Information Security of USB over IP Hardware Solutions
Recently I shared my experience in finding a solution for organizing centralized access to electronic protection keys in our organization. The comments raised a serious issue of information security of hardware solutions over USB over IP, which is very disturbing to us.
So, first, we still define the initial conditions.
To ensure the security of access to USB devices, organizational and technical measures have been taken:
')
1. Organizational security measures.
A managed USB over IP hub is installed in a high-quality key-lockable server cabinet. Physical access to it is ordered (ACS in the room itself, video surveillance, keys and access rights for a strictly limited circle of persons).
All USB devices used in the organization are divided into 3 groups:
2. Technical security measures.
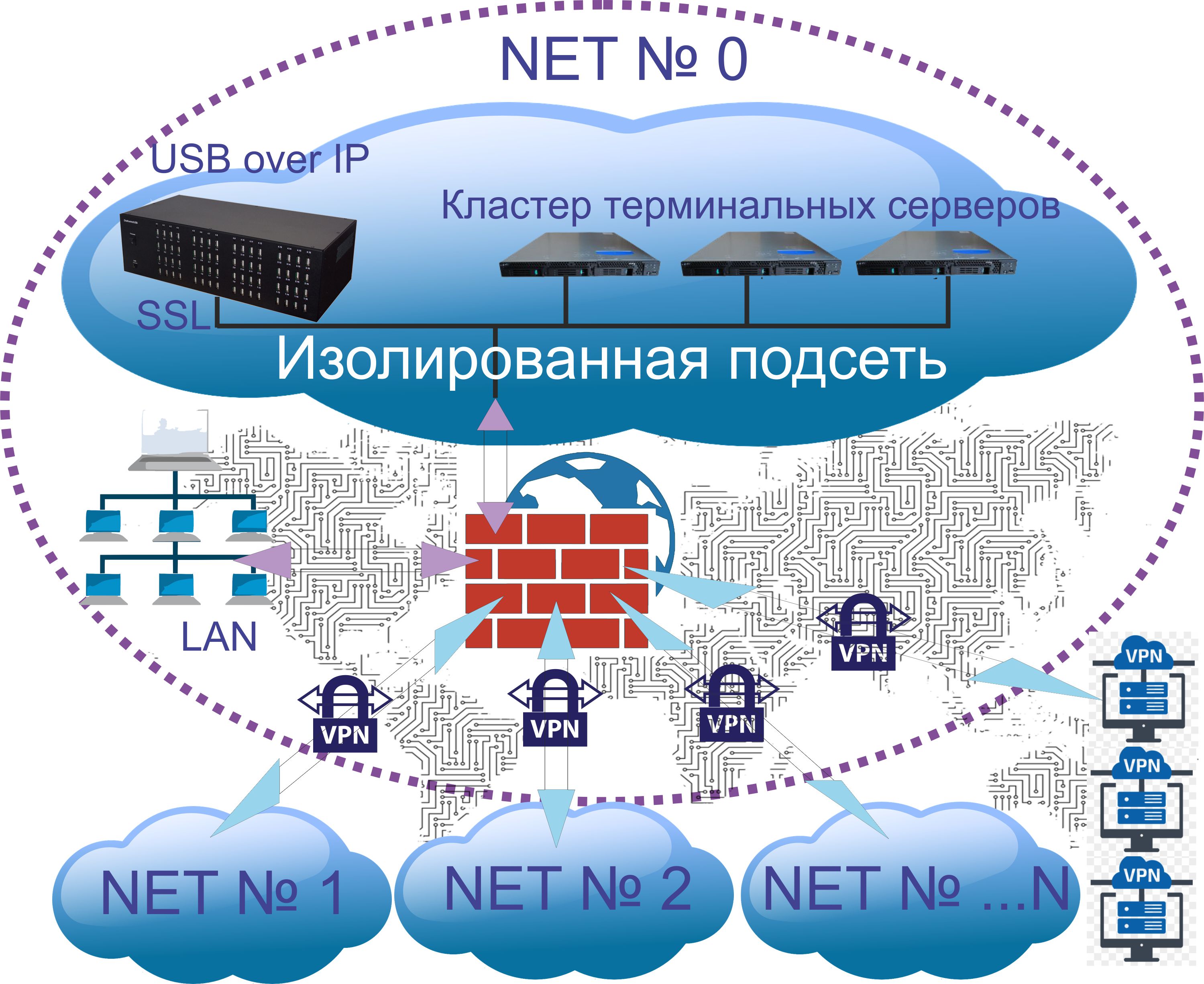
Network access to a managed USB over IP hub is provided only inside an isolated subnet. Access to an isolated subnet is provided:
On the most managed USB over IP hub DistKontrolUSB using its standard tools, the following functions are configured:
We assume that such organization of access to USB devices ensures their safe use:
In the comments I would like to hear specific practical measures that increase the information security of providing global access to USB devices.
