And again the wolf in sheep's clothing
Phishing site should look plausible enough and correspond to any legend of intruders. Often, as a legend, they choose something related to security, such resources cause more trust among potential victims. And here is a fresh example of this approach: sbersecure.ru .
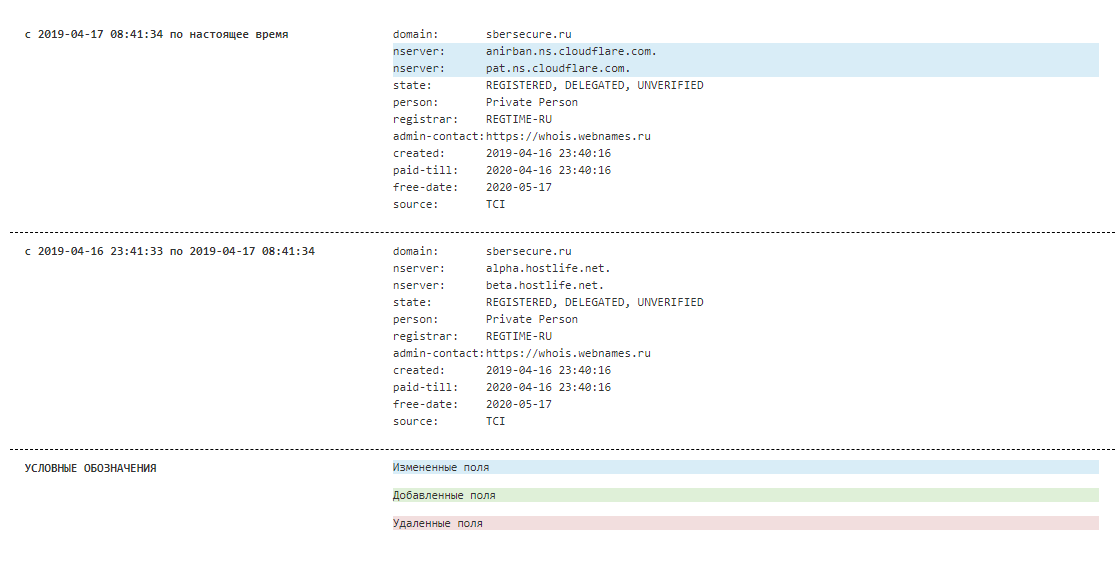
Events around the site developed rapidly. The domain name was registered on the evening of April 16, and the next day a phishing site was on it. Initially, the servers of the Russian Hostlife host were listed as the DNS, however, after only 9 hours, the addresses of CloudFlare, a company that does not need to be presented, appeared in the NS records. On April 17, at 15:00 Moscow time, the resource acquired an encryption certificate issued by the same CloudFlare.
