Security Week 15: attack on routers with DNS spoofing
 The topic of vulnerabilities in network routers is not the first time we are addressing, but the research of the Bad Packets and Ixia companies ( news , Bad Packets report, Ixia report ) is interesting because they provide an almost complete picture: how to break routers, what settings change, and what then it happens.
The topic of vulnerabilities in network routers is not the first time we are addressing, but the research of the Bad Packets and Ixia companies ( news , Bad Packets report, Ixia report ) is interesting because they provide an almost complete picture: how to break routers, what settings change, and what then it happens.Such attacks do not have any technically complex elements, and the goal of the attackers is simple - to earn money from advertising and, if possible, to steal passwords for access to banking systems and paid Internet services. In short: the attackers scanned the network to find vulnerable routers (mostly non-new D-Link production models). Having found such a router, they changed the DNS records in it, redirecting traffic to their own servers. Vulnerabilities were used for this trivial, access to the settings for non-patched devices occurred without authorization. The oldest devices in the target list are more than 10 years old, but despite this, in theory, cybercriminals could attack more than 15 thousand victims.
Specialists Bad Packets recorded three attacks with common signs at the end of December last year, as well as in February and the end of March 2019. In all cases, the Google Cloud Platform service was used for the first stage of the attack: a virtual server was created that made a dial-up of network devices.
The scan was aimed at finding devices with known vulnerabilities, mostly they were not the most modern routers manufactured by D-Link. Later, using the BinaryEdge service that collects information about the parameters of network devices, it was possible to estimate how many devices were in principle vulnerable to such an attack. Of the dozen models that were definitely attacked during this campaign, only one had recorded several thousand “hits”.
')

This is an D-Link DSL-2640B ADSL router. Stored megabyte Ethernet, WiFi 802.11g support - overall not bad for a model that has been available since 2007. Other models (for example, D-Link 2740R, 526B and others, only about a dozen versions), if they benefited attackers, then on a small scale - only a few hundred of such devices are available on the network.
In 2012, the traditional for network devices vulnerability was discovered in the 2640B model: if you force the user logged into the web interface of the router to click on the prepared link, you can gain control of the device. And in 2017, a more serious problem was discovered in the same router: it turned out that it was possible to replace DNS server records without authorization . Naturally, if the web interface of the router is accessible from the outside, which should not happen under normal conditions.
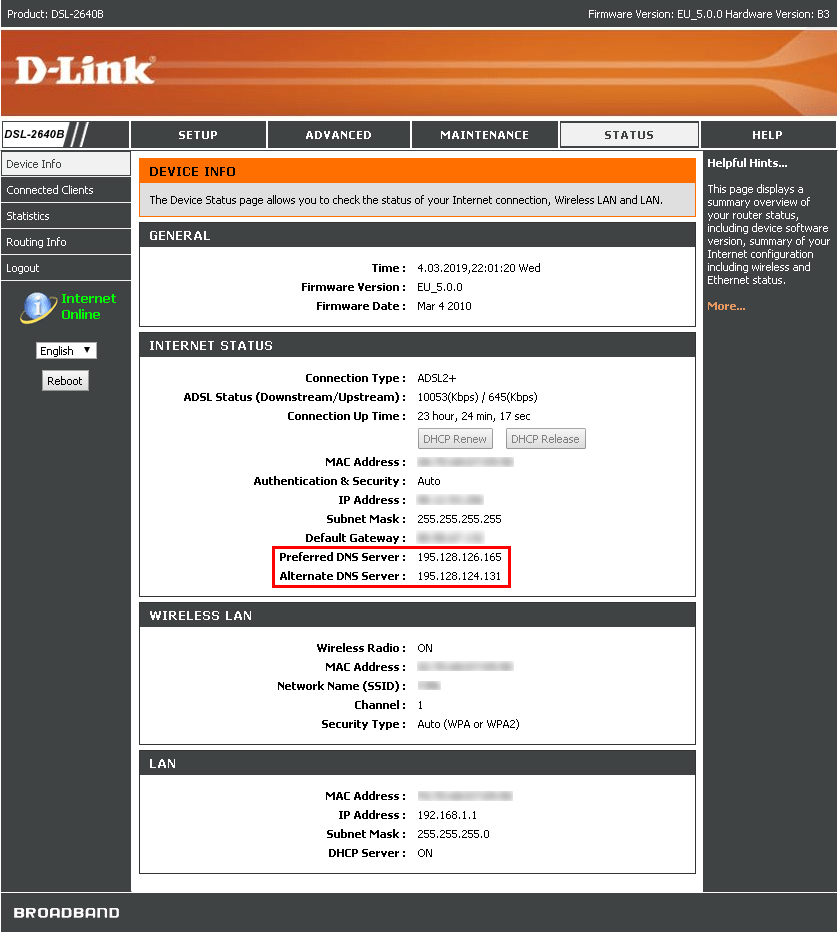
The consequences of DNS server substitution are obvious: attackers have the opportunity to substitute ad banners with their own, show fake websites to users at the "correct" address, attack computers connected to the router with the use of malware directly.
