Free Wireguard VPN service on AWS
For what?
With the growth of Internet censorship by authoritarian regimes, an increasing number of useful Internet resources and sites are being blocked. Including with technical information.
Thus, it becomes impossible to fully use the Internet and violates the fundamental right to freedom of speech enshrined in the Universal Declaration of Human Rights .
Article 19
Everyone has the right to freedom of opinion and expression; this right includes the freedom to freely adhere to one’s convictions and the freedom to seek, receive and impart information and ideas by any means and regardless of frontiers
In this guide, we will deploy our own free * VPN service based on Wireguard technology, in Amazon Web Services (AWS) cloud infrastructure, using a free account (for 12 months), on an instance (virtual machine) running Ubuntu Server 18.04 in 6 steps Lts .
I tried to make this walkthrough as friendly as possible to people far from IT. The only thing required is assiduity in repeating the steps described below.
Note
- AWS provides a free usage level for a period of 12 months, with a limit of 15 gigabytes of traffic per month.
- The most current version of this guide is located at https://wireguard.isystem.io
Stages
- AWS Free Account Registration
- Create an AWS instance
- Connect to an AWS instance
- Configuring Wireguard
- Configuring VPN Clients
- Verify VPN installation
useful links
1. Register an AWS Account
To register a free AWS account, you need a real phone number and a paying Visa or Mastercard credit card. I recommend using virtual cards that Yandex.Money or Qiwi wallet provides for free. To check the validity of the card, at registration 1 $ is deducted which is refunded.
1.1. Opening the AWS Management Console
You need to open a browser and go to: https://aws.amazon.com/ru/
Click on "Register"

1.2. Filling in personal data
Fill in the data and click on the "Continue" button
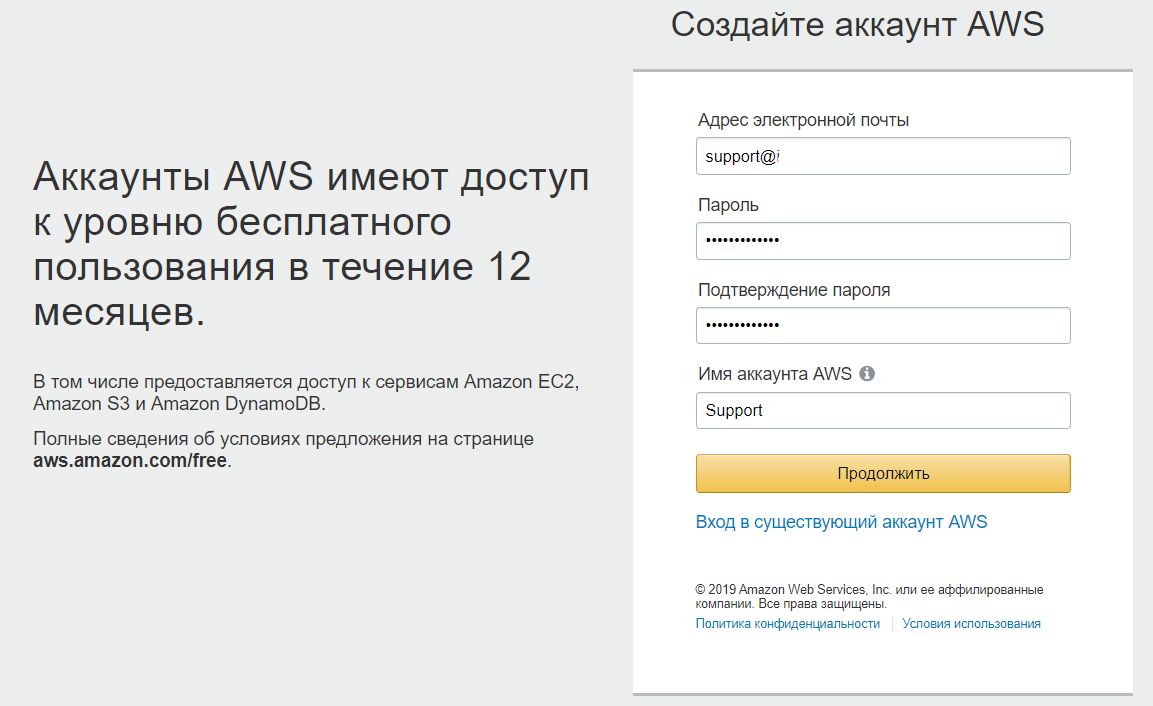
1.3. Filling contact information
Fill out contact information.
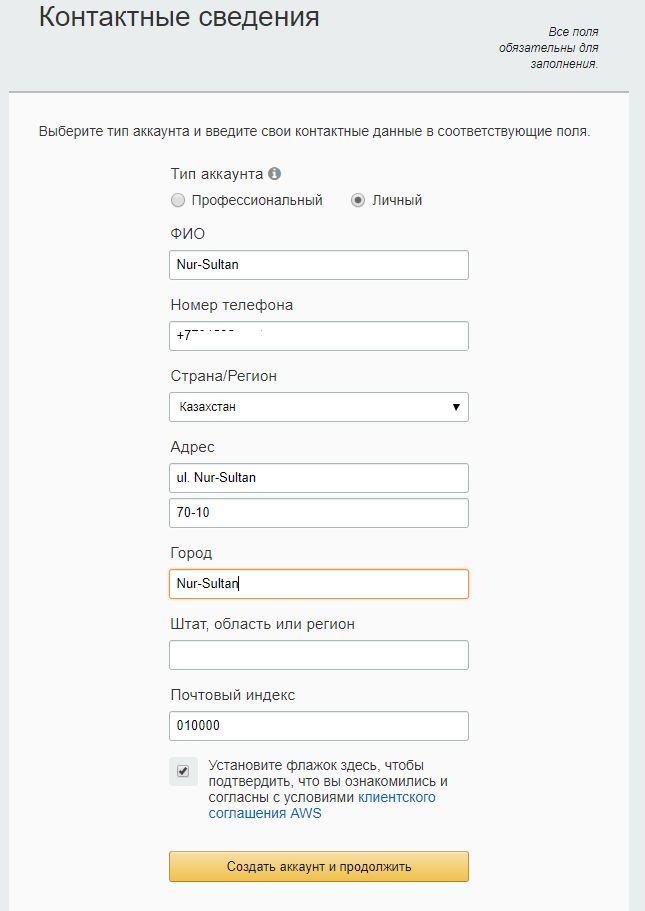
1.4. Specify billing information.
Card number, expiration date and cardholder name.

1.5. Account Verification
At this stage, the phone number is confirmed and $ 1 is directly debited from the payment card. A 4-digit code is displayed on the computer screen, and a call from Amazon is received on the specified phone. During a call, you must dial the code specified on the screen.

