Network tools, or where to start pentester?
Pentester novice toolkit: we present a brief digest of the main tools that will be useful in the pentest of the internal network. These tools are already actively used by a wide range of specialists, so everyone will be well aware of their capabilities and mastering it perfectly.

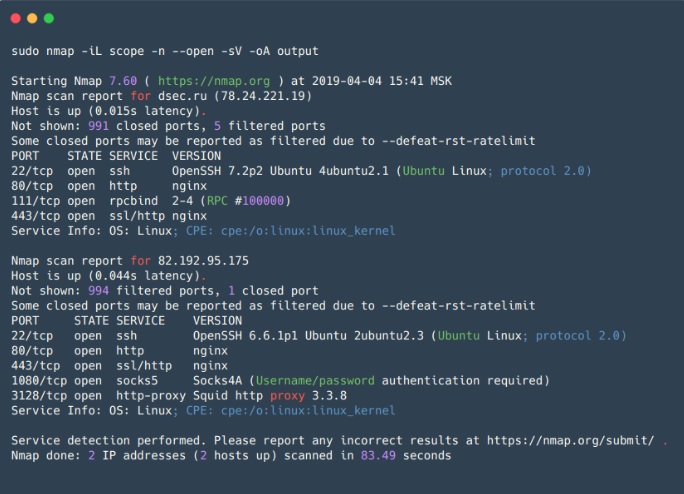
Nmap - opensource utility for scanning networks, is one of the most popular tools for security guards and system administrators. It is primarily used for port scanning, but, besides, it has a huge mass of useful functions, which, in fact, makes Nmap a super-combine for network research.
In addition to checking open / closed ports, Nmap can identify the service that is listening to the open port and its version, and sometimes helps identify the OS. Nmap has support for scripts to scan (NSE - Nmap Scripting Engine). Using scripts, it is possible to check vulnerabilities for various services (if, of course, there is a script for them, or you can always write your own) or stitch passwords from different services.
')
Thus, Nmap allows you to create a detailed map of the network, get maximum information about running services on hosts on the network, as well as proactively check some vulnerabilities. Nmap also has flexible scan settings, you can adjust the scan speed, the number of threads, the number of groups to scan, etc.
Convenient for scanning small networks and indispensable for spot scanning individual hosts.
Zmap (not to be confused with ZenMap), also an open source scanner, was created as a faster alternative to Nmap.
Unlike Nmap, Zmap does not wait for a response while sending a SYN packet, but continues scanning, waiting for responses from all hosts in parallel, so in fact it does not support the connection state. When the answer to the SYN packet comes, Zmap, by the contents of the packet, will understand which port and which host has been opened. In addition, Zmap sends only one SYN packet per scanned port. It is also possible to use PF_RING to quickly scan large networks, if you suddenly had a 10 Gigabit interface and a compatible network card at hand.
