Myths about 152-FZ, which can be costly for the operator of personal data
Hello! I lead the DataLine Cyber Defense Center. Customers come to us with the task of fulfilling the requirements of 152-FZ in the cloud or on a physical infrastructure.
Practically in each project it is necessary to carry out educational work on dispelling the myths around this law. I have collected the most frequent errors that can be costly for the budget and the nervous system of the operator of personal data. At once I will make a reservation that the cases of state offices (GIS) dealing with a state secret, KII, etc. will remain outside the scope of this article.

152-FZ is not about protecting systems and servers, but about protecting the personal data of subjects. Therefore, compliance with 152-FZ does not begin with antivirus, but with a large number of pieces of paper and organizational issues.
The main inspector, Roskomnadzor, will not look at the presence and condition of technical means of protection, but at the legal basis for the processing of personal data (PD):
')
Answers to these questions, as well as the processes themselves, should be recorded in the relevant documents. This is not a complete list of what you need to prepare the personal data operator:
After resolving these issues, you can proceed to the selection of specific measures and technical means. What exactly you need depends on the systems, their working conditions and actual threats. But more on that later.
Reality: compliance with the law is the establishment and observance of certain processes, first of all, and only the second - the use of special technical means.
When you outsource the storage of personal data to a cloud provider or to a data center, you will not cease to be an operator of personal data.
Let's call for help definition from the law:
Personal data processing - any action (operation) or set of actions (operations) performed with the use of automation tools or without the use of such tools with personal data, including the collection, recording, systematization, accumulation, storage, refinement (update, change), retrieval, use, transfer (distribution, provision, access), depersonalization, blocking, deletion, destruction of personal data.
Source: Article 3, 152-
Of all these actions, the service provider is responsible for the storage and destruction of personal data (when the client terminates the contract with him). Everything else is provided by the operator of personal data. This means that the operator, and not the service provider, determines the personal data processing policy, receives signed consent to the processing of personal data from its customers, prevents and investigates cases of personal data leaks, and so on.
Consequently, the personal data operator must still collect the documents listed above and carry out organizational and technical measures to protect their IPDD.
Usually, the provider helps the operator by ensuring compliance with the requirements of the law at the level of the infrastructure where the ISPD of the operator will be located: equipment racks or the cloud. He also collects a package of documents, takes organizational and technical measures for his piece of infrastructure in accordance with 152-FZ.
Some providers help with paperwork and the provision of technical means of protection for ISPDn themselves, that is, a level above the infrastructure. The operator can also outsource these tasks, but the responsibility and obligations under the law do not disappear anywhere.
Reality: referring to the services of the provider or data center, you can not transfer to it the obligations of the operator of personal data and get rid of responsibility. If the provider promises you this, then he, to put it mildly, is cunning.
Yes, if you do not forget to sign the order. By law, the operator may entrust the processing of personal data to another person, for example, the same service provider. An order is a kind of contract that lists what the service provider can do with the personal data of the operator.
The operator has the right to entrust the processing of personal data to another person with the consent of the subject of personal data, unless otherwise provided by federal law, on the basis of a contract concluded with this person, including a state or municipal contract, or by adopting a relevant act by a state or municipal body (hereinafter referred to as operator). A person who processes personal data at the request of the operator must comply with the principles and rules for the processing of personal data provided for by this Federal Law.
Source: Clause 3, Article 6, 152-
The obligation of the provider to maintain the confidentiality of personal data and ensure their security in accordance with the specified requirements is fixed here:
The statement of the operator should define the list of actions (operations) with personal data that will be performed by the person processing the personal data, and the processing objectives should establish the obligation of such a person to maintain the confidentiality of personal data and to ensure the security of personal data during their processing, as well as The requirements for the protection of personal data processed in accordance with Article 19 of this Federal Law must be specified.
Source: Clause 3, Article 6, 152-
For this, the provider is responsible to the operator, and not to the subject of personal data:
If the operator assigns the processing of personal data to another person, the responsibility to the subject of personal data for the actions of the said person is borne by the operator. The person who processes personal data on behalf of the operator is liable to the operator.
Source: 152-FZ .