1.6. Select a tariff plan.
Choosing - Basic plan (free)

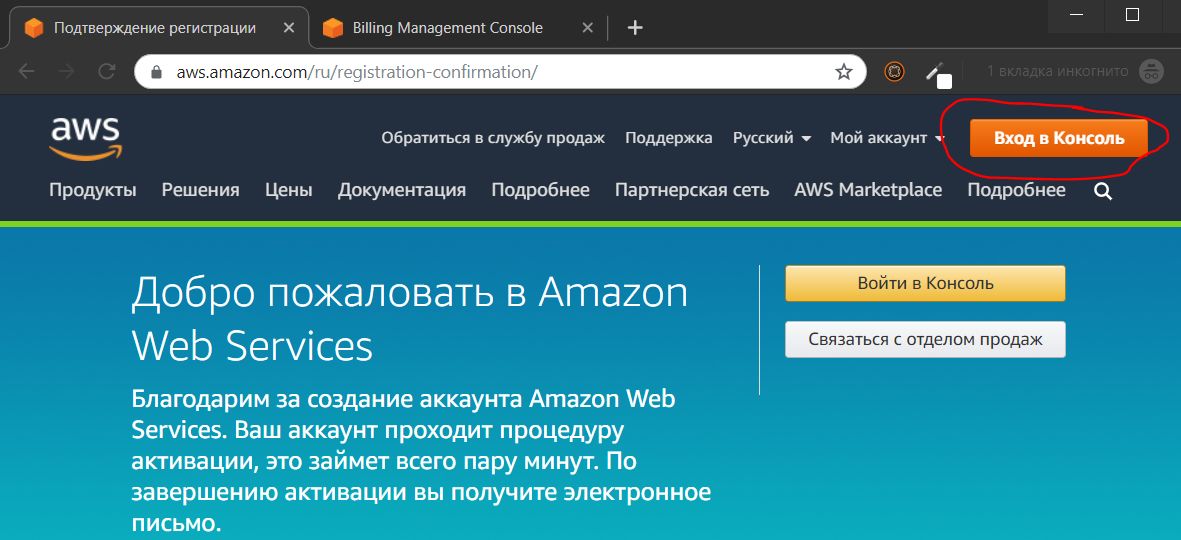
1.7. Login to the management console
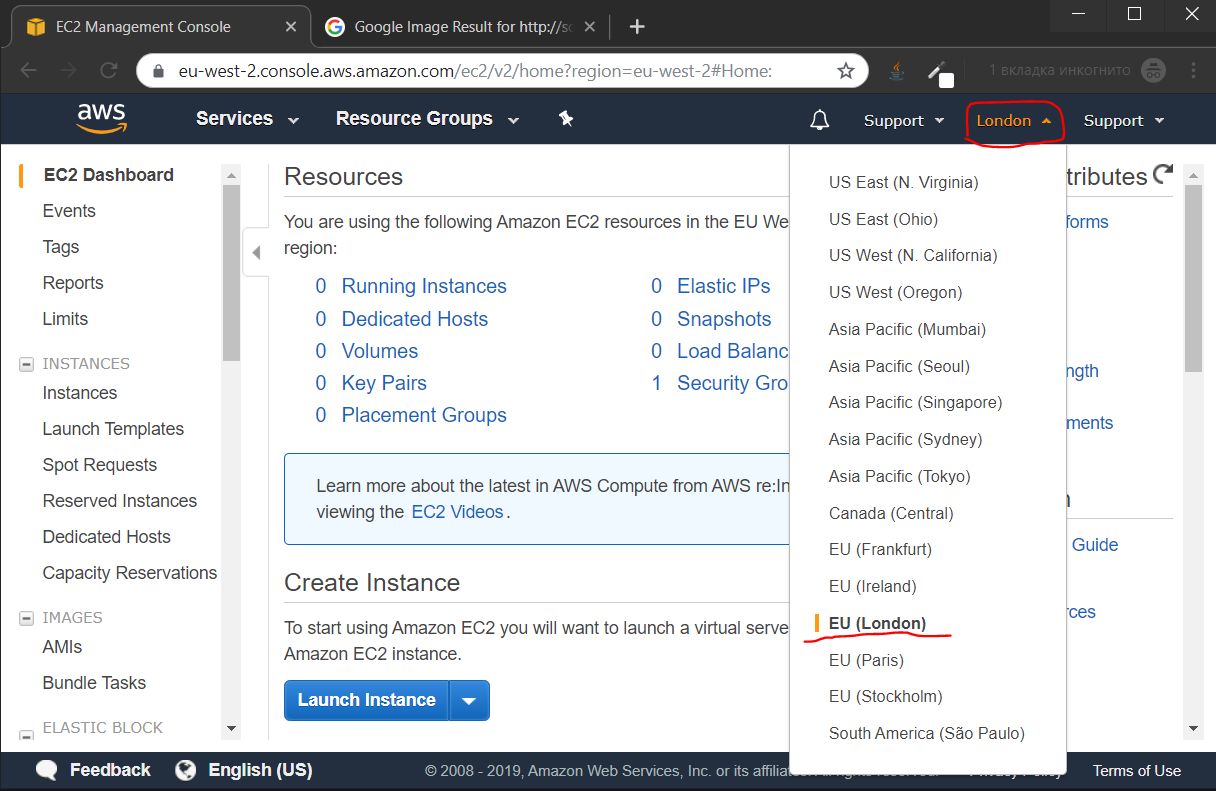
1.8. Choosing the location of the data center
1.8.1. Speed testing
Before choosing a datacenter, it is recommended to test through https://speedtest.net the speed of access to the nearest datacenters, in my location such results:
- Singapore
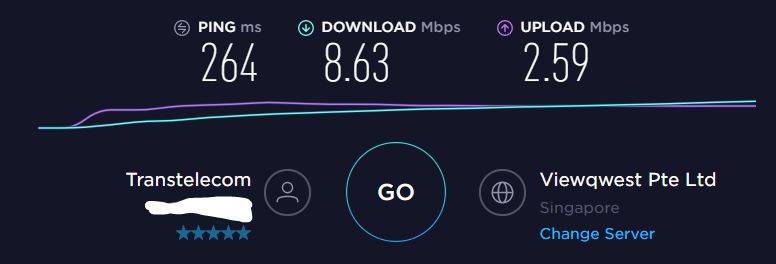
- Paris

- Frankfurt

- Stockholm

- London
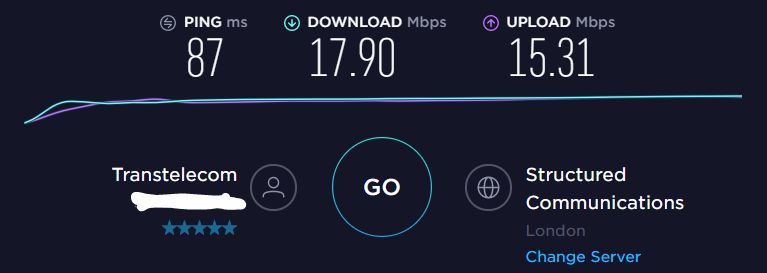
The best results for speed shows a data center in London. Therefore, I chose it for further configuration.
2. Creating an AWS instance
2.1 Creating a virtual machine (instance)
2.1.0. Launch step-by-step instance creation wizard
2.1.0.1. Go to the instance launch page
2.1.0.2. Launch step-by-step instance creation wizard

2.1.0.3. Select the type of operating system instance

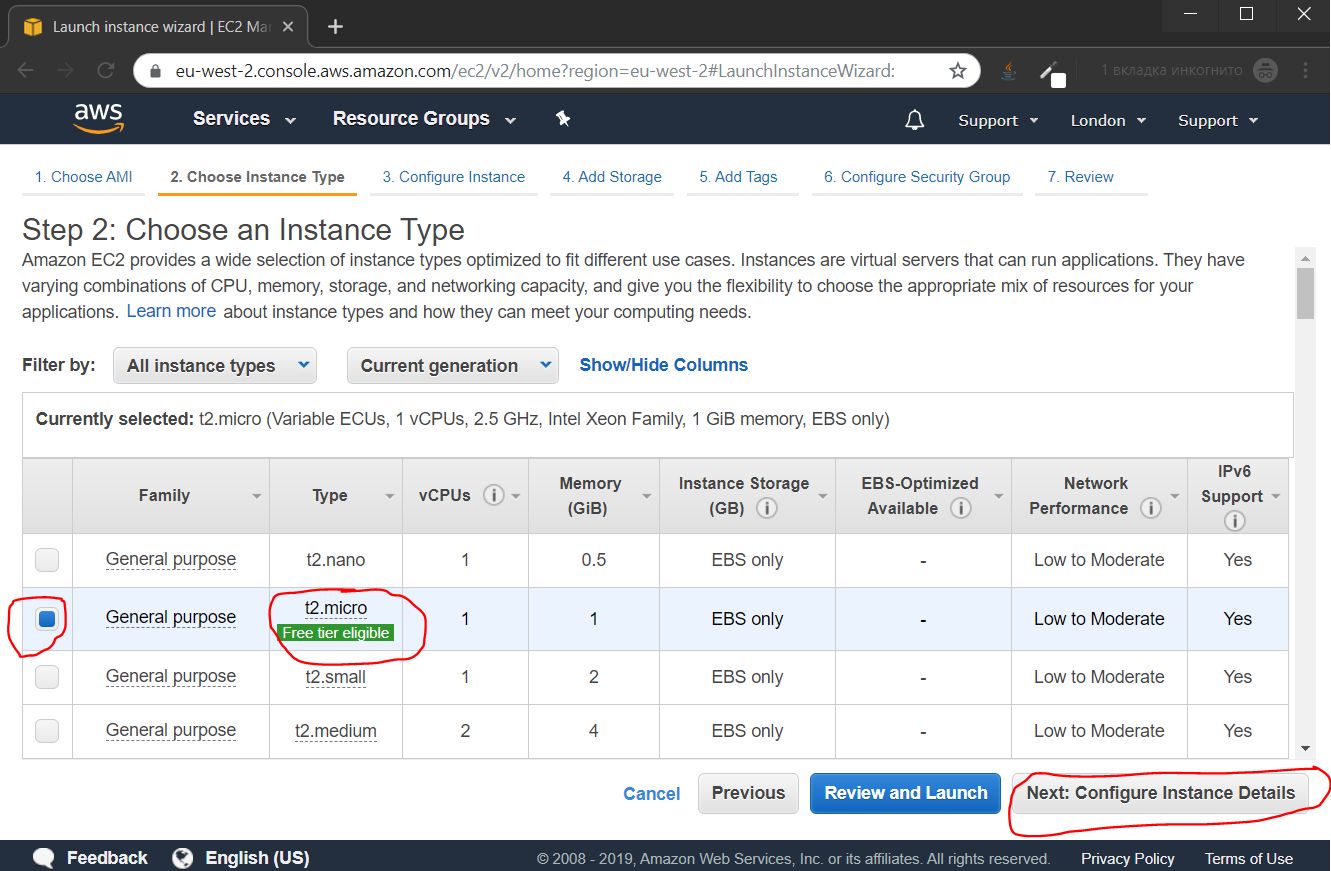
2.1.1. Select an instance type
The t2.micro instance is selected by default, and we need it, just click the Next: Configure Instance Detalis button
2.1.2. Setting instance parameters
In the future, we will connect a permanent public IP to our instance, so at this stage we disable the automatic assignment of a public IP, and click the Next button : Add Storage

