Inception bar: new phishing method
Good day, Habr! On the Internet, I came across an article in English "The inception bar: a new phishing method" by Jim Fisher. It describes an interesting phishing method, the mechanism of which is to use the screen space of the display line of the URL of the mobile version of Google Chrome. The original of the article is located on the experimental phishing page: you can independently access it and draw your own conclusion regarding the danger of the described method. Anyone who is interested, welcome under the cut!
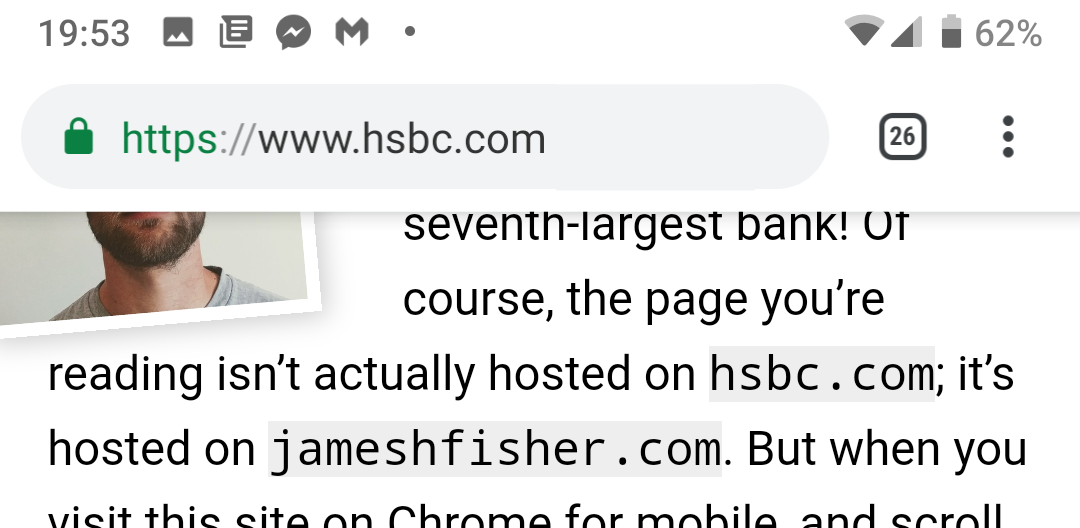
Welcome to HSBC, the seventh largest bank in the world. Of course, the page you are currently reading is not located on hsbc.com, but on jameshfisher.com. At the same time, if you visit this page from Chrome for mobile devices and look through it a little bit, the address line from hsbc.com is likely to appear on the page:
( link to the original page )
When scrolling down in the mobile version of Chrome, the browser hides the URL display string and transmits its screen space directly to the web page. Since the user identifies this space with a trustworthy UI, the phishing site uses it to impersonate another site, displaying a fake URL — the Inception string.
')
Further worse. Usually, when you scroll up, Chrome re-displays the URL. We can make him not do that! At that moment, when the browser hides the URL-string, we move the entire contents of the page to the so-called “scroll-camera” (English scroll jail) - a new element in which the “overflow: scroll” property is used. Now the user thinks that he is flipping the page up, although in fact he is flipping through the scrolling camera. As well as the sleeping heroes of the film “Beginning” (English Inception), the user believes that he is working from his browser, although in fact he is in the browser inside the browser.
Video:
Is the described mechanism a serious safety issue? To tell the truth, even I - the creator of the Inception-string - accidentally fell for this trick ( apparently, with my own experiments - a comment of the translator ). In this regard, I can imagine how many users can be deceived in this way, especially - less technically competent and knowledgeable. The user can verify the URL is correct only when the page loads. After he scrolled it down - there is not much chance of salvation.
While working on the presented concept, I took a screenshot of the address bar on the HSBC website from Google Chrome and placed it on this page. A page can define your browser and create an Inception string for it. With even more effort, the Inception string can be made interactive. Even if you could not fool a user on this page, you can try again after he enters something like gmail.com in the Inception line.
How to protect yourself from cheating? If you have doubts about the authenticity of a web page, do not just check the URL bar, but update (or even close and reopen) the page you doubt.
If the Google Chrome browser and others like it have a security problem, then how to solve it? There is a trade-off between increasing screen space and maintaining a trusted area on the screen, such as keeping a small part of the screen space above the death line instead of transferring the entire space to the web page. Chrome can use this small part of the space to display the fact that the address bar is hidden.
Describing a similar attack is a Fullscreen API based attack . Also - custom-cursor attack (2016) (English) , which works due to the fact that Chrome allows the web page to set its own cursor, which can be moved beyond the browser's viewport.
Welcome to HSBC, the seventh largest bank in the world. Of course, the page you are currently reading is not located on hsbc.com, but on jameshfisher.com. At the same time, if you visit this page from Chrome for mobile devices and look through it a little bit, the address line from hsbc.com is likely to appear on the page:
( link to the original page )

When scrolling down in the mobile version of Chrome, the browser hides the URL display string and transmits its screen space directly to the web page. Since the user identifies this space with a trustworthy UI, the phishing site uses it to impersonate another site, displaying a fake URL — the Inception string.
')
Further worse. Usually, when you scroll up, Chrome re-displays the URL. We can make him not do that! At that moment, when the browser hides the URL-string, we move the entire contents of the page to the so-called “scroll-camera” (English scroll jail) - a new element in which the “overflow: scroll” property is used. Now the user thinks that he is flipping the page up, although in fact he is flipping through the scrolling camera. As well as the sleeping heroes of the film “Beginning” (English Inception), the user believes that he is working from his browser, although in fact he is in the browser inside the browser.
Video:
Is the described mechanism a serious safety issue? To tell the truth, even I - the creator of the Inception-string - accidentally fell for this trick ( apparently, with my own experiments - a comment of the translator ). In this regard, I can imagine how many users can be deceived in this way, especially - less technically competent and knowledgeable. The user can verify the URL is correct only when the page loads. After he scrolled it down - there is not much chance of salvation.
While working on the presented concept, I took a screenshot of the address bar on the HSBC website from Google Chrome and placed it on this page. A page can define your browser and create an Inception string for it. With even more effort, the Inception string can be made interactive. Even if you could not fool a user on this page, you can try again after he enters something like gmail.com in the Inception line.
How to protect yourself from cheating? If you have doubts about the authenticity of a web page, do not just check the URL bar, but update (or even close and reopen) the page you doubt.
If the Google Chrome browser and others like it have a security problem, then how to solve it? There is a trade-off between increasing screen space and maintaining a trusted area on the screen, such as keeping a small part of the screen space above the death line instead of transferring the entire space to the web page. Chrome can use this small part of the space to display the fact that the address bar is hidden.
Describing a similar attack is a Fullscreen API based attack . Also - custom-cursor attack (2016) (English) , which works due to the fact that Chrome allows the web page to set its own cursor, which can be moved beyond the browser's viewport.
Source: https://habr.com/ru/post/449840/
All Articles