WhatsApp in the palm of your hand: where and how can you detect forensic artifacts?

Want to find out what types of forensic artifacts WhatsApp exist in different operating systems and where exactly they can be detected - then you should be here. With this article, Igor Mikhailov, a specialist in the Laboratory of Computer Forensics at Group-IB, opens a series of publications on WhatsApp forensic research and on what information can be obtained from analyzing the device.
Immediately, we note that different types of WhatsApp artifacts are stored in different operating systems, and if a researcher can extract certain types of WhatsApp data from one device, this does not mean that these types of data can be extracted from another device. For example, if a Windows system block is removed, then WhatsApp chats will probably not be found on its disks (with the exception of backup copies of iOS devices that can be detected on the same drives). With the withdrawal of laptops and mobile devices will have its own characteristics. Let's talk about this in more detail.
')
WhatsApp artifacts in the Android device
In order to extract WhatsApp artifacts from a device running Android OS, a researcher must have superuser rights ( 'root' ) on the device under study or be able to extract the physical memory dump of the device or its file system by other means (for example, using software vulnerabilities of a specific mobile device). devices).
Application files are located in the phone’s memory in the section in which user data is stored. As a rule, this section is named 'userdata' . Subdirectories and program files are located on the path: '/data/data/com.whatsapp/' .
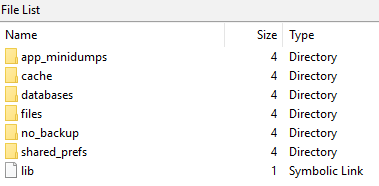
The main files that contain forensic artifacts of WhatsApp in Android OS are the databases 'wa.db' and 'msgstore.db' .
The 'wa.db' database contains a full list of WhatsApp user’s contacts, including a phone number, a display name, timestamps, and any other information provided when registering with WhatsApp. The file 'wa.db' is located along the path: '/data/data/com.whatsapp/databases/' and has the following structure:
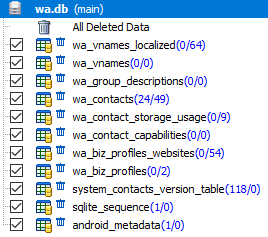
The most interesting tables in the 'wa.db' database for the researcher are:
- 'wa_contacts'
This table contains contact information: whatsApp contact id, status information, display name, time stamp, etc.
Appearance of the table: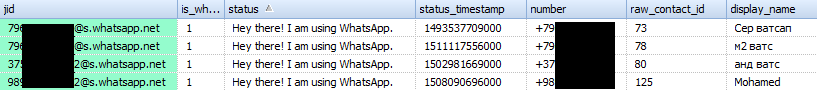 Table structure
Table structureField name Value _id record sequence number (in SQL table) jid WhatsApp contact ID, recorded in the format <phone number> @ s.whatsapp.net is_whatsapp_user contains '1' if the contact matches the actual WhatsApp user, '0' otherwise status contains the text displayed in the contact status status_timestamp contains a timestamp in Unix Epoch Time (ms) format number phone number associated with the contact raw_contact_id contact sequence number display_name contact display name phone_type phone type phone_label label associated with the contact number unseen_msg_count the number of messages that were sent by the contact but were not read by the recipient photo_ts contains a timestamp in Unix Epoch Time format thumb_ts contains a timestamp in Unix Epoch Time format photo_id_timestamp contains a timestamp in Unix Epoch Time (ms) format given_name field value is the same as 'display_name' for each contact wa_name WhatsApp's contact name (the name specified in the contact's profile is displayed) sort_name contact name used in sorting operations nickname nickname of the contact in WhatsApp (the nickname shown in the contact profile is displayed) company company (the company listed in the contact profile is displayed) title Appeal (Madam / Sir; Appeal configured in contact profile is displayed) offset bias - 'sqlite_sequence'
This table contains information on the number of contacts; - 'android_metadata'
This table contains information about the language localization of WhatsApp.
The database 'msgstore.db' contains information about sent messages, such as contact number, message text, message status, timestamps, information about sent files included in messages, etc. The file 'msgstore.db' is located along the path: '/data/data/com.whatsapp/databases/' and has the following structure:
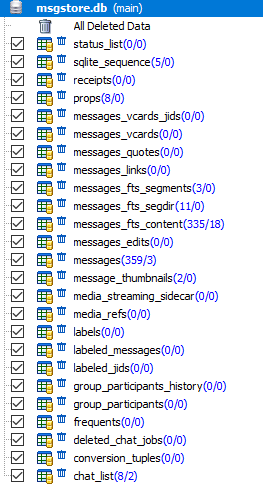
The most interesting tables in the 'msgstore.db' file for the researcher are:
- 'sqlite_sequence'
This table contains general information about this database, for example, the total number of stored messages, the total number of chats, etc.
Appearance of the table:
- 'message_fts_content'
Contains the text of the transmitted messages.