2.1.3. Connection storage
Specify the size of the "hard disk". For our purposes, 16 gigabytes is enough, and click Next: Add Tags
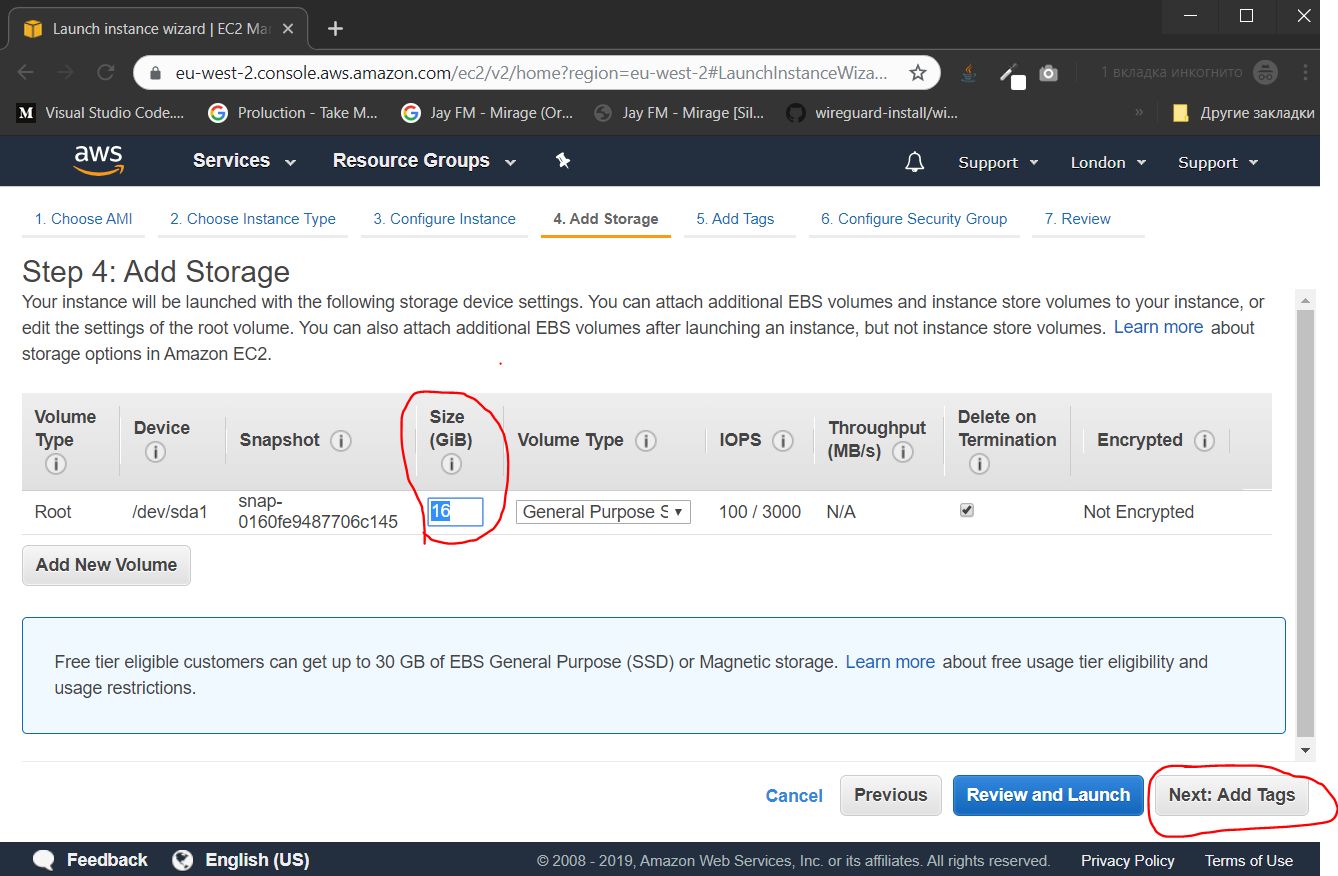
2.1.4. Tag customization
If we created several instances, they could be grouped by tags, to facilitate administration. In this case, this functionality is superfluous, immediately press the Next button : Configure Security Gorup