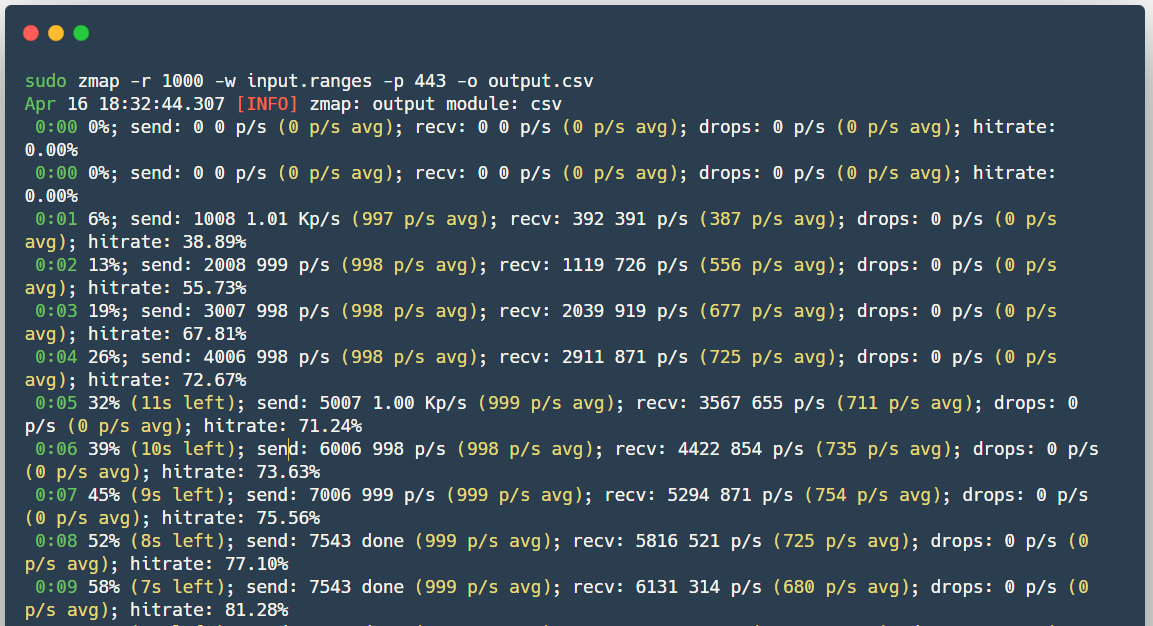
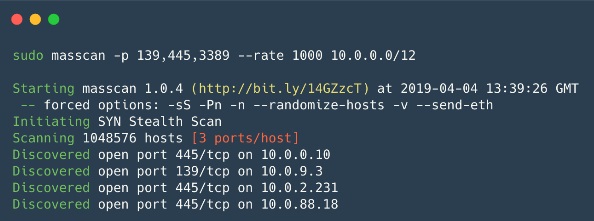
Masscan isamazing, but also an open source scanner that was created with one goal - to scan the Internet even faster (in less than 6 minutes at a speed of ~ 10 million packets / s). In fact, it works almost as well as Zmap, only even faster.
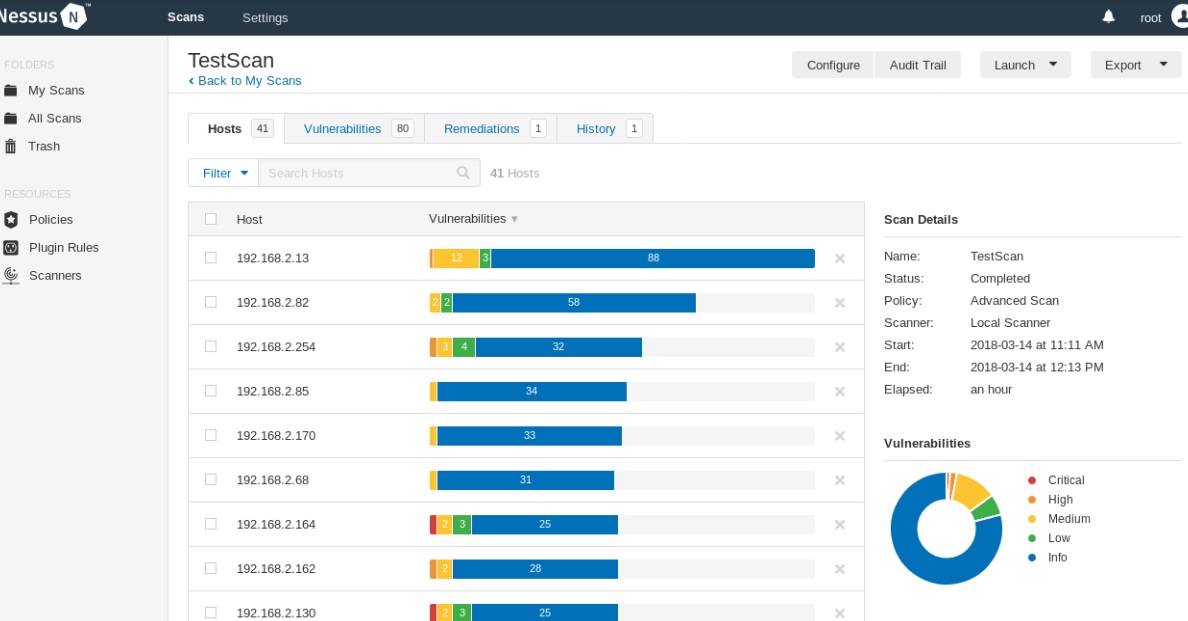
Nessus is a scanner to automate the verification and detection of known vulnerabilities in the system. The source code is closed, there is a free version of Nessus Home, which allows you to scan up to 16 IP addresses with the same speed and detailed analysis as in the paid version.
Able to identify vulnerable versions of services or servers, detect errors in system configuration, perform bruteforce vocabulary passwords. It can be used to determine the correctness of service settings (mail, updates, etc.), as well as in preparation for a PCI DSS audit. In addition, credentials for the host (SSH or domain account in Active Directory) can be sent to Nessus, and the scanner will gain access to the host and perform checks directly on it, this option is calledcredential scan . Convenient for companies conducting audits of their own networks.
Net-Creds is a Python tool for collecting passwords and hashes, as well as other information, such as visited URLs, downloaded files and other information from traffic, both in real time during the MiTM attack and from previously saved PCAP files . It is suitable for quick and superficial analysis of large volumes of traffic, for example, in network MiTM attacks, when time is limited, and manual analysis using Wireshark takes a lot of time.
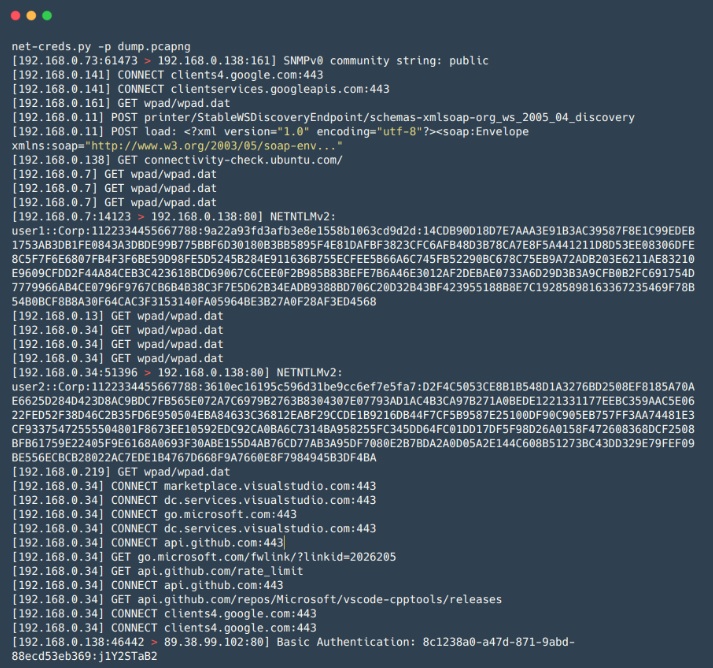