Appearance of the table: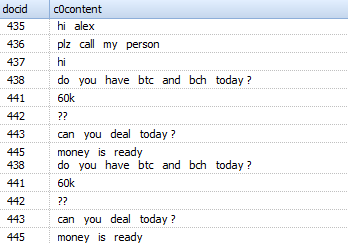
- 'messages'
This table contains information such as contact number, message text, message status, timestamps, information about transferred files included in messages.
Appearance of the table: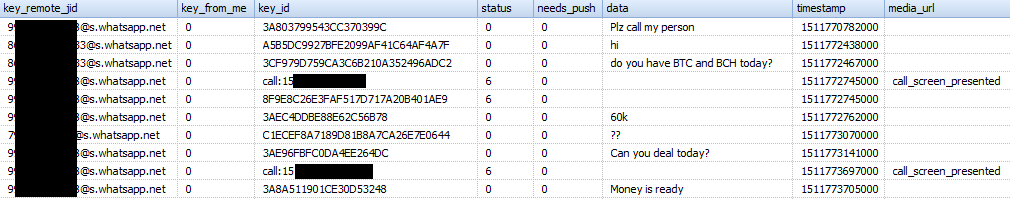 Table structure
Table structureField name Value _id record sequence number (in SQL table) key_remote_jid WhatsApp ID of the communication partner key_from_me message direction: '0' is incoming, '1' is outgoing key_id unique message identifier status message status: '0' - delivered, '4' - waiting on the server, '5' - received at destination, '6' - control message, '13' - message opened by the recipient (read) need_push is set to '2' if this is a broadcast message, otherwise it contains '0' data Message text (when the 'media_wa_type' parameter is '0') timestamp contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock media_url contains the URL of the file being transferred (when the 'media_wa_type' parameter is '1', '2', '3') media_mime_type The MIME type of the file being transferred (when the 'media_wa_type' parameter is '1', '2', '3') media_wa_type message type: '0' is text, '1' is a graphic file, '2' is an audio file, '3' is a video file, '4' is a contact card, '5' is geodata media_size file transfer size (when the 'media_wa_type' parameter is '1', '2', '3') media_name the name of the file being transferred (when the 'media_wa_type' parameter is '1', '2', '3') media_caption Contains the words 'audio', 'video' for the corresponding values of the 'media_wa_type' parameter (when the 'media_wa_type' parameter is '1', '3') media_hash base64-encoded hash of the transmitted file, calculated using the HAS-256 algorithm (when the 'media_wa_type' parameter is '1', '2', '3') media_duration duration in seconds for a media file (when the 'media_wa_type' parameter is '1', '2', '3') origin is set to '2' if this is a broadcast message, otherwise it contains '0' latitude geodata: latitude (when the 'media_wa_type' parameter is '5') longitude geodata: longitude (when the 'media_wa_type' parameter is '5') thumb_image service information remote_recource Sender ID (for group chats only) received_timestamp retrieval time, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock (when the 'key_from_me' parameter has '0', '-1' or another value) send_timestamp not used, usually '-1' receipt_server_timestamp time received by the central server, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock (when the 'key_from_me' parameter has '1', '-1' or another value receipt_device_timestamp the time the message was received by another subscriber, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock (when the 'key_from_me' parameter has '1', '-1' or another value read_device_timestamp time of opening (reading) a message, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock played_device_timestamp message playback time, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock raw_data file thumbnail (when the 'media_wa_type' parameter is '1' or '3') recipient_count number of recipients (for broadcast messages) participant_hash used when sending messages with geodata starred not used quoted_row_id unknown, usually contains the value '0' mentioned_jids not used multicast_id not used offset bias
This list of fields is not exhaustive. For different versions of WhatsApp, some fields may be present or absent. Additionally, there may be 'media_enc_hash' , 'edit_version' , 'payment_transaction_id' , etc. fields . - 'messages_thumbnails'
This table contains information about transferred images and timestamps. In the 'timestamp' column, the time is in Unix Epoch Time (ms) format. - 'chat_list'
This table contains information about chats.
Appearance of the table:
Also, when examining WhatsApp in a mobile device running Android, pay attention to the following files:
- The file 'msgstore.db.cryptXX' (where XX is one or two digits from 0 to 12, for example, msgstore.db.crypt12). Contains an encrypted backup of WhatsApp messages (a backup of the msgstore.db file). The file (or files) 'msgstore.db.cryptXX' is located along the following path: '/ data / media / 0 / WhatsApp / Databases /' (virtual SD card), '/ mnt / sdcard / WhatsApp / Databases / (physical SD map)'.
- File 'key' . Contains a cryptographic key. Located on the path: '/data/data/com.whatsapp/files/' . Used to decrypt encrypted WhatsApp backups.