2.1.5. Opening ports
At this stage, we configure the firewall by opening the necessary ports. The open port set is called the Security Group. We have to create a new security group, give it a name, a description, add a UDP port (Custom UDP Rule), in the Rort Range field you need to assign a port number from the range of dynamic ports 49152-65535. In this case, I chose port number 54321.
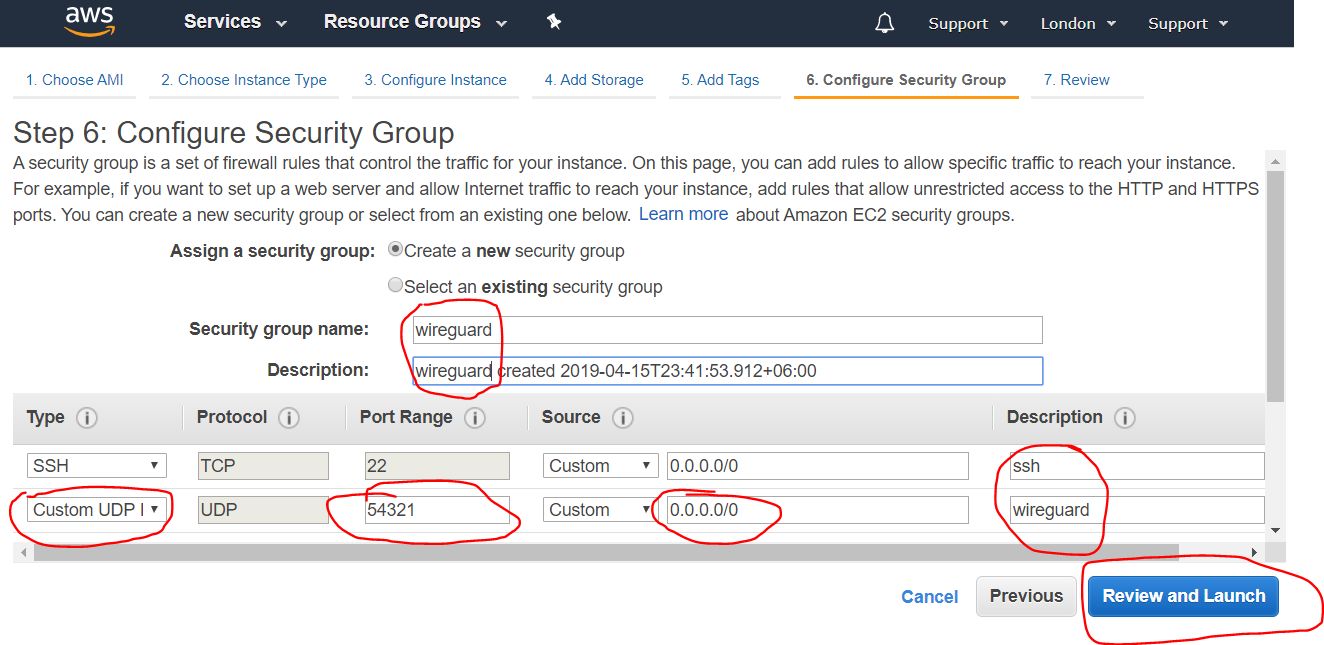
After filling in the required data, click on the Review and Launch button
2.1.6. Overview of all settings
On this page, we review all the settings of our instance, check whether all the settings are in order, and click the Launch button.
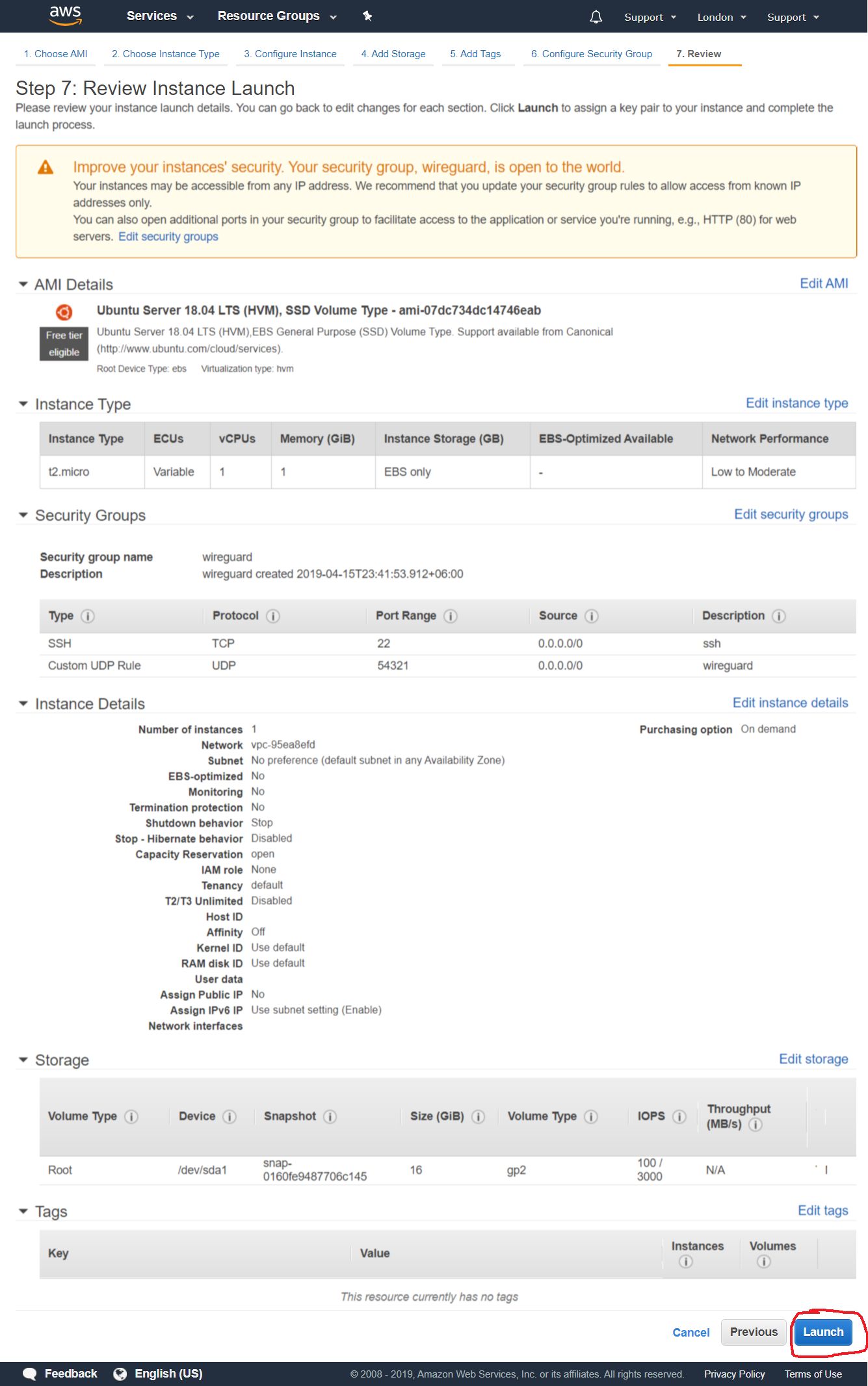
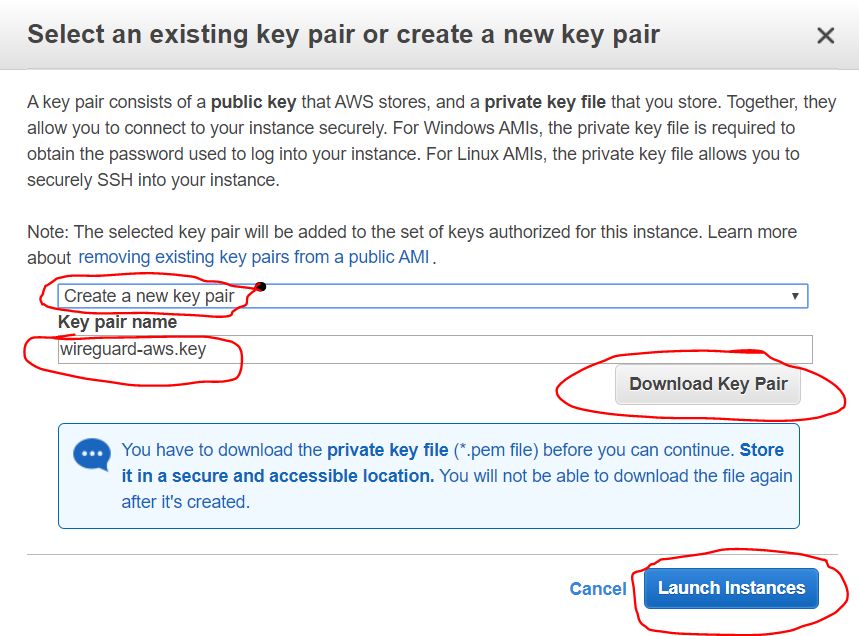
2.1.7. Creating access keys
Next comes a dialog box that prompts you to either create or add an existing SSH key, with which we will later connect remotely to our instance. We select the "Create a new key pair" option to create a new key. Set its name, and click the Download Key Pair button to download the generated keys. Save them to a safe place on the local computer disk. Once downloaded - click the Launch Instances button
2.1.7.1. Saving access keys
Shown here is the step of saving the generated keys from the previous step. After we clicked the Download Key Pair button, the key is saved as a certificate file with the extension * .pem. In this case, I named it wireguard-awskey.pem

2.1.8. Instance Creation Results Overview
Next, we see a message about the successful launch of the instance we just created. We can go to the list of our instances by clicking on the View instances button.