')
Let's get acquainted with the phishing site closer.
To create a resource, a rather popular way to partially copy the original site was used. In this case, the attackers took as a basis the “Ombudsman’s Office” page of the bank, changing the words “Ombudsman’s Office” to “Client’s Security Service”.
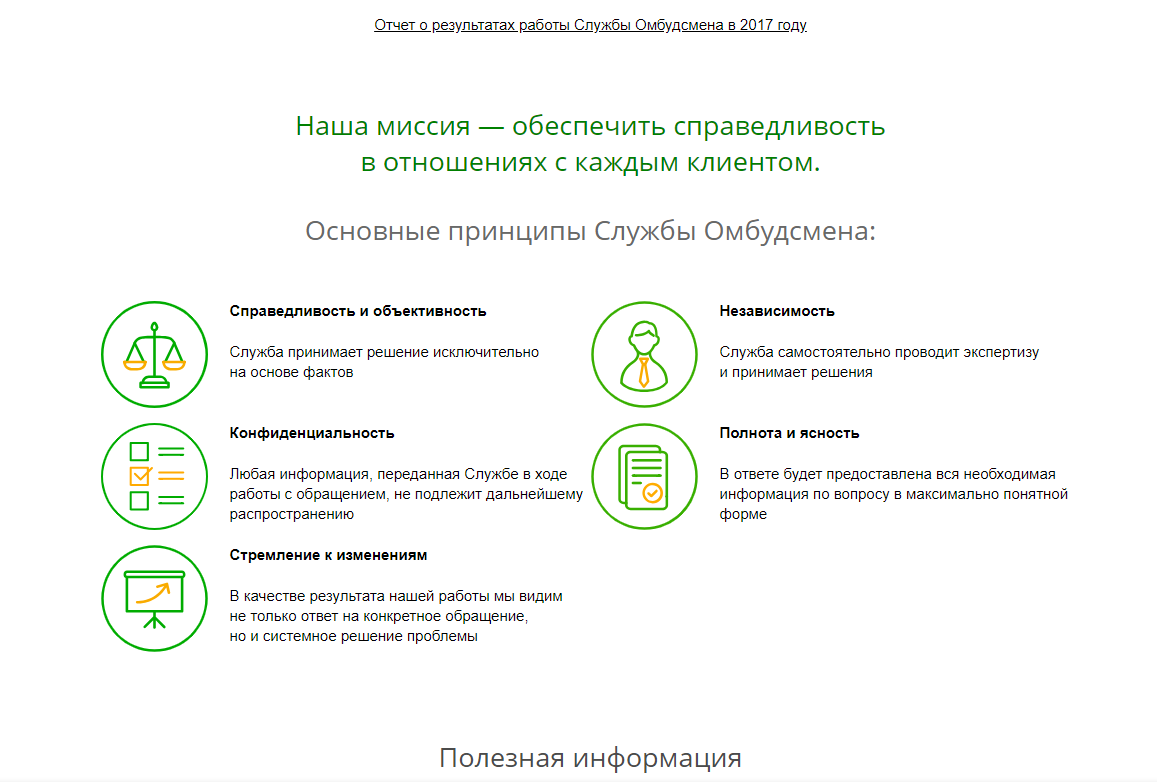
Here is the original Ombudsman Service page.
But a phishing site.
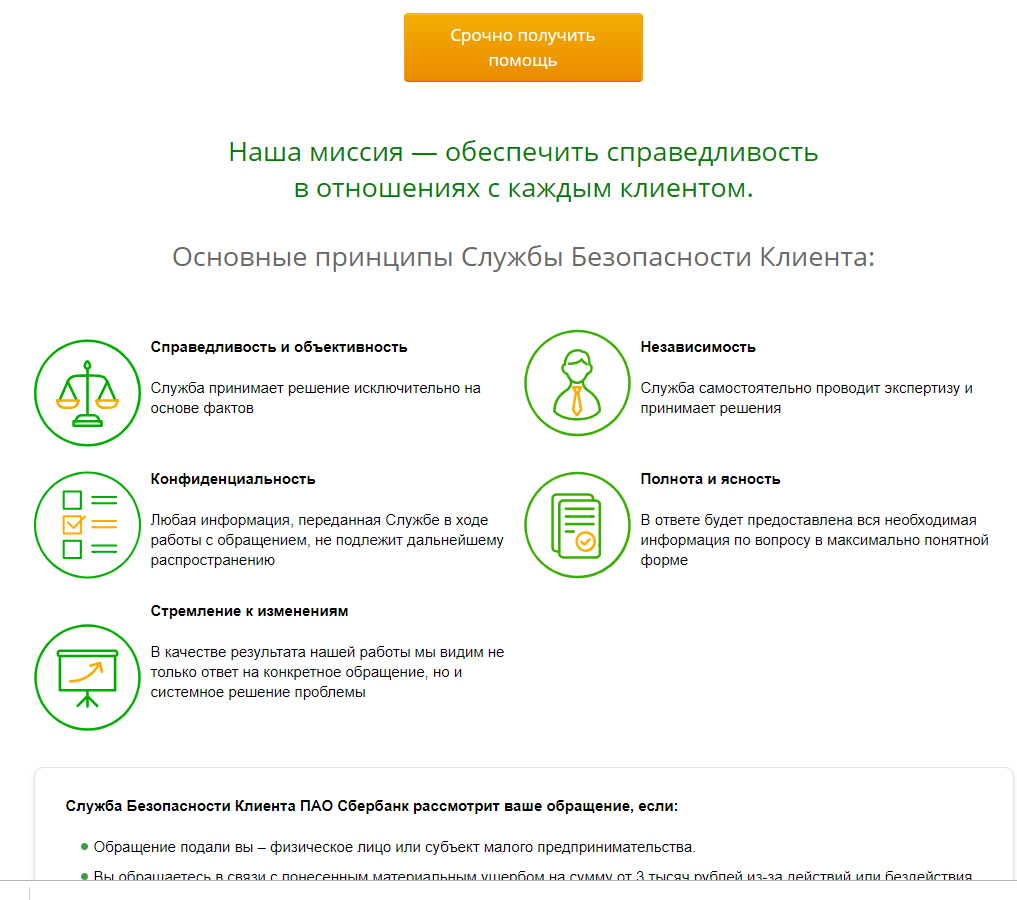
At the same time, the changes affected only the central part of the site; the header, context menus and footer completely repeat the original design. All links, including the link to the authorization page in the Sberbank Online service, lead to the real Sberbank website.