- The file 'com.whatsapp_preferences.xml' . Contains information about the account profile WhatsApp. The file is located along the path: '/data/data/com.whatsapp/shared_prefs/' .File fragment
<?xml version="1.0" encoding="ISO-8859-1"?> … <string name="ph">9123456789</string> ( , WhatsApp) … <string name="version">2.17.395</string> ( WhatsApp) … <string name="my_current_status">Hey there! I am using WhatsApp.</string> (, ) … <string name="push_name">Alex</string> ( ) … - File 'registration.RegisterPhone.xml' . Contains information about the phone number associated with the WhatsApp account. The file is located along the path: '/data/data/com.whatsapp/shared_prefs/' .File contents
<?xml version="1.0" encoding="ISO-8859-1"?> <map> <string name="com.whatsapp.registration.RegisterPhone.phone_number">9123456789</string> <int name="com.whatsapp.registration.RegisterPhone.verification_state" value="0"/> <int name="com.whatsapp.registration.RegisterPhone.country_code_position" value="-1"/> <string name="com.whatsapp.registration.RegisterPhone.input_phone_number">912 345-67-89</string> <int name="com.whatsapp.registration.RegisterPhone.phone_number_position" value="10"/> <string name="com.whatsapp.registration.RegisterPhone.input_country_code">7</string> <string name="com.whatsapp.registration.RegisterPhone.country_code">7</string> </map> - The file 'axolotl.db' . Contains cryptographic keys and other data that is necessary to identify the owner of the account. Located along the path: '/data/data/com.whatsapp/databases/' .
- The file 'chatsettings.db' . Contains application configuration information.
- The file 'wa.db' . Contains contact details. Very interesting (in the forensic aspect) and informative database. It can be found detailed information about deleted contacts.
You also need to pay attention to the following directories:
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Images /' . Contains transferred graphic files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Voice Notes /' . Contains voice messages in .OPUS files.
- The '/data/data/com.whatsapp/cache/Profile Pictures /' directory. Contains graphic files - images of contacts.
- The '/data/data/com.whatsapp/files/Avatars/' directory . Contains graphic files - thumbnail images of contacts. These files have the extension '.j', but, nevertheless, are JPEG image files (JPG).
- The '/data/data/com.whatsapp/files/Avatars/' directory . It contains graphic files - an image and a thumbnail of an image set as an avatar by the account owner.
- Directory '/data/data/com.whatsapp/files/Logs/' . Contains the program operation log (the file 'whatsapp.log') and backup copies of the program operation logs (files with the names of the format whatsapp-yyyy-mm-dd.1.log.gz).
WhatsApp log files:
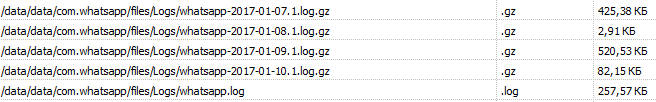
Fragment of the magazine
2017-01-10 09: 37: 09.757 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / init count: 0 timestamp: 0
2017-01-10 09: 37: 09.758 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / update cancel true
2017-01-10 09: 37: 09.768 LL_I D [1: main] app-init / load-me
2017-01-10 09: 37: 09.772 LL_I D [1: main] password file missing or unreadable
2017-01-10 09: 37: 09.782 LL_I D [1: main] statistics Text Messages: 59 sent, 82 received / Media Messages: 1 sent (0 bytes), 0 received (9850158 bytes) / Offline Messages: 81 received ( 19522 msec average delay) / Message Service: 116075 bytes sent, 211729 bytes received / Voip Calls: 1 outgoing calls, 0 incoming calls, 2492 bytes sent, 1530 bytes received / Google Drive: 0 bytes sent, 0 bytes received / Roaming: 1524 bytes sent, 1826 bytes received / Total Data: 118567 bytes sent, 10063417 bytes received
2017-01-10 09: 37: 09.785 LL_I D [1: main] media-state-manager / refresh-media-state / writable-media
2017-01-10 09: 37: 09.806 LL_I D [1: main] app-init / initialize / timer / stop: 24
2017-01-10 09: 37: 09.811 LL_I D [1: main] msgstore / checkhealth
2017-01-10 09: 37: 09.817 LL_I D [1: main] msgstore / checkhealth / journal / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkdb / data / data / com.whatsapp / databases / msgstore.db
2017-01-10 09: 37: 09.819 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager 16384 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager-journal 21032 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list axolotl.db 184320 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-wal 436752 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.822 LL_I D [1: main] msgstore / checkdb / list msgstore.db 540672 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-wal 0 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.824 LL_I D [1: main] msgstore / checkdb / list wa.db 69632 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-wal 428512 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db 4096 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-wal 70072 drw = 011
