Inside the secret lab Ledger

Donjon is an information security laboratory for the French company Ledger. Ledger produces hardware wallets that store private keys of cryptocurrency owners. Malefactors hunt for these keys, and the hardware wallet, respectively, protects keys from leakage. How reliable? “Donjon” makes every effort to ensure that such a question does not even arise.

These people do everything so that the owners of Ledger wallets can sleep peacefully.
For a long time, the existence of the laboratory was kept secret. It has eight employees who prefer to remain anonymous. It is only known that these are “world-class specialists” in cyber security and smart cards. These "white hackers" are looking for vulnerabilities in Ledger software and hardware, as well as in competitors' products. The laboratory itself is located in the Paris office of the company. The workspace is protected by an alarm system, and only the personnel of the Donjon can go there.
')
In the laboratory are engaged in research of different types of attacks. Software attacks to which cryptographs are exposed usually consist in the study of the unusual behavior of systems and interfaces. A typical example of what Donjon is hunting for: the Heartbleed bug of the OpenSSL open cryptographic library. This famous vulnerability spread in 2012 and consisted in the possibility of unauthorized reading of server memory, extracting from it, including the private key. It was fixed only in 2014, after which Google launched its Project Zero to prevent similar threats.
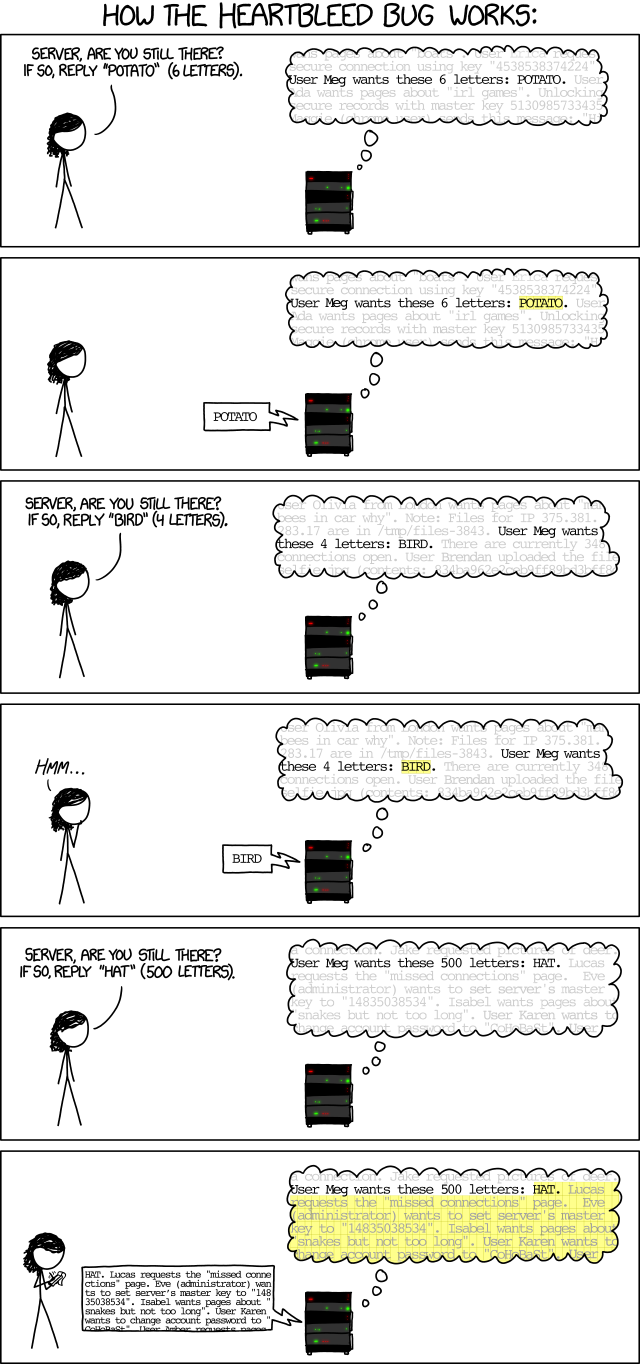
xkcd about what heartbleed is
Specialists of “Donjon” apply standard techniques: reverse engineering, statistical analysis, cryptography and fuzzing. Fuzzing is the transfer of random or unexpected data to a program. Last October, with its help, hackers found two vulnerabilities in the code of the crypto wallet of the rival firm Trezor.
These were buffer overflow errors. In both cases, the condition in the functions was incorrect; as often happens in such cases, the code worked, but not in the way its authors wanted. Read more about this in the Trezor blog .
Both vulnerabilities allowed you to remotely disable the wallet, attacking it through the browser, without user intervention. They affected firmware versions 1.6.2 and 1.6.3, and fixed errors in the new version.
As Ledger security director Charles Guillaume honestly said, the company develops only software from scratch. Chips and electronics provide third-party suppliers. Therefore, “Donjon”, like a medieval dungeon, is equipped with “torture” tools in order to methodically test wallets for physical vulnerabilities that may lead to data leakage.
Impressive and difficult attacks on third-party channels. Such attacks are aimed at the physical vulnerabilities of a working device. If an attacker steals or finds a lost cryptographic chain, he can measure the electromagnetic radiation and the change in power consumption of the device during the execution of the code. The hacker uses the received data to bypass the protection.

