What will be with authentication and passwords? Translation of the Javelin "Strong Authentication Status" report with comments

Spoiler from the title of the report "The number of cases of using strong authentication has increased due to the threats of new risks and the requirements of regulators."
The research company Javelin Strategy & Research published the report The State of Strong Authentication 2019 (the original in pdf format can be downloaded here ). This report says: what percentage of US and European companies use passwords (and why few people use passwords now); why the percentage of using two-factor authentication based on cryptographic tokens is growing so fast; why one-time codes sent via SMS are unsafe.
Anyone who is interested in the topic of the present, past and future authentication in enterprises and user applications is welcome.
From translator
Alas, the language in which this report is written is rather “dry” and formal. And the fivefold use of the word “authentication” in one short sentence is not the curved arms (or brains) of the translator, but the whim of the authors. When translating from two options - to give readers more close to the original, or a more interesting text, I sometimes chose the first, and sometimes the second. But be patient, dear readers, the content of the report is worth it.
')
Some insignificant and unnecessary for the narrative pieces were removed, otherwise most would not have mastered the entire text. Those who want to get acquainted with the report "without cuts" can do it in the original language, following the link.
Unfortunately, the authors are not always careful with the terminology. So, one-time passwords (One Time Password - OTP), they are sometimes called "passwords", and sometimes "codes." Authentication methods are still worse. It is not always easy for an unprepared reader to guess that “authentication using cryptographic keys” and “strong authentication” are one and the same. I tried to maximally unify the terms, moreover, in the report itself there is a fragment with their description.
Nevertheless, the report is highly recommended for reading, because it contains unique research results and correct conclusions.
All the facts and figures are given without any changes, and if you disagree with them, then it’s better not to argue with the translator, but with the authors of the report. But my comments (made up as quotations, and in the text are marked by Italian ) are my value judgment and for each of them I will be happy to argue (as well as on the quality of the translation).
Overview
Nowadays, digital channels of communication with customers are more important for business than ever. And within the enterprise, communication between employees is more focused on the digital environment than ever before. And how safe these interactions will be depends on the chosen method of user authentication. Attackers use weak authentication for mass hacking of user accounts. In response, regulators are tightening standards to make businesses better protect user accounts and data.
Threats related to authentication, extend not only to consumer applications, attackers can gain access to the application, working inside the enterprise. Such an operation allows them to impersonate corporate users. Attackers using weak authentication access points can steal data and perform other fraudulent activities. Fortunately, there are measures to combat this. Strong authentication will help to significantly reduce the risk of attack by an attacker, both on consumer applications and on business systems of enterprises.
This study explores: how enterprises implement authentication to protect user applications and enterprise business systems; factors that they take into account when choosing a solution for authentication; the role that strong authentication plays in their organizations; the benefits that these organizations receive.
Summary
Main conclusions
Since 2017, the percentage of strong authentication has increased dramatically. With the growing number of vulnerabilities affecting traditional authentication solutions, organizations are increasing their authentication capabilities with strong authentication. The number of organizations using multifactor authentication using cryptography (MFA) has tripled since 2017 for consumer and has increased by almost 50% for enterprise applications. The fastest growth is in mobile authentication due to the increasing availability of biometric authentication.
Here we see an illustration of the saying “until the thunder clap - the peasant does not cross.” When experts warned of the unreliability of passwords, no one was in a hurry to implement two-factor authentication. As soon as hackers started stealing passwords, people began to implement two-factor authentication.
True individuals are much more active in introducing 2FA. Firstly, it is easier for them to calm their fears, relying on the biometric authentication built into smartphones, in fact, very unreliable. Organizations need to invest in the acquisition of tokens and carry out work (in fact, very simple) to implement them. And secondly, about the leakage of passwords from services such as Facebook and Dropbox did not write just lazy, but the stories about how they stole passwords (and what happened next) in organizations, the CIOs of these organizations will not share under any circumstances.