It is also important to state in the assignment the obligation to ensure the protection of personal data:
The security of personal data when it is processed in the information system is provided by the operator of this system who processes personal data (hereinafter referred to as the operator), or the person who processes personal data on behalf of the operator on the basis of the contract concluded with this person (hereinafter the authorized person). The contract between the operator and the authorized person should provide for the obligation of the authorized person to ensure the security of personal data when they are processed in the information system.
Source: Government Decree of November 1, 2012 № 1119
Reality: if you give personal data to the provider, sign the order. In the order, specify the requirement to ensure the protection of PD subjects. Otherwise, you do not comply with the law regarding the transfer of personal data processing work by a third party and the provider regarding compliance with 152-FZ is not obliged to you.
Some customers persistently argue that their ISPD has a security level of 1 or 2. Most often this is not the case. Recall materiel to figure out why this happens.
UZ, or security level, determines what you will protect personal data from.
The following factors affect the security level:
About the types of threats we are told by the Government Decree of November 1, 2012 No. 1119 . Here is a description of each with my free translation into human language.
Type 1 threats are relevant to an information system if, for example, threats related to the presence of undocumented (non-declared) capabilities in the system software used in the information system are relevant to it.
If you recognize this type of threat as relevant, then you firmly believe that the CIA, MI-6 or Mossad agents placed a tab in the operating system in order to steal the personal data of specific subjects from your SPDN.
Threats of the 2nd type are relevant for an information system, if for it, including threats related to the presence of undocumented (undeclared) capabilities in the application software used in the information system.
If you think that threats of the second type are your case, then you are asleep and you see how the same CIA agents, MI6, Mossad, a malicious single hacker or a group placed bookmarks in some office software to hunt. for your personal data. Yes, there is doubtful application software such as μTorrent, but you can make a list of allowed software for installation and sign an agreement with users, not give users the rights of local administrators, etc.
Threats of the 3rd type are relevant for the information system if it is relevant for threats that are not related to the presence of undocumented (undeclared) capabilities in the system and application software used in the information system.
You are not suitable threats 1 and 2 types, then you here.
With the types of threats figured out, now we look at what level of security our ISPDn will have.
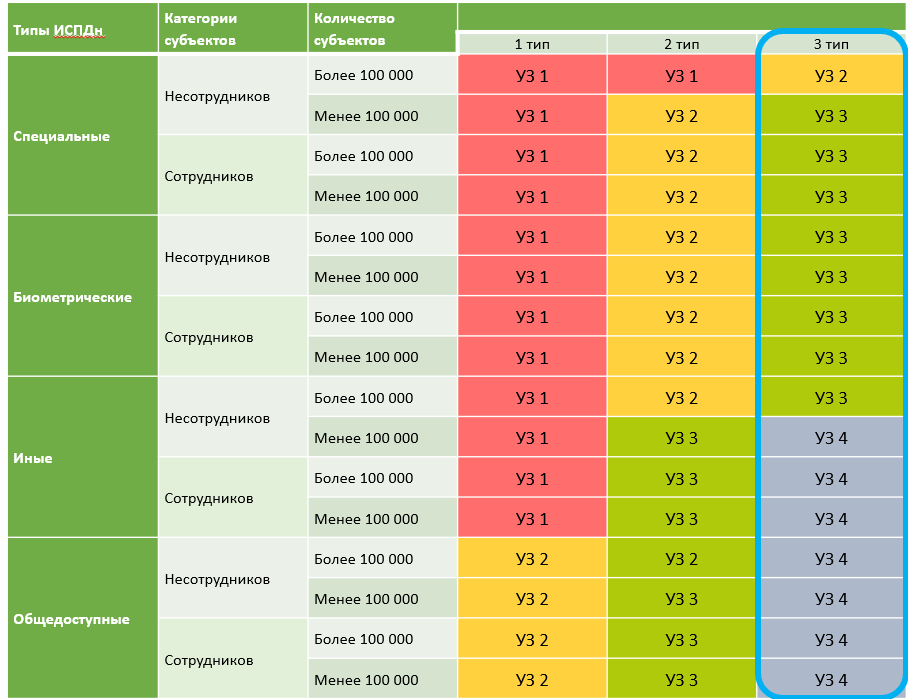
The table is based on the correspondences prescribed in the Decree of the Government of the Russian Federation of November 1, 2012 No. 1119 .
