Web developers write unsafe code by default
“If you want, I can encrypt the passwords”
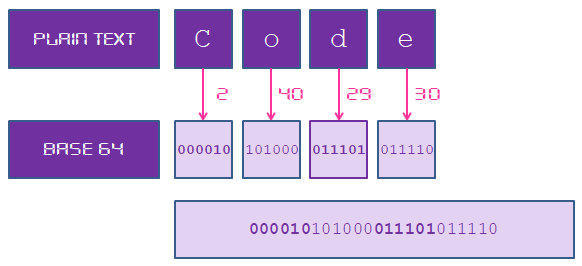
Some developers, who were instructed to use cryptography, used password base encryption with Base64.
When information about another data breach appears in the media, it is always puzzling why the company kept user passwords in clear text, did not protect the API, or made some other elementary mistake. Is it possible in our time such a security breach?
A new study from the University of Bonn (Germany) shows that freelance developers by default follow only unsafe practices, unless the customer requires more.
The researchers suggested that 260 Java developers at Freelancer.com develop a registration system for an imaginary social network that customers allegedly started to do. Of these, only 43 agreed to an order that provided for the use of Java, JSF, Hibernate and PostgreSQL technologies.
')
Half of the developers received 100 euros for the work, and half - 200 euros. Half of each of the two groups were instructed to use a secure password store, others did not.
Although the sample is obviously small, but the difference is so significant that it suggests some general trends. Here are some research findings:
- Among those who were not provided with instructions, 15 out of 18 kept passwords in clear text
- Three of the people who were assigned to use the secure vault also stored their passwords in clear text.
- Programmers who encrypted passwords used unsafe methods: 31 programmers used to encrypt methods such as Base64, MD5, SHA-1, etc.
- Only 12 freelancers applied secure methods such as bcrypt and PBKDF2.
8 people used to encrypt base64
10 - MD5
1 - SHA-1
3 - 3DES
3 - AES
5 - SHA-256
1 - HMAC / SHA1