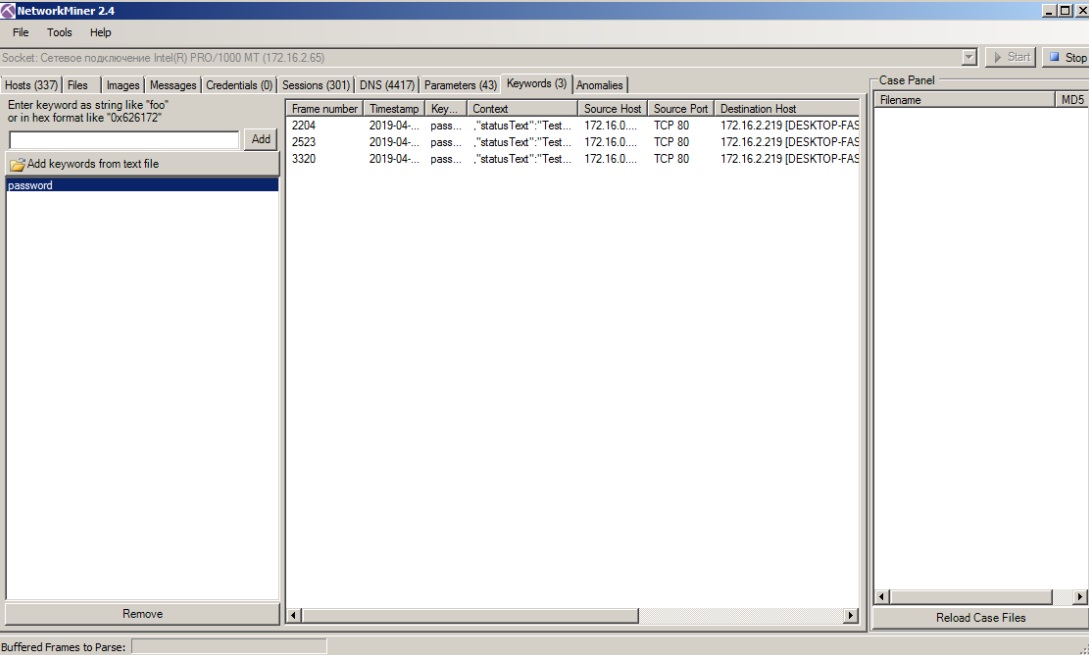
network-miner is an analogue of Net-Creds on the principle of operation, but it has more functionality, for example, it is possible to extract files transferred via SMB protocols. Like Net-Creds, convenient when you need to quickly analyze a large amount of traffic. Also has a user friendly graphical interface.
mitm6 is an IPv6 attack tool (SLAAC-attack). IPv6 is a priority in Windows (generally speaking, and in other operating systems too), and in the default configuration, the IPv6 interface is enabled, this allows an attacker to set up a DNS server for the victim using Router Advertisement packets, after which the attacker can change the victim's DNS . Perfect for carrying out a Relay attack with the ntlmrelayx utility, which allows you to successfully attack the Windows network.
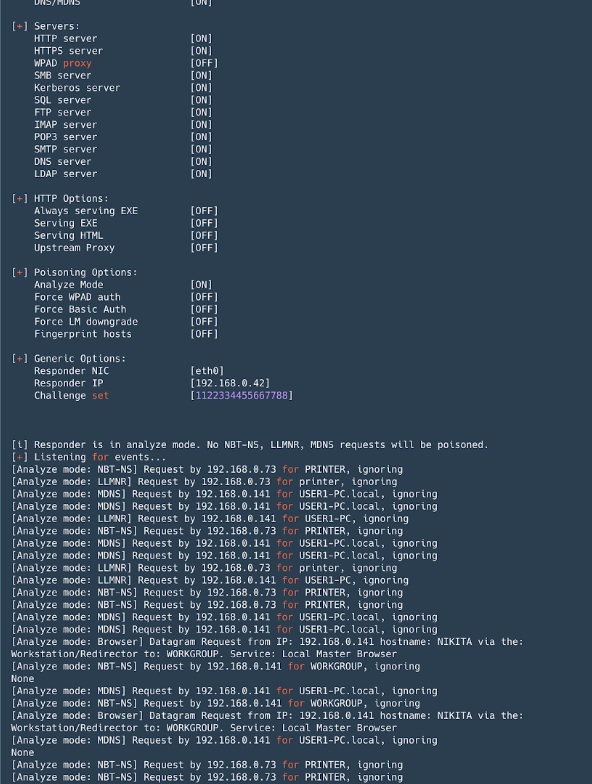
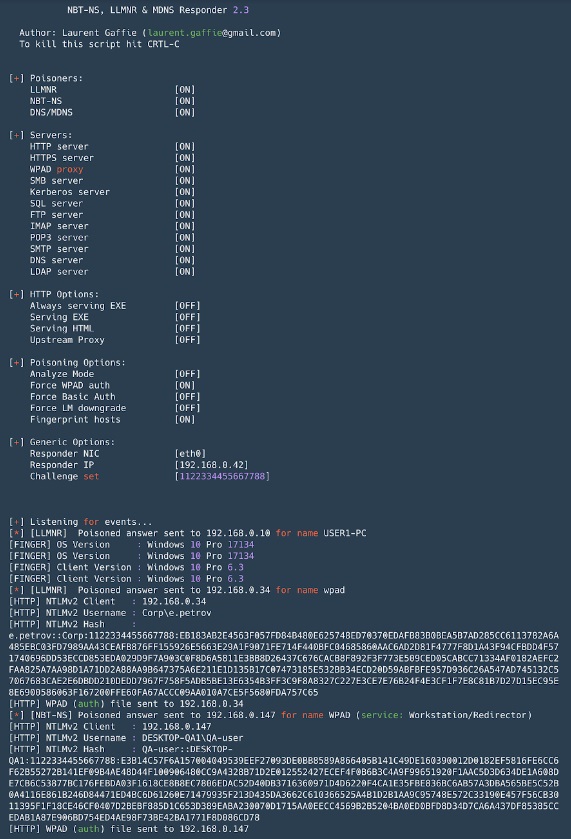
Responder is a tool for spoofing broadcast name resolution protocols (LLMNR, NetBIOS, MDNS). An indispensable tool in Active Directory networks. In addition to spoofing, it can intercept NTLM authentication, it also includes a set of tools for collecting information and implementing NTLM-Relay attacks.
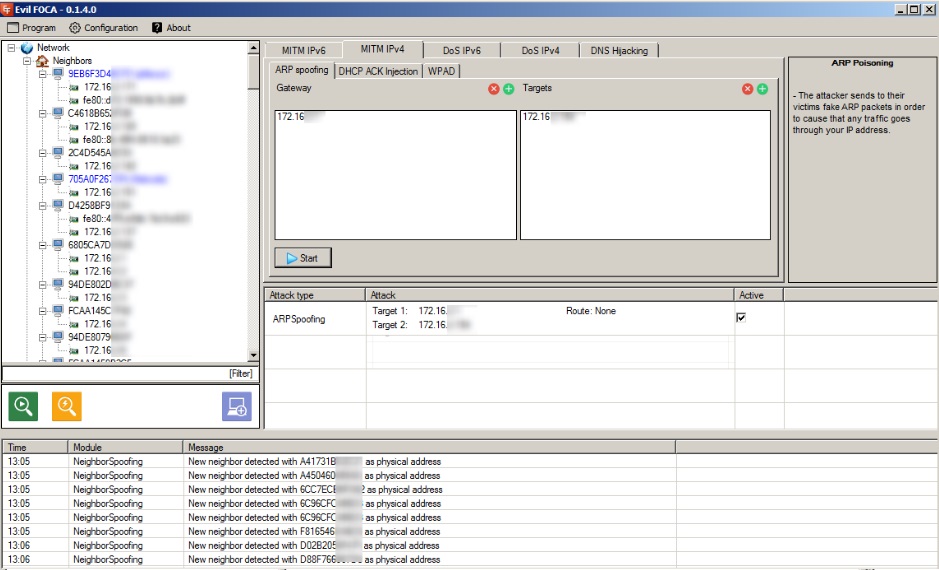
Evil Foca is a tool for testing various network attacks on IPv4 and IPv6 networks. Scans the local network, identifying devices, routers and their network interfaces, after which you can make various attacks on network participants.
Bettercap is a powerful framework for analyzing and attacking networks, and we are also talking about attacks on wireless networks, BLE (bluetooth low energy) and even MouseJack attacks on wireless HID devices. In addition, it contains the functionality to collect information from the traffic (similar to net-creds). In general, the Swiss knife (all in one). Recently, it still has a graphical web-based interface .

