cloud based on it - there is no need to comply with the requirements for protection against undeclared capabilities. Here, by the way, is the architecture of our protected cloud segment:

Systems for personal data 1 and 2 levels of security, we sell only on dedicated equipment. Only in this case, for example, the threat of UBI.101 is really not relevant, since server racks that are not united by one virtual environment cannot influence each other even when placed in one data center. For such cases, we offer the rental service of dedicated equipment (it is also called Hardware as a service, equipment as a service).
If you are not sure what level of security is required for your personal data system, we also help in their classification.
Conclusion
Our small market survey showed that some cloud operators are quite willing to risk the security of customer data and their own future to receive an order. But we in these matters adhere to a different policy, which we briefly described just above. We will be happy to answer in the comments on your questions.
Source: https://habr.com/ru/post/451528/
All Articles