General view of a phishing site.

A key element of a phishing resource is a button that says "Urgently get help." Clicking on it redirects us to the sbersecure.ru/help.html page. Parallel runs a whole bunch of java-scripts, most of which do not work. Curiously, one of the scripts accesses the resource ibbe.group-ib.ru . Apparently, this is the Secure Bank service script from Group-IB, inherited from a phishing resource from this site of the bank.
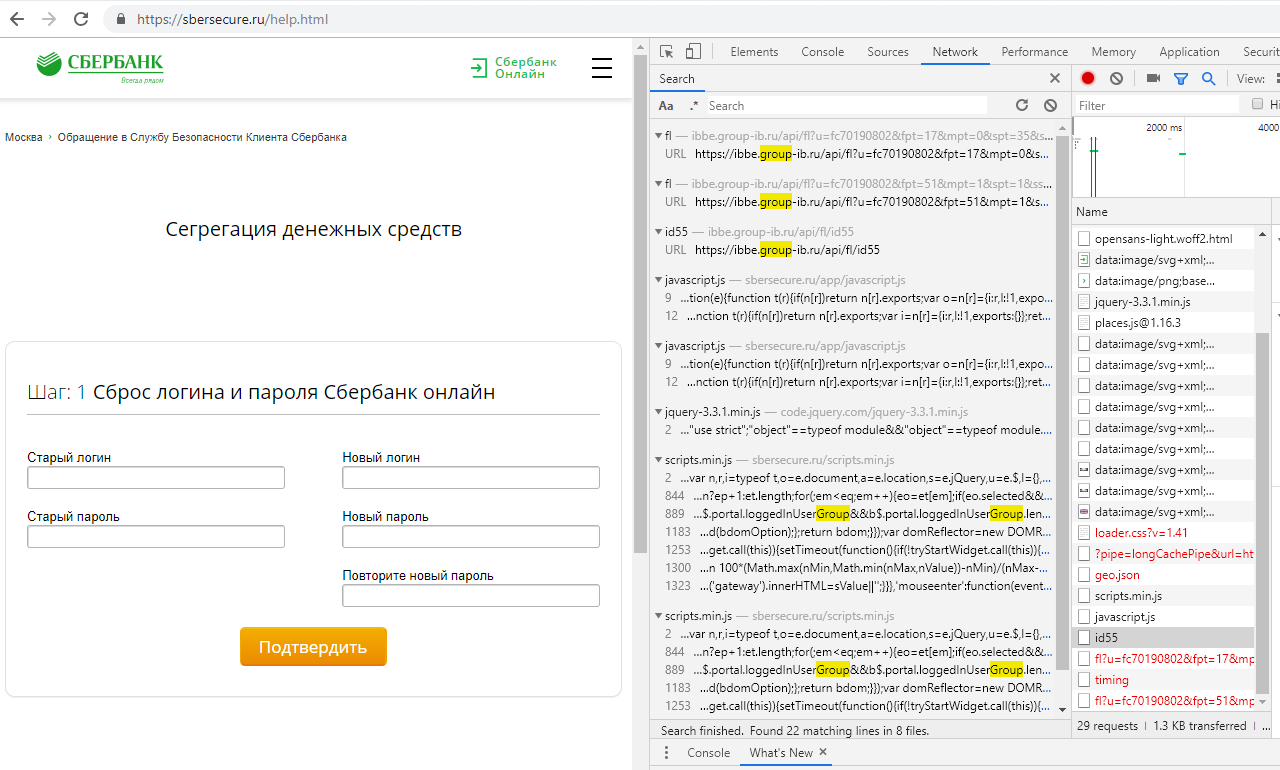
The second page of the resource is called “Segregation of Cash”. April 18, when this site came into view, it looked like this.