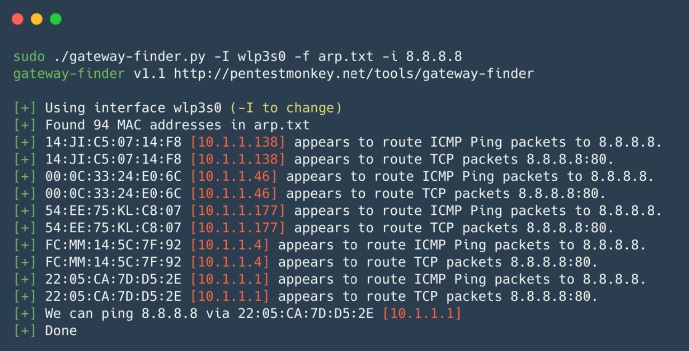
The gateway finder is a Python script that helps identify possible gateways on the network. Convenient for checking segmentation or searching for hosts that can route to the required subnet or Internet. Suitable for internal pentest when you need to quickly check for unauthorized routes or routes to other internal local networks.
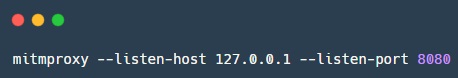
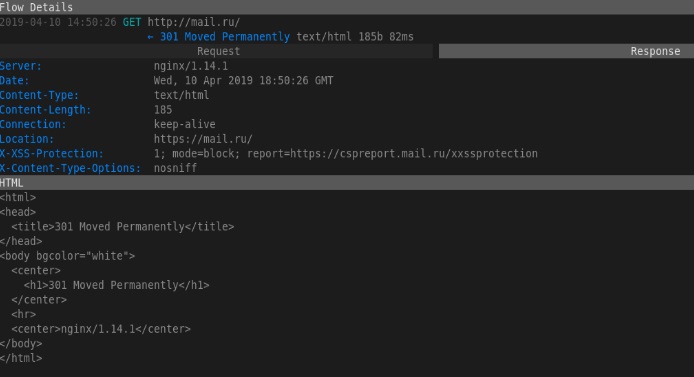
mitmproxy - opensource tool for analyzing SSL / TLS protected traffic. mitmproxy is convenient for intercepting and modifying protected traffic, of course, with some reservations; The tool does not attack SSL / TLS decryption. Used when you need to intercept and commit changes to traffic protected by SSL / TLS. Consists of Mitmproxy for traffic proxying, mitmdump is similar to tcpdump, but for HTTP (S) traffic, and mitmweb is a web interface for Mitmproxy.
SIET is a tool for exploiting the capabilities of the Cisco Smart Install protocol. It is possible to receive and modify the configuration, as well as to take control over the Cisco device. If you were able to get a Cisco device configuration, you can check it using CCAT , this tool is useful for analyzing the security of your Cisco device configuration.
Using the Cisco Smart Install protocol, you can:

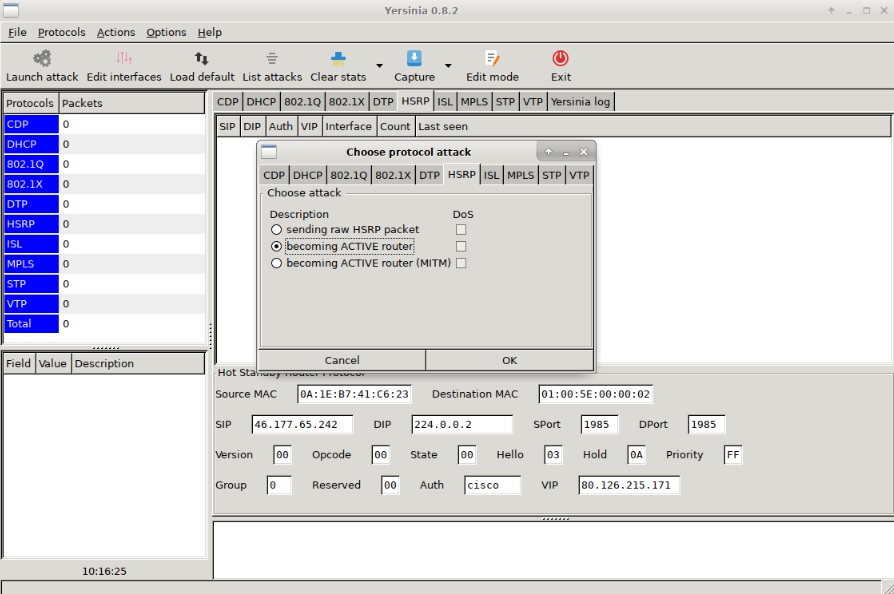
yersinia is a framework for L2 attacks, designed to exploit security flaws in various L2 network protocols.
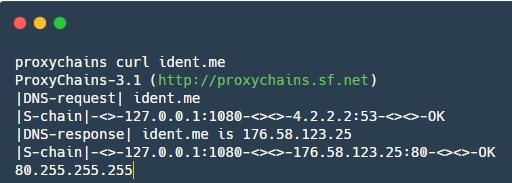
proxychains is a tool that allows you to redirect application traffic through a specified SOCKS proxy.
In this article, we briefly reviewed the advantages and disadvantages of the main pentest tools for the internal network. Stay tuned for updates, we plan to post such collections further: Web, databases, mobile applications - we will definitely write about this too.
Share your favorite utilities in the comments!

