Threat Hunting, or How to defend against 5% of threats
95% of information security threats are known, and you can defend against them with traditional means such as antivirus, firewall, IDS, WAF. The remaining 5% of the threats are unknown and the most dangerous. They constitute 70% of the risk for the company due to the fact that it is very difficult to detect them and even more so to protect against them. Examples of “black swans” are the epidemics of the WannaCry cryptographers, NotPetya / ExPetr, crypto miners, Stuxnet’s “cyber weapon” (which hit Iran’s nuclear facilities) and many (does anyone remember Kido / Conficker?) Of other attacks that are not very good at defending classical defense means of protection. We want to talk about how to counter these 5% of threats with the help of the Threat Hunting technology.

The continuous development of cyber-attacks requires constant detection and counteraction, which ultimately leads us to the idea of an endless arms race between attackers and defenders. Classic protection systems are no longer able to provide an acceptable level of protection, in which the level of risk does not affect the company's key indicators (economic, political, reputation) without refining them for a specific infrastructure, but in general they cover some of the risks. Already in the process of implementation and configuration, modern security systems find themselves in the role of a catch-up and must respond to the challenges of the new time.
 A source
A source
')
One answer to the challenges of modernity for an information security specialist can be Threat Hunting technology. The term Threat Hunting (hereinafter referred to as TH) appeared several years ago. The technology itself is quite interesting, but does not yet have any generally accepted standards and rules. Also complicated is the heterogeneity of information sources and the small number of Russian-language information sources on this topic. In this connection, we in “LANIT-Integration” decided to write a certain review of this technology.
TH technology relies on infrastructure monitoring processes. There are two main scenarios for internal monitoring - Alerting and Hunting . Alerting (by type of MSSP services) is a traditional method, searching for signatures and signs of attacks developed earlier and responding to them. This script is successfully implemented by traditional signature protection. Hunting (MDR type service) is a monitoring method that answers the question “Where do signatures and rules come from?”. This is the process of creating correlation rules by analyzing hidden or previously unknown indicators and signs of attack. It is to this type of monitoring that Threat Hunting belongs.

Only by combining both types of monitoring, we get protection that is close to ideal, but there always remains some level of residual risk.
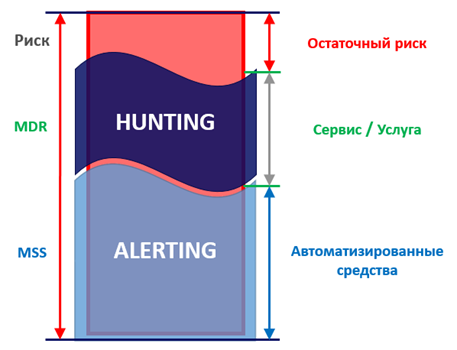 Protection using two types of monitoring
Protection using two types of monitoring
And this is why TH (and all the hunting!) Will be increasingly relevant:
 Threats, remedies, risks. A source
Threats, remedies, risks. A source
95% of all threats are already well understood . These include such types as spam, DDoS, viruses, rootkits and other classic malware. You can protect yourself from these threats with the same classical means of protection.
In the course of any project, 80% of the work takes 20% of the time , and the remaining 20% of the work takes 80% of the time. Similarly, among the entire threat landscape, 5% of the threats of a new type will amount to 70% of the risk to the company. In a company where information security management processes are organized, we can manage 30% of the risk of implementing known threats in one way or another by avoiding (relinquishing wireless networks in principle), accepting (introducing the necessary protections) or shifting (for example, to the integrator) this risk. Defending yourself against zero-day vulnerabilities , APT attacks, phishing, supply chain attacks , cyber espionage and national operations, as well as a large number of other attacks is much more difficult. The consequences of these 5% of threats will be much more serious (the average amount of losses of the bank from the group buhtrap - 143 million ), than the consequences of spam or viruses, which saves antivirus software.
With 5% of the threats have to face almost everything. Recently, we had to install one open-source-solution that uses the application from the repository PEAR (PHP Extension and Application Repository). Attempting to install this application through pear install failed, because the site was unavailable (now the stub is already hanging on it), I had to install it from GitHub. And just recently it turned out that PEAR was the victim of an attack through the supply chain .
You can still remember the attack using CCleaner , the NePetya cipher epidemic through the program update module for managing tax reporting MEDoc . Threats are becoming more sophisticated, and a logical question arises - “How can we still resist these 5% of threats?”
So, Threat Hunting is a process of proactive and iterative search and detection of advanced threats that cannot be detected by traditional means of protection. Advanced threats include, for example, attacks such as APT, 0-day vulnerability attacks, Living off the Land, and so on.
You can also rephrase that TH is a hypothesis testing process. This is mainly a manual process with elements of automation, in which the analyst, relying on his knowledge and qualifications, sifts large amounts of information in search of signs of compromise, corresponding to the initially defined hypothesis of the presence of a certain threat. A distinctive feature of it is the variety of sources of information.
It should be noted that Threat Hunting is not some kind of software or hardware product. These are not alerts that can be seen in a solution. This is not an IOC (compromise identifier) search process. And this is not some kind of passive activity that goes without the participation of information security analysts. Threat Hunting is, above all, a process.