If we have chosen the third type of actual threats, then in most cases we will have an OZ-3. The only exception when threats of type 1 and type 2 are not relevant, but the level of protection will still be high (US-2) are companies that process non-employee specific personal data of more than 100,000. For example, companies engaged in medical diagnosis and medical services.
There is also UZ-4, and it is mainly found in companies whose business is not related to the processing of personal data of non-employees, that is, customers or contractors, or personal databases are small.
Why is it so important not to overdo it with the level of security? It's simple: a set of measures and means of protection will depend on this to ensure this very level of security. The higher the ultrasound, the more it will be necessary to do in the organizational and technical terms (read: the more money and nerves need to be spent).
Here, for example, how the set of security measures is changing in accordance with the same PP-1119.

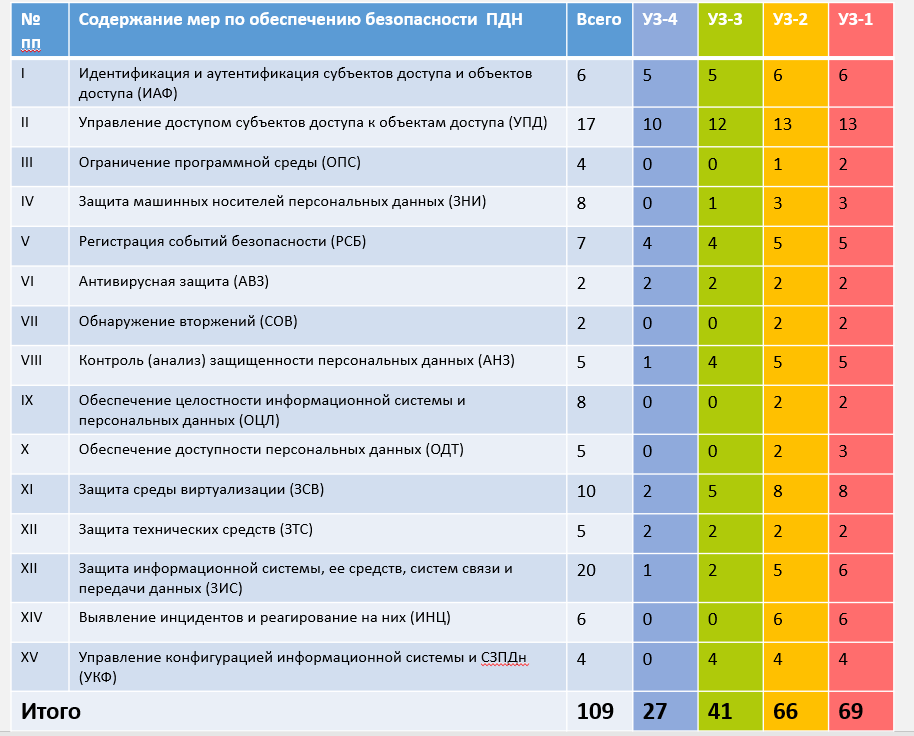
Now we are looking at how, depending on the chosen level of security, the list of necessary measures changes in accordance with the Order of the FSTEC of Russia No. 21 of February 18, 2013. There is a long appendix to this document, where the necessary measures are determined. In total there are 109 of them; mandatory measures are identified and marked with "+" for each ultrasound - they are calculated in the table below. If you leave only those that are needed for UZ-3, you get 41.
Reality: if you do not collect analyzes or biometrics of clients, you are notparanoid afraid of bookmarks in the system and application software, then, most likely, you have UZ-3. For it, there is a sane list of organizational and technical measures that are actually implemented.
If you want or are required to certify, then most likely you will have to use certified protective equipment. The certification will be carried out by the licensee of FSTEC of Russia, which:
If you do not need certification and you are ready to confirm the fulfillment of the requirements in a different way, named in the Order of the FSTEC of Russia No. 21 “Assessing the effectiveness of personal data security measures implemented under the personal data protection system”, then certified GIS are not mandatory for you. I will try to briefly provide a rationale.