Content:
- Nmap
- Zmap
- Masscan
- Nessus
- Net credits
- network-miner
- mitm6
- Responder
- Evil_Foca
- Bettercap
- gateway_finder
- mitmproxy
- Siet
- yersinia
- proxychains
Nmap
Nmap - opensource utility for scanning networks, is one of the most popular tools for security guards and system administrators. It is primarily used for port scanning, but, besides, it has a huge mass of useful functions, which, in fact, makes Nmap a super-combine for network research.
In addition to checking open / closed ports, Nmap can identify the service that is listening to the open port and its version, and sometimes helps identify the OS. Nmap has support for scripts to scan (NSE - Nmap Scripting Engine). Using scripts, it is possible to check vulnerabilities for various services (if, of course, there is a script for them, or you can always write your own) or stitch passwords from different services.
')
Thus, Nmap allows you to create a detailed map of the network, get maximum information about running services on hosts on the network, as well as proactively check some vulnerabilities. Nmap also has flexible scan settings, you can adjust the scan speed, the number of threads, the number of groups to scan, etc.
Convenient for scanning small networks and indispensable for spot scanning individual hosts.
Pros:
- It works quickly with a small range of hosts;
- Flexibility of settings - you can combine options in such a way as to obtain the most informative data in a reasonable time;
- Parallel scanning - the list of target hosts is divided into groups, and then each group is alternately scanned, parallel scanning is used inside the group. Also the division into groups is a slight drawback (see below);
- Predefined sets of scripts for different tasks - you can not spend a lot of time choosing specific scripts, but specify groups of scripts;
- The output of the results is 5 different formats, including XML, which can be imported into other tools.
Minuses:
- Host group scan - information about a host is not available until the entire group is scanned. This is solved by setting in the options the maximum group size and the maximum time interval during which the response to the request will be expected before you stop trying or make another one;
- When scanning, Nmap sends SYN-packets to the target port and waits for any response packet or timeout in case there is no answer. This adversely affects the performance of the scanner as a whole, in comparison with asynchronous scanners (for example, Zmap or masscan);
- When scanning large networks using flags to speed up scanning (--min-rate, --min-parallelism), it can produce false-negative results by skipping open ports on the host. Also, these options should be used with caution, considering that a large packet-rate may result in an unintended DoS.