Those who do not use strong authentication underestimate their risk to businesses and customers. Some organizations that currently do not use strong authentication tend to view logins and passwords as one of the most effective and easy-to-use user authentication methods. Others do not see the value of digital assets they own. After all, it is worth considering that cybercriminals are interested in any consumer and business information. Two thirds of the companies that use only passwords to authenticate their employees do this because they believe that passwords are good enough for the type of information they protect.
However, passwords are on the path to the grave. Over the past year, dependence on passwords has significantly decreased, both for consumer and corporate applications (from 44% to 31%, and from 56% to 47%, respectively), as organizations expand the use of traditional MFA and strong authentication.
But if you assess the situation as a whole, then the vulnerable authentication methods still prevail. For user authentication, about a quarter of organizations use SMS OTP (one-time password) along with secret questions. As a result, to protect against vulnerabilities, additional security measures have to be implemented, which increases costs. The use of much more reliable authentication methods, such as hardware cryptographic keys, is much less common, in about 5% of organizations.
The evolving regulatory environment promises to accelerate the implementation of strong authentication for consumer applications. With the introduction of PSD2, as well as new data protection regulations in the EU and several US states, such as California, companies feel that it is getting hot. Nearly 70% of companies agree that they face strong regulatory pressure to provide strong authentication for their customers. More than half of enterprises believe that in a few years their authentication methods will not be sufficient to meet regulatory standards.
The difference in the approaches of the Russian and US-European legislators to the protection of personal data of users of programs and services is clearly noticeable. Russian say: dear owners of services, do what you want and how you want, but if your admin merges the base, we will punish you. They say abroad: you must introduce a set of measures that will not allow you to merge the base. That is why requirements for the presence of strong two-factor authentication are being implemented there with might and main.
True, it is far from a fact that at one point our legislative machine will not come to its senses and will not take into account western experience. Then it will turn out that everyone needs to implement 2FA, which complies with Russian cryptographic standards, and urgently.
Creating a strong authentication framework allows companies to shift the focus from meeting regulatory requirements to meeting customer needs. For those organizations that still use simple passwords or receiving codes via SMS, the most important factor when choosing an authentication method will be compliance with regulatory requirements. But those companies that already use strong authentication can focus on choosing those authentication methods that increase customer loyalty.
When choosing a corporate authentication method within the enterprise, the requirements of regulators are no longer a significant factor. In this case, simplicity of integration (32%) and cost (26%) are much more important.
In the era of phishing, attackers can use corporate e-mail for fraud in order to fraudulently gain access to data, accounts (with appropriate access rights), and even to convince employees to make a money transfer to his account. Therefore, corporate email accounts and portals should be especially well protected.
Google has strengthened its protection by implementing strong authentication. More than two years ago, Google published a report on the implementation of two-factor authentication based on cryptographic security keys according to the FIDO U2F standard, reporting impressive results. According to the company, no phishing attacks were carried out against more than 85,000 employees.
Recommendations
Implement strong authentication for mobile and online applications. Multifactor authentication based on cryptographic keys much more reliably protects against hacking than traditional MFA methods. In addition, the use of cryptographic keys is much more convenient, because you do not need to use and transfer additional information - passwords, one-time passwords or biometric data from the user's device to the authentication server. In addition, standardizing authentication protocols makes it much easier to implement new authentication methods as they emerge, reducing usage costs and protecting against more sophisticated fraud schemes.
Get ready for sunset one-time passwords (OTP). Vulnerabilities inherent in OTP are becoming increasingly apparent, in an environment where cybercriminals use social engineering, smartphone cloning and malware to compromise these authentication tools. And if OTP in some cases have certain advantages, it is only from the point of view of universal accessibility for all users, but not from the point of view of security.