So, first, we still define the initial conditions.
- A large number of electronic security keys.
- Access to them is required from various geographic locations.
- We consider only hardware solutions USB over IP and try to secure this decision by taking additional organizational and technical measures (we are not considering the alternatives yet).
- Within the framework of the article I will not completely describe the threat models we are considering (much can be seen in the publication ), but I’ll focus on two points. We exclude from the model social engineering and illegal actions of the users themselves. Consider the possibility of unauthorized access to USB devices from any of the networks without having regular credentials.

To ensure the security of access to USB devices, organizational and technical measures have been taken:
')
1. Organizational security measures.
A managed USB over IP hub is installed in a high-quality key-lockable server cabinet. Physical access to it is ordered (ACS in the room itself, video surveillance, keys and access rights for a strictly limited circle of persons).
All USB devices used in the organization are divided into 3 groups:
- Critical. Financial EDS - used in accordance with the recommendations of banks (not via USB over IP)
- Important. EDS for trading platforms, services, EDM, reporting, etc., a number of keys for software - are used with the use of a managed USB over IP hub.
- Not critical. A number of keys for software, cameras, a number of flash drives and disks with non-critical information, USB modems are used with the use of a managed USB over IP hub.
2. Technical security measures.
Network access to a managed USB over IP hub is provided only inside an isolated subnet. Access to an isolated subnet is provided:
- from the terminal server farm,
- VPN (certificate and password) to a limited number of computers and laptops; they receive permanent addresses via VPN;
- via VPN tunnels connecting regional offices.
On the most managed USB over IP hub DistKontrolUSB using its standard tools, the following functions are configured:
- For access to USB devices, USB over IP hub uses encryption (SSL encryption is enabled on the hub), although this may already be superfluous.
- Configured "restriction of access to USB devices by IP address." Depending on the IP address, the user is granted or not access to the designated USB devices.
- Configured "Restriction of access to the USB port by login and password." Accordingly, users are assigned access rights to USB devices.
- "Restricting access to a USB device by login and password" decided not to use, because All USB keys are connected to a USB over IP hub permanently and are not rearranged from port to port. It’s more logical for us to provide users with access to a USB port with a USB device installed for a long time.
- Physical switching on and off of USB ports is carried out:
- For the keys to the software and EDM - with the help of the task scheduler and assigned tasks of the hub (a number of keys were programmed to turn on at 9.00 and turn off at 18.00, a number from 13.00 to 16.00);
- For keys from trading platforms and a number of software - authorized users through the WEB interface;
- Cameras, a number of flash drives and disks with non-critical information are always on.
We assume that such organization of access to USB devices ensures their safe use:
- from regional offices (conditionally NET №1 …… NET № N),
- for a limited number of computers and laptops connecting USB devices via the global network,
- for users published on terminal application servers.
In the comments I would like to hear specific practical measures that increase the information security of providing global access to USB devices.
Source: https://habr.com/ru/post/448110/
All Articles