2.2. Creating an external IP address
2.2.1. Starting external IP creation
Next we need to create a permanent external IP address, through which we will connect to our VPN server. To do this, select the item Elastic IPs from the NETWORK & SECTURITY category in the navigation pane on the left side of the screen and click the Allocate new address button

2.2.2. Setting up an external IP
In the next step, we need to enable the Amazon pool option (enabled by default), and click on the Allocate button
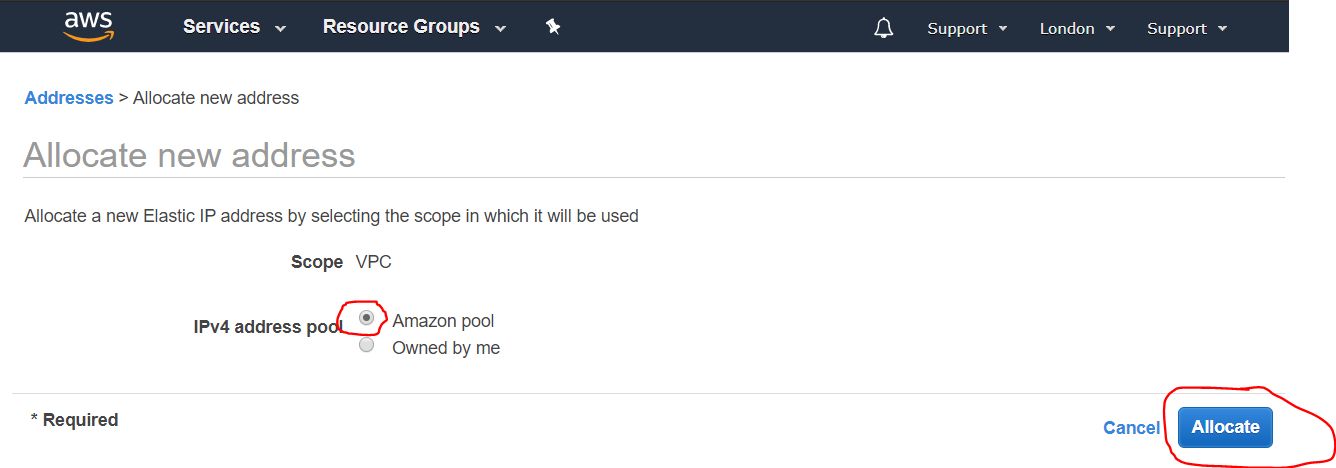
2.2.3. Overview of the results of creating an external IP address
The next screen will display the external IP address we received. It is recommended to remember it, and even better to write it down. it will be useful to us more than once in the process of further configuration and use of the VPN server. In this guide, as an example, I use the IP address 4.3.2.1 . How to write the address, click on the Close button
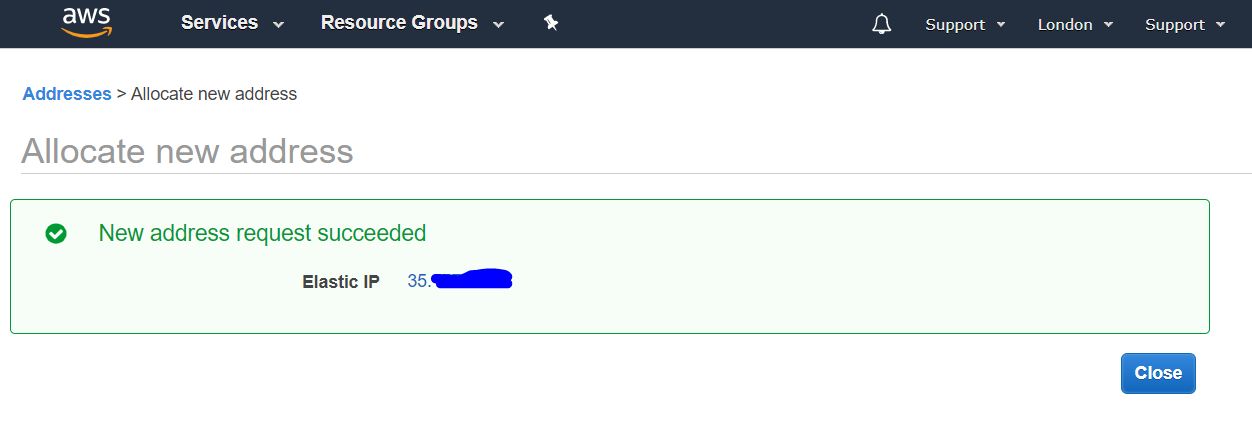
2.2.4. List of external IP addresses
Next we have a list of our permanent public IP addresses (elastics IP).

2.2.5. Assigning an external IP instance
In this list, we select the IP address we received, and click the right mouse button to bring up a drop-down menu. In it, select the Associate address item to assign it to the instance we created earlier.

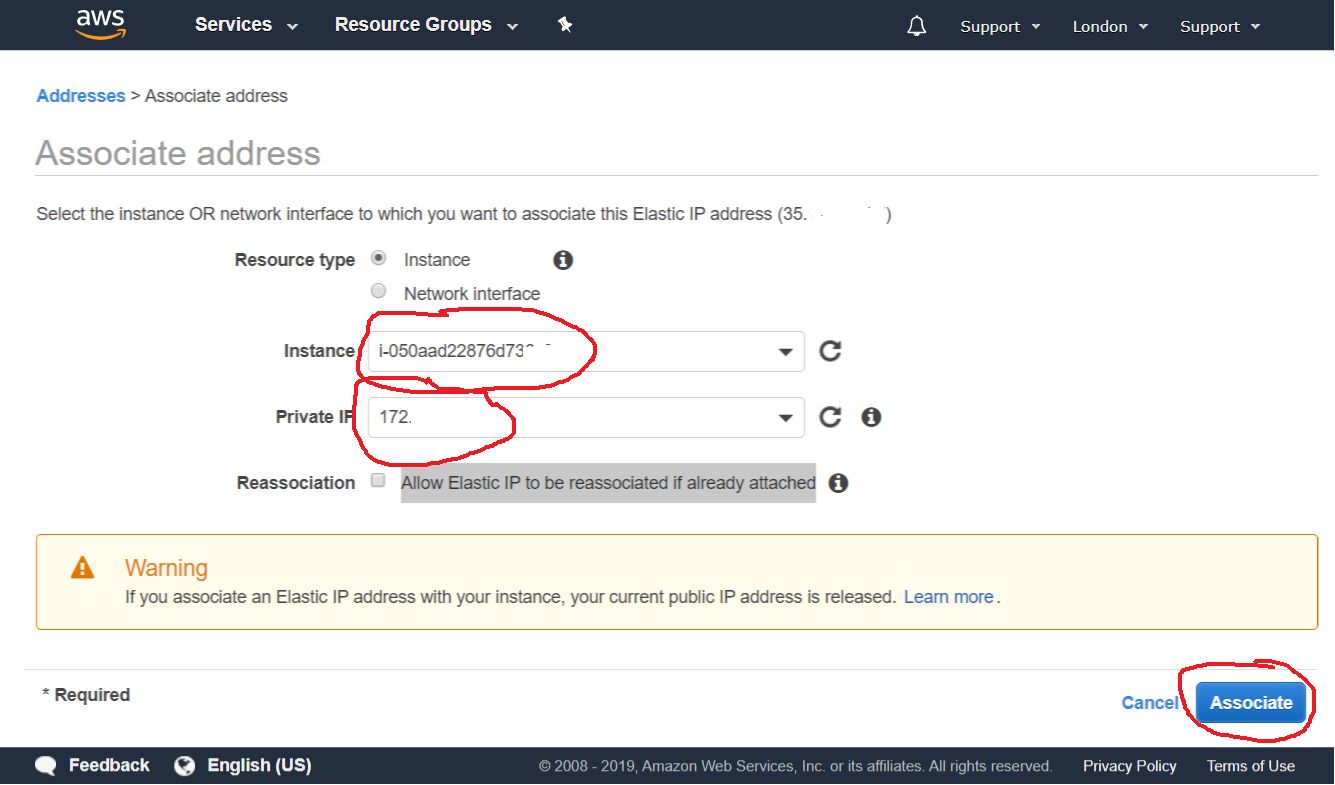
2.2.6. Configure external IP assignment
In the next step, select our instance from the drop-down list, and click the Associate button.
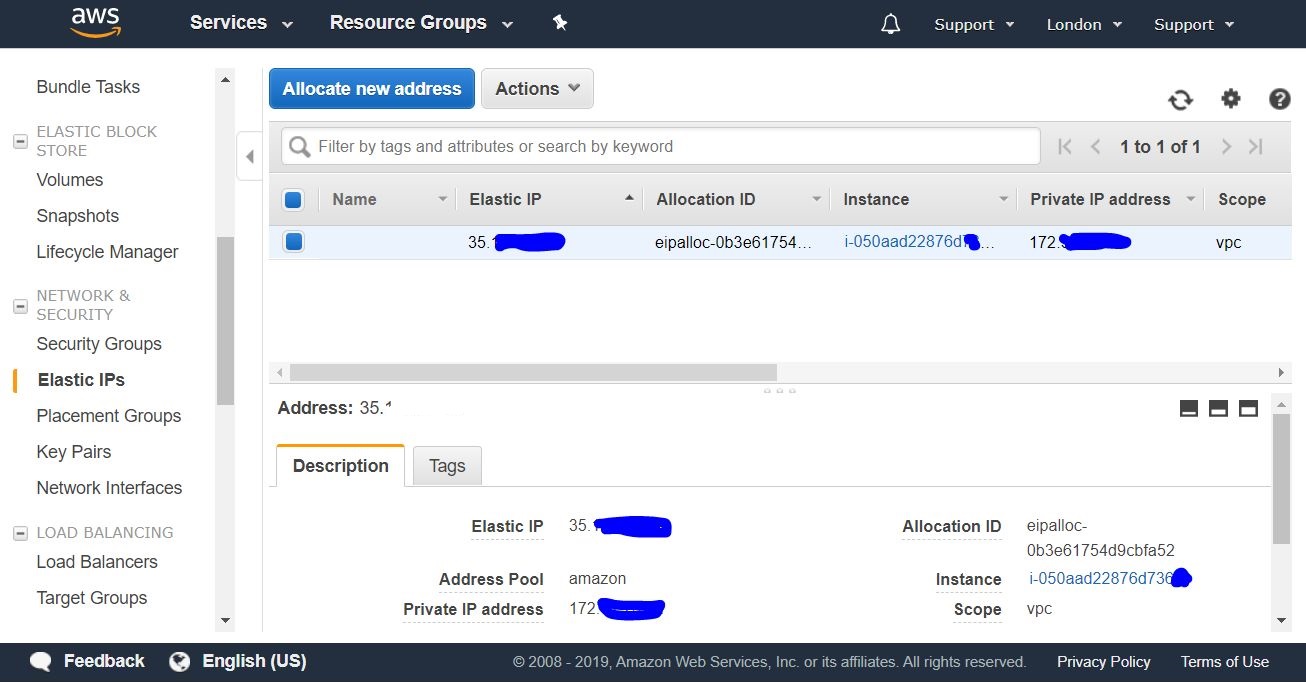
2.2.7. Overview of external IP assignment results
After that, we can see our instance and its private IP address is tied to our permanent public IP address.
Now we can connect to our newly created instance from outside, from our computer via SSH.
3. Connect to an AWS instance
SSH is a secure protocol for remotely managing computer devices.
3.1. Connecting via SSH from a computer to Windows
To connect to a Windows computer, first you need to download and install Putty .
3.1.1. Import Private Key for Putty
3.1.1.1. After installing Putty, you must run the PuTTYgen utility bundled with it to import the certificate key in the PEM format into a format suitable for use in the Putty program. To do this, in the top menu, select the item Conversions-> Import Key