It is impossible not to notice that the receipt of codes via SMS or Push-notifications, as well as the generation of codes using programs for smartphones - this is the use of those most one-time passwords (OTP) for which we are offered to prepare for sunset. From a technical point, the decision is very correct, because a rare cheater does not try to find out a one-time password from a trusting user. But I think that manufacturers of such systems will cling to the dying technology to the last.
Use strong authentication as a marketing tool to increase customer confidence. Strong authentication can not only improve the actual security of your business. Informing customers that your business uses strong authentication can reinforce public perception of the security of this business - an important factor when there is a significant customer demand for strong authentication methods.
Conduct a thorough inventory and assessment of the importance of corporate data and protect them in accordance with the importance. Even low-risk data, such as customer contact information ( no, the truth is, “low-risk” is written in the report, it’s very strange that they underestimate the importance of this information ) can bring considerable value to fraudsters and cause problems for the company. .
Use strong enterprise authentication. A number of systems are the most attractive targets for criminals. These include internal and Internet-connected systems, such as an accounting program or corporate data storage. Strong authentication does not allow attackers to gain unauthorized access, and also allows you to determine exactly who of the employees committed the malicious activity.
What is strong authentication?
When using strong authentication, several methods or factors are used to authenticate the user:
- Knowledge Factor: a shared secret between the user and the subject of user authentication (for example, passwords, answers to secret questions, etc.)
- Ownership factor: a device that only the user has (for example, a mobile device, a cryptographic key, etc.)
- Inherent inherent factor: the physical (often biometric) characteristics of the user (for example, fingerprint, iris pattern, voice, behavior, etc.)
The need to hack several factors significantly increases the likelihood of failure for attackers, since bypassing or deceiving various factors requires the use of several types of hacking tactics, for each factor separately.
For example, with 2FA “password + smartphone”, an attacker can perform authentication by looking at the user's password and making an exact software copy of his smartphone. And it is much more difficult than just stealing a password.
But if a password and a cryptographic token are used for 2FA, the copying option does not work here - it is impossible to duplicate the token. The scammer will need to steal the token from the user unnoticed. If the user notices the loss in time and notifies the admin, then the token will be blocked and the fraudster’s works will be in vain. That is why for the ownership factor you need to use specialized protected devices (tokens), not general devices (smartphones).
Using all three factors will make this authentication method quite expensive to implement and rather uncomfortable to use. Therefore, two of the three factors are commonly used.
The principles of two-factor authentication are described in more detail here in the “How two-factor authentication works” block.
It is important to note that at least one of the authentication factors used for strong authentication must use public key cryptography.
Strong authentication gives much more serious protection than single-factor authentication based on classic passwords and traditional MFA. Passwords can be overlooked or intercepted using keyloggers, phishing sites, or social engineering-based attacks (when a deceived victim herself tells her password). And the owner of the password will not know anything about the fact of theft. Traditional MFA (including OTP codes, binding to a smartphone or SIM card) can also be quite easily cracked, since it is not based on public key cryptography (by the way, there are many examples when using the same social engineering techniques scammers persuaded users tell them one-time password ).
Fortunately, since last year, the use of strong authentication and traditional MFA is gaining momentum in both consumer and corporate applications. The use of strong authentication in consumer applications has grown particularly rapidly. If in 2017 only 5% of companies used it, then in 2018 it is already three times as much - 16%. This can be explained by the increased availability of tokens that support public key cryptography algorithms (Public Key Cryptography - PKC). In addition, the increased pressure of European regulators after the adoption of new information protection rules, such as PSD2 and GDPR, had a strong effect even outside Europe ( including in Russia ).