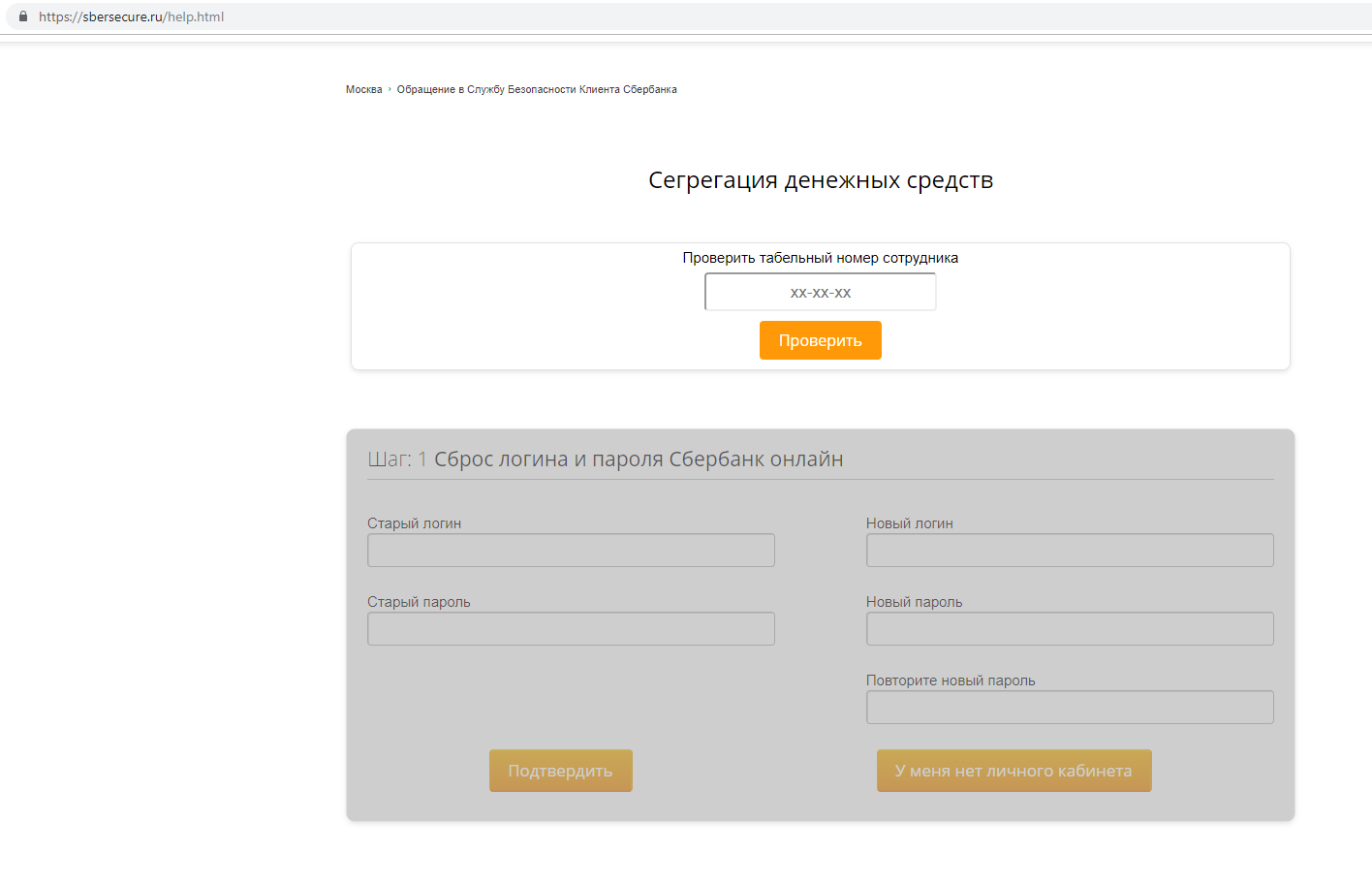
Attempts to enter an arbitrary personnel number of an employee did not lead to anything, while the second part, “Resetting login and password Sberbank online,” was inactive.
Over the weekend, the page has changed. The form for entering the personnel number has disappeared, but a form has become available intended to change the login and password from the personal account of the online bank. This clarifies the possible use of phishing resources.
