IoT security. Issue 2. Smart home

Smart home is represented by a wide range of devices. In the second part of the IoT security publication cycle, smart set-top boxes, smart kitchen, voice assistants and lighting will be covered. Link to 1 part .
Smart home security
Smart TV - Apple TV

Apple TV is a digital media player with a wide range of capabilities within a separate operating system, managed by phone, Siri, remote control and expandable by software due to third-party applications. Apple TV has several generations:
- I generation - Y'07, MacOS X, traditional HDD & USB Port
- II generation - Y'10, iOS + MicroUSB
- III generation - Y'12, iOS + MicroUSB
- IV generation - Y'15, tvOS (iOS) + USB-C & Bluetooth
- V generation (4K) - Y'17, tvOS (iOS) + Bluetooth, without USB
- VI generation - model 2018, without USB
Known ways to access Apple TV
Such methods can be accessed by the 1st generation models presented at the conference in 2009 “Hacking the Apple TV and Where is Your Forensic Data Lives”, Kevin Estis and Randy Robbins, Def Con 2009 ( presentation , video ). The model of this generation was made based on Mac OS X and access to the data was reduced to the analysis of the hard disk and the features of connecting to TV in general.
')
Access to data from Apple TV generations II-V is very similar in methodology to access to other Apple products and comes down to
- Backup analysis with various tools, including forensic tools.
- Search for a jailbreak to explore data outside of backups, or to research an already cracked TV
- Content analysis, weather clients, stream content: Netflix, iTunes, NHL, NBA, Vimeo, YouTube, etc.
- Access to application data in order to retrieve accounts and credit cards, as well as other useful information.
Jailbreak Utilities
Unlike watches, the Jailbreak kit of utilities for TV is widely represented, except for models of the 3rd generation:
- The actual list is updated, for example, on the pangu resource.
- Apple TV 1 - scripts, ssh, eject disc and other methods similar to Mac.
- Apple TV 2 - Seas0npass jail for tvOS 4.3 - tvOS 5.3 (untethered) & tvOS 6.1.2 (tethered) versions.
- Apple TV 4 - Pangu9 jail for tvOS 9.0 versions - tvOS 9.0.1, LiberTV jail for tvOS 9.1 versions - tvOS 10.1, GreenG0blin jail for tvOS 10.2.2 versions.
- Apple TV 4/5 - LiberTV jail for tvOS 11.0 and 11.1, Electra jail for tvOS 11.2 - tvOS 11.3.
Password management
The issue of password management for many devices is fundamental, and considering smart watches, it was noted that passwords and pincodes are not mandatory. For Apple TV, passwords, like for many other TVs, are not used at all except to restrict access to content and only affect purchases made in the app store within applications, content, changing settings, and deleting linked devices ( while tying devices does not requires a password ).
USB analysis
For earlier models, except for the last two years, the USB port, although formally reserved for official purposes, was used to obtain basic information about the device; officially disappeared, starting with the 5th generation model of the Apple 5th Gen (4k). Basic information includes device time information, logs, access to a Media folder that is not system (/ private / var / mobile / Media), information about mac addresses Wi-Fi, Bluetooth, Ethernet, device name, Serial ID, model . Ideviceinfo, idevicesyslog can be used as data acquisition tools .
Backups
Backups give access to the following data, which overlap with USB analysis data:
- Event log
- Data media in the database MediaLibrary.sqlitedb.
- iCloud data.
- Wi-Fi network.
- Timeline use of the device.
- Shopping databases incl. content.
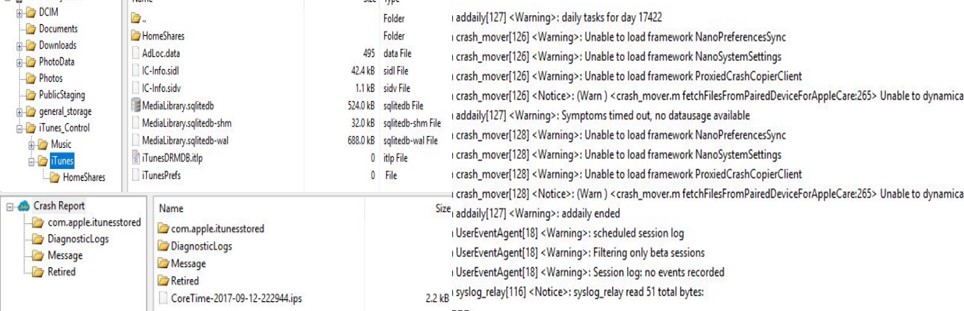
TV analysis with jailbreak
These TVs allow you to access more data: timezone, Wi-Fi history, keyboard dictionary, account information, settings, a list of weather cities, headboard information (user content information), as well as screenshots of user content, cached video , a list of installed applications and data of the applications themselves.