Three main components of Threat Hunting: data, technology, people.
Data (what?) , Including Big Data. Various traffic streams, information about previously conducted APT, analytics, data on user activity, network data, information from employees, information on the darknet and much more.
Technologies (how?) Of processing this data are all possible ways of processing this data, including Machine Learning.
People (who?) Are those who have extensive experience analyzing various attacks, developed intuition and the ability to detect an attack. These are usually information security analysts who must have the ability to generate hypotheses and find confirmation for them. They are the main link in the process.
Adam Bateman describes the PARIS model for the ideal TH process. The name seems to hint at a famous landmark in France. This model can be viewed in two directions - top and bottom.
In the process of hunting for threats, moving along the model from the bottom up, we will deal with a lot of evidence of malicious activity. Each proof has a measure such as confidence — a characteristic that reflects the weight of this proof. There are "iron", direct evidence of malicious activity, by which we can immediately reach the top of the pyramid and create the actual notification of an exactly known infection. And there is circumstantial evidence, the sum of which can also lead us to the top of the pyramid. As always, there is much more indirect evidence than direct evidence, which means that they should be sorted and analyzed, additional research should be carried out and it is desirable to automate it.
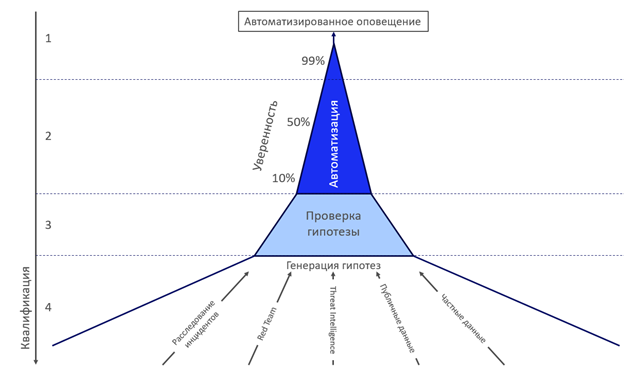 PARIS model. A source
PARIS model. A source
The upper part of the model (1 and 2) is based on automation technologies and various analytics, and the lower part (3 and 4) on people with certain qualifications that control the process. You can consider the model moving from top to bottom, where at the top of blue we have alerts from traditional means of protection (antivirus, EDR, firewall, signatures) with a high degree of confidence and confidence, and lower indicators (IOC, URL, MD5 and others), who have a lower degree of confidence and require additional study. And the lowest and the thickest level (4) is the generation of hypotheses, the creation of new scenarios for the operation of traditional means of protection. This level is not limited to the indicated sources of hypotheses. The lower the level, the greater the requirements for analyst qualifications.
It is very important that analysts do not just check the final set of predetermined hypotheses, but constantly work on generating new hypotheses and options for testing them.
In an ideal world, TH is a continuous process. But since there is no ideal world, let us analyze the model of maturity and methods in the context of people, processes and technologies used. Consider the model of an ideal spherical TH. There are 5 levels of using this technology. Consider them on the example of the evolution of a single team of analysts.
TH maturity levels in terms of people, processes and technology
Level 0: traditional, without the use of TH. Conventional analysts work with a standard set of alerts in the passive monitoring mode using standard tools and technologies: IDS, AV, sandboxes, and signature analysis tools.
Level 1: experimental, using TH. The same analysts with a basic knowledge of forensics and a good knowledge of networks and applications can implement one-time Threat Hunting by searching for indicators of compromise. EDR tools are added to the tools with partial coverage of data from network devices. Tools applied in part.
Level 2: Periodic, Temporary TH. The same analysts who have already pumped their knowledge of forensics, networks and applied parts are charged with the regular practice (sprint) of Threat Hunting, say, a week a month. The tools are added to complete the study of data from network devices, automation of data analysis from EDR and partial use of advanced features of EDR.
Level 3: proactive, frequent cases of TH. Our analysts organized themselves into a dedicated team, they began to have excellent knowledge of forensics and malware, as well as knowledge of the methods and tactics of the attacking side. The process is already carried out 24/7. The team is able to partially test the TH hypothesis, fully utilizing the advanced capabilities of the EDR with full coverage of data from network devices. Also, analysts are able to configure tools to fit their needs.
Level 4: Lead, use TH. The same team has acquired the ability to research, the ability to generate and automate the process of testing hypotheses TH. Now to the tools added tight integration of data sources, software development for the needs and non-standard use of the API.
 Basic Threat Hunting Techniques
Basic Threat Hunting Techniques
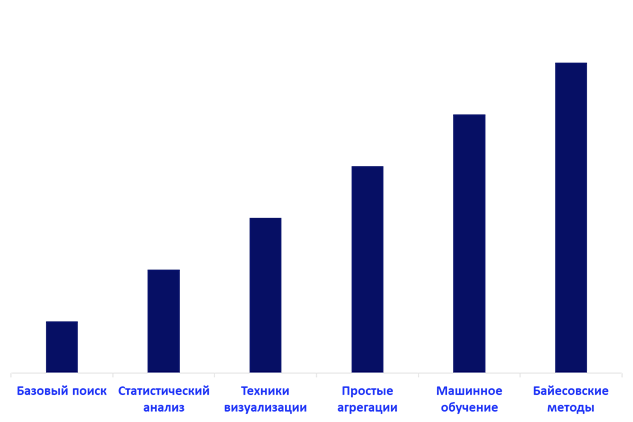
The TH techniques in terms of maturity of the technology used are: basic search, statistical analysis, visualization techniques, simple aggregations, machine learning, and Bayesian methods.
The simplest method is the basic search, which is used to narrow the field of study using certain queries. Statistical analysis is used, for example, to build a typical user or network activity in the form of a statistical model. Visualization techniques are used to visualize and simplify data analysis in the form of graphs and diagrams, which are much easier to catch patterns in the sample. The technique of simple aggregation by key fields is used to optimize search and analysis. The higher the maturity level of the TH process in an organization, the more relevant the use of machine learning algorithms becomes. They are also widely used in spam filtering, malicious traffic detection and fraud detection. A more advanced type of machine learning algorithm is Bayesian methods that allow classification, sample size reduction, and thematic modeling.
Sergio Kaltagiron, Andrew Pendegast and Christopher Betz, in their work The Diamond Model of Intrusion Analysis , showed the main key components of any malicious activity and the basic connection between them.
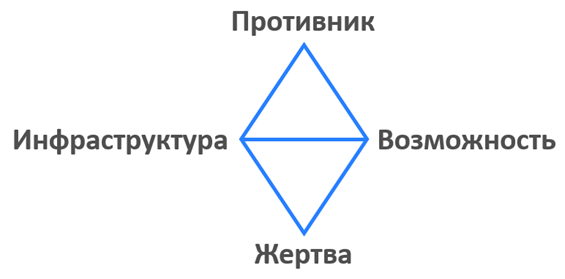 Diamond model for malicious activity