3.1.1.2. AWS key selection in PEM format
Next, select the key that we previously saved in step 2.1.7.1, in our case, its name is wireguard-awskey.pem

3.1.1.3. Setting key import parameters
At this step, we need to specify a comment for this key (description) and set a password for security and its confirmation. It will be requested at each connection. Thus, we protect the key with a password from unauthorized use. The password can not be set, but it is less secure if the key falls into the wrong hands. After press the button Save private key
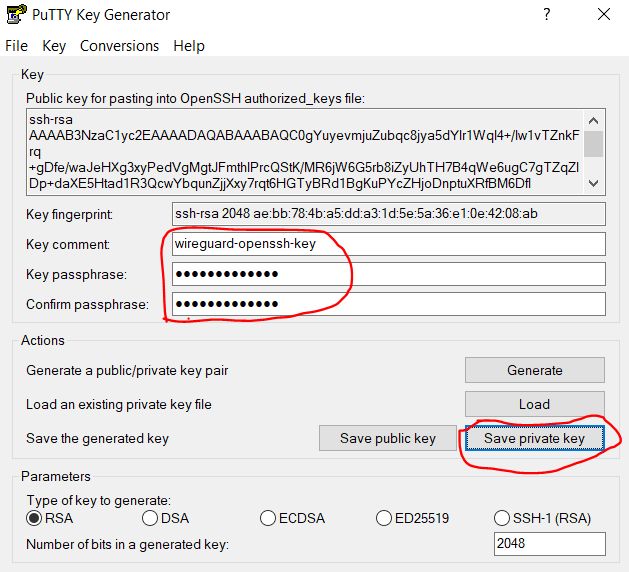
3.1.1.4. Save imported key
The save file dialog box opens, and we save our private key as a file with the .ppk extension, suitable for use in the Putty program.
Specify the key name (in our case, wireguard-awskey.ppk ) and click the Save button.

3.1.2. Creating and configuring a connection in Putty
3.1.2.1. Making a connection
Open the Putty program, select the Session category (it is open by default) and enter the public IP address of our server in the Host Name field, which we received in step 2.2.3. In the Saved Session field, enter an arbitrary name for our connection (in my case, wireguard-aws-london ), and then click the Save button to save the changes we have made.

3.1.2.2. Setting user autologin
Next in the Connection category, select the Data subcategory and in the Auto-login username field , enter the username ubuntu - this is the standard instance user on AWS with Ubuntu.

3.1.2.3. Selecting a private key for an SSH connection
Then go to the Connection / SSH / Auth subcategory and click on the Browse button next to the Private key file for authentication field to select the key certificate file.
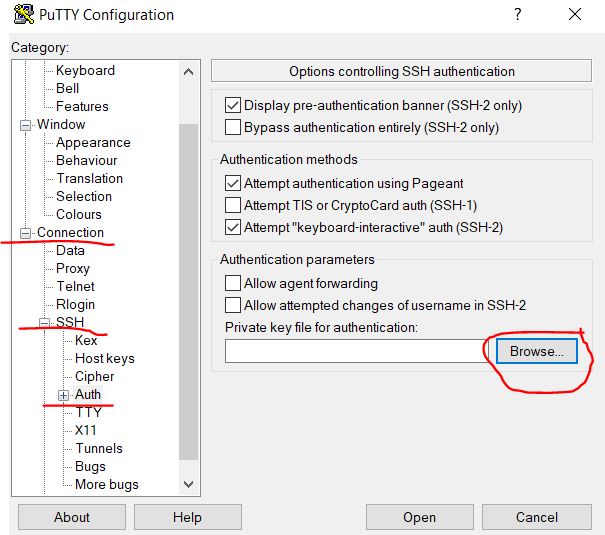
3.1.2.4. Opening an imported key
Specify the key that we imported earlier in step 3.1.1.4, in our case, this file is wireguard-awskey.ppk , and click the Open button.

3.1.2.5. Saving settings and launching connection
Returning to the Session category page, press the Save button again, to save the changes we made earlier in the previous steps (3.1.2.2 - 3.1.2.4). And then we click the Open button to open the remote SSH connection we’ve created and configured.

3.1.2.7. Configuring trust between hosts
In the next step, when you first try to connect, we are given a warning, we are not configured to trust between two computers, and ask whether to trust the remote computer. We click Yes , thereby adding it to the list of trusted hosts.

3.1.2.8. Enter the password to access the key
After this, a terminal window opens where the key password is requested, if you installed it earlier in step 3.1.1.3. When entering the password, no action is taken on the screen. If you make a mistake, you can use the backspace key.