Zmap
Zmap (not to be confused with ZenMap), also an open source scanner, was created as a faster alternative to Nmap.
Unlike Nmap, Zmap does not wait for a response while sending a SYN packet, but continues scanning, waiting for responses from all hosts in parallel, so in fact it does not support the connection state. When the answer to the SYN packet comes, Zmap, by the contents of the packet, will understand which port and which host has been opened. In addition, Zmap sends only one SYN packet per scanned port. It is also possible to use PF_RING to quickly scan large networks, if you suddenly had a 10 Gigabit interface and a compatible network card at hand.
Pros:
- Scanning speed;
- Zmap generates Ethernet frames bypassing the TCP / IP system stack;
- The ability to use PF_RING;
- ZMap randomizes targets to evenly distribute the load on the scanned side;
- Ability to integrate with ZGrab (a tool for collecting information about services at the application level L7).
Minuses:
- It can cause a denial of service in network equipment, for example, disable intermediate routers, despite the distributed load, since all packets will pass through one router.

Masscan
Masscan is
Pros:
- The syntax is similar to Nmap, and the program also supports some options compatible with Nmap;
- The speed of work is one of the fastest asynchronous scanners.
- Flexible scanning mechanism - resuming an interrupted scan, load sharing across multiple devices (as in Zmap).
Minuses:
- Similar to Zmap, the load on the network itself is extremely high, which can lead to DoS;
- By default, it is not possible to scan at the L7 application layer.

Nessus
Nessus is a scanner to automate the verification and detection of known vulnerabilities in the system. The source code is closed, there is a free version of Nessus Home, which allows you to scan up to 16 IP addresses with the same speed and detailed analysis as in the paid version.
Able to identify vulnerable versions of services or servers, detect errors in system configuration, perform bruteforce vocabulary passwords. It can be used to determine the correctness of service settings (mail, updates, etc.), as well as in preparation for a PCI DSS audit. In addition, credentials for the host (SSH or domain account in Active Directory) can be sent to Nessus, and the scanner will gain access to the host and perform checks directly on it, this option is called
Pros:
- Separate scenarios for each vulnerability, the base of which is constantly updated;
- The output of the results is plain text, XML, HTML and LaTeX;
- API Nessus - allows you to automate the processes of scanning and obtaining results;
- Credential Scan, you can use your Windows or Linux credentials to check for updates or other vulnerabilities;
- The ability to write your own embedded security modules - the scanner has its own NASL (Nessus Attack Scripting Language) scripting language;
- You can set the time for regular scanning of the local network - due to this, the Information Security Service will be aware of all changes in the security configuration, the emergence of new hosts and the use of vocabulary passwords or default passwords.
Minuses:
- There may be violations in the operation of scanned systems - with the safe checks option disabled, it is required to work carefully;
- The version that allows commercial use is not free.

Net credits
Net-Creds is a Python tool for collecting passwords and hashes, as well as other information, such as visited URLs, downloaded files and other information from traffic, both in real time during the MiTM attack and from previously saved PCAP files . It is suitable for quick and superficial analysis of large volumes of traffic, for example, in network MiTM attacks, when time is limited, and manual analysis using Wireshark takes a lot of time.
Pros:
- The identification of services is based on packet analysis instead of defining the service by the port number used;
- Easy to use;
- A wide range of retrievable data - including logins and passwords for FTP, POP, IMAP, SMTP, NTLMv1 / v2 protocols, as well as information from HTTP requests, such as login forms and basic auth.

network-miner
network-miner is an analogue of Net-Creds on the principle of operation, but it has more functionality, for example, it is possible to extract files transferred via SMB protocols. Like Net-Creds, convenient when you need to quickly analyze a large amount of traffic. Also has a user friendly graphical interface.
Pros:
- GUI;
- Visualization and classification of data into groups - simplifies traffic analysis and makes it fast.
Minuses:
- In the evaluation version, some functionality is limited.

mitm6
mitm6 is an IPv6 attack tool (SLAAC-attack). IPv6 is a priority in Windows (generally speaking, and in other operating systems too), and in the default configuration, the IPv6 interface is enabled, this allows an attacker to set up a DNS server for the victim using Router Advertisement packets, after which the attacker can change the victim's DNS . Perfect for carrying out a Relay attack with the ntlmrelayx utility, which allows you to successfully attack the Windows network.
Pros:
- It works fine on many networks, precisely because of the standard configuration of Windows hosts and networks;
Responder
Responder is a tool for spoofing broadcast name resolution protocols (LLMNR, NetBIOS, MDNS). An indispensable tool in Active Directory networks. In addition to spoofing, it can intercept NTLM authentication, it also includes a set of tools for collecting information and implementing NTLM-Relay attacks.
Pros:
- By default, it raises many servers with NTLM authentication support: SMB, MSSQL, HTTP, HTTPS, LDAP, FTP, POP3, IMAP, SMTP;
- Allows you to replace the DNS in the event of MITM attacks (ARP-spoofing, etc.);
- Fingerprint hosts that have made a broadcast request;
- Analyze mode - for passive observation of queries;
- The captured hash format with NTLM authentication is compatible with John the Ripper and Hashcat.
Minuses:
- When running on Windows, binding port 445 (SMB) is fraught with some difficulties (it requires stopping the corresponding services and rebooting).