Diamond model for malicious activity
According to this model, there are 4 Threat Hunting strategies that rely on the relevant key components.
1. A strategy focused on the victim. We assume that the victim has opponents, and they will deliver "opportunities" through e-mail. We are looking for enemy data in the mail. Search for links, attachments and etc. We are looking for confirmation of this hypothesis for a certain period (month, two weeks), if not found, then the hypothesis has not played.
2. Infrastructure oriented strategy. There are several methods for using this strategy. Depending on access and visibility, some are lighter than others. For example, we monitor domain name servers that are known to host malicious domains. Or we carry out the process of tracking all new domain name registrations for a known pattern used by the adversary.
3. A strategy focused on opportunities. In addition to the victim-centered strategy used by most of the network defenders, there is an opportunity-oriented strategy. It is the second most popular and focuses on detecting opportunities from the adversary, namely “malware” and the possibility of the adversary using such legitimate tools as psexec, powershell, certutil and others.
4. Strategy focused on the enemy. The enemy-oriented approach focuses on the enemy. These include the use of public information from publicly available sources (OSINT), collection of data about the enemy, his techniques and methods (TTP), analysis of previously occurring incidents, Threat Intelligence data, etc.
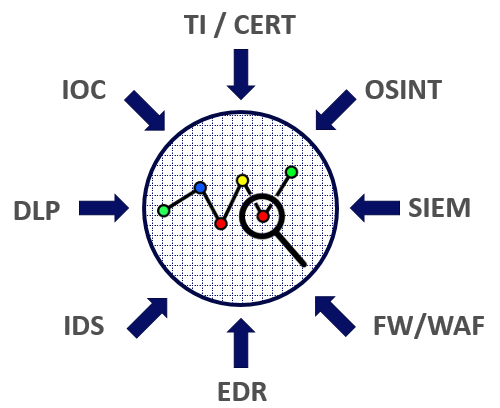 Some sources of information for Threat Hunting
Some sources of information for Threat Hunting
Sources of information can be very much. The ideal analyst should be able to extract information from all that is around. Typical sources in almost any infrastructure will be data from the means of protection: DLP, SIEM, IDS / IPS, WAF / FW, EDR. Also typical sources of information will be various indicators of compromise, Threat Intelligence services, CERT and OSINT data. Additionally, you can use the information from the darknet (for example, suddenly there is an order for breaking the mailbox of the head of the organization, or a candidate for the network engineer has become active), information received from HR (reviews about the candidate from the past job), information from the security service ( for example, the results of the counterparty check).
But before using all available sources, it is necessary to have at least one hypothesis.
 A source
A source
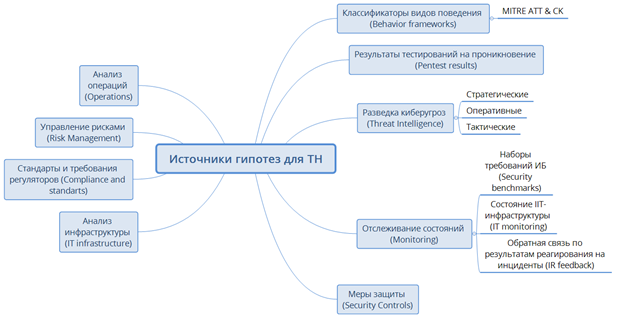
In order to test hypotheses, they must first be put forward. And in order to put forward many qualitative hypotheses, it is necessary to apply a systematic approach. The process of hypothesis generation is described in more detail in the article ; it is very convenient to take this scheme as the basis for the process of hypothesizing.
The main source of hypotheses will be the matrix ATT & CK (Adversarial Tactics, Techniques and Common Knowledge). It is, in essence, a knowledge base and model for assessing the behavior of intruders who implement their activities in the last steps of an attack, usually described with the help of the concept of Kill Chain. That is, at the stages after an intruder penetrates the internal network of the enterprise or the mobile device. Initially, the knowledge base included a description of 121 tactics and techniques used in the attack, each of which is described in detail in the Wiki format. As a source for the generation of hypotheses is well suited various analytics Threat Intelligence. Of particular note are the results of the analysis of infrastructure and penetration tests - these are the most valuable data that can give us iron hypotheses because they rely on a specific infrastructure with its specific flaws.
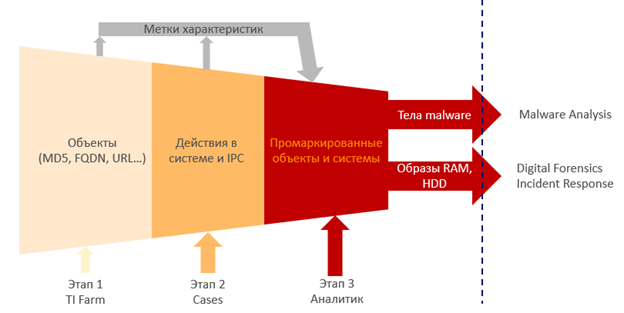
Sergey Soldatov gave a good scheme with a detailed description of the process; it illustrates the process of testing the TH hypotheses in a single system. I will indicate the main stages with a brief description.
 A source
A source
Stage 1: TI Farm
At this stage, it is necessary to select objects (by analyzing them together with all the data about the threats) and assigning them the labels of their characteristics. This is a file, URL, MD5, process, utility, event. Passing them through the systems of Threat Intelligence, you must hang tags. That is, this site was seen at CNC in a certain year, this MD5 was associated with such and such a Malvar, this MD5 swung from the site that distributed the malware.
Stage 2: Cases
At the second stage, we look at the interaction between these objects and identify the relationships between all these objects. We get labeled systems that do something bad.
Stage 3: Analyst
At the third stage, the case is transferred to an experienced analyst, who has a vast experience of analysis, and he makes a verdict. It parses up to bytes what, whence, how, why and why does this code. This body was malicious, this computer was infected. Opens the connection between objects, checks the results of the run through the sandbox.
The results of the analyst are passed on. Digital Forensics examines the images, Malware Analysis examines the found “bodies”, and the Incident Response team can go to the site and explore something already there. The result of the work will be a confirmed hypothesis, the identified attack and ways to counter it.
 A source
A source
Threat Hunting is a fairly young technology that can effectively withstand customized, new and non-standard threats, which has great prospects given the growing number of such threats and the increasing complexity of corporate infrastructure. It requires three components - data, tools and analytics. The benefits of Threat Hunting are not limited to the proactive implementation of threats. Do not forget that in the process of searching we dive into our infrastructure and its weak points through the eyes of a security analyst and we can further strengthen these places.
The first steps that, in our opinion, need to be done to initiate the TH process in your organization.
Ready to discuss the organization of the TH process in the comments.