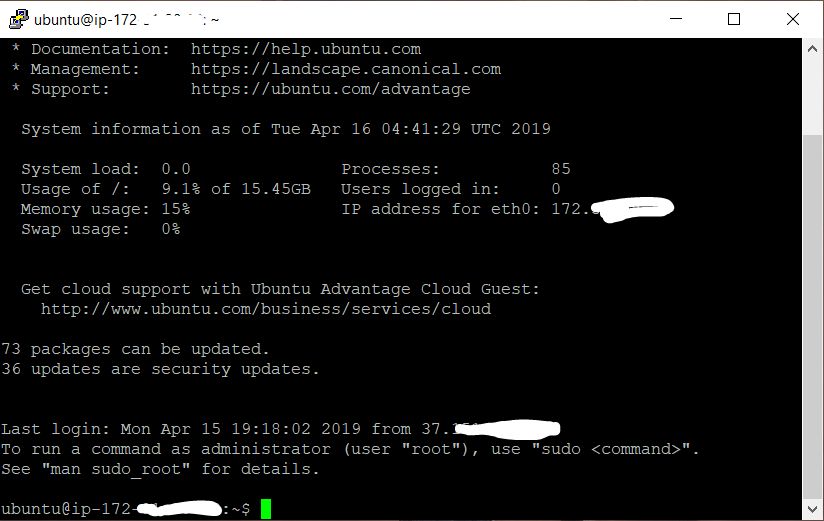
3.1.2.9. Welcome message about successful connection
After successfully entering the password, the welcome text is displayed to us in the terminal, which informs you that the remote system is ready to execute our commands.
4. Configuring the Wireguard server
The most current instructions for installing and using Wireguard using the scripts described below can be viewed in the repository: https://github.com/isystem-io/wireguard-aws
4.1. Install Wireguard
In the terminal, enter the following commands (you can copy to the clipboard, and paste in the terminal by pressing the right mouse button):
4.1.1. Repository cloning
We clone a repository with Wireguard installation scripts
git clone https://github.com/pprometey/wireguard_aws.git wireguard_aws 4.1.2. Moving to a directory with scripts
Go to the directory with the cloned repository
cd wireguard_aws 4.1.3 Starting the initialization script
Run the Wireguard installation script as root user
sudo ./initial.sh During the installation, you will be prompted for certain data required to configure Wireguard.
4.1.3.1. Input connection point
Enter the external IP address and the open port of the Wireguard server. We received the external IP address of the server in step 2.2.3, and the port was opened in step 2.1.5. We specify them together, 4.3.2.1:54321 colon, for example 4.3.2.1:54321 , and then presses the Enter key
Example output:
Enter the endpoint (external ip and port) in format [ipv4:port] (eg 4.3.2.1:54321): 4.3.2.1:54321 4.1.3.2. Enter internal IP address
Enter the IP address of the Wireguard server in a secure VPN subnet, if you do not know what it is, just press the Enter key to set the default value ( 10.50.0.1 )
Example output:
Enter the server address in the VPN subnet (CIDR format) ([ENTER] set to default: 10.50.0.1): 4.1.3.3. Specify DNS Server
Enter the IP address of the DNS server, or simply press the Enter key to set the default value 1.1.1.1 (Cloudflare public DNS)
Example output:
Enter the ip address of the server DNS (CIDR format) ([ENTER] set to default: 1.1.1.1): 4.1.3.4. Specifying WAN Interface
Next you need to enter the name of the external network interface that will listen to the internal network interface of the VPN. Just press Enter to set the default for AWS ( eth0 )
Example output:
Enter the name of the WAN network interface ([ENTER] set to default: eth0): 4.1.3.5. Specifying a customer name
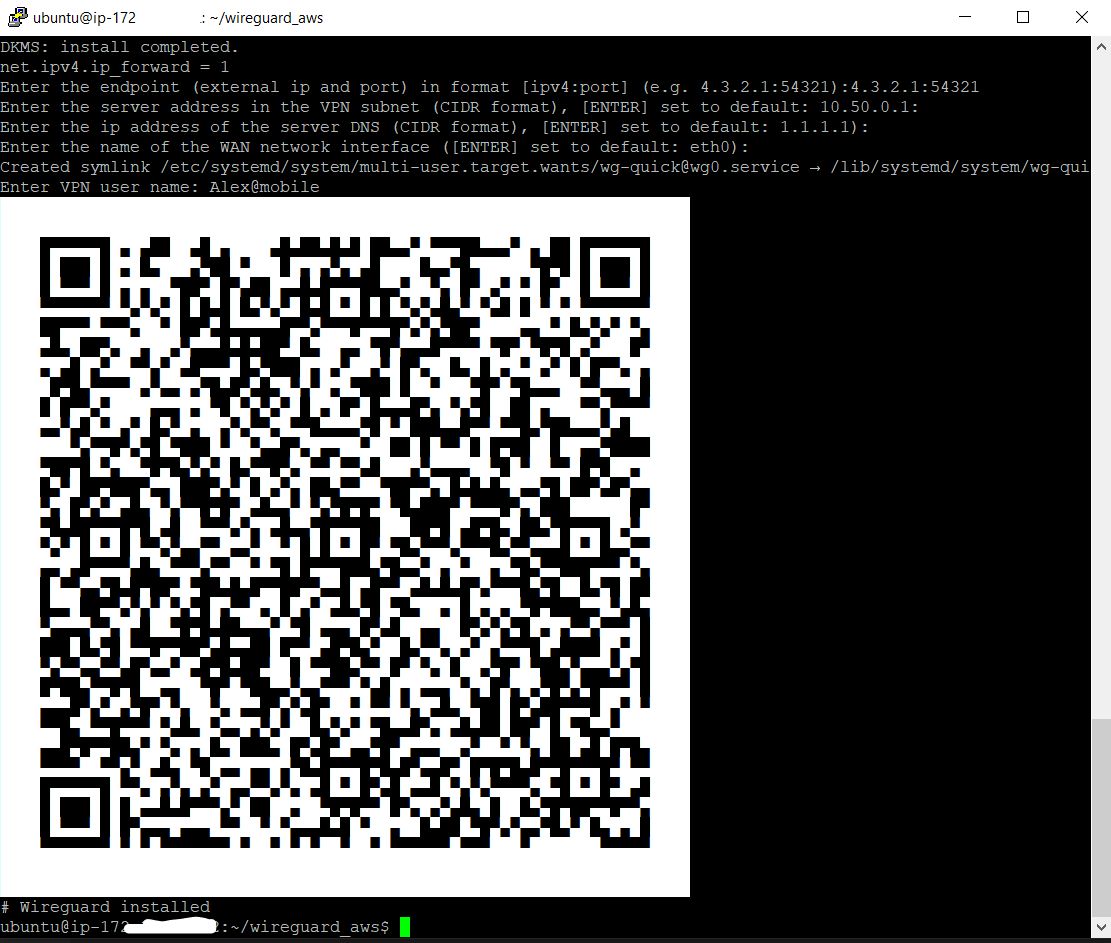
Enter the VPN username. The fact is that the Wireguard VPN server cannot start until at least one client is added. In this case, I entered the name Alex@mobile
Example output:
Enter VPN user name: Alex@mobile After that, the screen should display the QR code with the configuration of the newly added client, which must be read using the Wireguard mobile client on Android or iOS, to configure it. And also below the QR code, the text of the configuration file will be displayed in the case of manual configuration of clients. How to do this will be discussed below.
4.2. Add new VPN user
To add a new user, you need to run the script add-client.sh in the terminal
sudo ./add-client.sh The script asks for the username:
Example output:
Enter VPN user name: Also, the name can be passed to users as a script parameter (in this case, Alex@mobile ):
sudo ./add-client.sh Alex@mobile As a result of the script, in the directory with the client's name on the path /etc/wireguard/clients/{} , a file with the client configuration /etc/wireguard/clients/{} will be created, and QR code to configure mobile clients and configuration file contents.
4.2.1. User configuration file
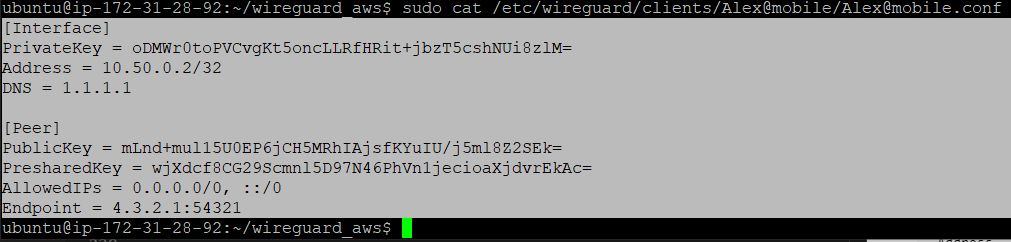
You can display the contents of the .conf file, for manual configuration of the client, using the cat
sudo cat /etc/wireguard/clients/Alex@mobile/Alex@mobile.conf result of execution:
[Interface] PrivateKey = oDMWr0toPVCvgKt5oncLLRfHRit+jbzT5cshNUi8zlM= Address = 10.50.0.2/32 DNS = 1.1.1.1 [Peer] PublicKey = mLnd+mul15U0EP6jCH5MRhIAjsfKYuIU/j5ml8Z2SEk= PresharedKey = wjXdcf8CG29Scmnl5D97N46PhVn1jecioaXjdvrEkAc= AllowedIPs = 0.0.0.0/0, ::/0 Endpoint = 4.3.2.1:54321 Description of client configuration file:
[Interface] PrivateKey = Address = IP DNS = [Peer] PublicKey = PresharedKey = AllowedIPs = ( - 0.0.0.0/0, ::/0) Endpoint = IP 4.2.2. QR client configuration code
The configuration code for a previously created client can be qrencode -t ansiutf8 on the terminal’s QR screen using the qrencode -t ansiutf8 (in this example, the client named Alex @ mobile is used):
sudo cat /etc/wireguard/clients/Alex@mobile/Alex@mobile.conf | qrencode -t ansiutf8 5. Configuring VPN Clients
5.1. Setting up a mobile client Android
The official Wireguard client for Android can be installed from the official GooglePlay store
After that, you need to import the configuration by reading the QR code with the client configuration (see clause 4.2.2) and give it a name:

