Development in the cloud, information security and personal data: digest for reading at the weekend from 1cloud
These are materials from our corporate and Habrablog about working with personal data, IT systems protection and cloud development. In this digest you will find posts with parsing terms, basic approaches and technologies, as well as materials on IT standards.

/ Unsplash / Zan Ilic
 / Unsplash / Alvaro Reyes
/ Unsplash / Alvaro Reyes
')
 / Unsplash / Luis Villasmil
/ Unsplash / Luis Villasmil
Our other selections:

/ Unsplash / Zan Ilic
Work with personal data, standards and basics of information security
- What is the essence of the law on personal data (PD) . Introductory material on legislative acts regulating the work with PD. We tell whom it concerns and does not concern Federal Law No. 152, and what should be understood as consent to the processing of PD. And we give a scheme of actions to comply with the requirements of the Federal Law, and also address the issues of security and remedies.
- Personal data: protection . We analyze the requirements for the protection of PD, types of threats and levels of security. In addition, we provide a list of legislative acts on the topic and a basic list of measures to ensure the safety of PD.
- PD and public cloud . The third part of our cycle of materials about personal data. This time we are talking about the public cloud: we are considering issues of protecting the OS, communication channels, virtual environment, and also talk about the distribution of responsibility for data security between the owner of the virtual server and the IaaS provider.
- Do we need cookies banners in the era of GDPR: discuss the situation and the requirements of the law . Cookie-banners do not like neither users nor the owners of Internet resources. We find out what regulation really requires, and talk about the workaround to the problem using the DNT framework and browser extensions.
- European regulators opposed cookie banners . Overview of the situation with notifying users about the installation of cookies. It will be about why government structures in several European countries claim that the use of banners contradicts the GDPR and violates the rights of citizens. We consider the issue from the perspective of relevant ministries, site owners, advertising companies and users. This habrapos has already scored more than 400 comments and is preparing to pass a mark of 25 thousand views.
 / Unsplash / Alvaro Reyes
/ Unsplash / Alvaro Reyes')
- What you need to know about digital signatures . Acquaintance with the topic for those who would like to understand what constitutes an EDS, and know how their identity system works. We also briefly review certification issues and figure out on which media keys can be stored and whether or not to buy specialized software.
- IETF-approved ACME is a standard for working with SSL certificates . We are talking about how the new standard will help automate the acquisition and configuration of SSL certificates. And as a result - to increase the reliability and security of domain name verification. We present the mechanism of work of ACME, opinions of representatives of the industry and features of similar solutions - the SCEP and EST protocols.
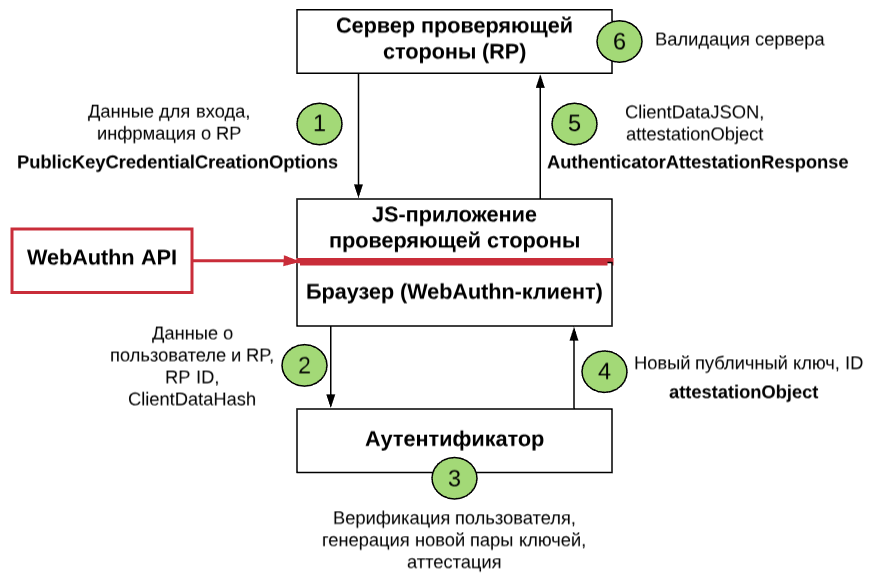
- The WebAuthn standard is officially completed . This is a new standard for passwordless authentication. We talk about how it works WebAuthn ( scheme below ), as well as the advantages, disadvantages and obstacles to the implementation of the standard.

- How backup works in the cloud . Basic information for those who would like to figure out how many copies should be made, where to place them, how often to update and how to set up a simple backup system in a virtual environment.
- How to protect a virtual server . An introductory post about basic ways to protect against the most common attack options. We give the main recommendations: from two-factor authentication to monitoring with examples of implementation in the cloud 1cloud.
Cloud Development
- DevOps in the cloud service: our experience . We describe how lined up the development of a cloud platform 1cloud. First, how we started on the basis of the traditional cycle “development - testing - debugging”. Further - about DevOps-practices which we apply now. The material covers the topics of making changes, building, testing, debugging, deploying software solutions and using DevOps tools.
- How does the process of Continuous Integration . Habrapost about CI and specialized tools. We tell what we understand as continuous integration, we introduce the history of the approach and its principles. Separately, we are talking about things that can prevent the introduction of CI in the company, and give a number of popular frameworks.
- The training stand for admins: how the cloud will help . In this article, we discuss what skills system administrators can “pump over” in the cloud environment: from OS and network configuration to test layouts of real projects and application migration.
- Why does a programmer need a workplace in the cloud ? Back in 2016, TechCrunch said on the pages that local software development is gradually "dying." She was replaced by remote work, and the workplaces of programmers went to the cloud. In our general overview of this topic, we discuss how to organize a workspace for a group of developers and deploy new software in a virtual environment.
- How developers use containers . We tell what happens with the applications inside the containers, and how to manage it all. We will also talk about application programming and working with high-load systems.
 / Unsplash / Luis Villasmil
/ Unsplash / Luis Villasmil- Participation in open source projects can be beneficial for companies . We share thoughts on how to benefit from an open approach. We discuss research and opinions.
Our other selections:
Source: https://habr.com/ru/post/448760/
All Articles