Attack on hardware wallet in progress
In practice, this idea allowed Ledger hackers to successfully crack the Trezor One wallet PIN. The PIN code is needed to access the device, and it gave a generous 15 attempts to enter the correct combination. "Donjon" learned to guess PIN for five times.
The following happened: a purse with a well-known PIN-code was disassembled, and then sensors were installed on its flash memory to measure power consumption and the electromagnetic field. Random numbers were entered into the wallet, and the oscilloscope wrote data from the probes. The data was marked as reactions to the correct and incorrect input, and then “fed” to the algorithm for learning.
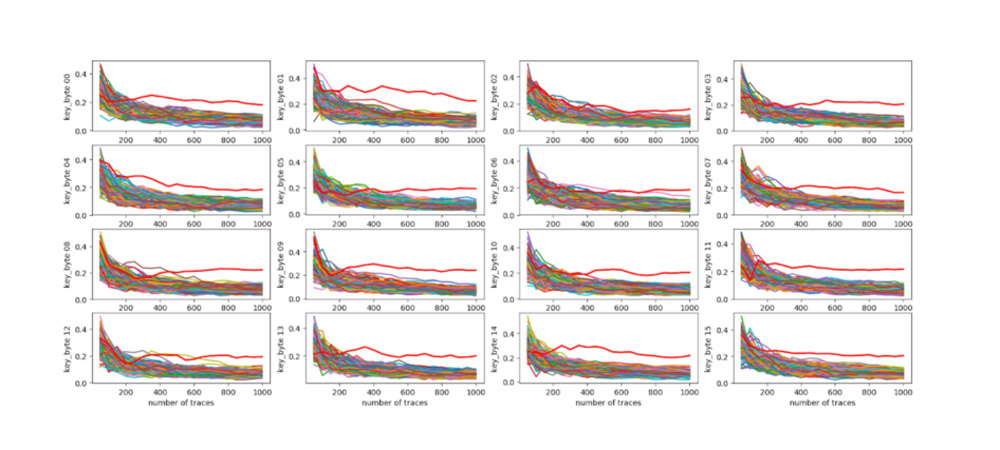
The results of the attack. The future has come, so the robot will understand them
Having taught the algorithm to distinguish different reactions, the researchers installed sensors on a second device. It played the role of a potentially stolen wallet, and exactly the same data was written from it when entering a PIN code. The algorithm that was trained on the first wallet recognized which numbers were correct and which were not, and guessed the PIN as a whole.
Since each new attempt to enter a PIN additionally has an increasing delay, such a hacking is a long process. To sort through all 15 codes, it might take a whole day of work. In case of success, the hacker gets unlimited access to other people's assets, so the game is worth the trouble.
The result of the experiment "Donzhon" again shared with competitors who took them very seriously and completely rewrote the PIN verification algorithm.
Setup for performing computation error attacks
Another favorite hacker technique is Ledger: an attack on calculation errors. This is a subtype of attack on third-party channels, which implies active intervention in the operation of the device: lowering and increasing the voltage in the circuit, increasing the clock frequency. A hardware wallet can be affected by ionizing radiation, a laser and an electromagnetic field. The attack allows you to bypass the PIN entry: increase the voltage, the device goes astray and skips checking the correctness of the entered numbers.
An experienced hacker will be able to extract other data that the hardware wallet should protect. For example, sid, a mnemonic phrase that opens access to all assets at once. This is a complicated but manageable procedure, and the Donjon team managed to do it with Keepkey, B Wallet, Trezor One and Trezor T purses.