2017-01-10 09: 37: 09.827 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.838 LL_I D [1: main] msgstore / checkdb / version 1
2017-01-10 09: 37: 09.839 LL_I D [1: main] msgstore / canquery
2017-01-10 09: 37: 09.846 LL_I D [1: main] msgstore / canquery / count 1
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery / timer / stop: 8
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery 517 | time spent: 8
2017-01-10 09: 37: 09.848 LL_I D [529: WhatsApp Worker # 3] media-state-manager / refresh-media-state / internal-storage available: 1,345,622,016 total: 5,687,922,688
2017-01-10 09: 37: 09.758 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / update cancel true
2017-01-10 09: 37: 09.768 LL_I D [1: main] app-init / load-me
2017-01-10 09: 37: 09.772 LL_I D [1: main] password file missing or unreadable
2017-01-10 09: 37: 09.782 LL_I D [1: main] statistics Text Messages: 59 sent, 82 received / Media Messages: 1 sent (0 bytes), 0 received (9850158 bytes) / Offline Messages: 81 received ( 19522 msec average delay) / Message Service: 116075 bytes sent, 211729 bytes received / Voip Calls: 1 outgoing calls, 0 incoming calls, 2492 bytes sent, 1530 bytes received / Google Drive: 0 bytes sent, 0 bytes received / Roaming: 1524 bytes sent, 1826 bytes received / Total Data: 118567 bytes sent, 10063417 bytes received
2017-01-10 09: 37: 09.785 LL_I D [1: main] media-state-manager / refresh-media-state / writable-media
2017-01-10 09: 37: 09.806 LL_I D [1: main] app-init / initialize / timer / stop: 24
2017-01-10 09: 37: 09.811 LL_I D [1: main] msgstore / checkhealth
2017-01-10 09: 37: 09.817 LL_I D [1: main] msgstore / checkhealth / journal / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkdb / data / data / com.whatsapp / databases / msgstore.db
2017-01-10 09: 37: 09.819 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager 16384 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager-journal 21032 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list axolotl.db 184320 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-wal 436752 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.822 LL_I D [1: main] msgstore / checkdb / list msgstore.db 540672 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-wal 0 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.824 LL_I D [1: main] msgstore / checkdb / list wa.db 69632 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-wal 428512 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db 4096 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-wal 70072 drw = 011
2017-01-10 09: 37: 09.827 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.838 LL_I D [1: main] msgstore / checkdb / version 1
2017-01-10 09: 37: 09.839 LL_I D [1: main] msgstore / canquery
2017-01-10 09: 37: 09.846 LL_I D [1: main] msgstore / canquery / count 1
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery / timer / stop: 8
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery 517 | time spent: 8
2017-01-10 09: 37: 09.848 LL_I D [529: WhatsApp Worker # 3] media-state-manager / refresh-media-state / internal-storage available: 1,345,622,016 total: 5,687,922,688
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Audio /' . Contains the received audio files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Audio / Sent /' . Contains sent audio files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Images /' . Contains the resulting graphic files.
- Catalog '/ data / media / 0 / WhatsApp / Media / WhatsApp Images / Sent /' . Contains the sent graphic files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Video /' . Contains the received video files.
- The '/ data / media / 0 / WhatsApp / Media / WhatsApp Video / Sent /' directory. Contains the sent video files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Profile Photos /' . Contains graphic files associated with the owner of the WhatsApp account.
- To save space in the memory of Android-smartphone part of the data WhatsApp can be stored on the SD card. On the SD card, in the root directory, is the 'WhatsApp' directory, where the following artifacts of this program can be found:

- Catalog '.Share' ( '/mnt/sdcard/WhatsApp/.Share/' ). Contains copies of files that were transferred to other WhatsApp users.
- The '.trash' directory ( '/mnt/sdcard/WhatsApp/.trash/' ). Contains deleted files.
- The 'Databases' directory ( '/ mnt / sdcard / WhatsApp / Databases /' ). Contains encrypted backups. They can be decrypted if there is a 'key' file extracted from the memory of the device being analyzed.
Files in the 'Databases' subdirectory: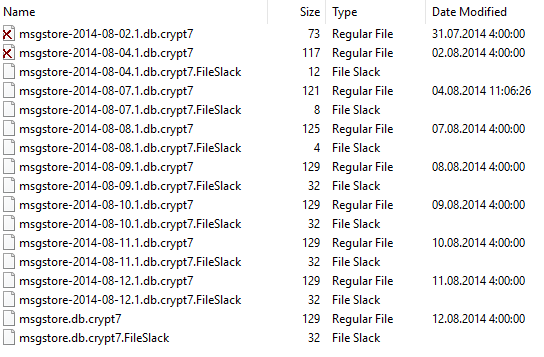
- The 'Media' directory ( '/ mnt / sdcard / WhatsApp / Media /' ). Contains the 'WallPaper' , 'WhatsApp Audio' , 'WhatsApp Images' , 'WhatsApp Profile Photos' , 'WhatsApp Video' , 'WhatsApp Voice Notes' subdirectories, which contain received and transmitted multimedia files (graphic files, video files, voice messages, Photos associated with the profile of the owner of the account WhatsApp, wallpaper).