Profiling
Profiling is one of the defense mechanisms in some recent versions of tvOS 11.3+ and iOS 11.3+. The mechanism allows you to specify a list or specific devices that will be allowed; after which the interaction will be limited to certain devices, and no third-party device can connect to your set-top box. The mechanism can be used both within the framework of Apple’s corporate management of devices, and within personal devices through profile settings with the necessary parameters (provided that you use Mac OS Server)
Amazon tv

Amazon Fire TV is a set-top box with a similar set of features. It comes in two editions - in the form of a standard set-top box (Fire TV box) and a compact version of the Chromecast type (Fire TV Stick). At the same time, like many Android solutions, applications can be downloaded via the ADB-sideload mechanism, which allows many users to receive content without paid subscriptions.
Due to the latter fact, root-tools are not widely used for FireOS, and the available routing tools are divided into classic root-tools and rooted firmware.
The best-known representative of root tools is KingRoot, which allows you to gain access mainly for older versions such as 5.0.5, although it is not limited to them. A special feature is also the fact that most of the tools are sharpened for using the keyboard and mouse, and not the TV remote, therefore it is important to have Bluetooth connections to connect wireless keyboards and mice.
Of the features of FireOS, sideloading without root is worth mentioning, a locked bootloader (51.1.xx is not blocked, 5.xxx is blocked, but 5.0.x can be unlocked, and there is no information about older versions), and it is acceptable to perform downgrade to perform root old versions.
Available versions of root tools and firmware:
- Fire TV 1 - root for versions 51.1.0.0 - 51.1.6.3, 5.0.3, 5.0.5, no root for 5.0.5.1, 5.2.1.0 - 5.2.6.3
- Fire TV 2 - root for versions 5.0.0 - 5.2.1.1, no root for 5.2.4.0 - 5.2.6.3
- Fire TV 2 - 5.2.6.6 - pre-rooted ROM
- Fire TV 3, Fire TV Cube - no root or pre-root ROMs
- Fire TV Stick 1 - root for versions 5.0.0 - 5.2.1.1 and no root for 54.1.2.3 and higher versions, 5.2.1.2 - 5.2.6.3
- Fire TV Stick 2 - no software root, but found a way to physically access the eMMC drive
- Fire TV Edition television - root for versions 5.2.5.0 and no root for 5.2.5.1 - 5.2.6.3
The official tools among forensic solutions are currently unknown, however forensics methods are typical for Android solutions (using DD, sideload + ADB, etc.)
When examining device data in the basic application set, the following useful data sets can be distinguished:
- Browser information is stored in browser.db and includes browser history and other information stored by Mozilla Firefox.
- Images - are stored in [root] /data/com.amazon.bueller.photos/files/cmsimages including. here are images from amazon cloud. There is a feature here: in spite of the originality of the images, the images on the TV are converted in the TV format (as a result, two files with the same extension and different names can be found on the device * -full.jpg and * -thumb.jpg).
- Bluetooth devices - information about devices, names, mac-addresses is stored in [root] /data/com.amazon.device.controllermanager/databases/devices.
- Amazon logs - various information about device activity with timestamps, which can be correlated with user activity and application launching [root] /data/com.amazon.device.logmanager/files + Log.amazon \ main.
- Amazon appstore - data stored in com.amazon.venezia.
- / cache / = cache and previews for downloaded and viewed applications + recommended.
- / databases / = sqlite files distributed by folders.
- / databases / contentProvider = “Apps” table containing application names with an indication of the cache and preview (“thumbnailUri”), (“previewUri”) in the ../cache folder.
- / databases / locker = orders, wish list, tasks, applications, cache, etc.
- / databases / logging = event logs.
