Doctor rides, rides
In open access, a MongoDB database was found that does not require authentication, which contained information from the Moscow Ambulance Stations (MSS).

Unfortunately, this is not the only problem: firstly, this time the data really leaked, and secondly - all sensitive information was stored on a server located in Germany ( I would like to ask - does this violate any law or departmental instructions? ) .
: . . , .
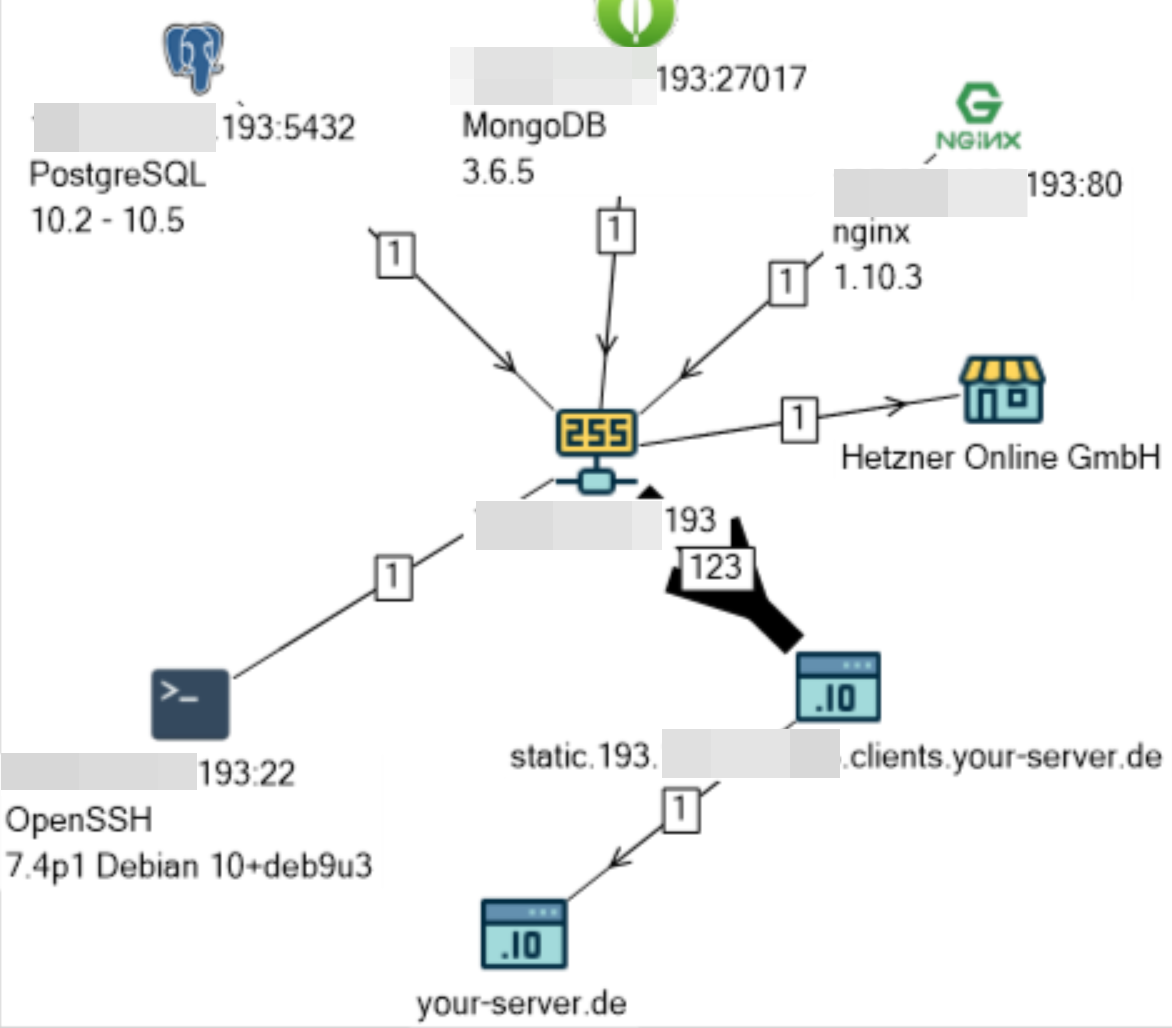
The server with the base, which is called “ ssmp ”, is located at the site of the famous hosting provider Hetzner in Germany.
By indirect evidence, the alleged owner of the server and the base, the Russian company OOO Computer Intelligent Systems, was established .
On the page ci-systems.com/solutions/programs-smp/, the company informs us:
KIS SMP is a software product designed to automate the operation of emergency (specialized) medical care stations (SMPs) within the boundaries of a constituent entity of the Russian Federation and provides:
- receive calls;
- call registration and forwarding;
- the formation, monitoring and management of mobile teams of stations of the NSR;
- massive reassignment of the emergency police teams in emergency response;
- the work of a single call center SMP;
- data exchange with external information systems.
The base had a size of 17.3 GB and contained:
- Date / time of call ambulance
- Name of ambulance crew members (including driver)
- ambulance car license plate
- the status of the ambulance car (for example, “arrival at the call”)
- call address
- Name, date of birth, gender of the patient
- description of the patient's condition (for example, “temperature> 39, poorly reduced, adult”)
- Name of the ambulance
- contact number
- and much more…
The data in the database is similar to a log of some system monitoring / tracking the process of performing the task. Of interest is the “ data ” field in the “ assign_data_history ” table.

(Of course, in the picture above, I tried to hide all personal data.)
As it was written at the very beginning - the lack of authentication this time is not the only problem.
The most important thing is that this database was first discovered by the Ukrainian hackers from the THack3forU grouping, who left different messages in the MongoDB found and destroyed the information. This time the lads distinguished themselves by this:
"Hacked by THack3forU! Chanel. \ NPutin huylo, \ nMєdvєdєv schmuck, \ nStruck Gamno, \ nRussia BOT!"
and of course by the fact that, having downloaded all 17 GB, they were uploaded in CSV format to the file hosting site Mega.nz. About how open MongoDB databases are discovered - here .
As soon as the owner of the database was installed, I sent him an alert with a proposal to still close access to the database, although it was already late - the data was “gone”.
The first time the search engine Shodan fixed this base on 06.28.2018, and access to it was finally closed on 08/04/2019, somewhere between 17:20 and 18:05 (MSK). A little less than 6 hours have passed since the notification.
News about information leaks and insiders can always be found on my Information Leaks Telegram channel.
')
Source: https://habr.com/ru/post/447290/
All Articles