5 - PBKDF2
7 - Bcrypt
The table below (incremented by click) shows the full results for each participant: how many days it took him to complete the task, how much of this time he spent on the implementation of security, and what encryption algorithm he applied. In the upper half of the table, those who have been given a direct instruction to encrypt information. Bold highlighted participants who first sent an unsafe solution, but then received additional instructions to implement a secure password store.
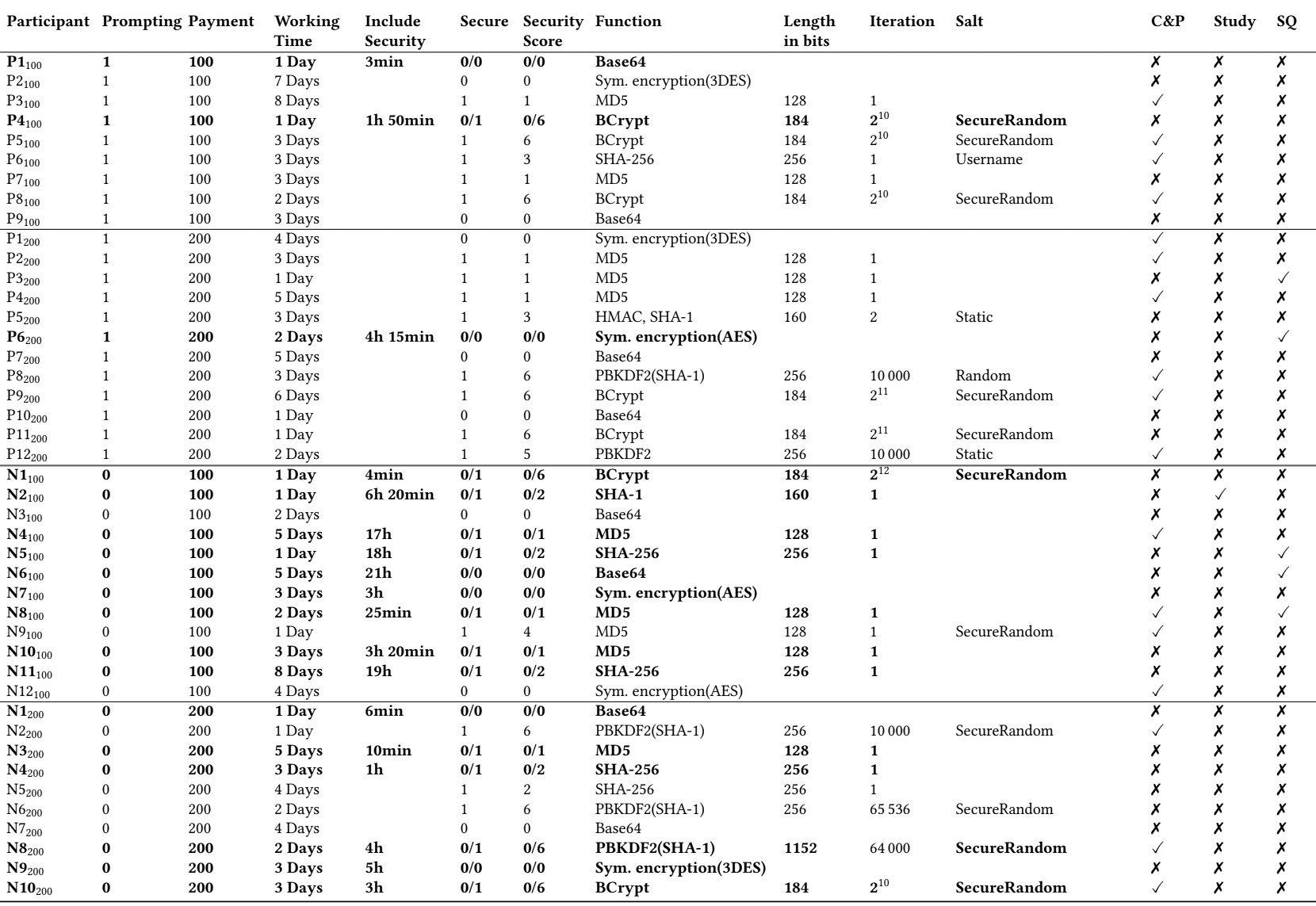
Overwhelmingly, programmers failed to implement basic security techniques, and 17 out of 43 copied code from random websites.
Only 15 developers used salt - a data string that is passed to the hash function along with the password, which significantly complicates brute force.
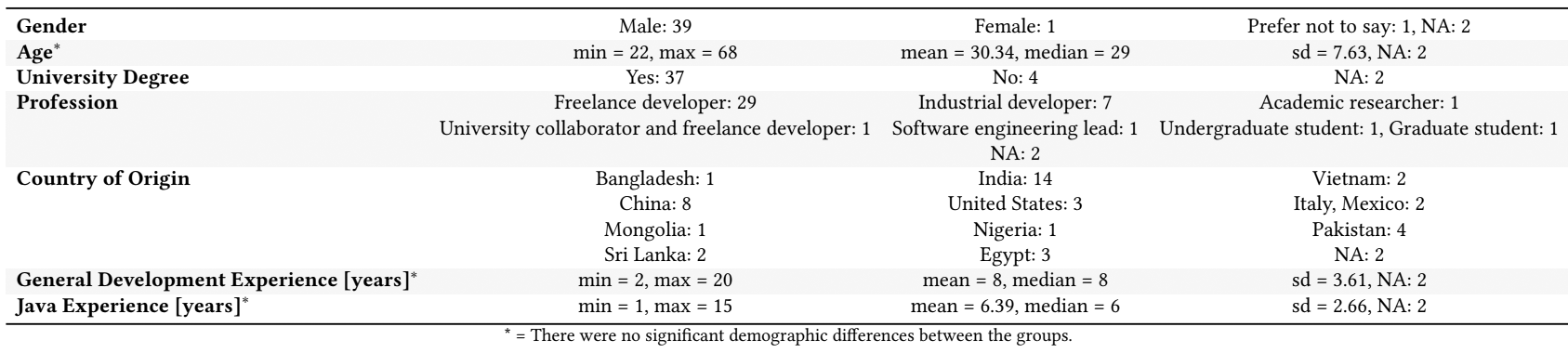
The table (you can increase by clicking) shows the demographic data of study participants. As you can see, these are mainly men, the average age is 30 years, from 11 countries (in two cases the country is not specified)
Low-paid and high-paid groups worked around the same level of quality.
In general, the research is rather depressing. It can be assumed that basic safety awareness among freelancers is incredibly low. Of the 18 participants who received special instructions to use cryptography, three decided to use Base64 and claimed, for example: "[I] encrypted everything, so the password is not visible" and "It is very difficult to decrypt."
Perhaps this behavior is specific only for freelancers, and staff members without outside instructions immediately try to make a safe decision? The study does not answer this question.

Source: https://habr.com/ru/post/449452/
All Articles