- Directory 'Profile Pictures' ( '/ mnt / sdcard / WhatsApp / Profile Pictures /' ). Contains graphic files associated with the owner’s WhatsApp account profile.
- Sometimes the 'files' directory ( '/ mnt / sdcard / WhatsApp / Files /' ) may appear on the SD card. This directory contains files that store program settings and user preferences.
Features of data storage in some models of mobile devices
In some models of mobile devices running Android, it is possible to store WhatsApp artifacts in another place. This is due to changes in the storage space of application data by the system software of the mobile device. For example, in Xiaomi mobile devices there is a function to create a second workspace (“SecondSpace”). When this function is activated, the location of the data changes. So, if in a conventional mobile device running the Android OS, user data is stored in the directory '/ data / user / 0 /' (which is a link to the usual '/ data / data /' ), then in the second workspace, application data is stored in the directory '/ data / user / 10 /' . That is, on the example of the location of the file 'wa.db' :
- in the usual Android smartphone: /data/user/0/com.whatsapp/databases/wa.db ' (which is equivalent to ' /data/data/com.whatsapp/databases/wa.db ') ;
- in the second workspace of the smartphone Xiaomi: '/data/user/10/com.whatsapp/databases/wa.db' .
WhatsApp artifacts in the iOS device
Unlike Android OS, in iOS, the data of the WhatsApp application is transferred to a backup copy (iTunes backup). Therefore, the extraction of data from this application does not require the extraction of the file system or the creation of a physical memory dump of the device under investigation. Most of the relevant information is contained in the database 'ChatStorage.sqlite' , which is located along the path: '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/' (in some programs this path is displayed as ' AppDomainGroup -group.net.whatsapp.WhatsApp.shared ' ).
Structure 'ChatStorage.sqlite' :
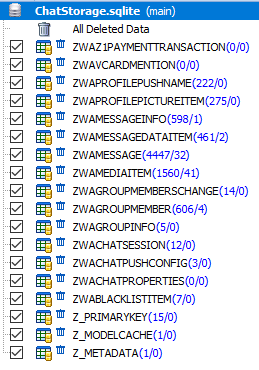
The most informative in the database 'ChatStorage.sqlite' are the tables 'ZWAMESSAGE' and 'ZWAMEDIAITEM' .
Appearance of the table 'ZWAMESSAGE' :
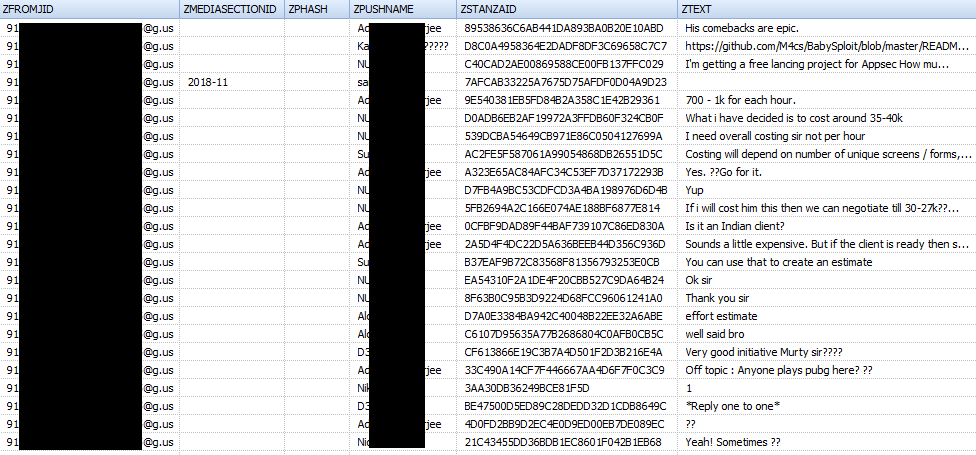
Table structure 'ZWAMESSAGE'
| Field name | Value |
|---|---|
| Z_PK | record sequence number (in SQL table) |
| Z_ENT | table identifier is '9' |
| Z_OPT | unknown, usually contains values from '1' to '6' |
| ZCHILDMESSAGESDELIVEREDCOUNT | unknown, usually contains the value '0' |
| ZCHILDMESSAGESPLAYEDCOUNT | unknown, usually contains the value '0' |
| ZCHILDMESSAGESREADCOUNT | unknown, usually contains the value '0' |
| ZDATAITEMVERSION | unknown, usually contains the value '3' is probably a text message pointer |
| ZDOCID | unknown |
| ZENCRETRYCOUNT | unknown, usually contains the value '0' |
| ZFILTEREDRECIPIENTCOUNT | unknown, usually contains the values '0', '2', '256' |
| ZISFROMME | message direction: '0' is incoming, '1' is outgoing |
| ZMESSAGEERRORSTATUS | message transfer status If the message is sent / received, it is '0' |
| ZMESSAGETYPE | message type |
| ZSORT | unknown |
| ZSPOTLIGHSTATUS | unknown |
| ZSTARRED | unknown, not used |
| ZCHATSESSION | unknown |
| ZGROUPMEMBER | unknown, not used |
| ZLASTSESSION | unknown |
| ZMEDIAITEM | unknown |
| ZMESSAGEINFO | unknown |
| ZPARENTMESSAGE | unknown, not used |