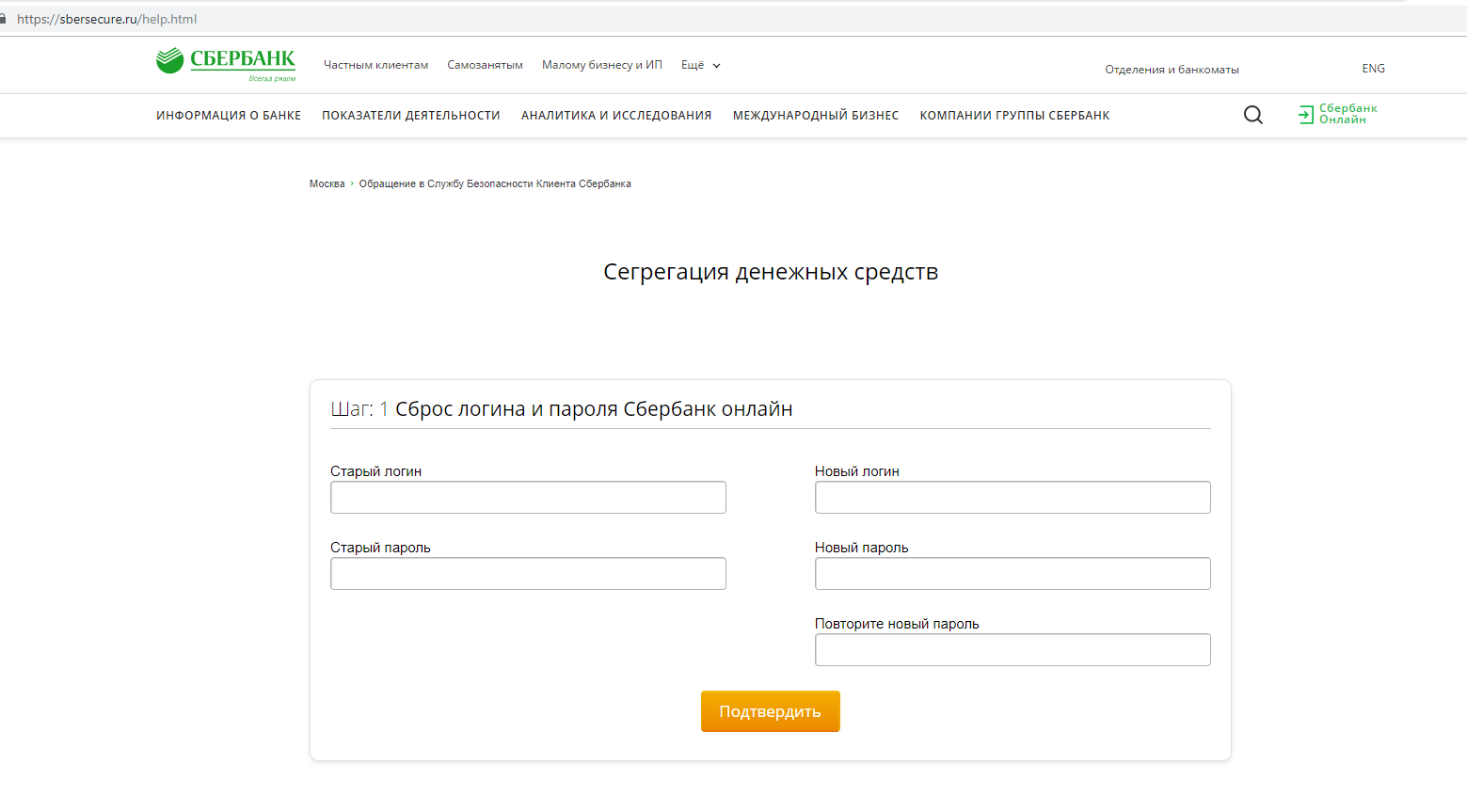
It would be foolish not to see what happens with the submitted data, so fill out the form with arbitrary words and click on the "Confirm" button.
Pressing the button in open form sends the following information to the sbersecure.ru/php/add_login_bank.php script: login and password from the Sberbank.Online service, information about the region of residence and IP address. Information from the fields for entering a new login and a new password is ignored for obvious reasons. After that, a redirect to the sbersecure.ru/get_info.html page occurs , where we are offered to enter the first name, last name, phone number, as well as card details, including the number, CVV and its validity period.