Voice Assistants (Amazon Echo Dot & Alexa app)
Amazon provides voice assistants in the form of an Echo physical device and a Alexa app software solution. They are intended for the same purposes of managing smart home and other devices that support integration with the Amazon API for voice assistants.

At the moment, the hardware assistant does not have ways to communicate with it via cable, familiar to Android or other Amazon devices, such as FireTablet: USB communication is limited to obtaining basic information through the MediaTek driver set and the SP Flash Tool of the device, and the device loader is blocked. Amazon allows developers to use their certificates to protect the transmitted data ( link number 1 , link number 2 ), but users are not given any opportunity to install additional root certificates on the device, which excludes the possibility of MITM. Also the device is protected from SSL Strip attacks. However, like many smart things, the firmware download is performed over HTTP without additional encryption.
GET /obfuscated-otav3-9/…/update-kindle-full_biscuit-XXXX_user_[XXXXXXXXX].bin HTTP/1.1 Host: amzdigitaldownloads.edgesuite.net Connection: close User-Agent: AndroidDownloadManager/5.1.1 (Linux; U; Android 5.1.1; AEOBC Build/LVY48F) ro.build.version.fireos=5.5.0.3 ro.build.version.fireos.sdk=4 Fire OS is based on Android and has the following correspondence.
- ver 5.x - Android 5.1.1 Lollipop. Echo is running version 5.x
- ver 6.x - Android 7.1 Nougat
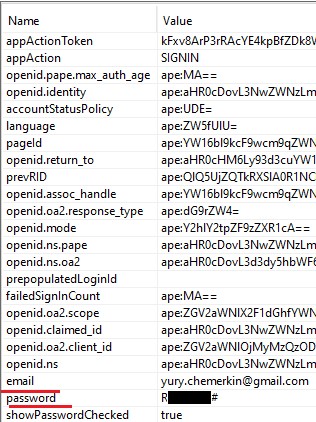
At the same time, speaking of the software assistant, it should be noted widespread support not only of the Kindle OS, but Android and iOS, as well as the lack of protection mechanisms against MITM. For example, credentials can be obtained in the query 'https://www.amazon.com/ap/signin'
{"Credentials":{"AccessKeyId":"ASIAXHE6EPSWNVIGFBVP","Expiration":1.538588872E9,"SecretKey":"+8gSx7/H.....U="},"IdentityId":"us-east-1:503e25f6-2302-4dcd-8cb2-64a0e888f76b"}- Mail, Password from POST request 'https://www.amazon.com/ap/signin'.
- Token and device information.
- The country code is “RU”.
Also in the traffic information about the user profile (or profiles, as multi-user usage is supported) is transmitted:
- Name, address for payment, address for delivery.
- Device ID, account, device capabilities and their types.
- Answers in .mp3 format are stored for several months.
Local data within the backup contains mainly the metrics and logs of devices, the list of devices and their serial numbers, account summary and settings.
One of the interesting ways to attack assistants is to select a pin-code, which can be performed with a minimum delay between attempts and no limit on the number of times. This method was published in Security Analysis of the Amazon Echo in 2017 with the accompanying script. The procedure is as follows:
- The computer waits for the word to wake up and the next command is a purchase request.
- Alexa offers results and offers to order.
- The computer confirms the order and Alexa requests a four-digit PIN.
- The first attempt to select a PIN is performed.
- Alexa accepts or does not accept PIN.
- The process is repeated until the correct PIN is found. Each iteration of 2 attempts to request PINs takes 30 seconds and, based on the assumption of a total pool of 10,000 PIN codes, it takes 42 hours to select the correct code.
Smart kitchen / teapots (Redmond)
Redmond is a supplier of smart technology in Russia. To work with a set of "smart features", we offer the Ready for Sky offer, which is made in two versions - an application for direct interaction via Bluetooth and a hub application, which on the one hand directly interacts with the device, and on the other hand, allows you to control equipment via the Internet.

From local data that fall into backup copies (R4S.sqlite), only a list of devices and models, a list of recipes and parameters, user data without a password (only username, email), as well as user devices and mac-addresses of devices are found.