The continuous development of cyber-attacks requires constant detection and counteraction, which ultimately leads us to the idea of an endless arms race between attackers and defenders. Classic protection systems are no longer able to provide an acceptable level of protection, in which the level of risk does not affect the company's key indicators (economic, political, reputation) without refining them for a specific infrastructure, but in general they cover some of the risks. Already in the process of implementation and configuration, modern security systems find themselves in the role of a catch-up and must respond to the challenges of the new time.

')
One answer to the challenges of modernity for an information security specialist can be Threat Hunting technology. The term Threat Hunting (hereinafter referred to as TH) appeared several years ago. The technology itself is quite interesting, but does not yet have any generally accepted standards and rules. Also complicated is the heterogeneity of information sources and the small number of Russian-language information sources on this topic. In this connection, we in “LANIT-Integration” decided to write a certain review of this technology.
Relevance
TH technology relies on infrastructure monitoring processes. There are two main scenarios for internal monitoring - Alerting and Hunting . Alerting (by type of MSSP services) is a traditional method, searching for signatures and signs of attacks developed earlier and responding to them. This script is successfully implemented by traditional signature protection. Hunting (MDR type service) is a monitoring method that answers the question “Where do signatures and rules come from?”. This is the process of creating correlation rules by analyzing hidden or previously unknown indicators and signs of attack. It is to this type of monitoring that Threat Hunting belongs.