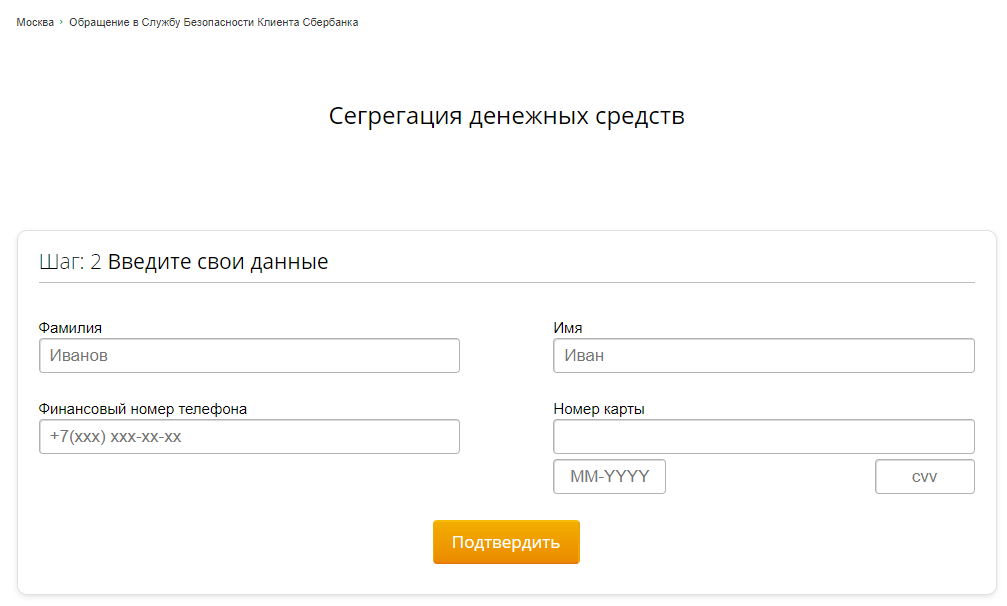
Not bad, is it? But we are, as it were, on the page of the bank’s security service ... We enter dummy data (the site does not check card numbers for validity) and a real-life telephone number. The entered data fly away to sbersecure.ru/php/input_user_data.php , and we find ourselves on the next page.
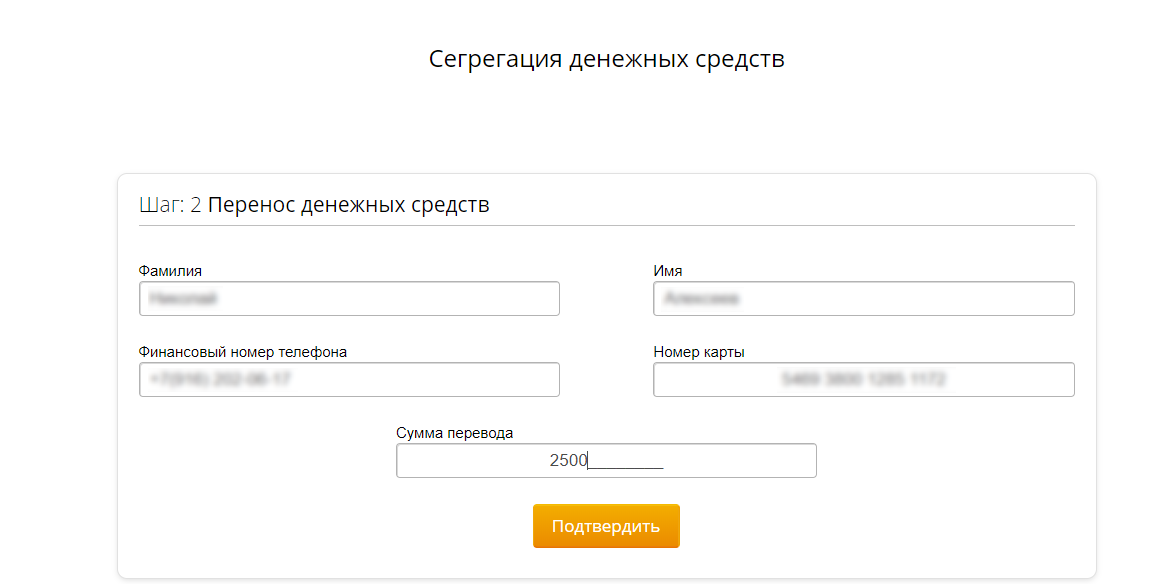
The logic is not completely clear, perhaps, since we are talking about the segregation of funds, here the victim would have to enter the data of his second bank card. Again, fill the field with plausible garbage, indicating the existing phone number. The entered data is transferred to sbersecure.ru/php/input_frand.php . Honestly, I don’t know what frand can mean, but I suspect that this is a distorted friend.