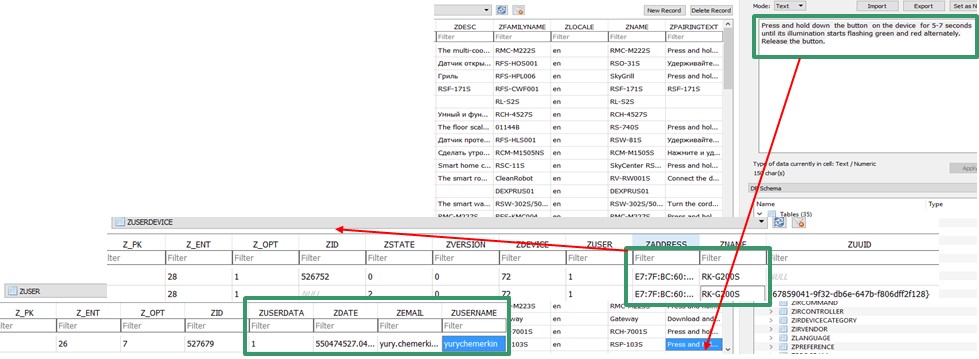
Within the network data, there is no protection against data interception with a certificate, so you can access the firmware version and the device image (this data is transmitted via http), a list of recipes for the device, a list of actions
https://content.readyforsky.com/api/program/catalog/id:IN:90,97?locale=en "id": 90, "protocol_id": 0, "value": "BOILING", / HEATING "value": "40", | "value": "55", | "value": "70", | "value": "85", | "value": "95". Also, credentials, tokens, incl. when prompted to change the password
https://content.readyforsky.com/headless/change-password {"current_password": "1", "plainPassword": "1"} { "error": "invalid_grant", "error_description": "The access token provided is invalid."} { "access_token": "YjNhYmEwOWM1ZDcwYTk0ODU1ODhmZDZiMDRjNjA5NzUyN2YzM2VhNGUyMjBhYzc0ZjBhYWRhY2IzZmNjMzdiOA", "expires_in": 86400, "token_type": "bearer", "scope": "r4s", "refresh_token": "YzE4ZGUwN2NkMzdiMDBlYmM5NGQwMGVjYmU4YThkYTVkMGE1ZTc4ODQ2MDRkNjhhZWY4NGIxZjlkODRhZGI3MQ“ } User information (https://content.readyforsky.com/api/user/current) and information about the internal network structure (IP address), device information (model, mac-address, hub name)
Client Address | 192.168.1.38:50654 (port changes)
Remote Address | content.readyforsky.com/178.62.194.132:443 (fixed port)
https://content.readyforsky.com/api/device/user “name": "RK-G200S", "address": "E7:7F:BC:60:C2:2A", "name": "Gateway XIAOMI Redmi 4X", "address": "77d3efcf-f627-402e-bbed-4ee0c8290417", Lighting
Smart lighting was designed to optimize costs, based on the automation of tasks. It is presented in the article by popular models:
- Lightify
- IKEA TRÅDFRI
- Philips HUE

Lightify
LIGHTIFY Home is an Internet of Things platform with cloud support and the ability to extend functionality. Work requires Lightify-account. Data transfer is performed using QUIC protocol with encryption over UDP; for QUIC and gQUIC decryption, wireshark of the latest version 2.9 ( v2.9.1rc0-332-ga0b9e8b652, v2.9.1rc0-487-gd486593ce3 ) is recommended , but better than 3.0 and higher , because in various builds of version 2.9 there were problems with support for protocol decryption (and version 2.8.6 was offered as a stable version for download). Lightify Gateway works over TCP without encryption (with local interaction) and using a binary protocol that is parsed and for which there is support from third-party tools . Accounting data is stored locally as part of backup files.