Only by combining both types of monitoring, we get protection that is close to ideal, but there always remains some level of residual risk.

And this is why TH (and all the hunting!) Will be increasingly relevant:

95% of all threats are already well understood . These include such types as spam, DDoS, viruses, rootkits and other classic malware. You can protect yourself from these threats with the same classical means of protection.
In the course of any project, 80% of the work takes 20% of the time , and the remaining 20% of the work takes 80% of the time. Similarly, among the entire threat landscape, 5% of the threats of a new type will amount to 70% of the risk to the company. In a company where information security management processes are organized, we can manage 30% of the risk of implementing known threats in one way or another by avoiding (relinquishing wireless networks in principle), accepting (introducing the necessary protections) or shifting (for example, to the integrator) this risk. Defending yourself against zero-day vulnerabilities , APT attacks, phishing, supply chain attacks , cyber espionage and national operations, as well as a large number of other attacks is much more difficult. The consequences of these 5% of threats will be much more serious (the average amount of losses of the bank from the group buhtrap - 143 million ), than the consequences of spam or viruses, which saves antivirus software.
With 5% of the threats have to face almost everything. Recently, we had to install one open-source-solution that uses the application from the repository PEAR (PHP Extension and Application Repository). Attempting to install this application through pear install failed, because the site was unavailable (now the stub is already hanging on it), I had to install it from GitHub. And just recently it turned out that PEAR was the victim of an attack through the supply chain .