Clause 2 of Article 19 of 152- states that it is necessary to use protective equipment that has passed the conformity assessment procedure in the prescribed manner :
Ensuring the security of personal data is achieved, in particular:
[...]
3) the use of the information security measures passed in the prescribed manner.
In paragraph 13 of PP-1119 there is also a requirement to use information security tools that have passed the procedure for assessing compliance with legal requirements:
[...]
the use of information security tools that have undergone a procedure for assessing compliance with the requirements of the legislation of the Russian Federation in the field of information security, in the event that the use of such tools is necessary to neutralize actual threats.
Clause 4 of the Order of FSTEC No. 21 virtually duplicates paragraph PP-1119:
Measures to ensure the security of personal data are implemented, including through the use of information security tools in the information system, which have passed the conformity assessment procedure in the prescribed manner in cases where the use of such tools is necessary to neutralize actual threats to the security of personal data.
What do these formulations have in common? That's right - there is no requirement for them to use certified protective equipment. The fact is that there are several forms of conformity assessment (voluntary or mandatory certification, declaration of conformity). Certification is just one of them. The operator may use non-certified means, but it will be necessary to demonstrate to the regulator when checking that they have passed the conformity assessment procedure in some form.
If the operator decides to use certified means of protection, then it is necessary to choose SZI in accordance with the UZ, which is clearly stated in the Order of FSTEC No. 21 :
Technical measures to protect personal data are implemented through the use of information security tools, including software (hardware and software) tools in which they are implemented, having the necessary security functions.
When using information security certified information security systems in information systems:
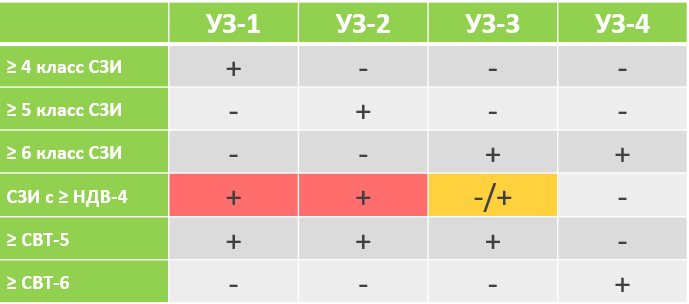
Paragraph 12 of the Order No. 21 of FSTEC of Russia .
Reality: the law does not require the mandatory use of certified remedies.
There are several nuances:
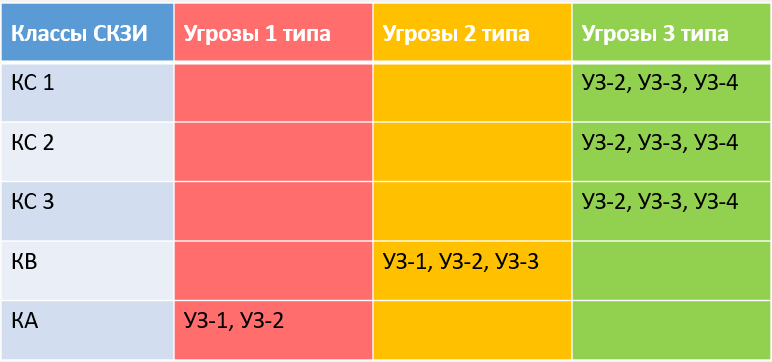
For ISPDN with UZ-3 it is possible to use KS1, KS2, KS3. KC1 is, for example, C-Terra Virtual Gateway 4.2 for channel protection.
KC2, KC3 are represented only by hardware-software complexes, such as: ViPNet Coordinator, APKS Continent, S-Terra Gateway, etc.
If you have a UZ-2 or 1, then you will need KV1, 2 and KA class cryptographic tools. These are specific software and hardware systems, they are difficult to exploit, and performance characteristics are modest.
Reality: the law does not oblige the use of SKZI, certified by the FSB.
Practically in each project it is necessary to carry out educational work on dispelling the myths around this law. I have collected the most frequent errors that can be costly for the budget and the nervous system of the operator of personal data. At once I will make a reservation that the cases of state offices (GIS) dealing with a state secret, KII, etc. will remain outside the scope of this article.