IKEA TRÅDFRI
IKEA bulbs also provide control on and off, but as a bonus, there is a change of colors. New models are already divided into original Ikea and branded with Xiaomi. Currently does not support remote control. Firmware update is traditionally performed via http JSON-file, which contains incl. available firmware for all TRÅDFRI devices
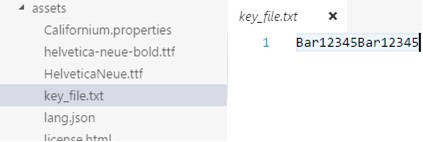
http://fw.ota.homesmart.ikea.net/feed/version_info.json The interaction is carried out over UDP using DTLS (SSL for UDP) and encryption. The pre-shared key used for handshaking when binding devices is the secret key. To connect the application with the hub, the user needs to scan the QR code that contains the “Serial Number” (in fact, the MAC address) and the “Security Code” of the device. The security code is stored locally within the keystorage framework and is used for further encryption using the AES algorithm. However, if the application is running on an old Android 4.3 device or below or a downgrade APK attack was performed, the key can be found in the APK itself in the file “key_file.txt” and will be hard-coded “Bar12345Bar12345”. Downgrade-attack is quite popular both within the framework of forensic solutions and conventional adb-commands to downgrade the apk-application version, in order to exploit the vulnerabilities of previous versions in data protection. Support and the ability to perform downgrade attacks depends on the device, OS version and device manufacturer, as well as the compatibility of the new and old version of the application databases.
Philips HUE
Philips Hue offers a wide range of smart lighting products for indoor and outdoor use. In 2016, the lighting of this manufacturer was already attacked via ZigBee from a distance of 200 meters due to an error in the communication protocol. Online communication between the hub and servers is performed securely and protected from data interception. At the first acquaintance, the key for data expansion on AES was not found (there is an assumption that it may be included in the firmware). The interaction between the application and the server works over SSL with protection against SSL Strip & MITM attacks. Local interaction - via HTTP.
PUT http://192.168.1.38/api/Ds7KfNjjYtC8uN mU8azGBiOSj-uacXI0q0JKaTs/groups/1/action as well as loading firmware
http://iotworm.eyalro.net/ Tips
Tips for protecting smart devices can be divided into the following groups:
Network Security Group
- Masking titles . By default, device names have base names associated with the device model, manufacturer, or user name. For this reason, it is not recommended to give names that uniquely identify user information.
- Encryption The use of encryption in home networks and parameters to avoid weak encryption.
- Guest networks . The proposed division of Wi-Fi for the use of critical information and visitors / friends, or disable this mode.
- Network segmentation . The network is divided into virtual segments based on the degree of criticality of the transmitted data, for example, the allocation of devices and hubs into one IOT subnet, devices that interact with critical and bank data into another IOT subnet, and test or untrusted devices into the third. If the router supports multi SSIDs mode, then this can also be used to separate networks.
- Firewall Firewall is a must-have in an environment where more and more devices are accessible via the Internet and you need to limit the scenarios of their availability.
- Restriction of public use . I propose to divide and limit the storage of critical data on wearable devices that may be lost, especially given that in the cloud many data are aggregated and become cross-accessible. Also for public devices, it is not recommended to enable connection modes with untrusted devices, as well as to use a large number of applications that do not properly protect data.
Password Management Group
- Default credentials . All devices by default or do not have passwords, or have a known list of default passwords that should be changed immediately.
- Unique passwords . As a rule, the recommendation is to use unique passwords that have been tested by several password managers.
Software Management Group
- Settings. Change default settings and change settings based on usage scenarios.
- Opportunities. Disabling or limiting features that are not required in scripts. For example, remote control, linking devices of the category of smart home or car with Facebook or other social networks.
- Applications. Differentiating devices and applications from the point of view of critical data, instead of mixing within a single device, as well as reducing the number of applications that do not protect the stored or transmitted data.
- Updating the system solves security problems, but not always a new update brings 100% protection, such as the ability to make backup copies with any new password for iOS 11+. Also, a number of IOT-devices and even ordinary routers, the older they are, the more often they do not offer convenient updating mechanisms from the user's point of view, therefore it is necessary to monitor changes and update devices on your own.
- VPN to protect the network, network segments and individual applications and devices, especially in public outlets.
Hack Tools group
- Suspicious applications - applications outside official stores, junk applications.
- Hacked - hacked applications "without registration and SMS" + pirated, as well as tools for hacking.
- Firmware - firmware vendors (although the facts are known pre-installed malicious code), as well as clean firmware.
Group "Cloud and third-party utilities and services"
- Cloud IoT - analysis of cloud solutions audit reports.
- Third-party services for IOT - often automation solutions are the point of data collection in one place (within a user account) and in case of security problems they represent a large array of critical user data and mechanisms for managing smart things.
Source: https://habr.com/ru/post/447720/
All Articles