You can still remember the attack using CCleaner , the NePetya cipher epidemic through the program update module for managing tax reporting MEDoc . Threats are becoming more sophisticated, and a logical question arises - “How can we still resist these 5% of threats?”
Threat Hunting Definition
So, Threat Hunting is a process of proactive and iterative search and detection of advanced threats that cannot be detected by traditional means of protection. Advanced threats include, for example, attacks such as APT, 0-day vulnerability attacks, Living off the Land, and so on.
You can also rephrase that TH is a hypothesis testing process. This is mainly a manual process with elements of automation, in which the analyst, relying on his knowledge and qualifications, sifts large amounts of information in search of signs of compromise, corresponding to the initially defined hypothesis of the presence of a certain threat. A distinctive feature of it is the variety of sources of information.
It should be noted that Threat Hunting is not some kind of software or hardware product. These are not alerts that can be seen in a solution. This is not an IOC (compromise identifier) search process. And this is not some kind of passive activity that goes without the participation of information security analysts. Threat Hunting is, above all, a process.
Threat Hunting

Three main components of Threat Hunting: data, technology, people.
Data (what?) , Including Big Data. Various traffic streams, information about previously conducted APT, analytics, data on user activity, network data, information from employees, information on the darknet and much more.
Technologies (how?) Of processing this data are all possible ways of processing this data, including Machine Learning.
People (who?) Are those who have extensive experience analyzing various attacks, developed intuition and the ability to detect an attack. These are usually information security analysts who must have the ability to generate hypotheses and find confirmation for them. They are the main link in the process.
PARIS model
Adam Bateman describes the PARIS model for the ideal TH process. The name seems to hint at a famous landmark in France. This model can be viewed in two directions - top and bottom.
In the process of hunting for threats, moving along the model from the bottom up, we will deal with a lot of evidence of malicious activity. Each proof has a measure such as confidence — a characteristic that reflects the weight of this proof. There are "iron", direct evidence of malicious activity, by which we can immediately reach the top of the pyramid and create the actual notification of an exactly known infection. And there is circumstantial evidence, the sum of which can also lead us to the top of the pyramid. As always, there is much more indirect evidence than direct evidence, which means that they should be sorted and analyzed, additional research should be carried out and it is desirable to automate it.

The upper part of the model (1 and 2) is based on automation technologies and various analytics, and the lower part (3 and 4) on people with certain qualifications that control the process. You can consider the model moving from top to bottom, where at the top of blue we have alerts from traditional means of protection (antivirus, EDR, firewall, signatures) with a high degree of confidence and confidence, and lower indicators (IOC, URL, MD5 and others), who have a lower degree of confidence and require additional study. And the lowest and the thickest level (4) is the generation of hypotheses, the creation of new scenarios for the operation of traditional means of protection. This level is not limited to the indicated sources of hypotheses. The lower the level, the greater the requirements for analyst qualifications.
It is very important that analysts do not just check the final set of predetermined hypotheses, but constantly work on generating new hypotheses and options for testing them.
TH use maturity model
In an ideal world, TH is a continuous process. But since there is no ideal world, let us analyze the model of maturity and methods in the context of people, processes and technologies used. Consider the model of an ideal spherical TH. There are 5 levels of using this technology. Consider them on the example of the evolution of a single team of analysts.
| Maturity levels | People | Processes | Technology |
| Level 0 | SOC Analysts | 24/7 | Traditional instruments: |
| Traditional | Alerts set | Passive monitoring | IDS, AV, Sandboxing, |
| Without th | Work with alerts | signature analysis tools, Threat Intelligence data. | |
| Level 1 | SOC Analysts | One-time TH | Edr |
| Experimental | Basic knowledge of forensic | IOC Search | Partial coverage of data from network devices |
| TH experiments | Good knowledge of networks and application | Partial application | |
| Level 2 | Temporary occupation | Sprints | Edr |
| Periodic | Average knowledge of forensic | Week per month | Full application |
| Temporary TH | Excellent knowledge of networks and applications | Regular th | Full automation of the use of EDR data |
| Partial use of advanced EDR features | |||
| Level 3 | Dedicated TH Team | 24/7 | Partial ability to test TH hypotheses |
| Preventive | Excellent knowledge of forensics and malware | Proactive th | Full use of advanced EDR features |
| TH special cases | Excellent knowledge of the attacking side | TH special cases | Full coverage of data from network devices |
| Configuration under the needs | |||
| Level 4 | Dedicated TH Team | 24/7 | Full ability to test TH hypotheses |
| Leading | Excellent knowledge of forensics and malware | Proactive th | Level 3, plus: |
| TH use | Excellent knowledge of the attacking side | Verification, automation and verification of the hypotheses TH | tight integration of data sources; |
| Ability to research | development for the needs and non-standard use of the API. |
Level 0: traditional, without the use of TH. Conventional analysts work with a standard set of alerts in the passive monitoring mode using standard tools and technologies: IDS, AV, sandboxes, and signature analysis tools.
Level 1: experimental, using TH. The same analysts with a basic knowledge of forensics and a good knowledge of networks and applications can implement one-time Threat Hunting by searching for indicators of compromise. EDR tools are added to the tools with partial coverage of data from network devices. Tools applied in part.
Level 2: Periodic, Temporary TH. The same analysts who have already pumped their knowledge of forensics, networks and applied parts are charged with the regular practice (sprint) of Threat Hunting, say, a week a month. The tools are added to complete the study of data from network devices, automation of data analysis from EDR and partial use of advanced features of EDR.
Level 3: proactive, frequent cases of TH. Our analysts organized themselves into a dedicated team, they began to have excellent knowledge of forensics and malware, as well as knowledge of the methods and tactics of the attacking side. The process is already carried out 24/7. The team is able to partially test the TH hypothesis, fully utilizing the advanced capabilities of the EDR with full coverage of data from network devices. Also, analysts are able to configure tools to fit their needs.
Level 4: Lead, use TH. The same team has acquired the ability to research, the ability to generate and automate the process of testing hypotheses TH. Now to the tools added tight integration of data sources, software development for the needs and non-standard use of the API.
Threat Hunting Techniques