Myth 1. I set up an antivirus, firewall, fenced racks. Do I keep the law?
152-FZ is not about protecting systems and servers, but about protecting the personal data of subjects. Therefore, compliance with 152-FZ does not begin with antivirus, but with a large number of pieces of paper and organizational issues.
The main inspector, Roskomnadzor, will not look at the presence and condition of technical means of protection, but at the legal basis for the processing of personal data (PD):
')
- for what purpose do you collect personal data;
- Do not you collect them more than you need for your purposes;
- how much personal data is stored;
- Is there a personal data processing policy?
- do you collect consent for PD processing, for a cross-border transfer, for processing by third parties, etc.
Answers to these questions, as well as the processes themselves, should be recorded in the relevant documents. This is not a complete list of what you need to prepare the personal data operator:
- The standard form of consent to the processing of personal data (these are the sheets that we now sign almost everywhere where we leave our full name, passport data).
- The policy of the operator in relation to the processing of PD ( there are recommendations for registration).
- Order on the appointment of a person responsible for organizing the processing of PD.
- Job Description of the person responsible for organizing the processing of PD.
- Rules of internal control and (or) audit of compliance with PD processing requirements of the law.
- The list of personal data information systems (ISPDn).
- Regulations for the provision of access to the subject of his PD.
- Regulations investigate incidents.
- Order on the admission of workers to the processing of PD.
- Regulation of interaction with regulators.
- Notification of ILV, etc.
- The form of instructions for processing PD.
- Model of ISPDn threats.
After resolving these issues, you can proceed to the selection of specific measures and technical means. What exactly you need depends on the systems, their working conditions and actual threats. But more on that later.
Reality: compliance with the law is the establishment and observance of certain processes, first of all, and only the second - the use of special technical means.
Myth 2. I store personal data in the cloud, a data center that meets the requirements of 152-FZ. Now they are responsible for enforcing the law.
When you outsource the storage of personal data to a cloud provider or to a data center, you will not cease to be an operator of personal data.
Let's call for help definition from the law:
Personal data processing - any action (operation) or set of actions (operations) performed with the use of automation tools or without the use of such tools with personal data, including the collection, recording, systematization, accumulation, storage, refinement (update, change), retrieval, use, transfer (distribution, provision, access), depersonalization, blocking, deletion, destruction of personal data.
Source: Article 3, 152-
Of all these actions, the service provider is responsible for the storage and destruction of personal data (when the client terminates the contract with him). Everything else is provided by the operator of personal data. This means that the operator, and not the service provider, determines the personal data processing policy, receives signed consent to the processing of personal data from its customers, prevents and investigates cases of personal data leaks, and so on.
Consequently, the personal data operator must still collect the documents listed above and carry out organizational and technical measures to protect their IPDD.
Usually, the provider helps the operator by ensuring compliance with the requirements of the law at the level of the infrastructure where the ISPD of the operator will be located: equipment racks or the cloud. He also collects a package of documents, takes organizational and technical measures for his piece of infrastructure in accordance with 152-FZ.
Some providers help with paperwork and the provision of technical means of protection for ISPDn themselves, that is, a level above the infrastructure. The operator can also outsource these tasks, but the responsibility and obligations under the law do not disappear anywhere.
Reality: referring to the services of the provider or data center, you can not transfer to it the obligations of the operator of personal data and get rid of responsibility. If the provider promises you this, then he, to put it mildly, is cunning.
Myth 3. I have the necessary package of documents and measures. I keep personal data with the provider, which promises compliance with 152-FZ. All in openwork?
Yes, if you do not forget to sign the order. By law, the operator may entrust the processing of personal data to another person, for example, the same service provider. An order is a kind of contract that lists what the service provider can do with the personal data of the operator.
The operator has the right to entrust the processing of personal data to another person with the consent of the subject of personal data, unless otherwise provided by federal law, on the basis of a contract concluded with this person, including a state or municipal contract, or by adopting a relevant act by a state or municipal body (hereinafter referred to as operator). A person who processes personal data at the request of the operator must comply with the principles and rules for the processing of personal data provided for by this Federal Law.