Voila!
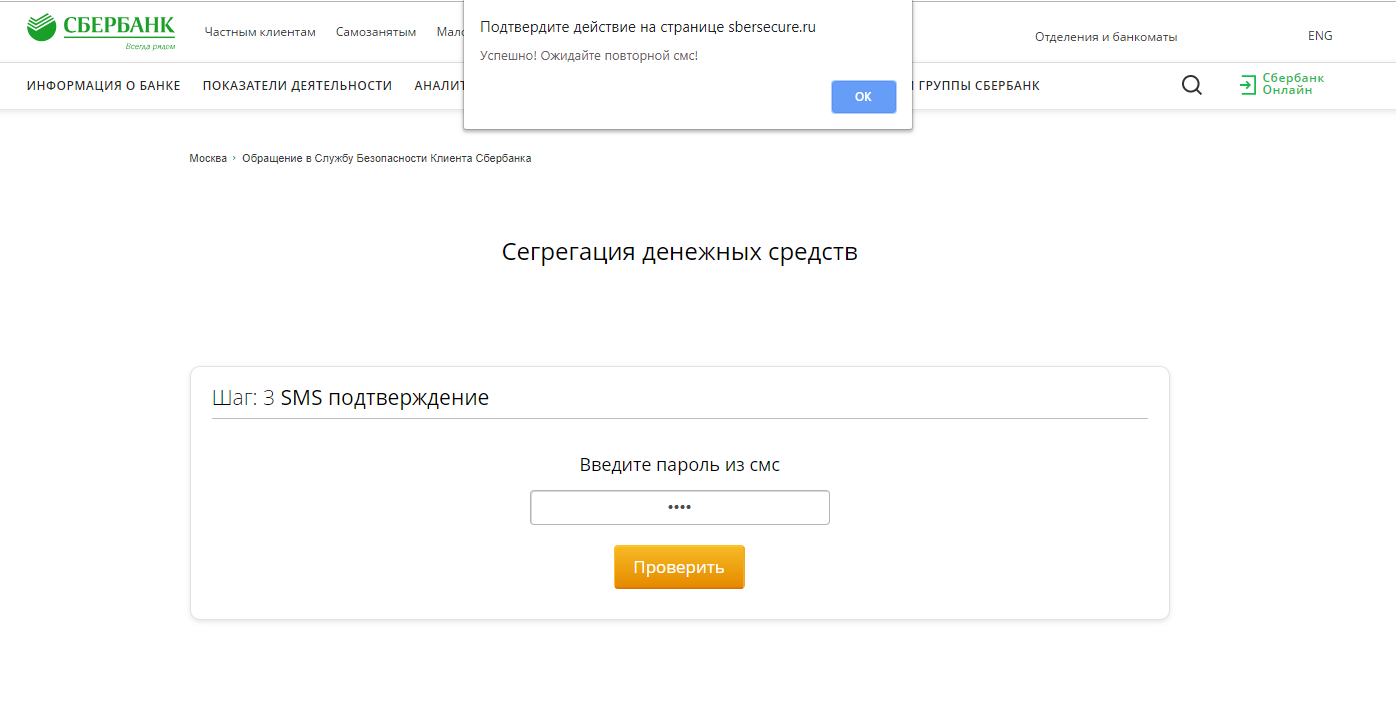
Quite predictably, we are on the code entry page of the SMS message. At the same time, a text message from Yandex arrives on the phone. It seems that someone is trying to make a transfer using the Yandex.Money service. Enter the code, the data on the phone number and the entered characters go to sbersecure.ru/php/input_sms_2.php , and returns to the previous page.
Following this, another SMS comes to the specified number. To continue this cycle can be almost infinite.
Of course, if we talk about the details of the money transfer scheme, this is largely a guess. For the purity of the experiment, you should enter the data of a valid, albeit virtual, bank card, try to track the movement of finances and so on, but even now it is clear that with the help of this site the attackers get at least:
With such information at your disposal, you can easily steal money from bank accounts in a variety of ways.
Naturally, my colleagues and I could not calmly walk past such a resource, so on the evening of April 18 we sent information about it to Sberbank, using the feedback form on the official website. After 2 days, on April 20, we received a letter stating that our appeal was registered.