The TH techniques in terms of maturity of the technology used are: basic search, statistical analysis, visualization techniques, simple aggregations, machine learning, and Bayesian methods.
The simplest method is the basic search, which is used to narrow the field of study using certain queries. Statistical analysis is used, for example, to build a typical user or network activity in the form of a statistical model. Visualization techniques are used to visualize and simplify data analysis in the form of graphs and diagrams, which are much easier to catch patterns in the sample. The technique of simple aggregation by key fields is used to optimize search and analysis. The higher the maturity level of the TH process in an organization, the more relevant the use of machine learning algorithms becomes. They are also widely used in spam filtering, malicious traffic detection and fraud detection. A more advanced type of machine learning algorithm is Bayesian methods that allow classification, sample size reduction, and thematic modeling.
Diamond Model and Strategy TH
Sergio Kaltagiron, Andrew Pendegast and Christopher Betz, in their work The Diamond Model of Intrusion Analysis , showed the main key components of any malicious activity and the basic connection between them.

According to this model, there are 4 Threat Hunting strategies that rely on the relevant key components.
1. A strategy focused on the victim. We assume that the victim has opponents, and they will deliver "opportunities" through e-mail. We are looking for enemy data in the mail. Search for links, attachments and etc. We are looking for confirmation of this hypothesis for a certain period (month, two weeks), if not found, then the hypothesis has not played.
2. Infrastructure oriented strategy. There are several methods for using this strategy. Depending on access and visibility, some are lighter than others. For example, we monitor domain name servers that are known to host malicious domains. Or we carry out the process of tracking all new domain name registrations for a known pattern used by the adversary.
3. A strategy focused on opportunities. In addition to the victim-centered strategy used by most of the network defenders, there is an opportunity-oriented strategy. It is the second most popular and focuses on detecting opportunities from the adversary, namely “malware” and the possibility of the adversary using such legitimate tools as psexec, powershell, certutil and others.
4. Strategy focused on the enemy. The enemy-oriented approach focuses on the enemy. These include the use of public information from publicly available sources (OSINT), collection of data about the enemy, his techniques and methods (TTP), analysis of previously occurring incidents, Threat Intelligence data, etc.
Sources of information and hypotheses in TH

Sources of information can be very much. The ideal analyst should be able to extract information from all that is around. Typical sources in almost any infrastructure will be data from the means of protection: DLP, SIEM, IDS / IPS, WAF / FW, EDR. Also typical sources of information will be various indicators of compromise, Threat Intelligence services, CERT and OSINT data. Additionally, you can use the information from the darknet (for example, suddenly there is an order for breaking the mailbox of the head of the organization, or a candidate for the network engineer has become active), information received from HR (reviews about the candidate from the past job), information from the security service ( for example, the results of the counterparty check).
But before using all available sources, it is necessary to have at least one hypothesis.