| ZMESSAGEDATE | OS X Epoch Time Timestamp |
| ZSENTDATE | message sending time in OS X Epoch Time format |
| ZFROMJID | WhatsApp sender ID |
| ZMEDIASECTIONID | contains the year and month of the media file sending |
| ZPHASH | unknown, not used |
| ZPUSHPAME | the name of the contact who sent the media file in UTF-8 format |
| ZSTANZID | unique message identifier |
| ZTEXT | Message text |
| ZTOJID | Whatsapp recipient id |
| OFFSET | bias |
Appearance of the table 'ZWAMEDIAITEM' :
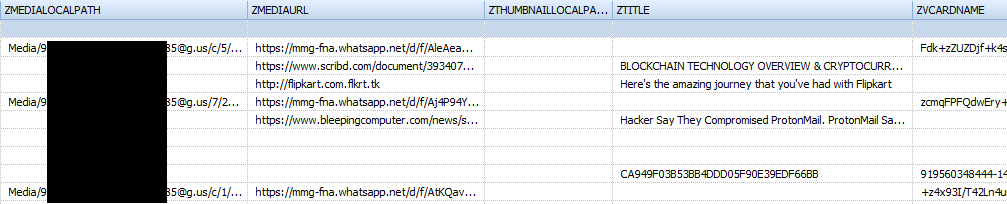
Table structure 'ZWAMEDIAITEM'
| Field name | Value |
|---|---|
| Z_PK | record sequence number (in SQL table) |
| Z_ENT | table identifier is '8' |
| Z_OPT | unknown, usually contains values from '1' to '3'. |
| ZCLOUDSTATUS | contains the value '4' if the file is loaded. |
| ZFILESIZE | contains the length of the file (in bytes) for the downloaded files |
| ZMEDIAORIGIN | unknown, usually '0' |
| ZMOVIEDURATION | media file length, for pdf files may contain the number of document pages |
| ZMESSAGE | contains a sequence number (the number is different from the one specified in the 'Z_PK' column) |
| ZASPECTRATIO | aspect ratio, not used, usually has the value '0' |
| ZHACCURACY | unknown, usually '0' |
| ZLATTITUDE | pixel width |
| ZLONGTITUDE | pixel height |
| ZMEDIAURLDATE | timestamp in OS X Epoch Time format |
| ZAUTHORNAME | author (for documents, may contain file name) |
| ZCOLLECTIONNAME | not used |
| ZMEDIALOCALPATH | file name (with path) in the device file system |
| ZMEDIAURL | The URL where the media file was located. If the file was transferred from one subscriber to another, it was encrypted and its extension will be indicated as the extension of the file being transferred - .enc |
| ZTHUMBNAILLOCALPATH | Path to file thumbnail in device file system |
| ZTITLE | file header |
| ZVCARDNAME | media file hash, when transferring a file to a group, may contain the sender's identifier |
| ZVCARDSTRING | contains information about the type of the file being transferred (for example, image / jpeg); when transferring a file to a group it may contain the recipient's identifier |
| ZXMPPTHUMBPATH | Path to file thumbnail in device file system |
| ZMEDIAKEY | unknown, probably contains a key to decrypt the encrypted file. |
| ZMETADATA | message metadata |
| Offset | bias |
Other interesting database tables for 'ChatStorage.sqlite' are:
- 'ZWAPROFILEPUSHNAME' . Associates the WhatsApp ID with the contact name;
- 'ZWAPROFILEPICTUREITEM' . Associates WhatsApp ID with contact avatar;
- 'Z_PRIMARYKEY' . The table contains general information about this database, such as the total number of stored messages, the total number of chats, etc.
Also, when examining WhatsApp in a mobile device running iOS, pay attention to the following files:
- File 'BackedUpKeyValue.sqlite' . Contains cryptographic keys and other data that is necessary to identify the owner of the account. Located along the path: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ .
- File 'ContactsV2.sqlite' . Contains information about the user's contacts, such as name, phone number, contact status (as text), WhatsApp ID, etc. Located along the path: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ .
- File 'consumer_version' . Contains the version number of the installed WhatsApp application. Located along the path: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ .
- The file 'current_wallpaper.jpg' . Contains the current wallpaper of the WhatsApp program. Located along the path: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ . Older versions of the application use the file 'wallpaper' , which is located along the path: '/private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/' .
- File 'blockedcontacts.dat' . Contains information about blocked contacts. Located along the path: /private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/ .
- File 'pw.dat' . Contains an encrypted password. Located along the path: '/private/var/mobile/Applications/net.whatsapp.WhatsApp/Library/' .
- The file 'net.whatsapp.WhatsApp.plist' (or the file 'group.net.whatsapp.WhatsApp.shared.plist' ). Contains information about the account profile WhatsApp. The file is located along the path: '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/Library/Preferences/' .
Content of the file 'group.net.whatsapp.WhatsApp.shared.plist'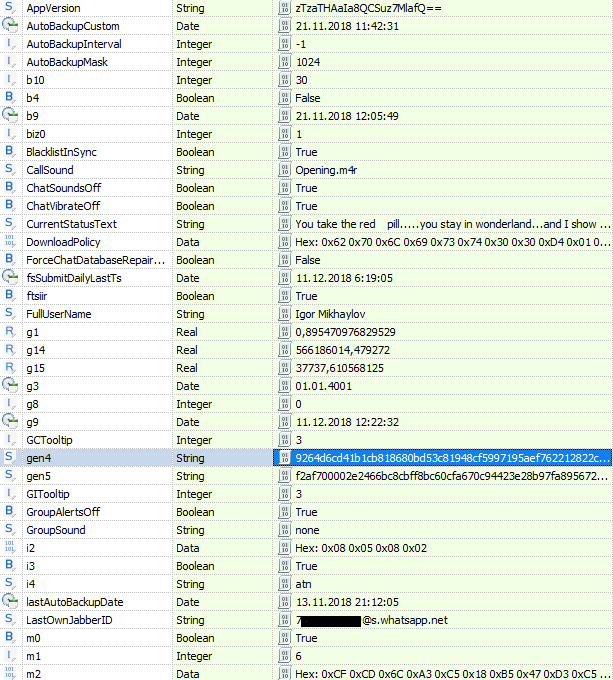

You also need to pay attention to the following directories:
- The '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/Media/Profile/' directory. Contains thumbnails of contacts, groups (files with the extension .thumb ), avatars of contacts, avatar of the owner of the WhatsApp account (file 'Photo.jpg' ).
- The '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ Message / Media /' directory. Contains multimedia files and their thumbnails
- The '/private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/' directory. It contains the program operation log (the 'calls.log' file) and backup copies of the program operation logs (the 'calls.backup.log' file).
- The '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/stickers/' directory. Contains stickers (files in '.webp' format).
- Directory '/private/var/mobile/Applications/net.whatsapp.WhatsApp/Library/Logs/' . Contains logs of the program.
WhatsApp artifacts in Windows
- 'C: \ Program Files (x86) \ WhatsApp \'
- 'C: \ Users \% User profile% \ AppData \ Local \ WhatsApp \'
- 'C: \ Users \% User profile% \ AppData \ Local \ VirtualStore \ Program Files (x86) \ WhatsApp \'
In the 'C: \ Users \% User profile% \ AppData \ Local \ WhatsApp \' directory is located the log file 'SquirrelSetup.log' , which contains information on checking for updates and installing the program.
In the 'C: \ Users \% User profile% \ AppData \ Roaming \ WhatsApp \' directory there are several subdirectories:
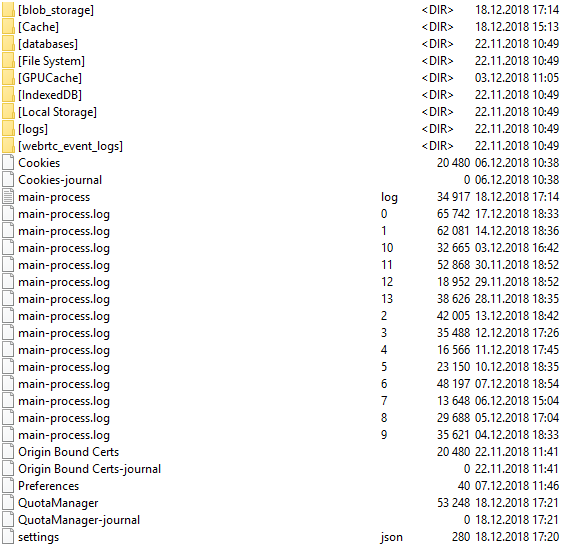
The file 'main-process.log' contains information about the operation of the WhatsApp program.
The 'databases' subdirectory contains the 'Databases.db' file, but this file does not contain any information about chats or contacts.