Later we repeated the request using the special form for sending messages about fraudulent resources, which was very difficult to find without Google's help: www.sberbank.ru/ru/person/dist_services/warning/form
Hopefully, the bank will quickly respond to the message, and the phishing site will disappear from the network as fast as it appeared.
Events around the site developed rapidly. The domain name was registered on the evening of April 16, and the next day a phishing site was on it. Initially, the servers of the Russian Hostlife host were listed as the DNS, however, after only 9 hours, the addresses of CloudFlare, a company that does not need to be presented, appeared in the NS records. On April 17, at 15:00 Moscow time, the resource acquired an encryption certificate issued by the same CloudFlare.

')
Let's get acquainted with the phishing site closer.
To create a resource, a rather popular way to partially copy the original site was used. In this case, the attackers took as a basis the “Ombudsman’s Office” page of the bank, changing the words “Ombudsman’s Office” to “Client’s Security Service”.
Here is the original Ombudsman Service page.

But a phishing site.

At the same time, the changes affected only the central part of the site; the header, context menus and footer completely repeat the original design. All links, including the link to the authorization page in the Sberbank Online service, lead to the real Sberbank website.
General view of a phishing site.

A key element of a phishing resource is a button that says "Urgently get help." Clicking on it redirects us to the sbersecure.ru/help.html page. Parallel runs a whole bunch of java-scripts, most of which do not work. Curiously, one of the scripts accesses the resource ibbe.group-ib.ru . Apparently, this is the Secure Bank service script from Group-IB, inherited from a phishing resource from this site of the bank.

The second page of the resource is called “Segregation of Cash”. April 18, when this site came into view, it looked like this.

Attempts to enter an arbitrary personnel number of an employee did not lead to anything, while the second part, “Resetting login and password Sberbank online,” was inactive.
Over the weekend, the page has changed. The form for entering the personnel number has disappeared, but a form has become available intended to change the login and password from the personal account of the online bank. This clarifies the possible use of phishing resources.

It would be foolish not to see what happens with the submitted data, so fill out the form with arbitrary words and click on the "Confirm" button.
Pressing the button in open form sends the following information to the sbersecure.ru/php/add_login_bank.php script: login and password from the Sberbank.Online service, information about the region of residence and IP address. Information from the fields for entering a new login and a new password is ignored for obvious reasons. After that, a redirect to the sbersecure.ru/get_info.html page occurs , where we are offered to enter the first name, last name, phone number, as well as card details, including the number, CVV and its validity period.

Not bad, is it? But we are, as it were, on the page of the bank’s security service ... We enter dummy data (the site does not check card numbers for validity) and a real-life telephone number. The entered data fly away to sbersecure.ru/php/input_user_data.php , and we find ourselves on the next page.

The logic is not completely clear, perhaps, since we are talking about the segregation of funds, here the victim would have to enter the data of his second bank card. Again, fill the field with plausible garbage, indicating the existing phone number. The entered data is transferred to sbersecure.ru/php/input_frand.php . Honestly, I don’t know what frand can mean, but I suspect that this is a distorted friend.
Voila!

Quite predictably, we are on the code entry page of the SMS message. At the same time, a text message from Yandex arrives on the phone. It seems that someone is trying to make a transfer using the Yandex.Money service. Enter the code, the data on the phone number and the entered characters go to sbersecure.ru/php/input_sms_2.php , and returns to the previous page.
Following this, another SMS comes to the specified number. To continue this cycle can be almost infinite.
Of course, if we talk about the details of the money transfer scheme, this is largely a guess. For the purity of the experiment, you should enter the data of a valid, albeit virtual, bank card, try to track the movement of finances and so on, but even now it is clear that with the help of this site the attackers get at least:
- Surname
- Name
- Full bank card details
- Phone number
- Login and password to enter the service "Sberbank.Online"
With such information at your disposal, you can easily steal money from bank accounts in a variety of ways.
Naturally, my colleagues and I could not calmly walk past such a resource, so on the evening of April 18 we sent information about it to Sberbank, using the feedback form on the official website. After 2 days, on April 20, we received a letter stating that our appeal was registered.
Later we repeated the request using the special form for sending messages about fraudulent resources, which was very difficult to find without Google's help: www.sberbank.ru/ru/person/dist_services/warning/form
Hopefully, the bank will quickly respond to the message, and the phishing site will disappear from the network as fast as it appeared.
Source: https://habr.com/ru/post/449036/
All Articles