What exactly happens with the attacked router, found out in the company Ixia. It was done this way: on the test system, the attackers' server was installed as a DNS server, then a list of 10,000 domain names of the most popular sites was run (according to the Alexa version). It was necessary to find out for which domains a fake DNS server is trying to lead victims to its own versions of sites. Site spoofing was fixed for four global services: Paypal, GMail, Uber and Netflix. Other domains (more than ten in total) were local services of banks and network providers in Brazil.
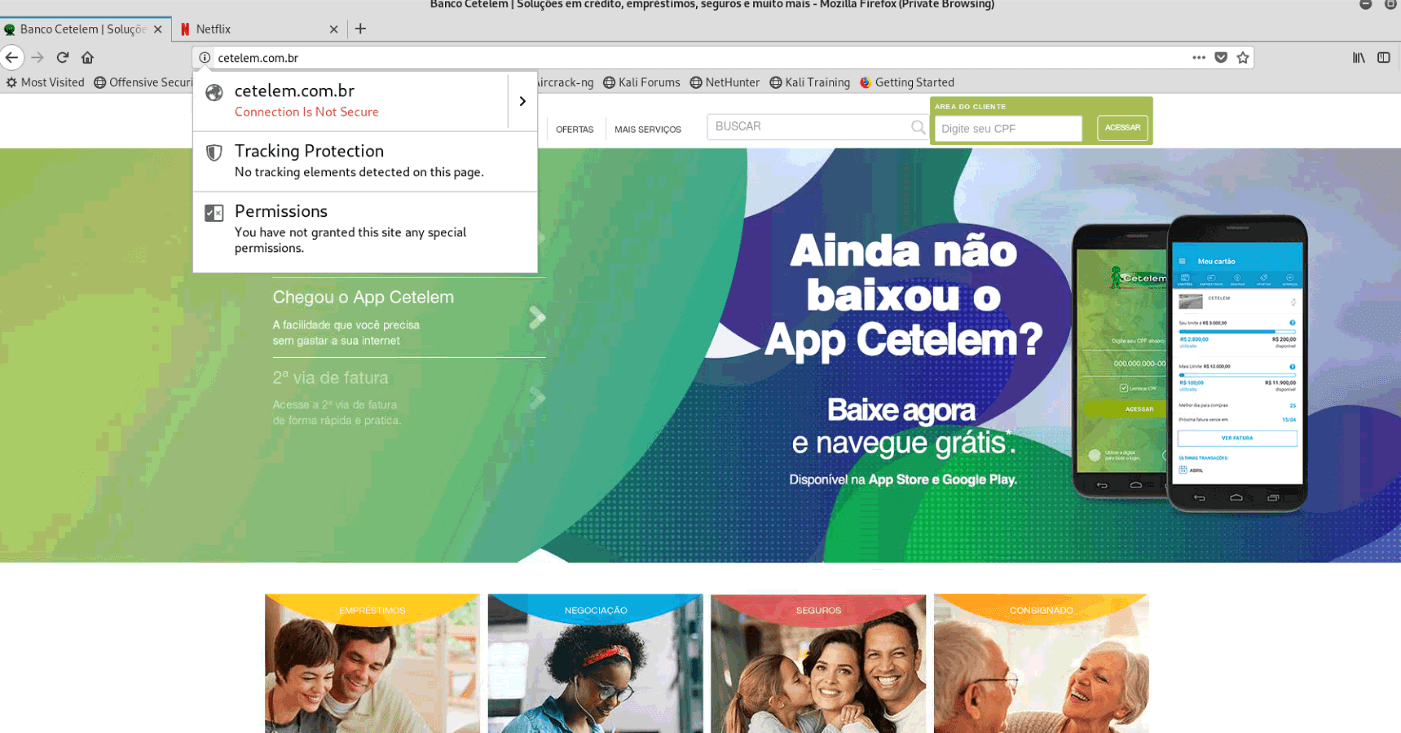
A copy of the banking service looks reliable, only a lack of HTTPS connection indicates a fake. The attackers apparently did not have time to properly prepare some of the redirects: instead of cetelem.com , for example, the standard Apache web server plug was shown. In the event of a specific attack in March of this year, both fake websites and the DNS server itself also hosted on the Google cloud platform. In response to a request from Arstechnica , Google reported that malicious services were blocked and measures were taken to automatically block such operations in the future. However, the point is not Google: other waves of attack used servers in Canada and Russia.
In general, in this particular case we are not talking about a large-scale attack. Defective devices that have been around for many years, with fairly long-known vulnerabilities, and which for some reason (erroneous configuration, insecure default settings), in principle, allow you to open a web interface when accessing from the Internet, and not just from the local network. In this case, it is hardly worth relying on a patch for the old firmware, it is easier to upgrade. Why are attackers even attacking such relatively few types of devices? It is quite simple and profitable.
Large-scale attacks with DNS spoofing have been fixed for the last ten years, there have been more creative methods, such as attacking routers with a malicious application, after connecting to Wi-Fi. Then there are a lot of ways to dishonestly withdraw money: phishing and subsequent resale of passwords on the black market (recently paid service accounts for streaming music and video have become a hot commodity, direct theft of funds through banking and payment services, distribution of malicious software. In the same Brazil, similar attacks took on the character of an epidemic , the score goes to hundreds of thousands of attacked devices. So today we have before us a fairly well documented, but a small episode of the turbulent activity of cybercrime.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/447258/
All Articles