Evil_Foca
Evil Foca is a tool for testing various network attacks on IPv4 and IPv6 networks. Scans the local network, identifying devices, routers and their network interfaces, after which you can make various attacks on network participants.
Pros:
- Convenient for MITM attacks (ARP spoofing, DHCP ACK injection, SLAAC attack, DHCP spoofing);
- DoS attacks can be performed - with ARP-spoofing for IPv4 networks, with SLAAC DoS in IPv6 networks;
- You can perform DNS hijacking;
- Easy to use, user-friendly graphical interface.
Minuses:
- It works only under Windows.

Bettercap
Bettercap is a powerful framework for analyzing and attacking networks, and we are also talking about attacks on wireless networks, BLE (bluetooth low energy) and even MouseJack attacks on wireless HID devices. In addition, it contains the functionality to collect information from the traffic (similar to net-creds). In general, the Swiss knife (all in one). Recently, it still has a graphical web-based interface .
Pros:
- Accounting sniffer - you can catch visited URLs and HTTPS hosts, HTTP authentication, credentials for many different protocols;
- Many built-in MITM attacks;
- Modular HTTP (S) transparent proxy - you can control traffic depending on your needs;
- Built-in HTTP server;
- Support for caplets - files that allow scripting to describe complex and automated attacks.
Minuses:
- Some modules - for example, ble.enum - are partially not supported by macOS and Windows, some are designed only for Linux - packet.proxy.

gateway_finder
The gateway finder is a Python script that helps identify possible gateways on the network. Convenient for checking segmentation or searching for hosts that can route to the required subnet or Internet. Suitable for internal pentest when you need to quickly check for unauthorized routes or routes to other internal local networks.
Pros:
- Easy to use and customize.

mitmproxy
mitmproxy - opensource tool for analyzing SSL / TLS protected traffic. mitmproxy is convenient for intercepting and modifying protected traffic, of course, with some reservations; The tool does not attack SSL / TLS decryption. Used when you need to intercept and commit changes to traffic protected by SSL / TLS. Consists of Mitmproxy for traffic proxying, mitmdump is similar to tcpdump, but for HTTP (S) traffic, and mitmweb is a web interface for Mitmproxy.
Pros:
- It works with various protocols, and also supports modification of various formats, from HTML to Protobuf;
- API for Python - allows you to write scripts for non-standard tasks;
- It can work in transparent proxy mode with traffic interception.
Minuses:
- The dump format is not compatible with anything - it is difficult to use grep, you have to write scripts.


Siet
SIET is a tool for exploiting the capabilities of the Cisco Smart Install protocol. It is possible to receive and modify the configuration, as well as to take control over the Cisco device. If you were able to get a Cisco device configuration, you can check it using CCAT , this tool is useful for analyzing the security of your Cisco device configuration.
Pros:
Using the Cisco Smart Install protocol, you can:
- Change the address of the tftp server on the client device by sending one distorted TCP packet;
- Copy the device configuration file;
- Replace device configuration, for example, by adding a new user;
- Update iOS image on device;
- Run an arbitrary set of commands on the device. This is a new feature that works only in versions 3.6.0E and 15.2 (2) E iOS.
Minuses:
- It works with a limited set of Cisco devices, you also need a “white” IP to receive a response from the device, or you need to be in the same network with the device;

yersinia
yersinia is a framework for L2 attacks, designed to exploit security flaws in various L2 network protocols.
Pros:
- Allows attacks on the protocols STP, CDP, DTP, DHCP, HSRP, VTP and others.
Minuses:
- Not the most convenient interface.

proxychains
proxychains is a tool that allows you to redirect application traffic through a specified SOCKS proxy.
Pros:
- It helps to redirect the traffic of some applications that by default do not know how to work with a proxy.

In this article, we briefly reviewed the advantages and disadvantages of the main pentest tools for the internal network. Stay tuned for updates, we plan to post such collections further: Web, databases, mobile applications - we will definitely write about this too.
Share your favorite utilities in the comments!
Source: https://habr.com/ru/post/447882/
All Articles