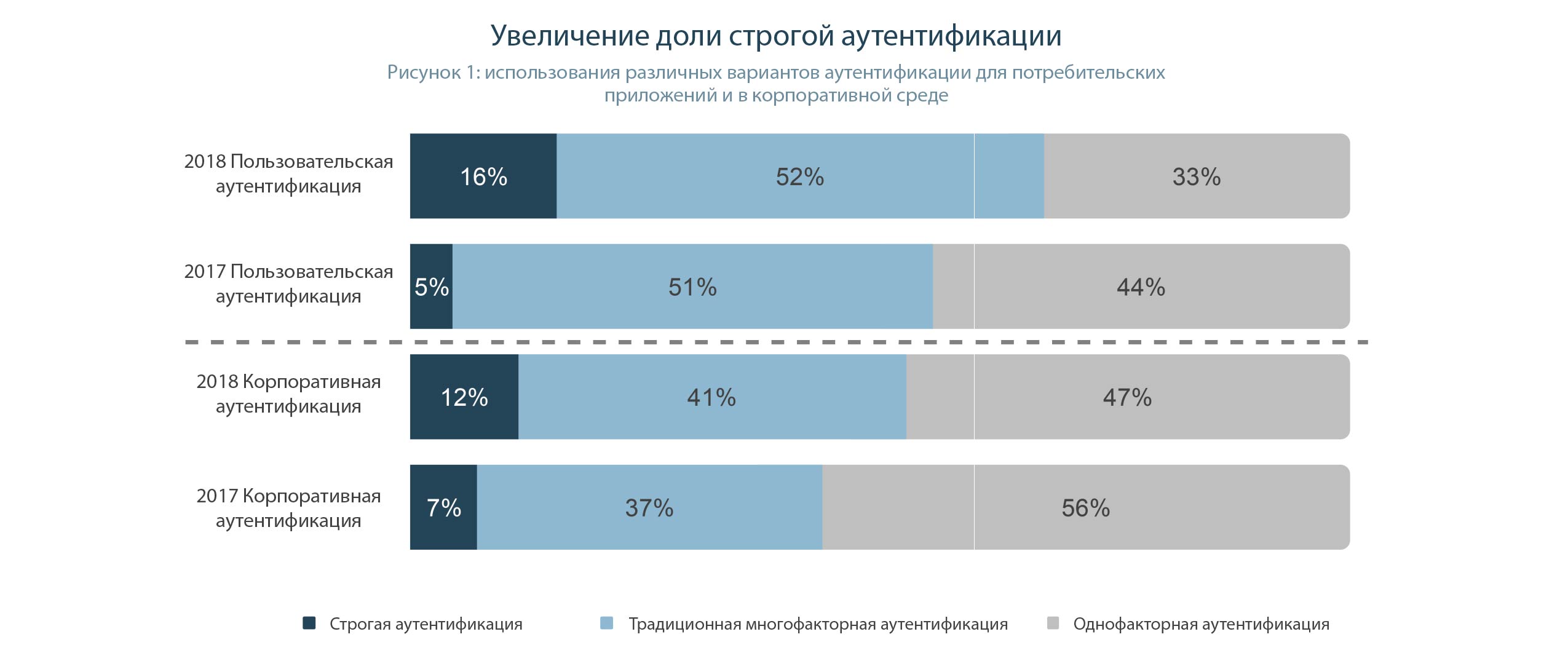
Let's take a closer look at these numbers. As we see, the percentage of private traders using multifactor authentication increased by an impressive 11% over the year. And it happened, obviously, at the expense of password lovers, since the numbers of those who believe in the security of push notifications, SMS and biometrics have not changed.
But with two-factor authentication for corporate use, everything is not so good. First, judging by the report, only 5% of employees were transferred from password authentication to tokens. And secondly, the number of those who in the corporate environment uses alternatives to the MFA has grown by 4%.
I'll try to play analytics and give my interpretation. In the center of the digital world of individual users is a smartphone. Therefore, it is not surprising that most of them use the capabilities provided by the device - biometric authentication, SMS and Push notifications, as well as one-time passwords generated by applications on the smartphone itself. People usually do not think about safety and reliability when using their usual tools.
That is why the percentage of users of primitive "traditional" authentication factors remains unchanged. But those who previously used passwords understand how much they risk, and when choosing a new authentication factor, they stop at the newest and most secure version - the cryptographic token.