Source: Clause 3, Article 6, 152-
The obligation of the provider to maintain the confidentiality of personal data and ensure their security in accordance with the specified requirements is fixed here:
The statement of the operator should define the list of actions (operations) with personal data that will be performed by the person processing the personal data, and the processing objectives should establish the obligation of such a person to maintain the confidentiality of personal data and to ensure the security of personal data during their processing, as well as The requirements for the protection of personal data processed in accordance with Article 19 of this Federal Law must be specified.
Source: Clause 3, Article 6, 152-
For this, the provider is responsible to the operator, and not to the subject of personal data:
If the operator assigns the processing of personal data to another person, the responsibility to the subject of personal data for the actions of the said person is borne by the operator. The person who processes personal data on behalf of the operator is liable to the operator.
Source: 152-FZ .
It is also important to state in the assignment the obligation to ensure the protection of personal data:
The security of personal data when it is processed in the information system is provided by the operator of this system who processes personal data (hereinafter referred to as the operator), or the person who processes personal data on behalf of the operator on the basis of the contract concluded with this person (hereinafter the authorized person). The contract between the operator and the authorized person should provide for the obligation of the authorized person to ensure the security of personal data when they are processed in the information system.
Source: Government Decree of November 1, 2012 № 1119
Reality: if you give personal data to the provider, sign the order. In the order, specify the requirement to ensure the protection of PD subjects. Otherwise, you do not comply with the law regarding the transfer of personal data processing work by a third party and the provider regarding compliance with 152-FZ is not obliged to you.
Myth 4. Mossad is spying on me, or I certainly have UZ-1
Some customers persistently argue that their ISPD has a security level of 1 or 2. Most often this is not the case. Recall materiel to figure out why this happens.
UZ, or security level, determines what you will protect personal data from.
The following factors affect the security level:
- type of personal data (special, biometric, publicly available and other);
- who owns personal data - employees or non-employees of the operator of personal data;
- the number of personal data subjects is more or less than 100 thousand.
- types of actual threats.
About the types of threats we are told by the Government Decree of November 1, 2012 No. 1119 . Here is a description of each with my free translation into human language.
Type 1 threats are relevant to an information system if, for example, threats related to the presence of undocumented (non-declared) capabilities in the system software used in the information system are relevant to it.
If you recognize this type of threat as relevant, then you firmly believe that the CIA, MI-6 or Mossad agents placed a tab in the operating system in order to steal the personal data of specific subjects from your SPDN.
Threats of the 2nd type are relevant for an information system, if for it, including threats related to the presence of undocumented (undeclared) capabilities in the application software used in the information system.
If you think that threats of the second type are your case, then you are asleep and you see how the same CIA agents, MI6, Mossad, a malicious single hacker or a group placed bookmarks in some office software to hunt. for your personal data. Yes, there is doubtful application software such as μTorrent, but you can make a list of allowed software for installation and sign an agreement with users, not give users the rights of local administrators, etc.
Threats of the 3rd type are relevant for the information system if it is relevant for threats that are not related to the presence of undocumented (undeclared) capabilities in the system and application software used in the information system.
You are not suitable threats 1 and 2 types, then you here.
With the types of threats figured out, now we look at what level of security our ISPDn will have.

The table is based on the correspondences prescribed in the Decree of the Government of the Russian Federation of November 1, 2012 No. 1119 .
If we have chosen the third type of actual threats, then in most cases we will have an OZ-3. The only exception when threats of type 1 and type 2 are not relevant, but the level of protection will still be high (US-2) are companies that process non-employee specific personal data of more than 100,000. For example, companies engaged in medical diagnosis and medical services.
There is also UZ-4, and it is mainly found in companies whose business is not related to the processing of personal data of non-employees, that is, customers or contractors, or personal databases are small.
Why is it so important not to overdo it with the level of security? It's simple: a set of measures and means of protection will depend on this to ensure this very level of security. The higher the ultrasound, the more it will be necessary to do in the organizational and technical terms (read: the more money and nerves need to be spent).
