Positive Technologies Experts Revealed Attempts to Mass Exploit Critical Threats to Confluence
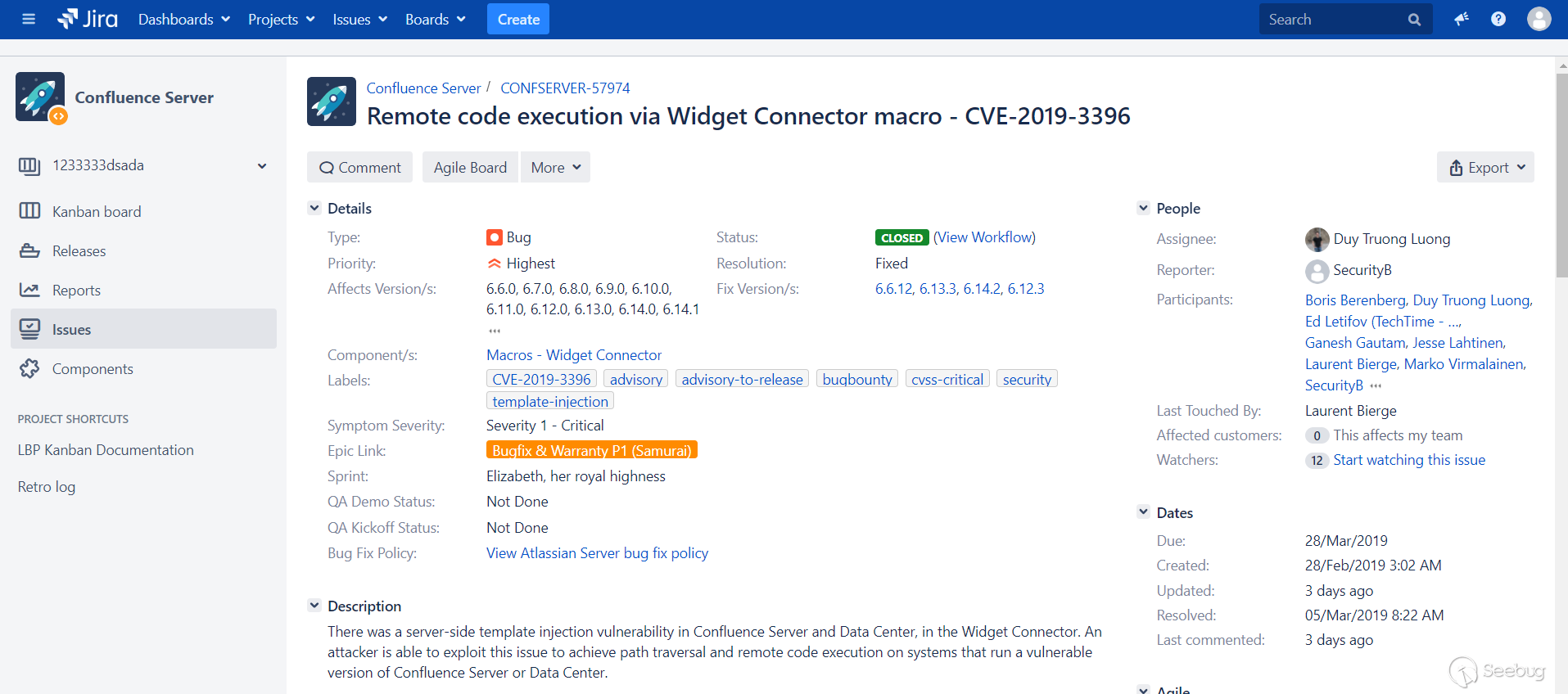
Image: Knownsec 404 Team
Information security researchers from Knownsec 404 Team studied the patch for the vulnerability discovered in March in Confluence and published the code for its operation. Using this security error allows attackers to be able to execute any commands on the Confluence server and download malware.
')
Shortly after the publication of the exploit to vulnerability, experts PT ESC found a massive attempt to exploit it. We tell you what the problem is and how to defend yourself.
What is the problem
Vulnerability CVE-2019-3396 arose due to an error in the code for the Widget Connector module in the Confluence Server. With its help, an attacker can force vulnerable Confluence to download a malicious template from his server and execute any commands. The attack does not require authorization on the server.
In a security bulletin published by the developers of Confluence from Atlassian, the vulnerability is described as follows:
An attacker can exploit a vulnerability to inject patterns on the service side, bypass the path and execute code remotely on systems with vulnerable Confluence Server and Data Server.
In addition, researchers from Assetnote and DEVCORE discovered a CVE-2019-3395 vulnerability in the WebDAV plugin. It allows server-side forgery (Server Side Request Forgery, SSRF). Hackers can send random HTTP and WebDAV requests from vulnerable Confluence Server and Data Server instances.
Vulnerable software versions:
- All versions 1.xx, 2.xx, 3.xx, 4.xx and 5.xx
- All versions 6.0.x, 6.1.x, 6.2.x, 6.3.x, 6.4.x, and 6.5.x
- All versions 6.6.x to 6.6.12
- All versions 6.7.x, 6.8.x, 6.9.x, 6.10.x and 6.11.x
- All versions 6.12.x to 6.12.3
- All versions 6.13.x to 6.13.3
- All versions 6.14.x to 6.14.2
Bug fixed:
- In version 6.6.12 and later versions 6.6.x
- In version 6.12.3 and later versions 6.12.x
- In version 6.13.3 and later versions 6.13.x
- In version 6.14.2 and higher.
Exploitation
Details of the vulnerability were published on April 10, and the next day, experts from Positive Technologies ESC discovered a massive scan of 8090 ports on the Internet - this is the standard port for the Confluence server.
It is easy to detect attempted attacks: it will always be accompanied by incoming POST requests to the URL / rest / tinymce / 1 / macro / preview and, in the case of a server hacking, outgoing requests to the attacker's FTP server to download the file with the .vm extension. According to the ZoomEye search service, at least 60,000 Confluence servers are available on the Internet.
In addition, experts have witnessed infection of Confluence servers by the Linux Spike Trojan malware, formerly known as MrBlack. It is an ELF file and is mainly intended for DDoS attacks.
When entering the system, the malware is fixed with the help of the rc.local file and starts each time the infected computer starts. After launch, in a separate thread and in an infinite loop, it collects information about the system and sends it to the server controlled by the attacking C2. Data collected includes information about the processor, network interfaces, and running processes. After that, an endless loop starts in a separate stream, in which it sends the string “VERSONEX: 1 | 1 | 1 | 1 | 1 | Hacker” to the server, and waits for a command in response.
The commands that can run the malware:
- execute the command through the shell
- start DDOS
- to finish work
The DDOS command contains the AES encrypted addresses of the servers to which the attack should be launched. The malware decrypts using a stitched key.
Available DDOS attack options:
- SYN flood
- LSYN flood
- UDP flood
- UDPS flood
- TCP flood
- CC flood
How to protect
Vulnerability CVE-2019-3396 was fixed on March 20, 2019. On the Atlassian website there is a security bulletin with its description and a list of versions with a fix. To fix the vulnerability, users need to upgrade the system to the versions included in the patch.
Also, to detect attempts to exploit the CVE-2019-3396 vulnerability and Linux Spike activity, we developed rules for Suricata IDS:
Source: https://habr.com/ru/post/447904/
All Articles