As for the corporate market, it is important to understand which system is being authenticated. If the login to the Windows domain is implemented, cryptographic tokens are used. Opportunities for their use for 2FA are already laid in Windows and Linux, and the alternative options are long and difficult to implement. Here you have the migration of 5% from passwords to tokens.
And the implementation of 2FA in the corporate information system very much depends on the qualifications of the developers. And developers are much easier to take ready-made modules for generating one-time passwords than to understand the work of cryptographic algorithms. As a result, even incredibly security-critical applications like the Single Sign-On or Privileged Access Management systems use OTP as the second factor.
Multiple vulnerabilities in traditional authentication methods
Although many organizations remain dependent on obsolete single-factor systems, vulnerabilities in traditional multifactor authentication are becoming increasingly apparent. One-time passwords are usually from six to eight characters in length, delivered via SMS, remain the most common form of authentication (of course, in addition to the password knowledge factor). And if the words "two-factor authentication" or "two-step verification" are mentioned in the popular press, they almost always refer to authentication using one-time SMS passwords.
Here the author is a little mistaken. Delivery of one-time passwords via SMS has never been a two-factor authentication. This is in its pure form the second stage of two-stage authentication, where the first stage is to enter a login and password.
In 2016, the National Institute of Standards and Technology (NIST) updated its authentication rules to eliminate the use of one-time passwords sent via SMS. However, these rules were significantly relaxed after protests in the industry.
So, follow the plot. The American regulator rightly recognizes that the outdated technology is not capable of ensuring the safety of users and introduces new standards. Standards designed to protect users of online and mobile applications (including banking). The industry is wondering how much money it will have to pay for the purchase of truly reliable cryptographic tokens, for reworking applications, for deploying a public-key infrastructure and “rearing”. On the one hand, users were convinced of the reliability of one-time passwords, and on the other hand, attacks on NIST were underway. As a result, the standard was softened, and the number of hacks, password theft (and money from banking applications) increased dramatically. But the industry did not have to shell out.
Since then, the weaknesses inherent in SMS OTP have become more apparent. Fraudsters use various ways to compromise SMS-messages:
- SIM card duplication. The attackers create a copy of the SIM (with the help of employees of the cellular operator, or independently, using special software and hardware ). As a result, the attacker receives an SMS with a one-time password. In one particularly famous case, hackers even managed to compromise the AT & T account of the investor of cryptocurrency Michael Turpin, and steal nearly $ 24 million in cryptocurrency. As a result, Turpin said that AT & T was to blame because of the weak verification measures that led to the duplication of the SIM card.
Awesome logic. That is the truth is only AT & T's fault? No, the fault of the mobile operator is that the sellers in the salon of communication issued a duplicate of SIM cards, undoubtedly. What about the cryptocurrency exchange authentication system? Why didn't they use strong cryptographic tokens? Money for the introduction was a pity? And Michael himself is not to blame? Why did he not insist on changing the authentication mechanism or not using only those exchanges that implement two-factor authentication based on cryptographic tokens?
The introduction of truly reliable authentication methods is delayed because of the fact that before the hacking, users show amazing carelessness, and after that they blame anyone and everything except their ancient and “holey” authentication technologies for their troubles - Malware (malware). One of the earliest functions of mobile malware was intercepting and sending text messages to attackers. Also, man-in-the-browser and man-in-the-middle (man-in-the-middle) attacks can capture one-time passwords when they are entered on infected laptops or desktop devices.
When the Sberbank application in your smartphone blinks with a green icon in the status bar, it also searches for malware on your phone. The purpose of this event is to turn the untrusted execution environment of a typical smartphone into, at least some sideways, trusted.