Here, for example, how the set of security measures is changing in accordance with the same PP-1119.

Now we are looking at how, depending on the chosen level of security, the list of necessary measures changes in accordance with the Order of the FSTEC of Russia No. 21 of February 18, 2013. There is a long appendix to this document, where the necessary measures are determined. In total there are 109 of them; mandatory measures are identified and marked with "+" for each ultrasound - they are calculated in the table below. If you leave only those that are needed for UZ-3, you get 41.

Reality: if you do not collect analyzes or biometrics of clients, you are not
Myth 5. All means of protection (GIS) of personal data must be certified by FSTEC of Russia
If you want or are required to certify, then most likely you will have to use certified protective equipment. The certification will be carried out by the licensee of FSTEC of Russia, which:
- interested to sell more certified GIS;
- will be afraid of the revocation of the license by the regulator if something goes wrong.
If you do not need certification and you are ready to confirm the fulfillment of the requirements in a different way, named in the Order of the FSTEC of Russia No. 21 “Assessing the effectiveness of personal data security measures implemented under the personal data protection system”, then certified GIS are not mandatory for you. I will try to briefly provide a rationale.
Clause 2 of Article 19 of 152- states that it is necessary to use protective equipment that has passed the conformity assessment procedure in the prescribed manner :
Ensuring the security of personal data is achieved, in particular:
[...]
3) the use of the information security measures passed in the prescribed manner.
In paragraph 13 of PP-1119 there is also a requirement to use information security tools that have passed the procedure for assessing compliance with legal requirements:
[...]
the use of information security tools that have undergone a procedure for assessing compliance with the requirements of the legislation of the Russian Federation in the field of information security, in the event that the use of such tools is necessary to neutralize actual threats.
Clause 4 of the Order of FSTEC No. 21 virtually duplicates paragraph PP-1119:
Measures to ensure the security of personal data are implemented, including through the use of information security tools in the information system, which have passed the conformity assessment procedure in the prescribed manner in cases where the use of such tools is necessary to neutralize actual threats to the security of personal data.
What do these formulations have in common? That's right - there is no requirement for them to use certified protective equipment. The fact is that there are several forms of conformity assessment (voluntary or mandatory certification, declaration of conformity). Certification is just one of them. The operator may use non-certified means, but it will be necessary to demonstrate to the regulator when checking that they have passed the conformity assessment procedure in some form.
If the operator decides to use certified means of protection, then it is necessary to choose SZI in accordance with the UZ, which is clearly stated in the Order of FSTEC No. 21 :
Technical measures to protect personal data are implemented through the use of information security tools, including software (hardware and software) tools in which they are implemented, having the necessary security functions.
When using information security certified information security systems in information systems:

Paragraph 12 of the Order No. 21 of FSTEC of Russia .
Reality: the law does not require the mandatory use of certified remedies.
Myth 6. I need crypto protection
There are several nuances:
- Many believe that cryptography is required for any SPDN. In fact, they should be used only if the operator does not see any other protection measures for himself, except for the use of cryptography.
- If there is no cryptography in any way, then you need to use ICFs certified by the FSB.
- For example, you decided to place ISPDN in the cloud of a service provider, but do not trust it. You describe your fears in the threat and intruder model. You have a PDN, so you decided that cryptography is the only way to protect: you will encrypt virtual machines, build secure channels through cryptographic protection. In this case, you will have to use ICPs certified by the FSB of Russia.
- Certified SKZI are selected in accordance with a certain level of security in accordance with the Order number 378 of the FSB .
For ISPDN with UZ-3 it is possible to use KS1, KS2, KS3. KC1 is, for example, C-Terra Virtual Gateway 4.2 for channel protection.
KC2, KC3 are represented only by hardware-software complexes, such as: ViPNet Coordinator, APKS Continent, S-Terra Gateway, etc.
If you have a UZ-2 or 1, then you will need KV1, 2 and KA class cryptographic tools. These are specific software and hardware systems, they are difficult to exploit, and performance characteristics are modest.

Reality: the law does not oblige the use of SKZI, certified by the FSB.
Source: https://habr.com/ru/post/446696/
All Articles