This board in the "Donjon" is used to attack the cryptographic chips
Unfortunately, the details of the latest hacking "Donzhon" does not disclose. Hackers have a very strict “code of honor”: they first crack the device, then pass the details of the vulnerability to Ledger or competitors and wait for corrections. Only after that the public is notified that the problem existed.
Hackers reported back in December 2018 about the possibility of extracting seed from wallets. Vulnerability is still not fixed. According to Guillaume, in principle, nothing can be done with this defect, so the Donjon team will not tell you exactly how the wallets were hacked.
To prevent attacks on computational errors in the Ledger cryptographs, a separate Secure Element security chip is used. These chips are put on credit cards, SIM-cards and biometric passports. He detects an attempt to attack and actively responds to it. Secure Element also hides electromagnetic radiation and power consumption to prevent an attacker from “listening” to himself.
Chip ready to attack
In many other cryptographs, all calculations take place on a conventional microcontroller. In Ledger, such an architecture is considered unsafe, including because their own hackers "split" simple chips, like nuts. Competitors, including Trezor, countered the claim that for such a hacking, you must have physical access to the device and expert knowledge in the field of cryptography. Most holders of ethereum or bitcoin are much more worried because of remote attacks, so manufacturers concentrate on software security.

xkcd about hackers everyday life
A pragmatic approach is bearing fruit in the present. However, Ledger is looking to the future, which, as the company believes, cryptocurrency exists. The pickpocket, who pulled a flash drive out of a tourist's pocket yesterday, could not figure out that he had the key to wealth. In a year, he will know for sure who will sell the stolen hardware cryptocars to someone else hacking them.
With the popularization of hardware wallets, “markets” for the resale of stolen devices will inevitably appear. Exactly the same as they exist for resale of stolen credit card data. In Ledger, sleighs are being prepared in the summer and, therefore, they are already testing other crypto device manufacturers with ideas of complex hacks (with lasers and neural networks).

Ledger Nano S wallet: certified, secure and fully protected (wrench protection not included)
According to Eric Larshevek, CEO of Ledger, the point is not to look for flaws among competitors, but to increase the responsibility of the blockchain industry as a whole. Now the owner of any crypto wallet is his own bank and his own security system. Putting responsibility on the shoulders of the client is very convenient for companies that can not certify their goods at all.
Meanwhile, the Ledger Nano S wallet was the first on the market to be successfully certified by Agence Nationale de Sécurité des Systèmes d'Information, the French national cyber security agency. Ledger is not enough. “I think the industry needs more safety certification schemes,” says Guillaume. While there are no such schemes, Donjon makes every effort to ensure that Ledger hardware wallets are as secure as possible.
Written on Ledger. You can purchase hardware wallets of the French company in our online store.


Source: https://habr.com/ru/post/449690/
All Articles