By the way, a smartphone, as an absolutely untrusted device, on which anything can be performed, is another reason to use only hardware tokens for authentication, which are protected and free from viruses and trojans. - Social engineering. When fraudsters know that the victim has one-time passwords via SMS, they can directly contact the victim, posing as a trusted organization, such as her bank or credit union, to deceive the victim and force her to provide the code she just received.
I repeatedly encountered this type of fraud in person, for example, when I tried to sell something on a popular online flea market. I myself really mocked the scammer who tried to fool me. But alas, I regularly read the news as another victim of fraudsters "did not think," the confirmation code reported and lost a large amount. And all this because the bank simply does not want to get involved in the implementation of cryptographic tokens in its applications. After all, if something happens, then the customers "are to blame."
While alternative methods for delivering one-time passwords may mitigate some of the vulnerabilities in this authentication method, other vulnerabilities remain in place. Standalone code generation applications are the best protection against interception, since even malicious programs practically cannot directly interact with the code generator ( seriously? The report author forgot about remote control? ), But OTP can still be intercepted when entered into the browser ( for example, using keylogger ), via a hacked mobile application; and can also be obtained directly from the user through social engineering.
The use of several risk assessment tools, such as device recognition ( identifying attempts to perform operations with devices not belonging to the legal user ), geolocation (a user who was just in Moscow trying to perform an operation from Novosibirsk ) and behavioral analytics, is of great importance for eliminating vulnerabilities, but one solution is not a panacea. For each situation and data type, you must carefully assess the risks and choose which authentication technology should be used.
No authentication solution is a panacea.
Figure 2. Authentication options table
| Authentication | Factor | Description | Key Vulnerabilities |
| Password or PIN | Knowledge | A fixed value, which may include letters, numbers and a number of other characters | Can be intercepted, overlooked, stolen, picked up or hacked. |
| Knowledge Based Authentication | Knowledge | Questions, answers to which only a legal user can know | Can be intercepted, picked up, obtained using the methods of social engineering |
| Hardware OTP ( example ) | Possession | Special device that generates one-time passwords | The code can be intercepted and repeated, or the device can be stolen. |
| Software OTP | Possession | Application (mobile, accessible through a browser, or sending codes by e-mail), which generates one-time passwords | The code can be intercepted and repeated, or the device can be stolen. |
| SMS OTP | Possession | One-time password delivered via SMS text message | The code can be intercepted and repeated, either a smartphone or a SIM card can be stolen, or the SIM card can be duplicated. |
| Smart cards ( example ) | Possession | A card that contains a cryptographic chip and secure key storage that uses a public key infrastructure for authentication. | Can be physically stolen ( but the attacker will not be able to use the device without knowledge of the PIN code; in the case of several incorrect input attempts, the device will be blocked ) |
| Security keys - tokens ( example , another example ) | Possession | A USB device that contains a cryptographic chip and secure key storage that uses a public key infrastructure for authentication. | Can be physically stolen (but the attacker will not be able to use the device without knowledge of the PIN code; in the case of several incorrect input attempts, the device will be blocked) |
| Snapping to device | Possession | A process that creates a profile, often using JavaScript, or using tokens such as cookies and Flash Shared Objects to ensure that a particular device is used. | Markers can be stolen (copied), also the characteristics of a legal device can be imitated by an attacker on his device. |
| Behavior | Integrity | Analyzed how the user interacts with the device or program. | Behavior can be simulated |
| Fingerprints | Integrity | The stored fingerprints are compared with read out optically or electronically. | The image can be stolen and used for authentication. |
| Eye scan | Integrity | The characteristics of the eye, such as the pattern of the iris of the pupil, are compared with the new scans obtained by the optical method | The image can be stolen and used for authentication. |
| Face recognition | Integrity | Characteristics of the face are compared with the new scans obtained by the optical method | The image can be stolen and used for authentication. |
| Voice recognition | Integrity | The characteristics of the recorded voice sample are compared with the new samples. | Record can be stolen and used for authentication, or emulated |
See you!
Source: https://habr.com/ru/post/449442/
All Articles