After successfully importing the configuration, you can enable the VPN tunnel. On the successful connection will say the little key in the system tray Android

5.2. Windows Client Setup
Initially, you need to download and install the TunSafe program for Windows - this is the Wireguard client for Windows.
5.2.1. Creating a configuration file for import
Right-click to create a text file on the desktop.

5.2.2. Copying the contents of the configuration file from the server
Then go back to the Putty terminal and display the contents of the configuration file of the desired user, as described in step 4.2.1.
Next, select the right-click configuration text in the terminal Putty, after the selection is completed, it is automatically copied to the clipboard.
5.2.3. Copying configuration to local configuration file
This field is returned to the text file we created earlier on the desktop, and paste the configuration text from the clipboard into it.
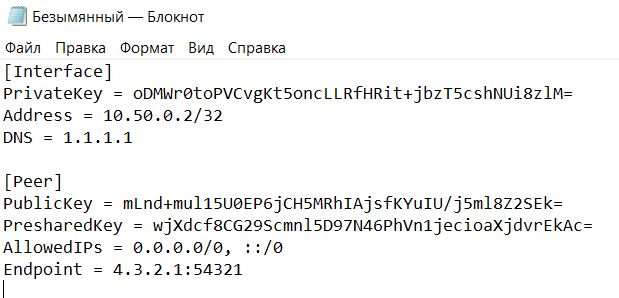
5.2.4. Saving the local configuration file
Save the file with the .conf extension (in this case with the name london.conf )
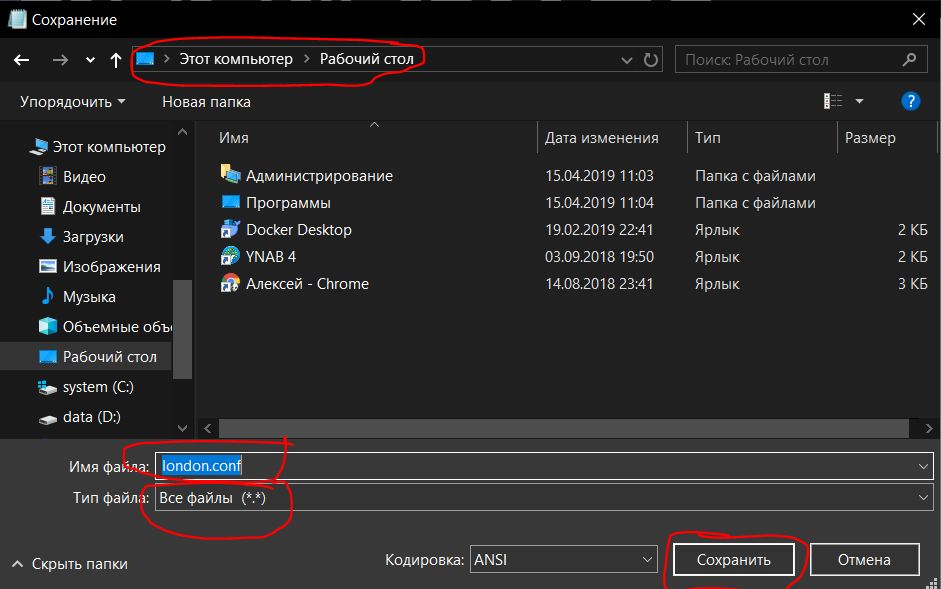
5.2.5. Import local configuration file
Next, you need to import the configuration file into the TunSafe program.

5.2.6. Establishing a VPN connection
Select this configuration file and connect by clicking the Connect button.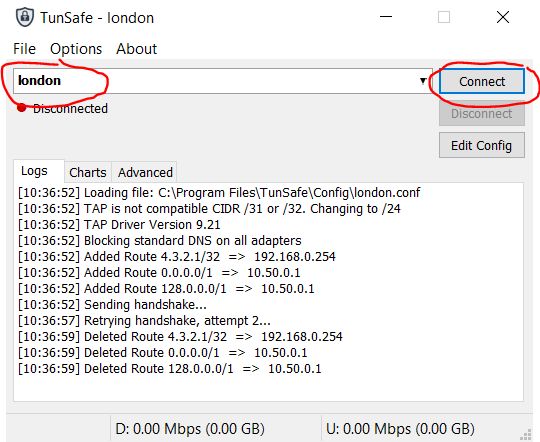
6. Verify successful connection
To check the success of the connection through the VPN tunnel, you need to open a browser and go to the site https://2ip.ua/ru/
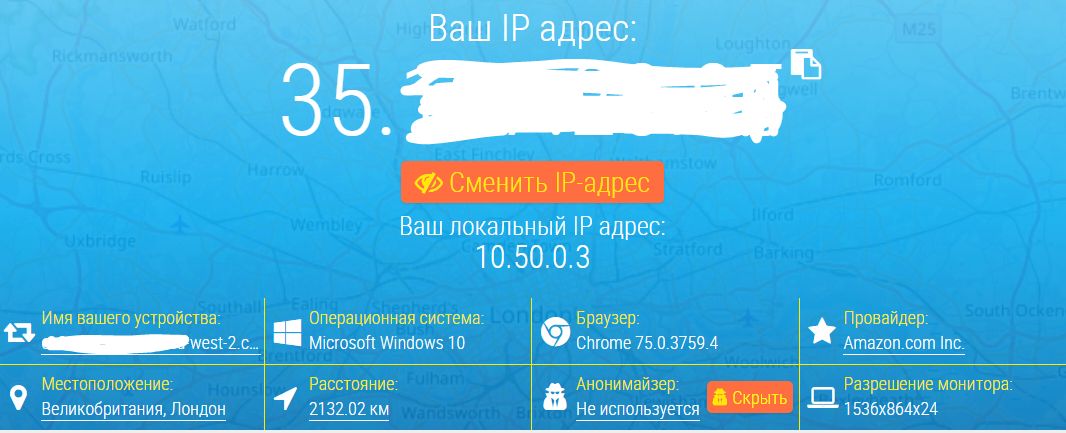
The displayed IP address must match the one we received in step 2.2.3.
If so, then the VPN tunnel is working successfully.
From a terminal in Linux, you can check your IP address by entering the command:
curl http://zx2c4.com/ip Or you can just go to the pornohab if you are in Kazakhstan.
')
Source: https://habr.com/ru/post/448528/
All Articles