The most interesting from a forensic point of view are the files in the 'Cache' directory. These are mainly files with the name 'f _ *******' (where * is a number from 0 to 9) containing encrypted multimedia files and documents, but among them there are also unencrypted files. Of particular interest are the 'data_0' , 'data_1' , 'data_2' , 'data_3' files located in the same subdirectory. The 'data_0' , 'data_1' , 'data_3' files contain external links to the transmitted encrypted multimedia files and documents.
An example of the information contained in the 'data_1' file

Also, the 'data_3' file may contain graphic files.
The 'data_2' file contains contact avatars (can be restored by searching for file headers).
Avatars contained in the 'data_2' file:

Thus, it is impossible to find chat rooms in the computer’s memory, but you can find:
- multimedia files;
- documents transmitted via WhatsApp;
- Account Owner Contact Information
WhatsApp artifacts in MacOS
In MacOS, you can find types of artifacts of WhatsApp, similar to those found in Windows.
Program files are directories:
- 'C: \ Applications \ WhatsApp.app \'
- 'C: \ Applications \ ._ WhatsApp.app \'
- 'C: \ Users \% User profile% \ Library \ Preferences \'
- 'C: \ Users \% User profile% \ Library \ Logs \ WhatsApp \'
- 'C: \ Users \% User profile% \ Library \ Saved Application State \ WhatsApp.savedState \'
- 'C: \ Users \% User profile% \ Library \ Application Scripts \'
- 'C: \ Users \% User profile% \ Library \ Application Support \ CloudDocs \'
- 'C: \ Users \% User profile% \ Library \ Application Support \ WhatsApp.ShipIt \'
- 'C: \ Users \% User profile% \ Library \ Containers \ com.rockysandstudio.app-for-whatsapp \'
- 'C: \ Users \% User profile% \ Library \ Mobile Documents \ <text variable> WhatsApp \ Accounts'
This directory contains subdirectories whose names are the phone numbers associated with the owner of the WhatsApp account. - 'C: \ Users \% User profile% \ Library \ Caches \ WhatsApp.ShipIt \'
This directory contains information about the installation program. - 'C: \ Users \% User profile% \ Pictures \ Media Library iPhoto.photolibrary \ Masters \' , 'C: \ Users \% User profile% \ Pictures \ Media Library iPhoto.photolibrary \ Thumbnails \'
These directories contain utility files for the program, including photos and thumbnails of WhatsApp contacts. - 'C: \ Users \% User profile% \ Library \ Caches \ WhatsApp \'
This directory contains several SQLite databases that are used to cache data. - 'C: \ Users \% User profile% \ Library \ Application Support \ WhatsApp \'
This directory contains several subdirectories: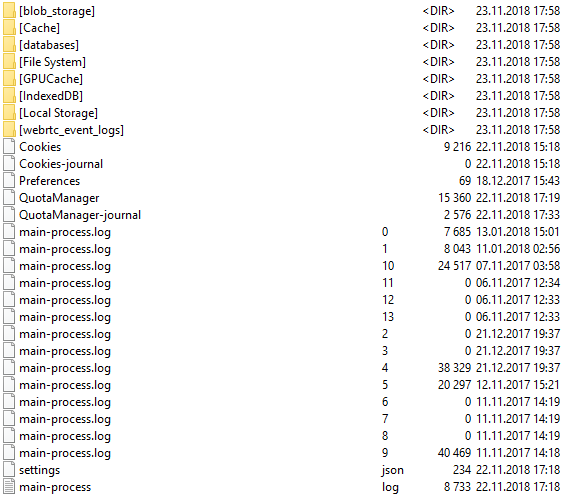
The 'C: \ Users \% User profile% \ Library \ Application Support \ WhatsApp \ Cache \ ' directory contains the files ' data_0 ' , ' data_1 ' , ' data_2 ' , ' data_3 ' and files with the names ' f _ **** *** ' (where * is a number from 0 to 9). Information about what information these files contain is described in the "WhatsApp artifacts in Windows" section.
The directory 'C: \ Users \% User profile% \ Library \ Application Support \ WhatsApp \ IndexedDB \' may contain multimedia files (files do not have extensions).
The file 'main-process.log' contains information about the operation of the WhatsApp program.
Sources
- Forensic analysis of WhatsApp Messenger on Android smartphones, by Cosimo Anglano, 2014.
- Whatsapp Forensics: Eksplorasi sistem berkas dan basis data pada aplikasi Android dan iOS by Ahmad Pratama, 2014.
In the following articles in this series:
Decryption of encrypted WhatsApp databases
An article that will provide information on how the WhatsApp encryption key is generated and gives practical examples showing how to decrypt the encrypted databases of this application.
Extract WhatsApp data from cloud storage
An article in which we will tell you what kind of WhatsApp data is stored in the clouds, and we will describe methods for extracting this data from cloud storage.
Extracting WhatsApp data: practical examples
An article that will be step by step described by what programs and how to extract WhatsApp data from various devices.
Source: https://habr.com/ru/post/447592/
All Articles