In order to test hypotheses, they must first be put forward. And in order to put forward many qualitative hypotheses, it is necessary to apply a systematic approach. The process of hypothesis generation is described in more detail in the article ; it is very convenient to take this scheme as the basis for the process of hypothesizing.
The main source of hypotheses will be the matrix ATT & CK (Adversarial Tactics, Techniques and Common Knowledge). It is, in essence, a knowledge base and model for assessing the behavior of intruders who implement their activities in the last steps of an attack, usually described with the help of the concept of Kill Chain. That is, at the stages after an intruder penetrates the internal network of the enterprise or the mobile device. Initially, the knowledge base included a description of 121 tactics and techniques used in the attack, each of which is described in detail in the Wiki format. As a source for the generation of hypotheses is well suited various analytics Threat Intelligence. Of particular note are the results of the analysis of infrastructure and penetration tests - these are the most valuable data that can give us iron hypotheses because they rely on a specific infrastructure with its specific flaws.
Hypothesis testing process
Sergey Soldatov gave a good scheme with a detailed description of the process; it illustrates the process of testing the TH hypotheses in a single system. I will indicate the main stages with a brief description.

Stage 1: TI Farm
At this stage, it is necessary to select objects (by analyzing them together with all the data about the threats) and assigning them the labels of their characteristics. This is a file, URL, MD5, process, utility, event. Passing them through the systems of Threat Intelligence, you must hang tags. That is, this site was seen at CNC in a certain year, this MD5 was associated with such and such a Malvar, this MD5 swung from the site that distributed the malware.
Stage 2: Cases
At the second stage, we look at the interaction between these objects and identify the relationships between all these objects. We get labeled systems that do something bad.
Stage 3: Analyst
At the third stage, the case is transferred to an experienced analyst, who has a vast experience of analysis, and he makes a verdict. It parses up to bytes what, whence, how, why and why does this code. This body was malicious, this computer was infected. Opens the connection between objects, checks the results of the run through the sandbox.
The results of the analyst are passed on. Digital Forensics examines the images, Malware Analysis examines the found “bodies”, and the Incident Response team can go to the site and explore something already there. The result of the work will be a confirmed hypothesis, the identified attack and ways to counter it.

Results
Threat Hunting is a fairly young technology that can effectively withstand customized, new and non-standard threats, which has great prospects given the growing number of such threats and the increasing complexity of corporate infrastructure. It requires three components - data, tools and analytics. The benefits of Threat Hunting are not limited to the proactive implementation of threats. Do not forget that in the process of searching we dive into our infrastructure and its weak points through the eyes of a security analyst and we can further strengthen these places.
The first steps that, in our opinion, need to be done to initiate the TH process in your organization.
- Take care of endpoint and network infrastructure protection. Take care of the visibility (NetFlow) and control (firewall, IDS, IPS, DLP) of all processes in your network. Know your network from the border router to the most recent host.
- Learn MITER ATT & CK .
- To conduct regular pentest at least key external resources, analyze its results, highlight the main objectives for the attack and close their vulnerabilities.
- Implement an open source Threat Intelligence system (for example, MISP, Yeti) and analyze logs with it.
- Implement an incident response platform (IRP): R-Vision IRP, The Hive, a sandbox for analyzing suspicious files (FortiSandbox, Cuckoo).
- Automate routine processes. Log analysis, incident management, staff information are a huge field for automation.
- Learn to interact effectively with engineers, developers, technical support to work together on incidents.
- Document the entire process, key points, achieved results, to return to them later or share this data with colleagues;
- Remember about the social side: be aware of what is happening with your employees, whom you recruit and who you give access to the information resources of the organization.
- To keep abreast of trends in the field of new threats and ways of protection, to increase your level of technical literacy (including in the work of IT services and subsystems), to attend conferences and communicate with colleagues.
Ready to discuss the organization of the TH process in the comments.
Or come to work with us!
Source: https://habr.com/ru/post/447580/
All Articles